Dynamic password input rule
A dynamic password and rule technology, applied in the direction of user identity/authority verification, etc., can solve problems such as user identity authentication information protection threats, and achieve the effect of preventing phishing/domain spoofing/memory attacks and keyboard hacking attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
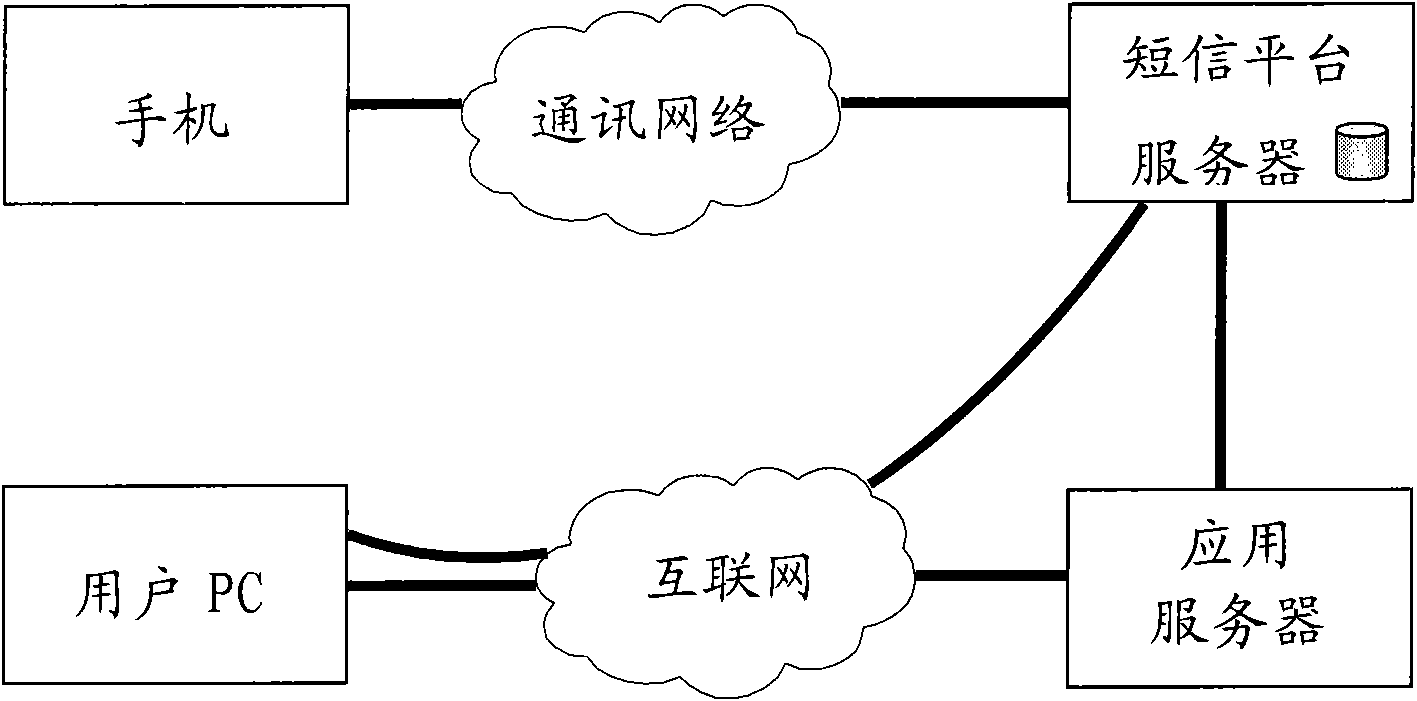
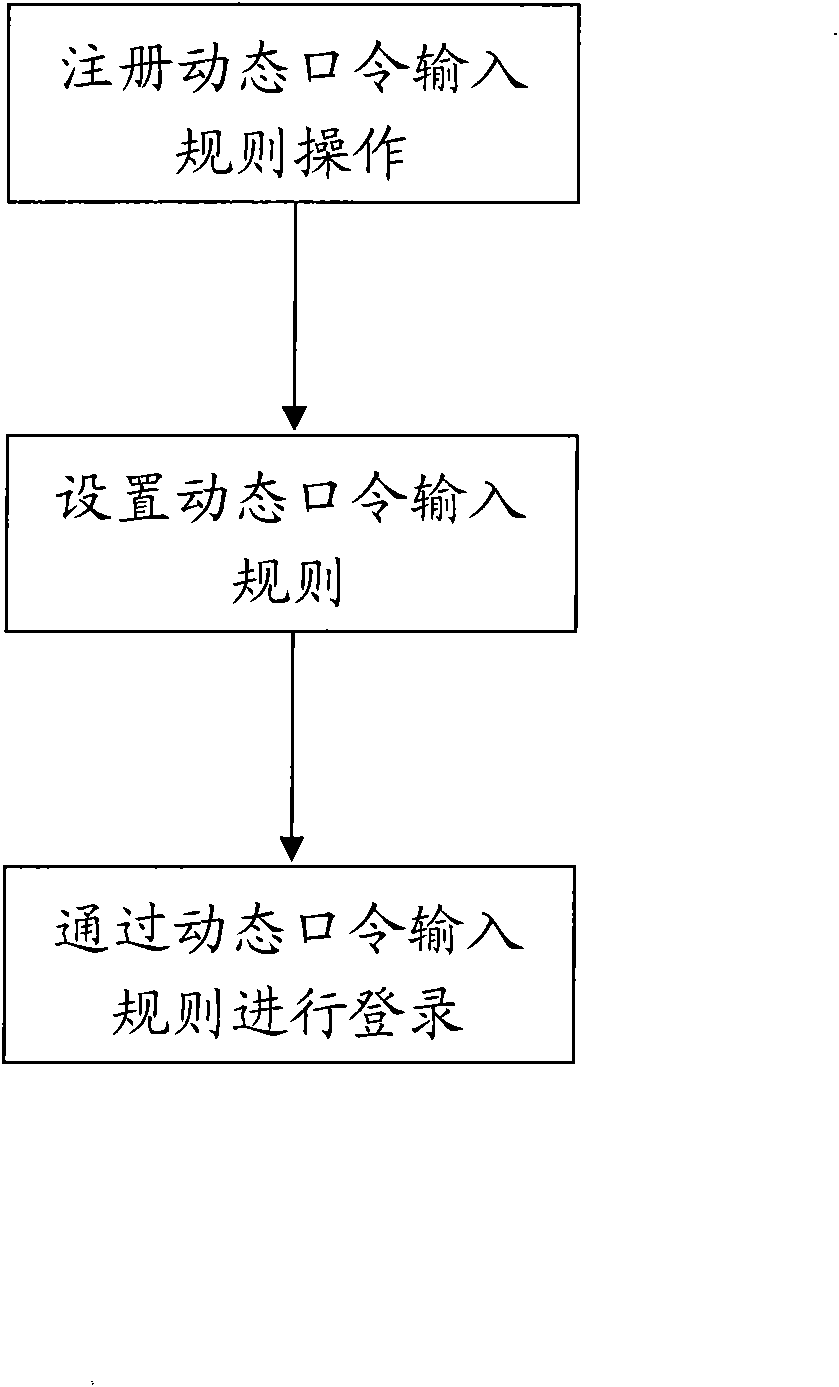
[0019] What the present embodiment described is a kind of dynamic password input rule, and the system that described rule uses comprises: mobile phone, communication network, short message platform server, user PC, Internet, application server, such as figure 1 shown. The mobile phone is an ordinary general-purpose mobile phone without any special requirements. Communication networks include mobile communication networks, the Internet, wired telephone networks, local area networks, wireless communication networks, and all communication networks that are used in the public domain and can communicate with each other are included. The SMS platform server includes a dynamic password input rule application control center that accepts the user's request information and verifies the user's identity through the user database. For authenticated legal users, the command password generation module generates a dynamic password, and the generated dynamic password is sent to the applicatio...
Embodiment 2
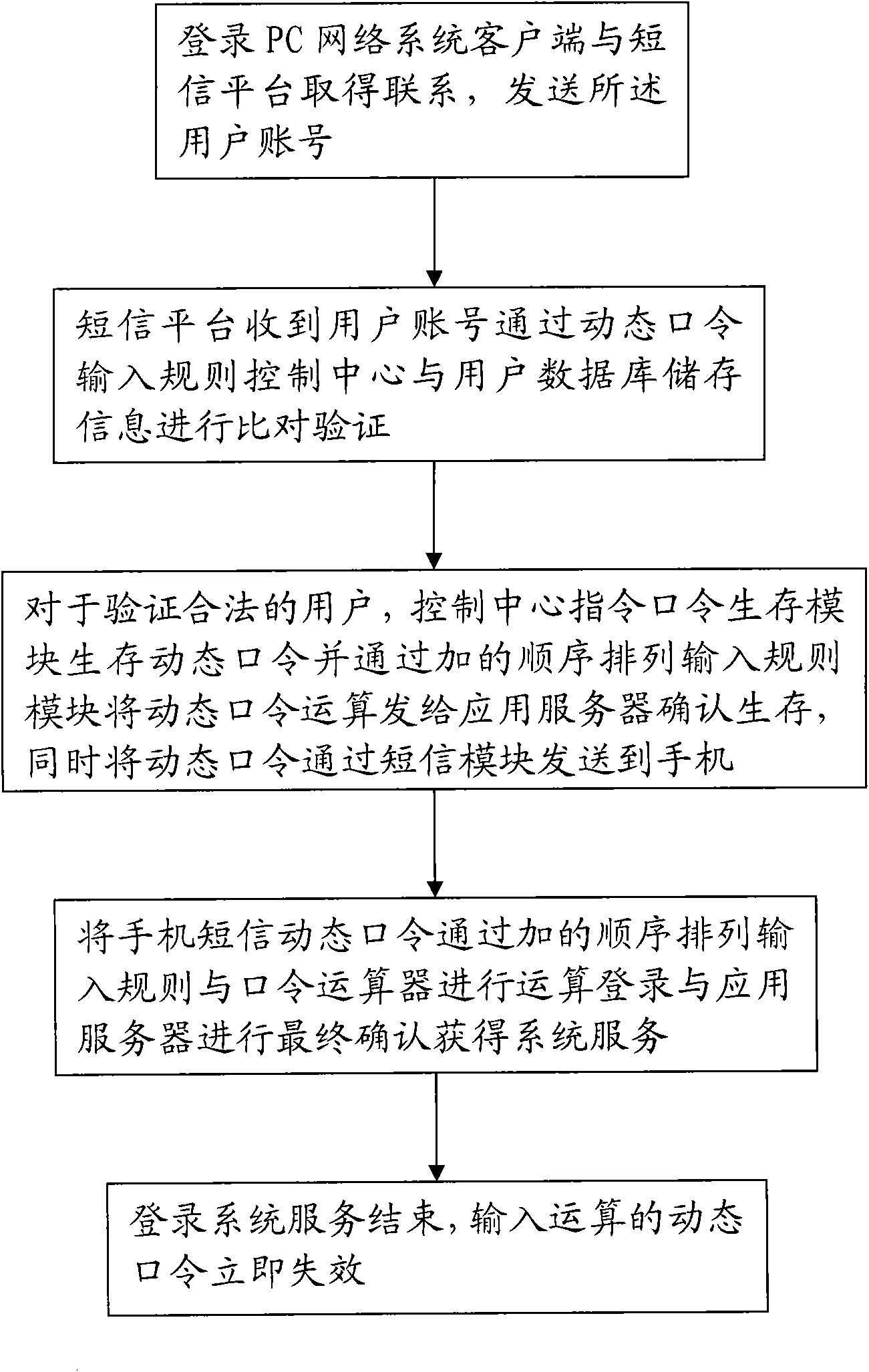
[0033] This embodiment is an improvement in the steps of logging in through the dynamic password input rules in the dynamic password input rules described in the first embodiment, as image 3 shown.
[0034] The sub-steps in the step of logging in through the dynamic password input rule include:
[0035] The sub-step of logging in the PC network system client to get in touch with the SMS platform, and sending the user account number.
[0036] The short message platform receives the user account and enters the rule control center through the dynamic password to compare and verify the information stored in the user database. If the information comparison and verification error will stop the operation immediately, if the information comparison verification is correct, then enter the next sub-step.
[0037] For authenticated legal users, the control center instructs the password survival module to save the dynamic password and arranges the input rule module to send the dynamic pa...
Embodiment 3
[0041] What is described in this embodiment is the step of logging in through the dynamic password input rules described in the second embodiment. The dynamic passwords described in the step of adding input rules are arranged in order.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com