System and method for realizing multifunctional information security device
An information security and multi-function technology, applied in the system field of realizing multi-function information security equipment, can solve the problems of increased cost, reduced reliability, and the inability of two devices to appear at the same time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
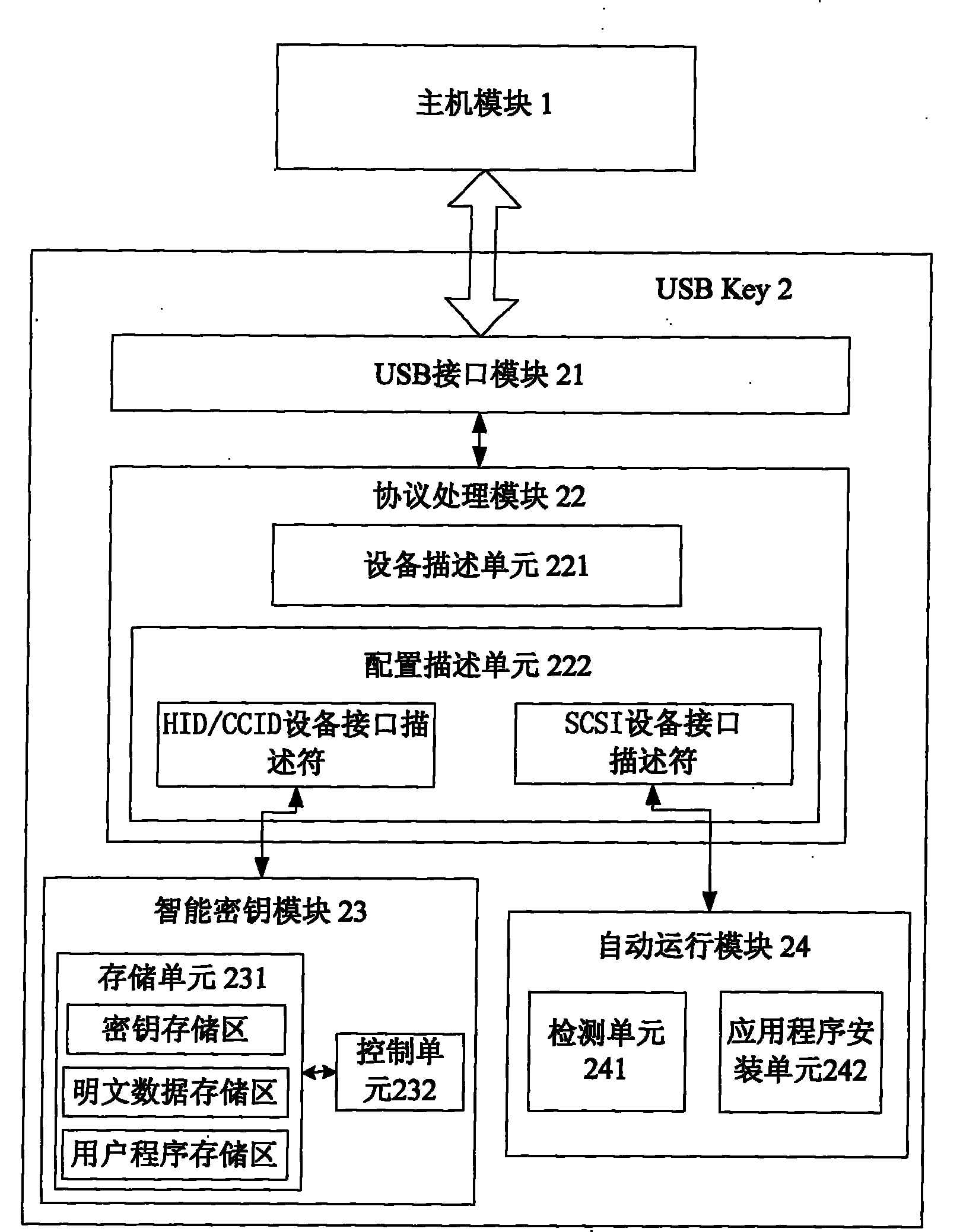
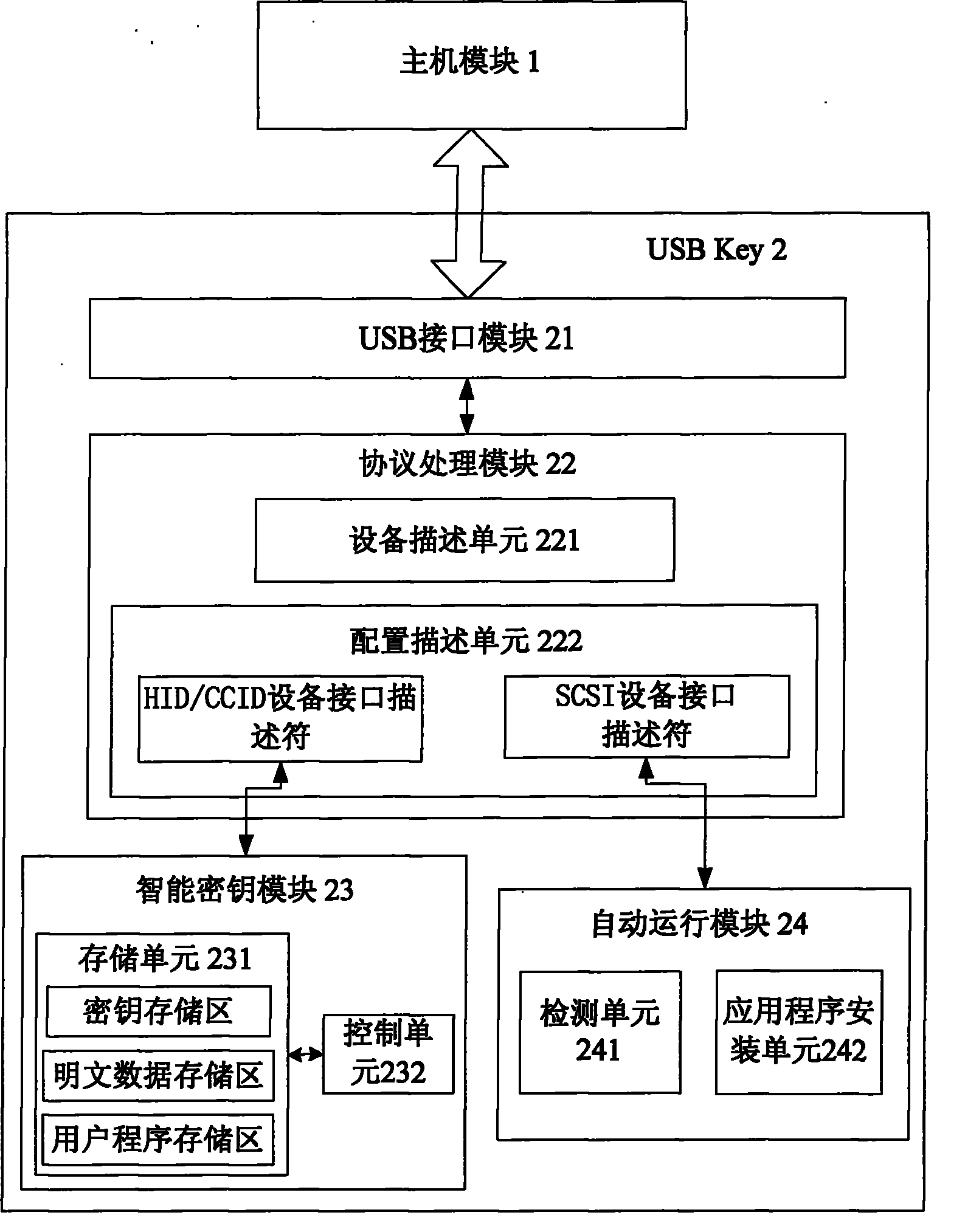
[0072] Such as figure 1 As shown, this embodiment provides a system for realizing multifunctional information security equipment, including a host module 1 and a USB Key 2, and the USB Key 2 includes a USB interface module 21, a protocol processing module 22, an intelligent key module 23, an automatic operation Module 24, protocol processing module 22 includes device description unit 221 and configuration description unit 222, configuration description unit 222 includes HID / CCID device interface descriptor and SCSI device interface descriptor, HID / CCID device interface descriptor and smart key module 23 Connected, the SCSI device interface descriptor is connected with the automatic operation module 24.
[0073] In USB Key 2,
[0074] The USB interface module 21 is used to establish a connection between the USB Key 2 and the host module 1 through the USB interface, and analyze and process the USB communication protocol;
[0075] The USB interface module 21 is a USB interface ...
Embodiment 2
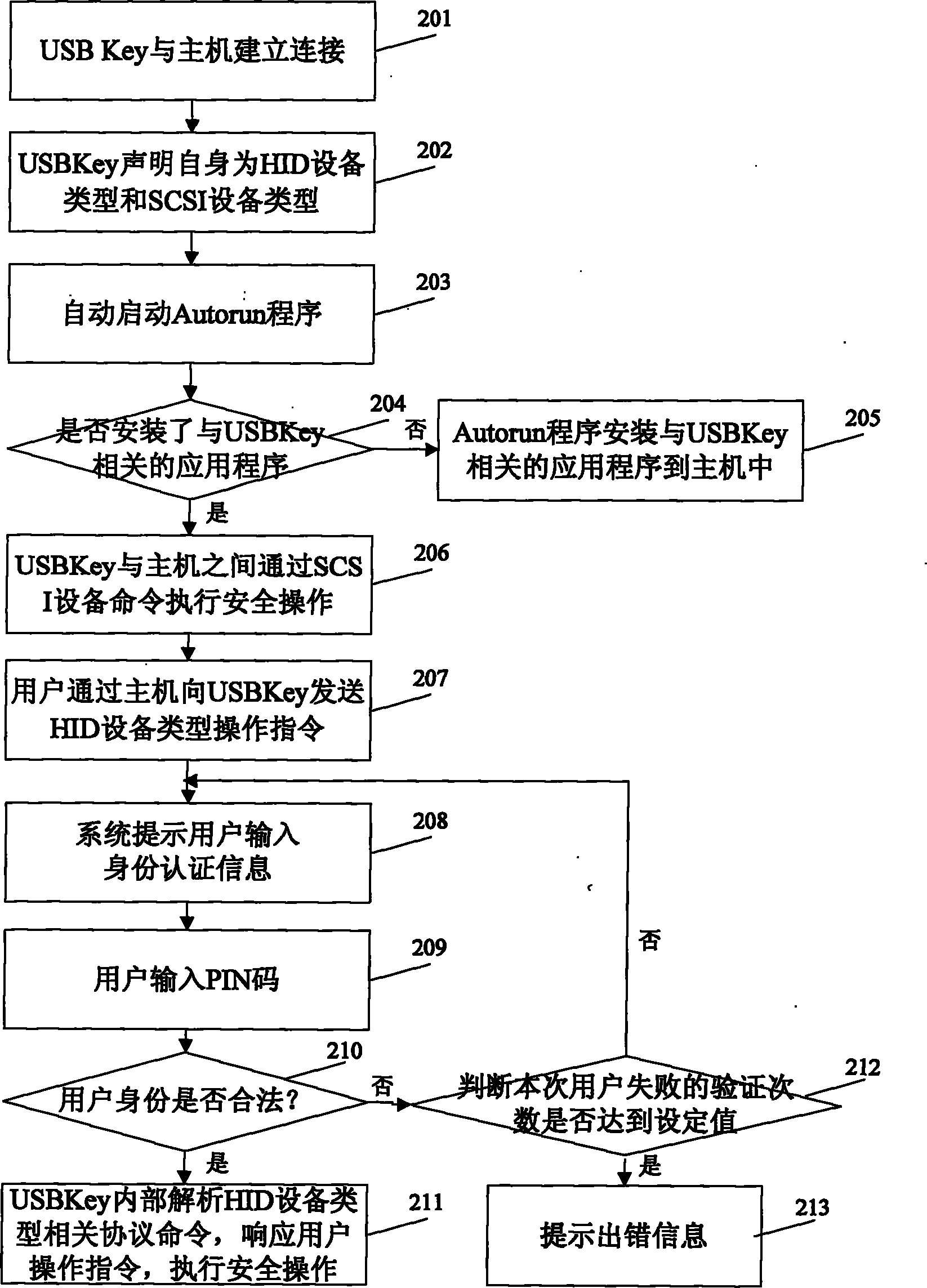
[0094] Such as figure 2 As shown, this embodiment provides a method for implementing a multifunctional information security device, which specifically includes the following steps:
[0095] Step 201: establish a connection between the USB Key and the host;
[0096] Step 202: USB Key declares itself as HID device type and SCSI device type;
[0097] In this embodiment, the USB Key declares itself to be an HID device type and a SCSI device type by reporting the device descriptors to the host as HID device descriptors and SCSI device descriptors.
[0098] Step 203: automatically start the Autorun program;
[0099] The Autorun program is pre-written by the USB Key manufacturer and stored in the USB Key.
[0100] Step 204: Autorun program detects whether the application program related to USB Key has been installed in the host computer, if the application program related to USB Key has been installed in the host computer, then perform step 206, if the application program related...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com