Method for reconstructing network attack path based on frequent pattern-growth algorithm
A frequent pattern growth and attack path technology, applied in the field of network information security, can solve problems such as difficulty in ensuring the accuracy of results, resource consumption, and the Apriori algorithm is not suitable for mining long frequent sequences, so as to reduce system overhead and improve mining efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
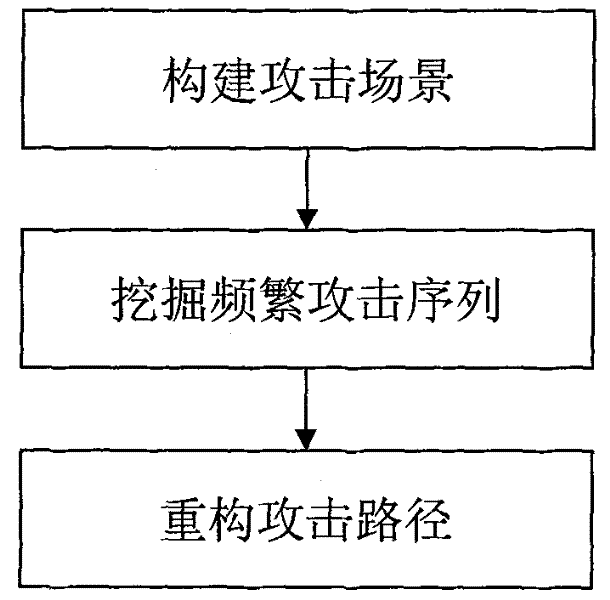
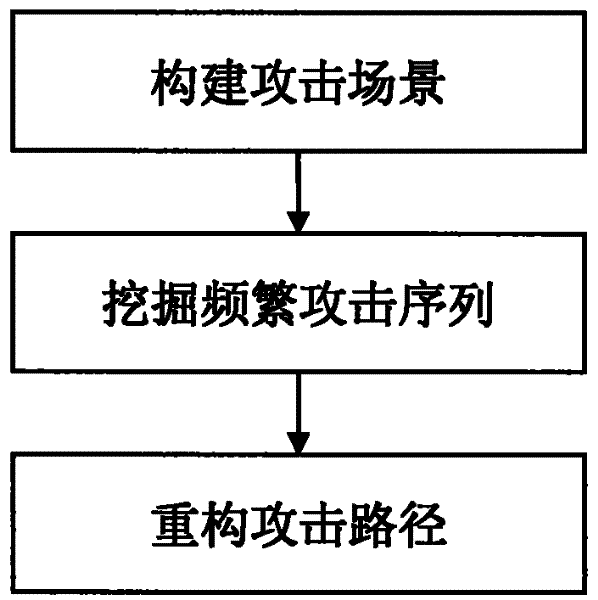
[0091] The method of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
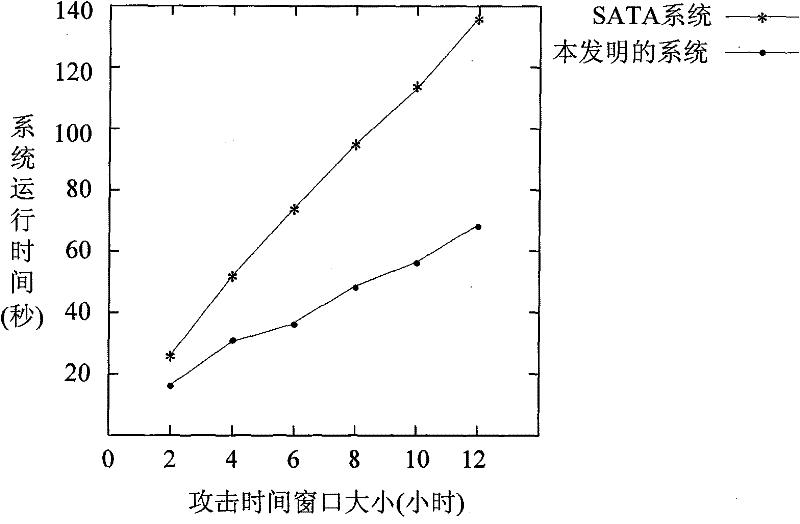
[0092] In order to test the validity of the method proposed by the present invention, a set of application system designed based on the principle of the method is used for experiments. The experimental hardware environment is a pre-built local area network, in which three hosts are configured, and the hosts are connected by a hub; the software environment is: IDS uses snort, scanner uses x-scan, and antivirus software uses Kaspersky. Randomly select a host as the attacker, and control it to attack another host as the attacked host. Anti-virus software and scanners are installed on the attacked host, and IDS is installed on the third host.
[0093] In order to simulate the real attack scenario more effectively, the background data traffic in the attack scenario is simulated using the DAPRA2000 dataset. After the experiment start...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com