Network data mining method, network data transmitting method and equipment
A network data and network technology, applied in the field of computer networks, can solve problems such as occupying network bandwidth resources, not being targeted, and reducing user access experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
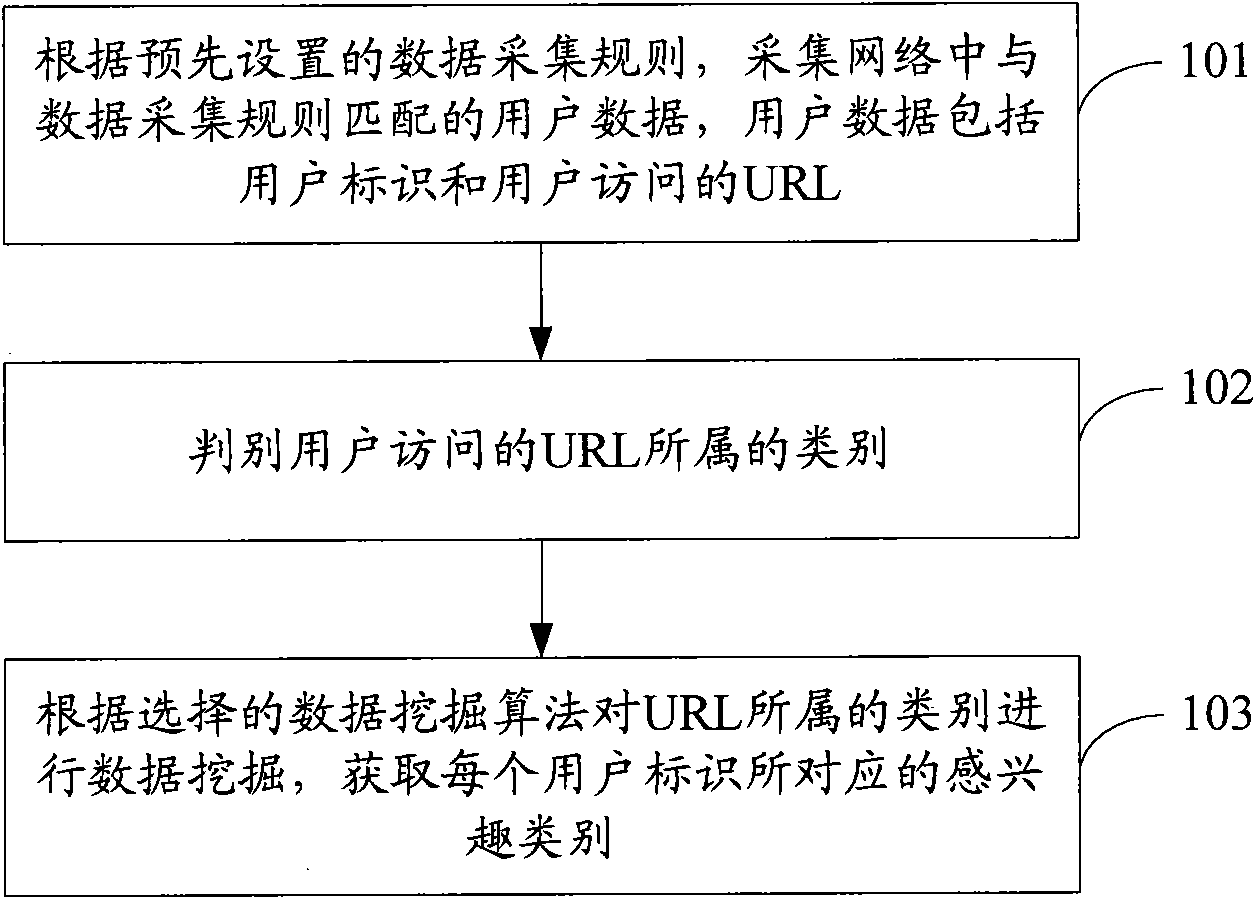
[0073] see figure 1 , is the flow chart of the first embodiment of the network data mining method of the present invention:
[0074] Step 101: According to the pre-set data collection rules, collect user data in the network that matches the data collection rules, and the user data includes user identifiers and URLs accessed by users.
[0075] Wherein, the user data may specifically be user behavior data; the data collection rules include: rule characteristics and rule actions, and the rule actions are used to indicate the operations that should be performed on the user data conforming to the rule characteristics, including: statistics or copying.
[0076] Among them, the statistical data in the user network data include user service usage time, user bandwidth usage, user traffic statistics by time / category, etc.; the copied data in the user network data includes the identity information of the user accessing network resources, URL, access time, access method, etc.
[0077] S...
no. 2 example
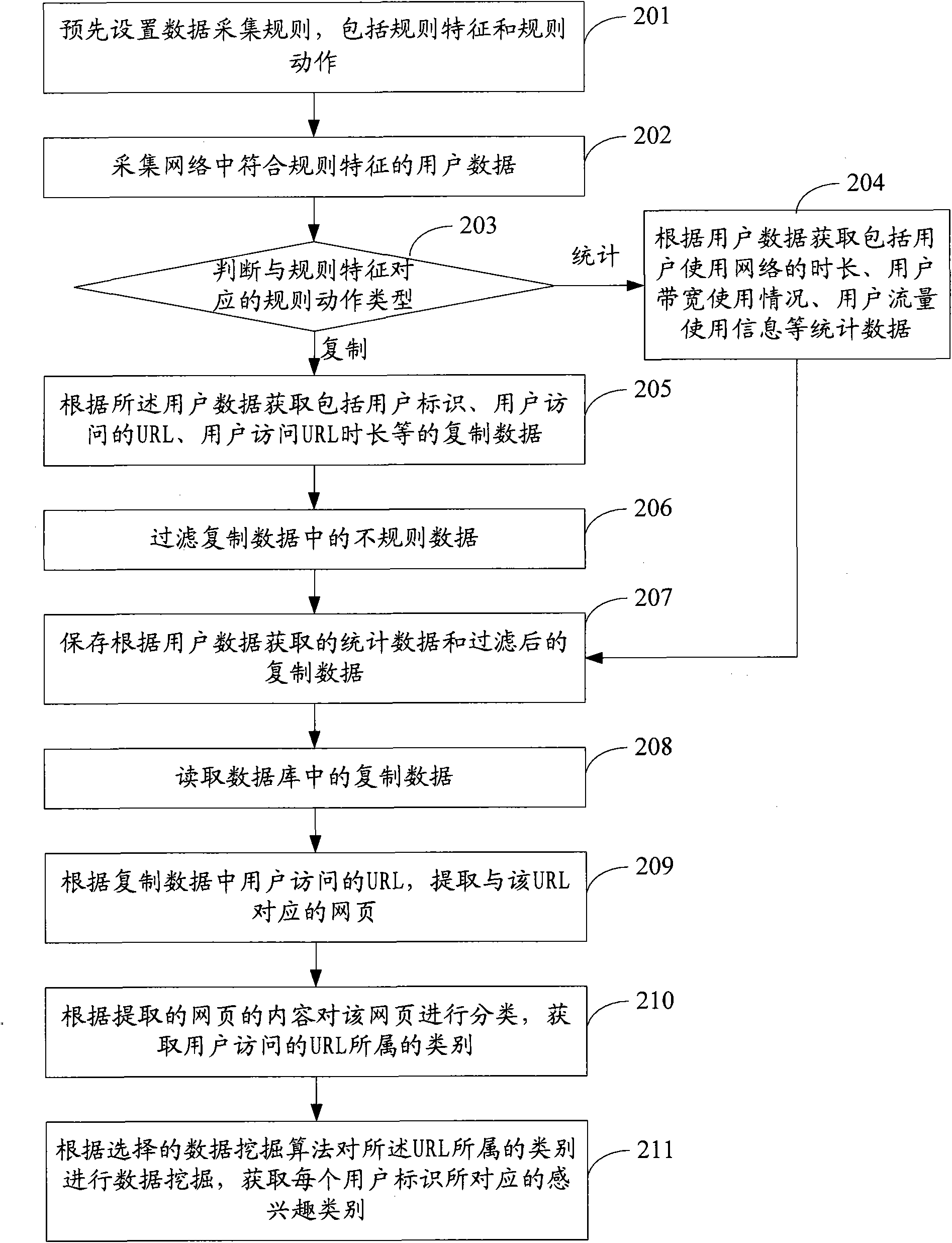
[0081] see figure 2 , is the flow chart of the second embodiment of the network data mining method of the present invention:
[0082] Step 201: Preset data collection rules, including rule features and rule actions.
[0083] Among them, the rule characteristics describe the conditions that should be met for collecting user data, such as IP address characteristics, port characteristics, content characteristics, etc.; rule actions describe the operations performed on user data that matches the rule characteristics, such as statistics, copying, etc.
[0084] Step 202: Collect user data in the network that conforms to the rules.
[0085] User data collection can be implemented on DPI (Deep Packet Inspection) equipment, network access equipment or backbone network equipment. When user data is collected, user identity and user business can be identified through deep content detection technology, so as to realize the collection of high-speed link user business data. Among them, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com