Binary linear transformation method for diffusion layer in substitution-permutation network block encryption
A binary linear and permutation network technology, applied in electrical components, safety communication devices, digital transmission systems, etc., can solve problems such as inexhaustibility, high computational complexity, and failure to reach the theoretical optimal value, and achieve high operating efficiency, Achieve logical and simple effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention is further described by examples below, but it should be noted that the purpose of announcing the embodiments is to help further understand the present invention, but those skilled in the art can understand: without departing from the spirit of the present invention and the appended claims Various substitutions and modifications are possible within the scope. Therefore, the present invention should not be limited to the content disclosed in the examples, and the protection scope of the present invention is subject to the scope defined in the claims.
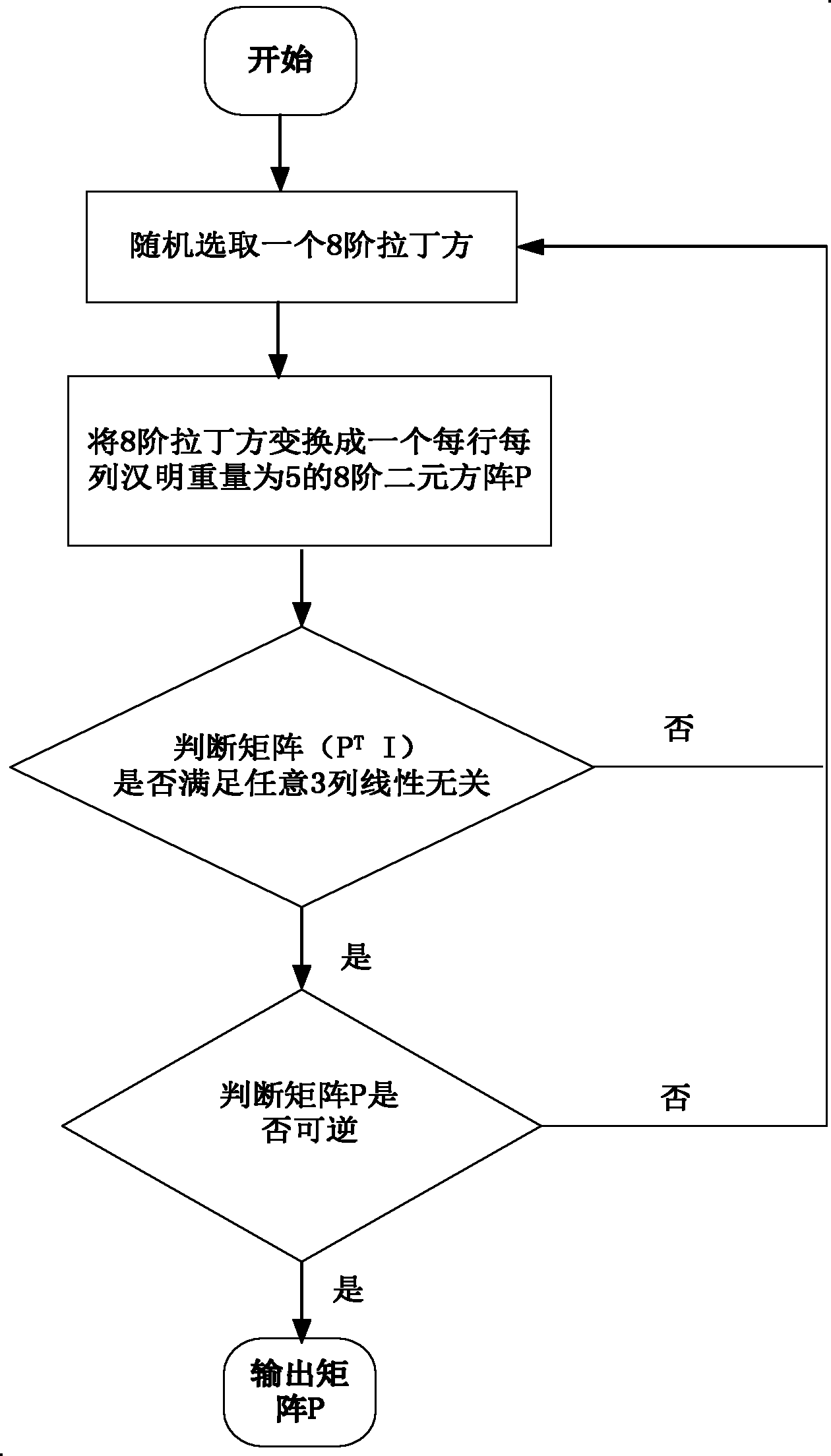
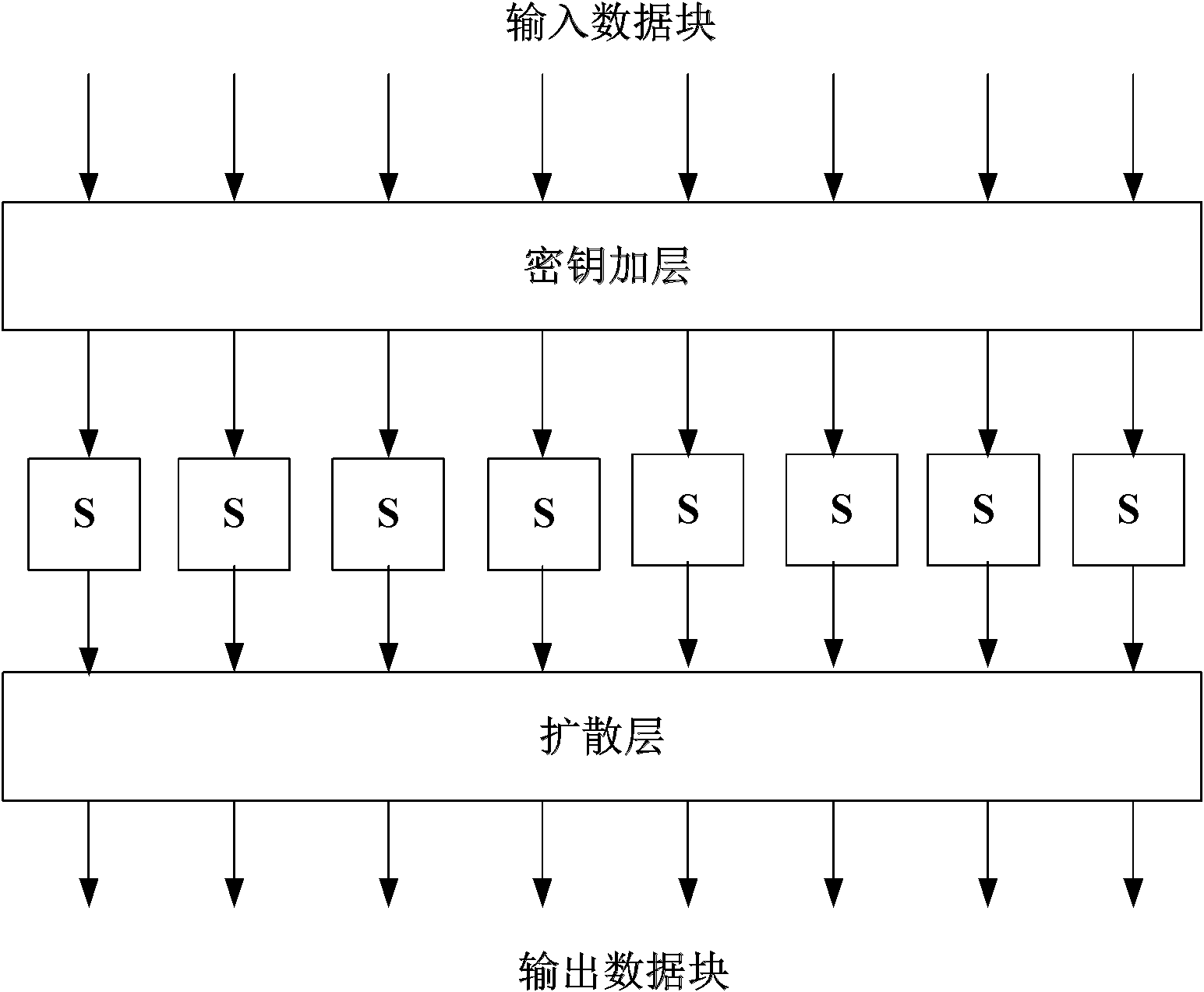
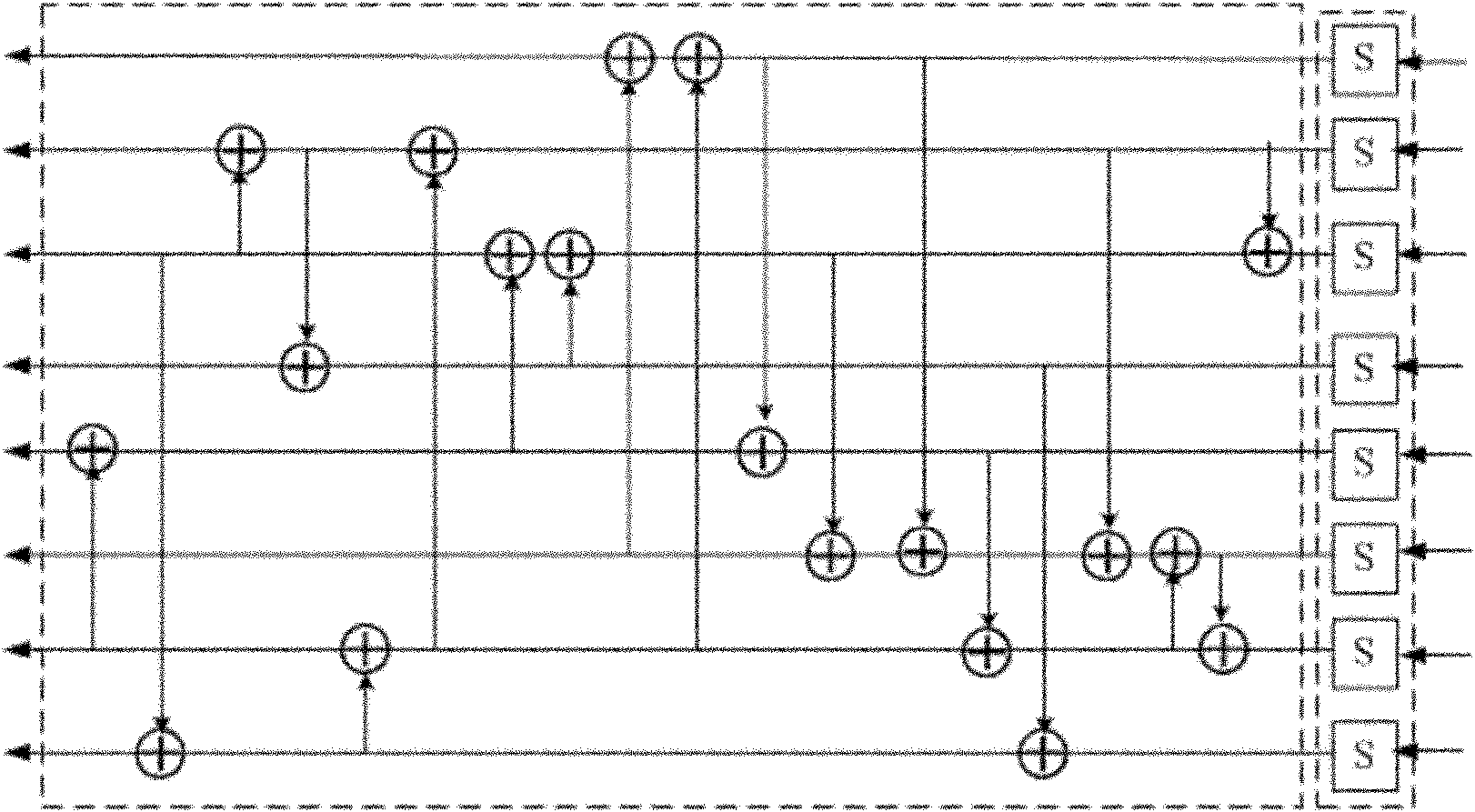
[0025] As we all know, it is difficult to generate all standard Latin squares of order 6 and above, and it can be said to be a historical problem. A processing method provided by this example is to first analyze the properties of the four heavy five elements, write four heavy five elements according to this property, and then convert it into the first four lines of the 8th-order Latin square, and fina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com