Network identity authentication method based on U-disk and dynamic differential password and system thereof
A network identity and authentication method technology, applied in the field of two-factor network identity authentication, can solve the problems of immature biometric authentication technology, insecure user names and passwords, and inability to solve the problem of popularization, achieving easy purchase, easy implementation, light weight effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
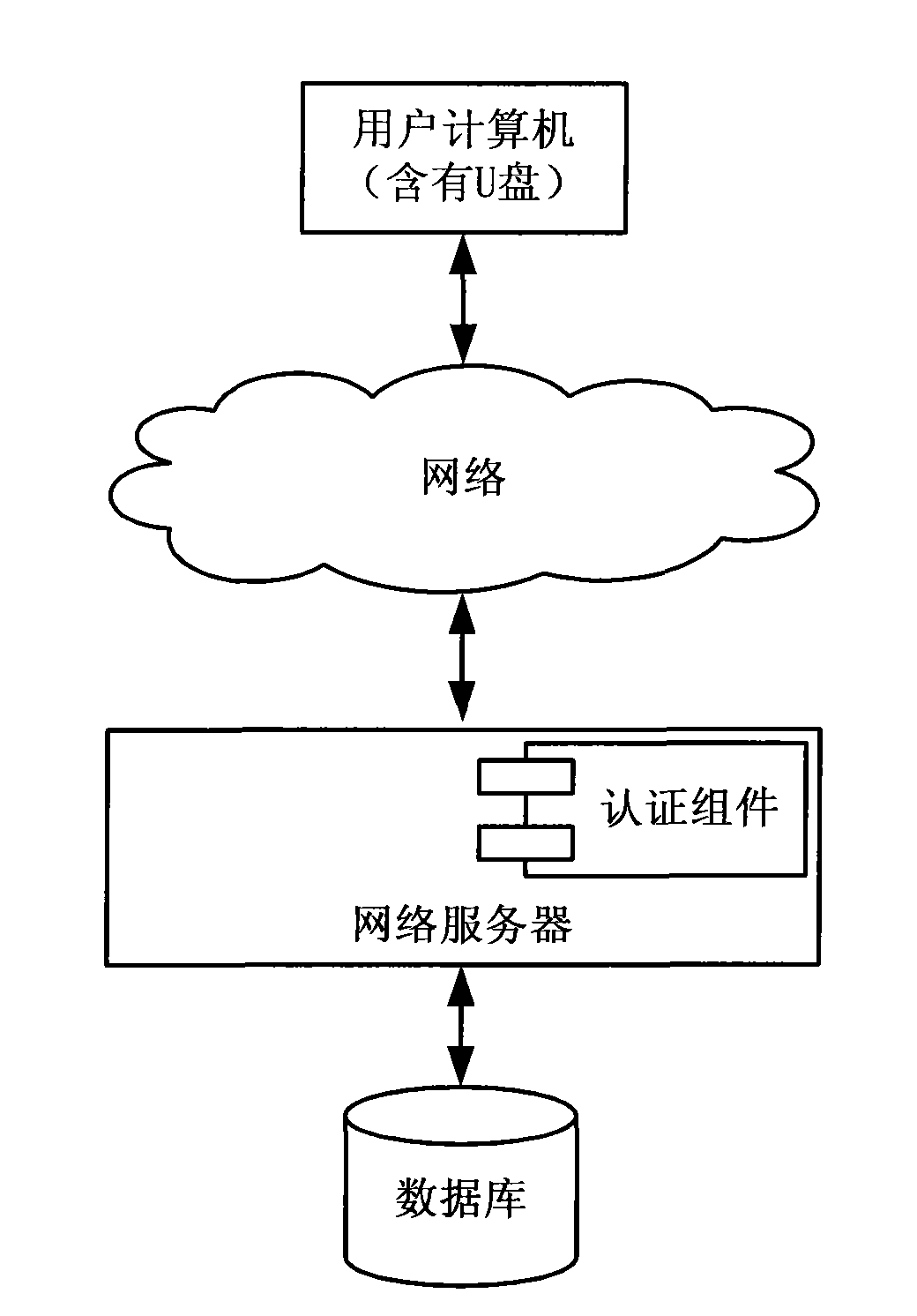
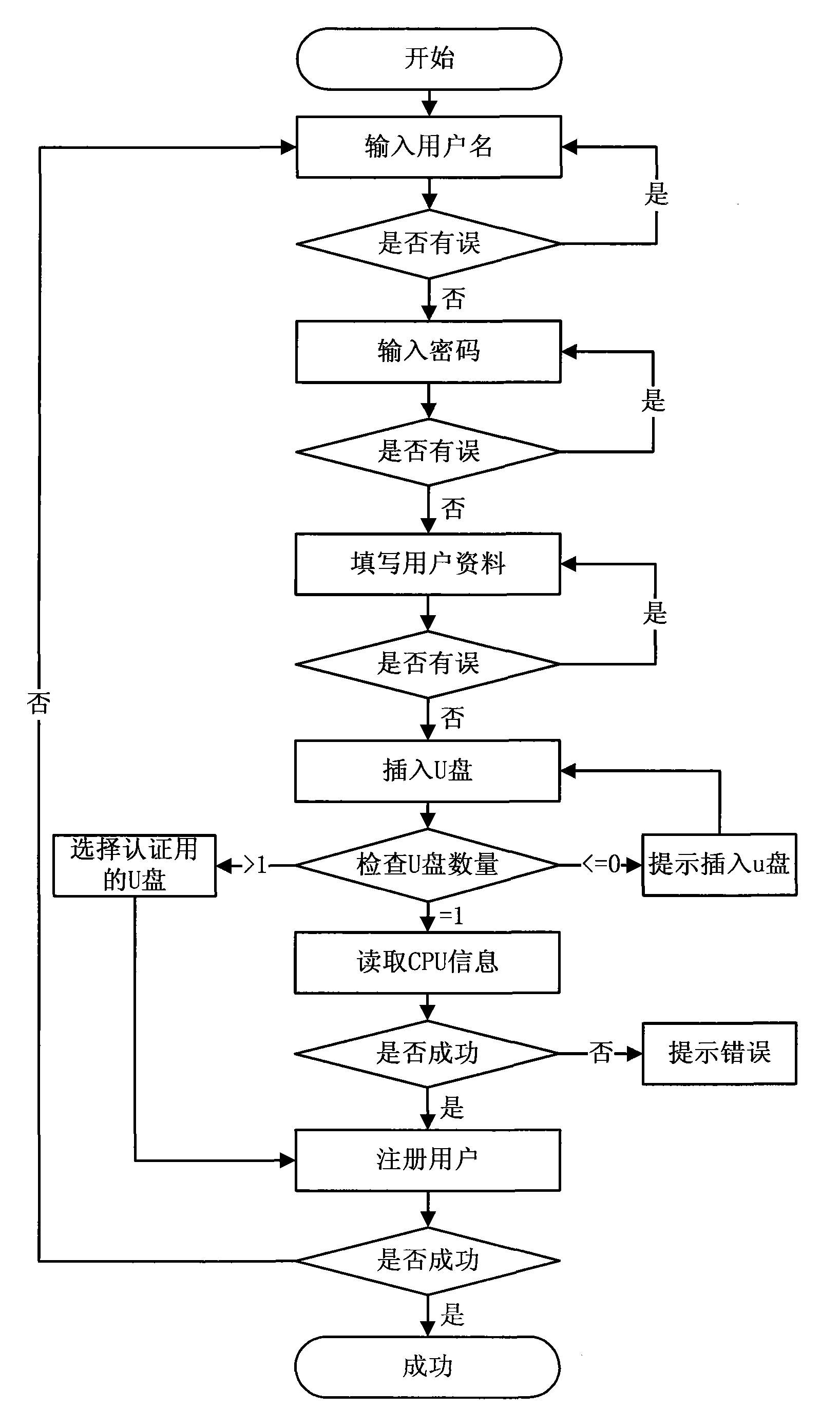
[0049] In order to make the purpose of the present invention, technical solutions and advantages clearer, the embodiment of the present invention will be further described below in conjunction with the accompanying drawings: because the USB interface and U disk are quite popular, what the present invention realizes is exactly based on U disk and dynamic difference password A network identity authentication method and system. Depend on figure 1 Visible, realize that the concrete system of the present invention is the same as traditional network system, all comprises: user computer, network server, database server, and its difference just is:
[0050] 1. The user's computer also includes a U disk plugged into the computer's USB interface;
[0051] 2. The network server contains two-factor authentication components based on U disk and dynamic differential password.
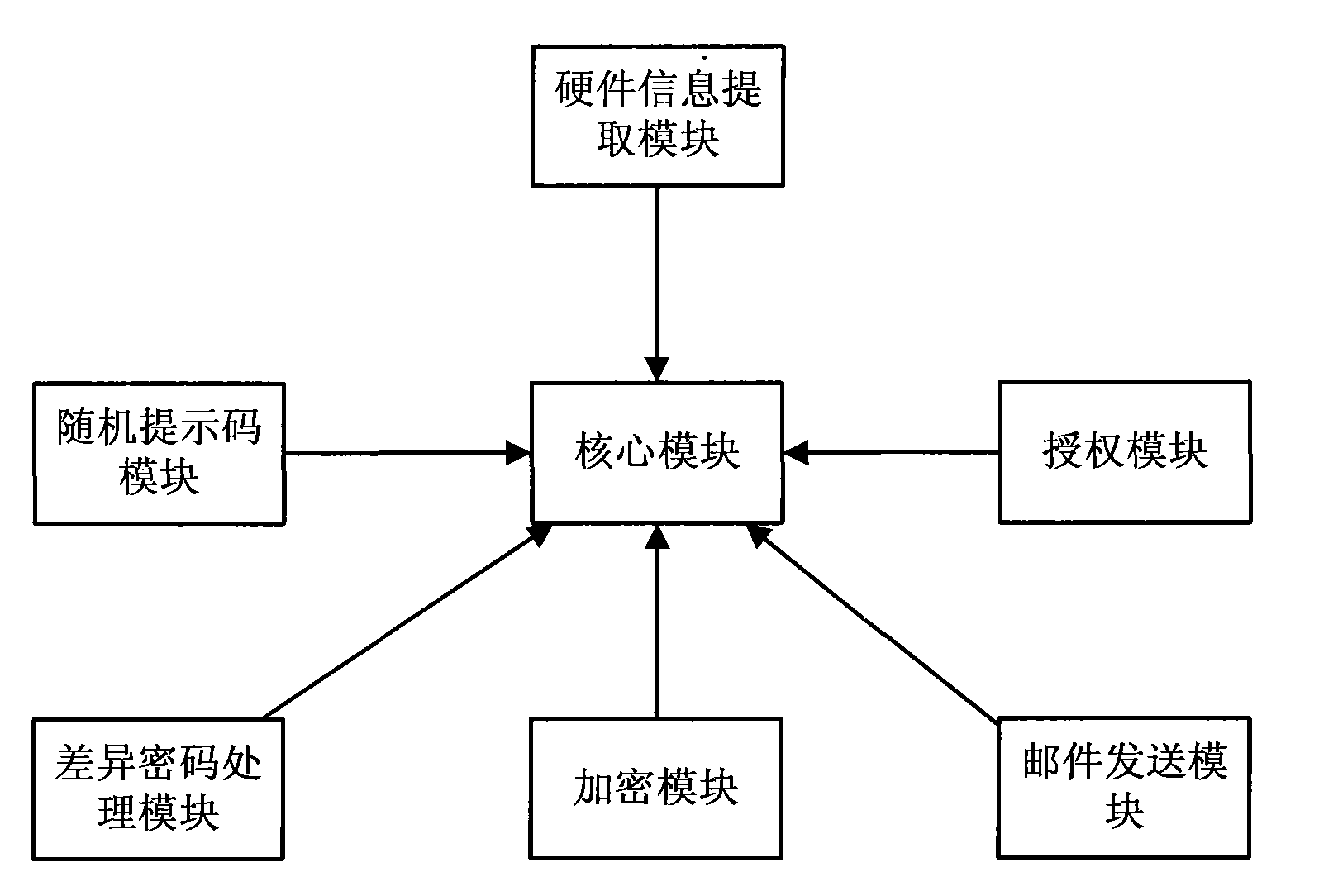
[0052] The authentication component as described in figure 2 As shown, it includes: a core module, a hardware ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap