Security network invasion detection system suitable for virtual machine environment
An intrusion detection system and intrusion detection technology, applied in the field of computer security, can solve the problems of undetectable intrusion behavior and threats to the security of the intrusion detection system, and achieve the effect of strong anti-attack ability and robustness, and convenient global unified configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The invention utilizes the isolation of the virtual machine, the transparency of the underlying system, and high efficiency to design a network intrusion detection system built on a novel virtual machine architecture. In this system, not only using the structural characteristics of the virtual machine to achieve a more secure and robust intrusion detection system, but also paying great attention to how to use the mature intrusion detection theory to provide a new type of computer based on virtual computing theory The architecture implements security guarantees. The present invention will be described in further detail below in conjunction with the accompanying drawings.
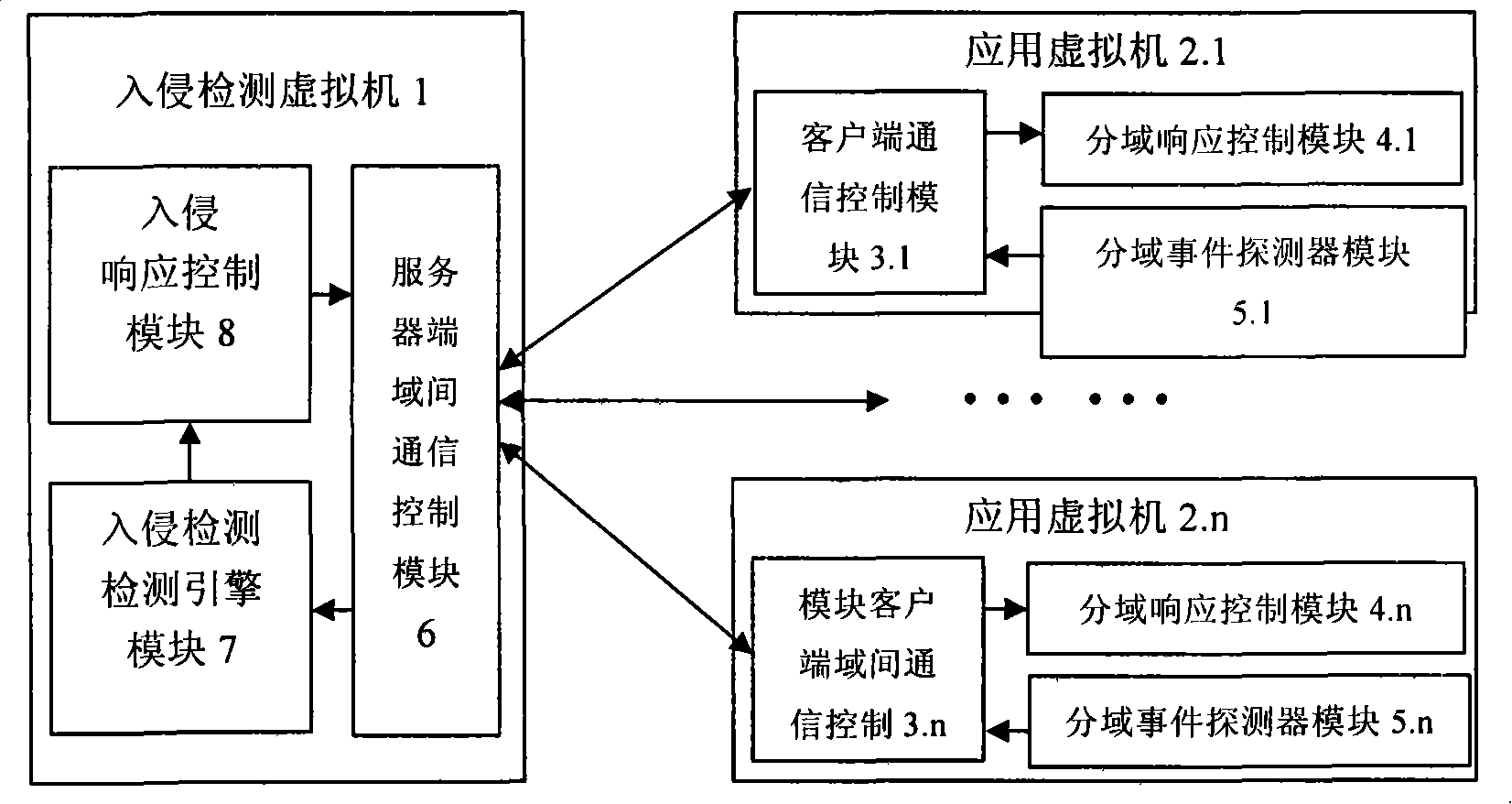
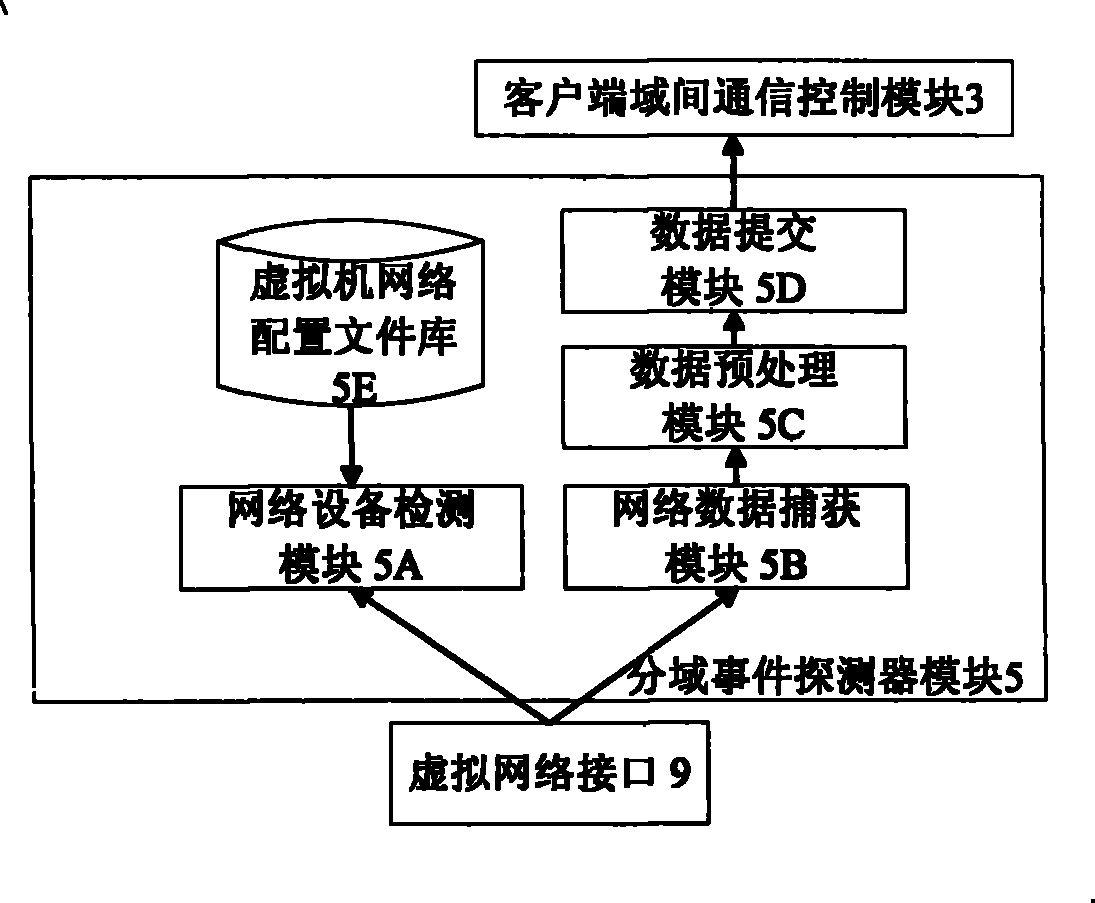
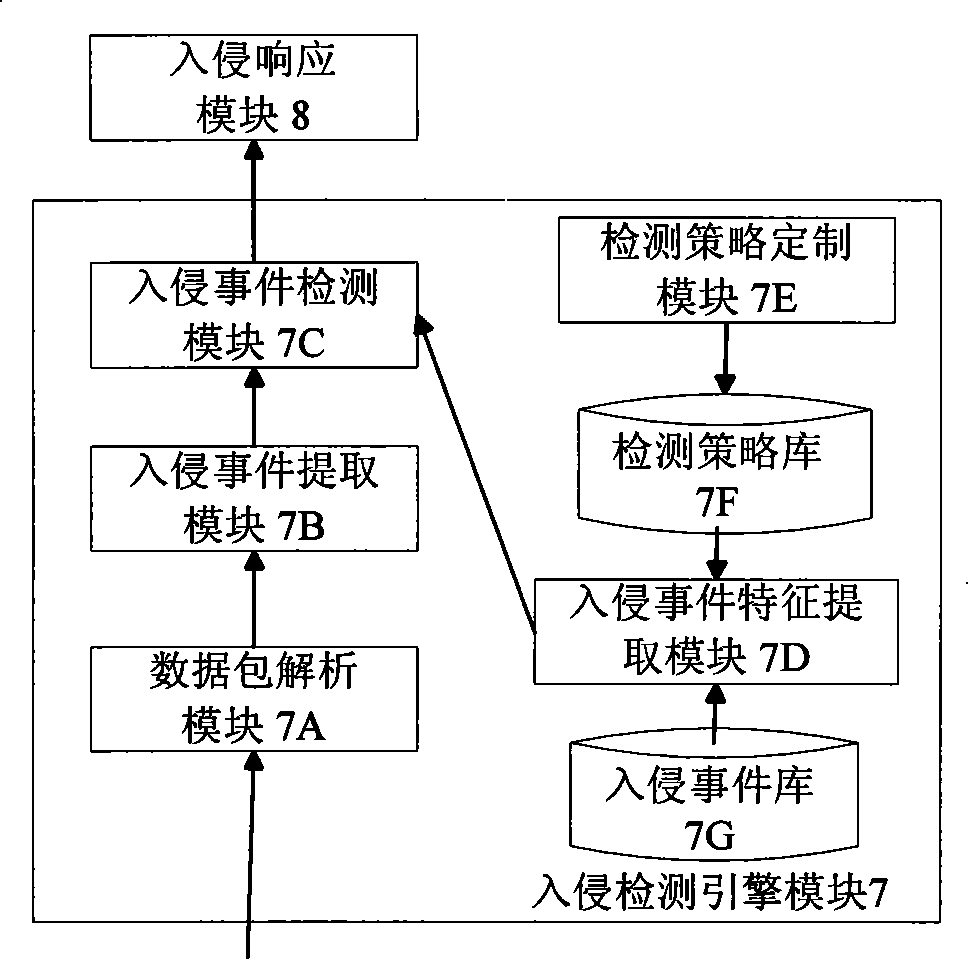
[0029] like figure 1 As shown, the safety net intrusion detection system suitable for virtual machines is mainly divided into two parts in terms of architecture: one part is the intrusion detection part located in the intrusion detection virtual machine 1, including the server-side inter-domain commun...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com