VPN authentication method
An authentication method and legal technology, applied in the field of computer networks, can solve the problem of insufficient authentication strength, and achieve the effect of reducing the probability of user account theft and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] At first, illustrate the inventive method:
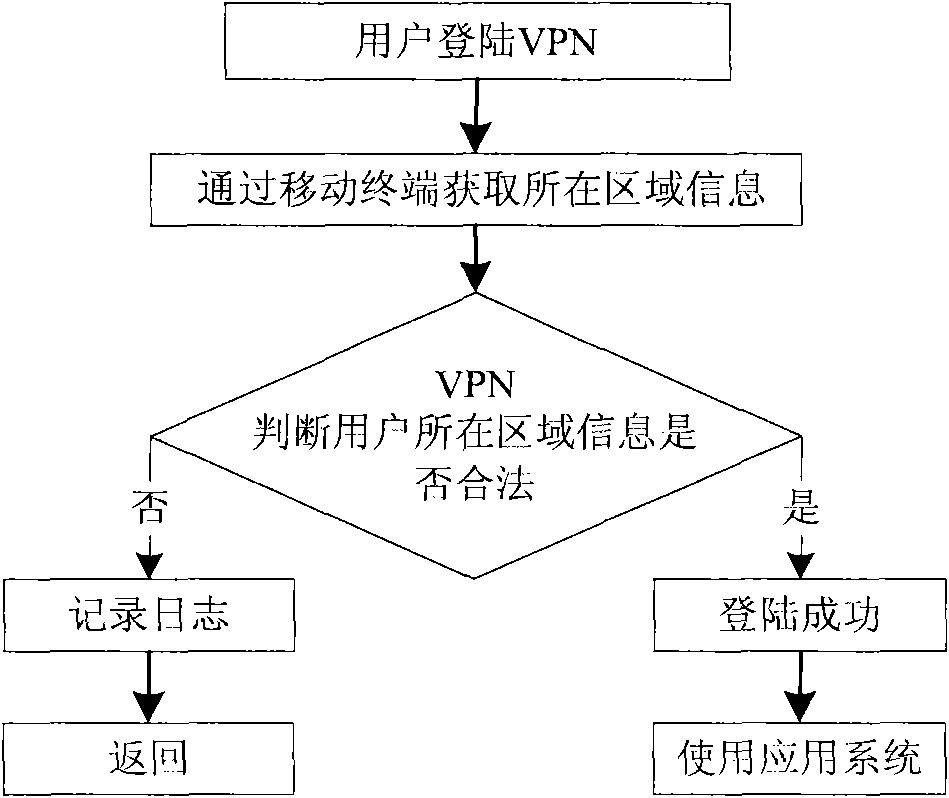
[0028] like figure 1 As shown, in the VPN authentication method of the present invention, on the mobile terminal user side, before the user logs in to the VPN, it is necessary to obtain the area information of the user through the mobile terminal, and the mobile terminal checks whether the current area information of the user is legal, thereby judging whether to allow The user logs in and uses the VPN.
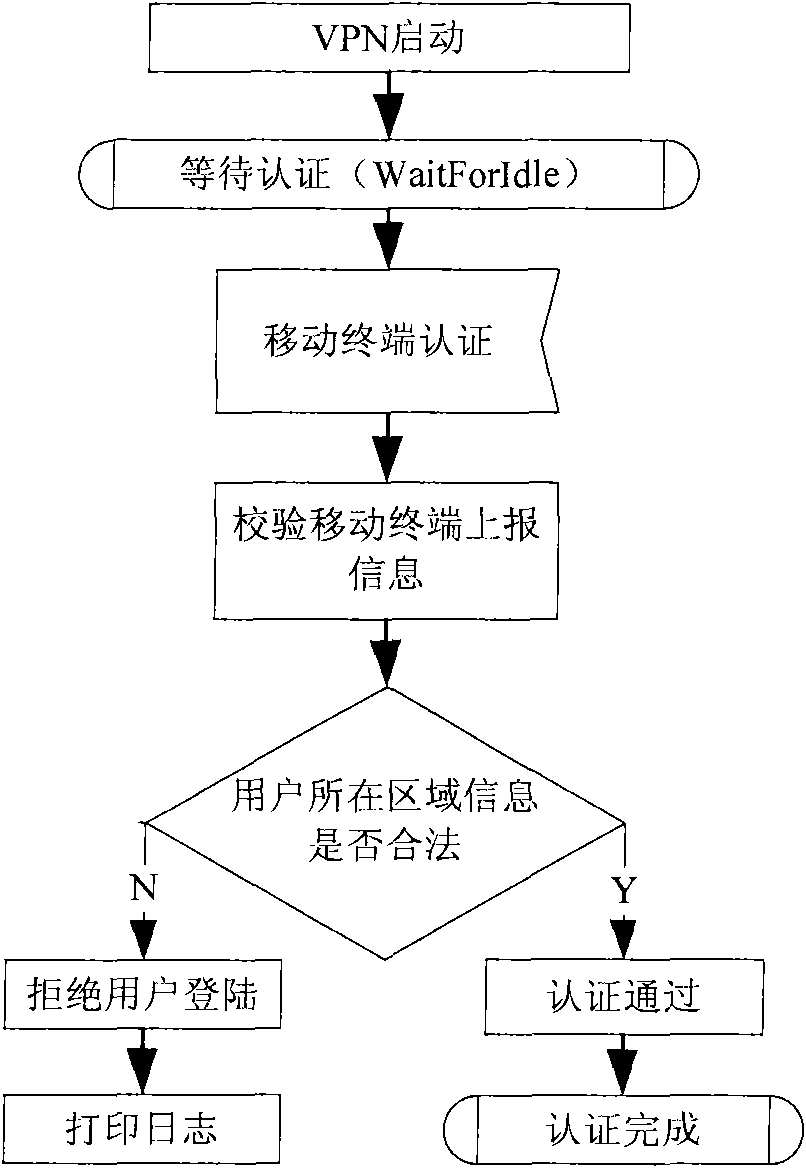
[0029] like figure 2 As shown, in the VPN authentication method of the present invention, on the network side, after the VPN is started, the user login message is monitored. After the user logs in, the area information reported by the user is obtained, and the information is verified to determine whether the area information of the user is illegal. , if it is an illegal area, deny the user access to the VPN, otherwise allow the user access for further authentication.
[0030] Further, the method of the present invention i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com