Method and system for processing strategy conflict by user equipment
A technology for user equipment and processing strategies, applied in network traffic/resource management, access restrictions, electrical components, etc., can solve problems such as UE's inability to access the network in time and affect user experience, and achieve the effect of improving experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
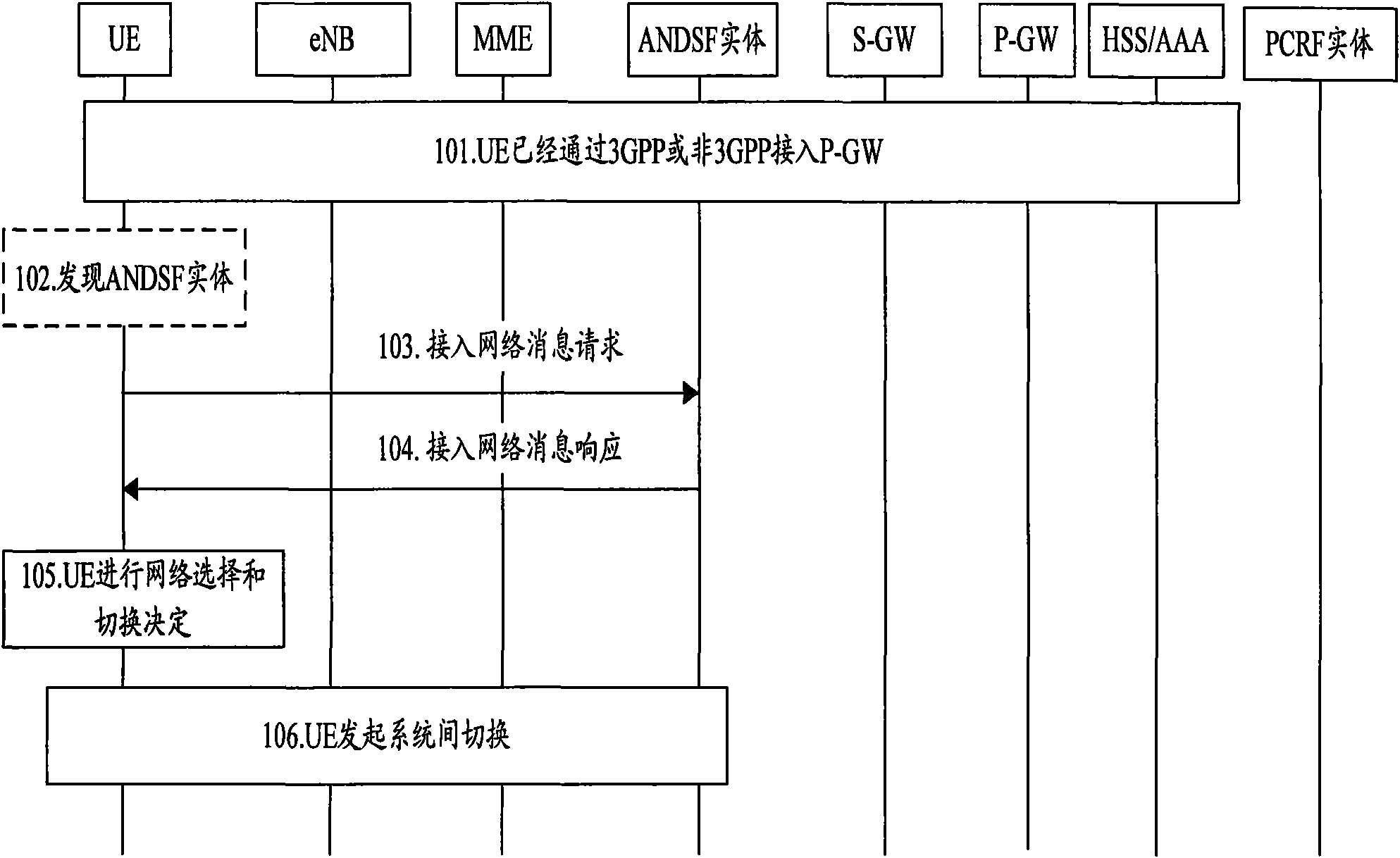
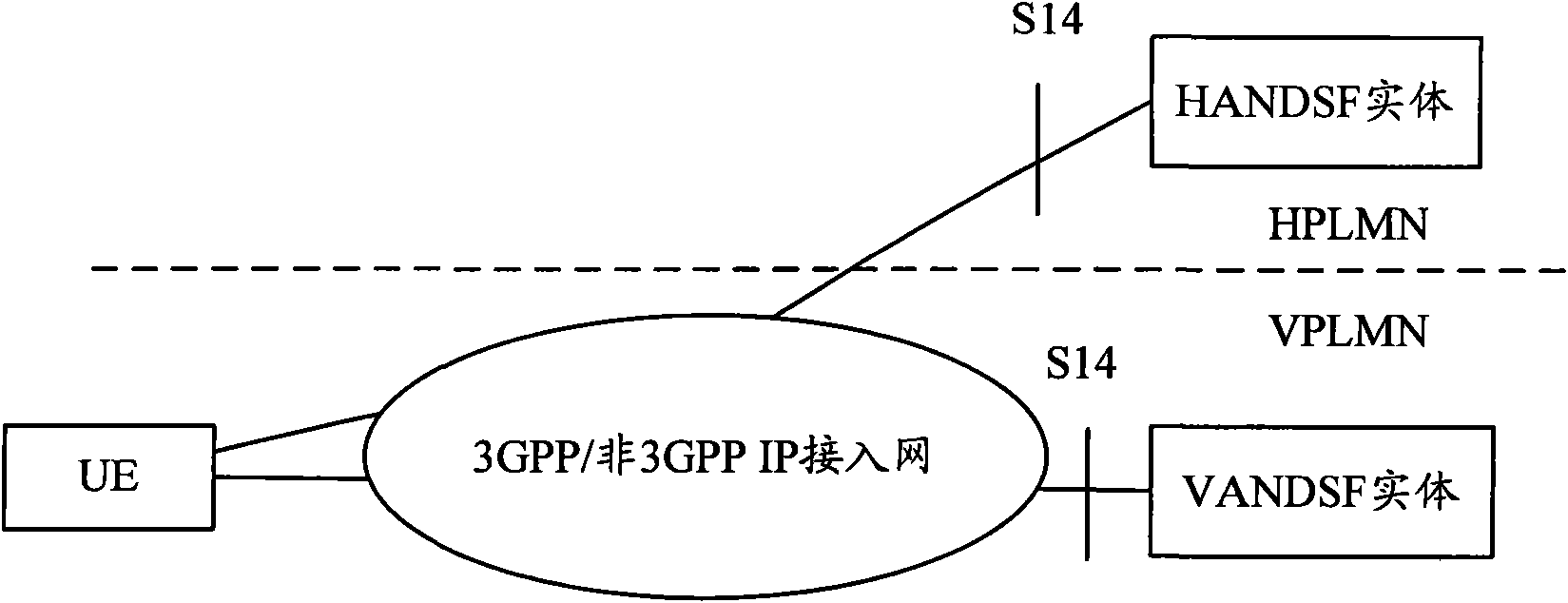
[0063] The UE first accesses the EPS system through a 3GPP access network or a trusted / untrusted non-3GPP access network. In the roaming scenario, the UE obtains different policies A1 and A2 from the HANDSF entity and the VANDSF entity respectively. This embodiment mainly deals with the case that policy A1 has RAT redundancy. The process of this embodiment includes the following steps:
[0064] Step 301, according to the policy A2 delivered by the VANDSF entity, screen different RAT categories in the policy A2, and sort the RAT categories according to the priority of the policy A2.
[0065] Step 302, according to the sorting of RAT categories, sort the access networks of different RAT categories in the policy A1 into corresponding RAT categories according to their priorities.
[0066] Here, if the RAT category in policy A1 is redundant, the RAT category is added to the end of the sequence, and the access networks to which it belongs are sorted by priority.
[0067] Step 303...
Embodiment 2
[0085] The UE first accesses the EPS system through a 3GPP access network or a trusted / untrusted non-3GPP access network. In the roaming scenario, the UE obtains different policies A1 and A2 from the HANDSF entity and the VANDSF entity respectively. This embodiment mainly deals with the situation that policy A2 has access network redundancy. The process of this embodiment includes the following steps:
[0086] Step 401: According to the policy A2 delivered by the VANDSF entity, screen different RAT categories in the policy A2, and sort the RAT categories according to the priority of the policy A2.
[0087] Step 402, according to the sorting of RAT categories, sort the access networks of different RAT categories in the policy A1 into corresponding RAT categories according to their priorities.
[0088] Here, if the RAT category in policy A1 is redundant, the RAT category is added to the end of the sequence, and the access networks to which it belongs are sorted by priority.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com