Recertification method, system and authentication device
A re-authentication and authentication technology, applied in transmission systems, data exchange through path configuration, electrical components, etc., can solve problems such as increasing the difficulty of implementation, and achieve the effects of reducing implementation complexity, shortening delay, and avoiding impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
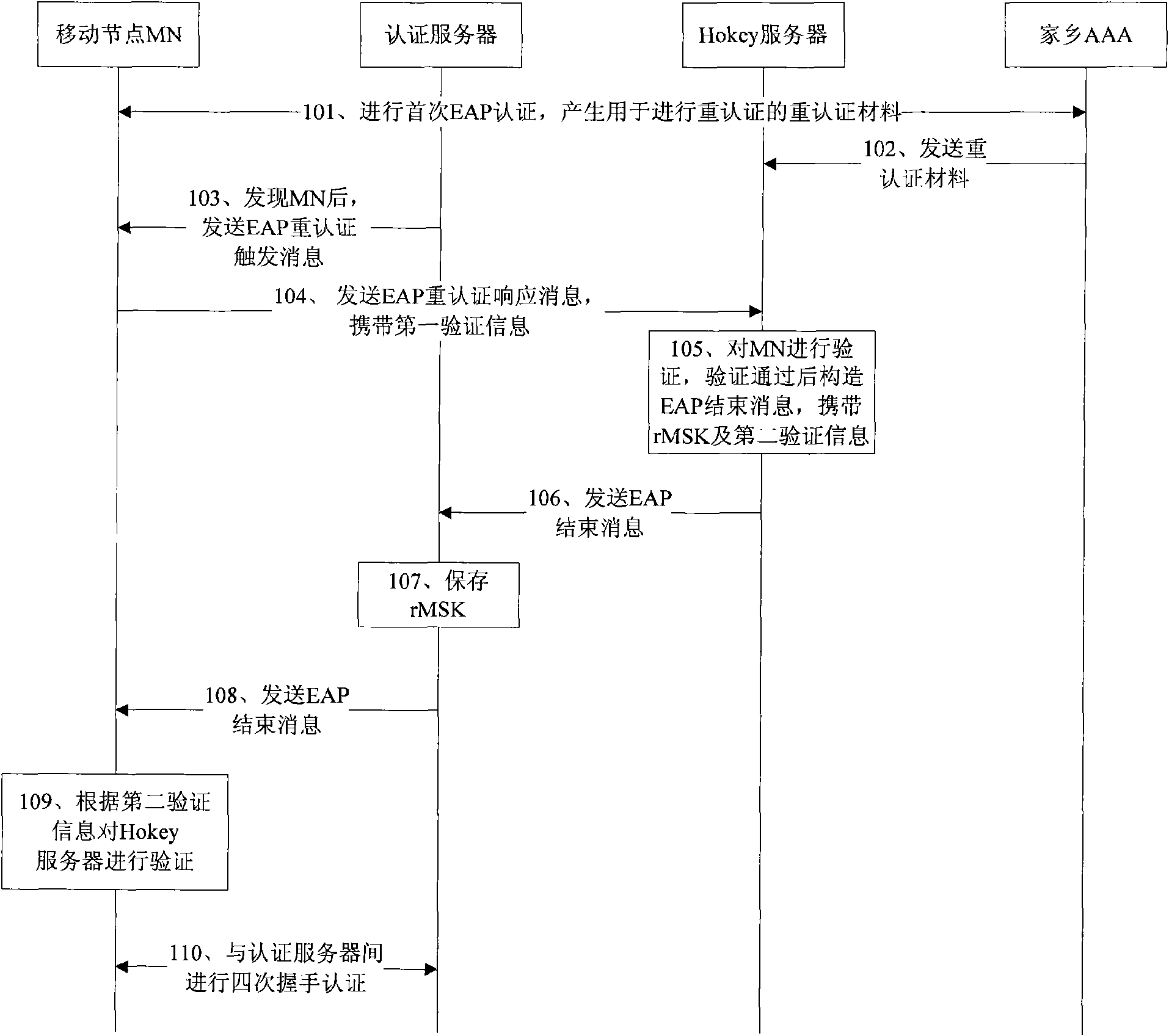
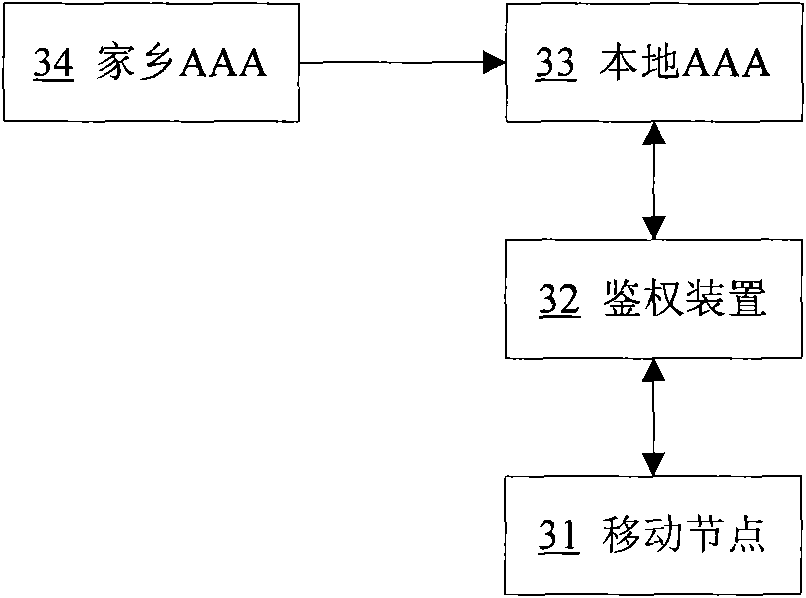
[0034] In the embodiment of the present invention, the mobile node MN that supports re-authentication is authenticated once by the authentication device of the visited network, thereby avoiding the change of the existing network equipment and the existing protocol framework during the re-authentication process, and improving the re-authentication efficiency.
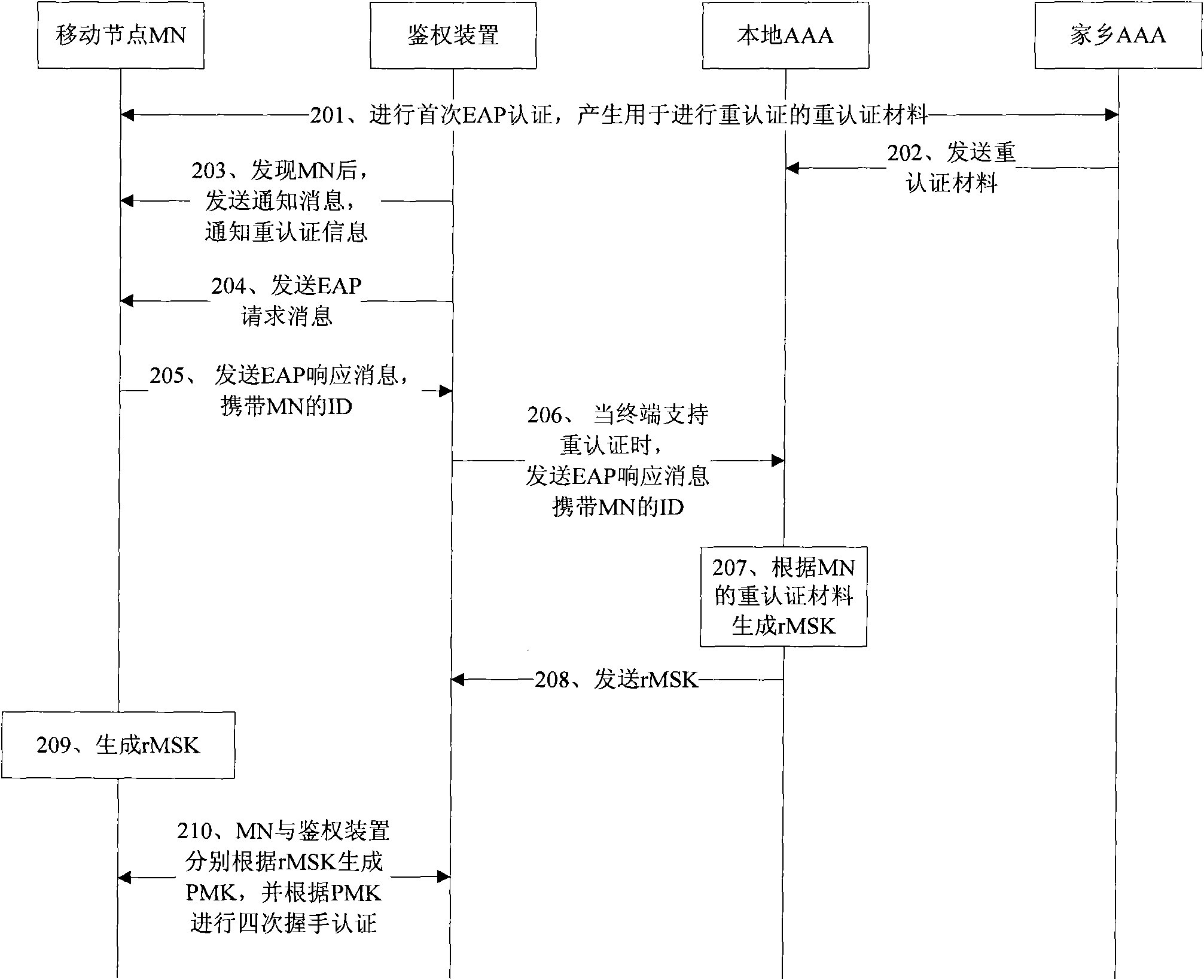
[0035] Such as figure 2 As shown, it is a flow chart of a re-authentication method provided by the embodiment of the present invention. The re-authentication in the embodiment of the present invention refers to the re-authentication performed in the visited network after the mobile node MN moves from the home network to the visited network. In order to realize re-authentication, when the mobile node accesses the home network, it needs to complete the first access authentication with the home AAA, and the re-authentication material for re-authentication is generated between the MN and the home AAA (step 201) . Wherein,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com