Method and device for processing cipher key list items
A processing method and key table technology, applied in the field of communications, can solve the problems of allocation failure, unsatisfactory distribution of key table entries, and users not being able to go online.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
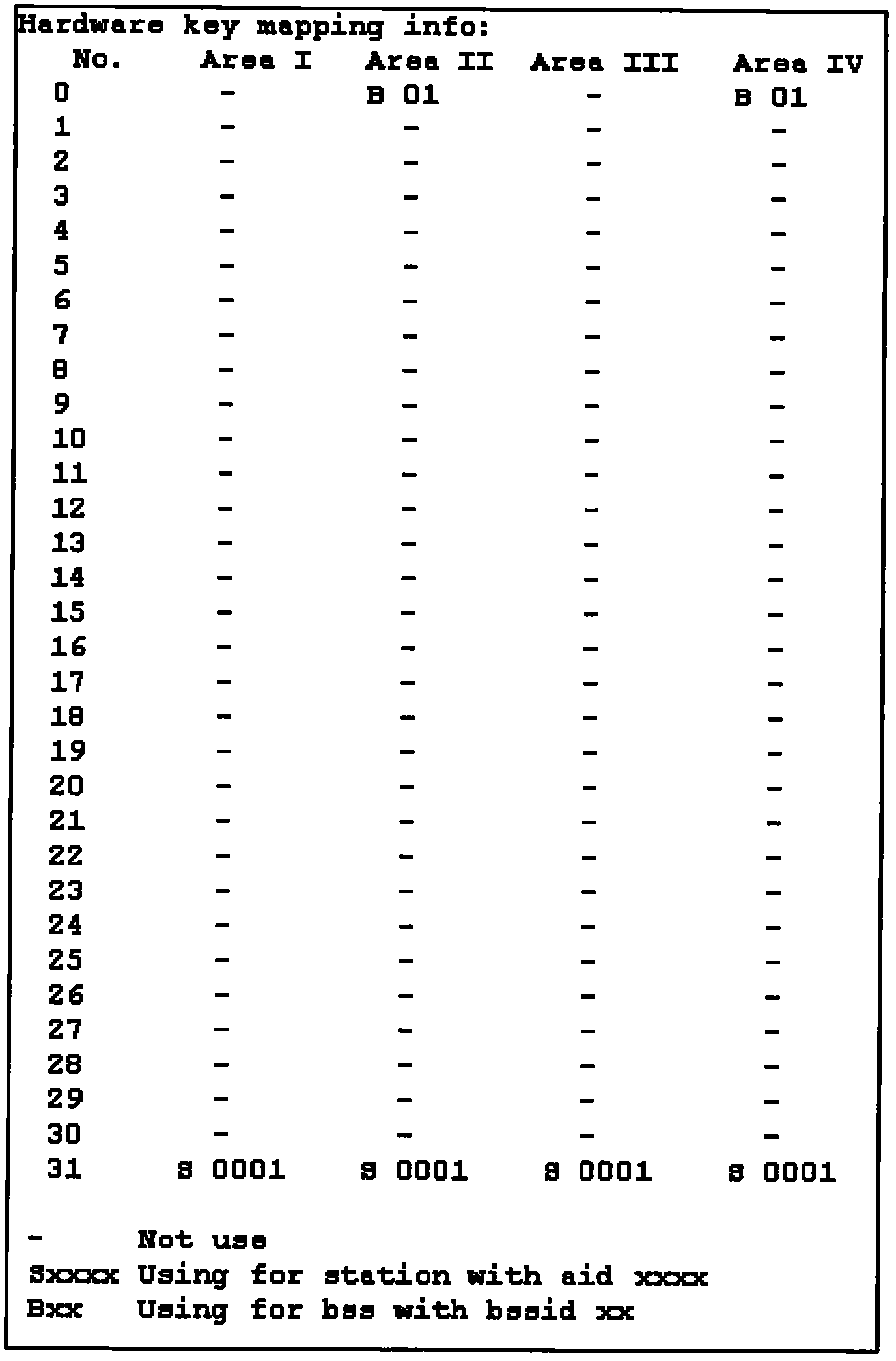
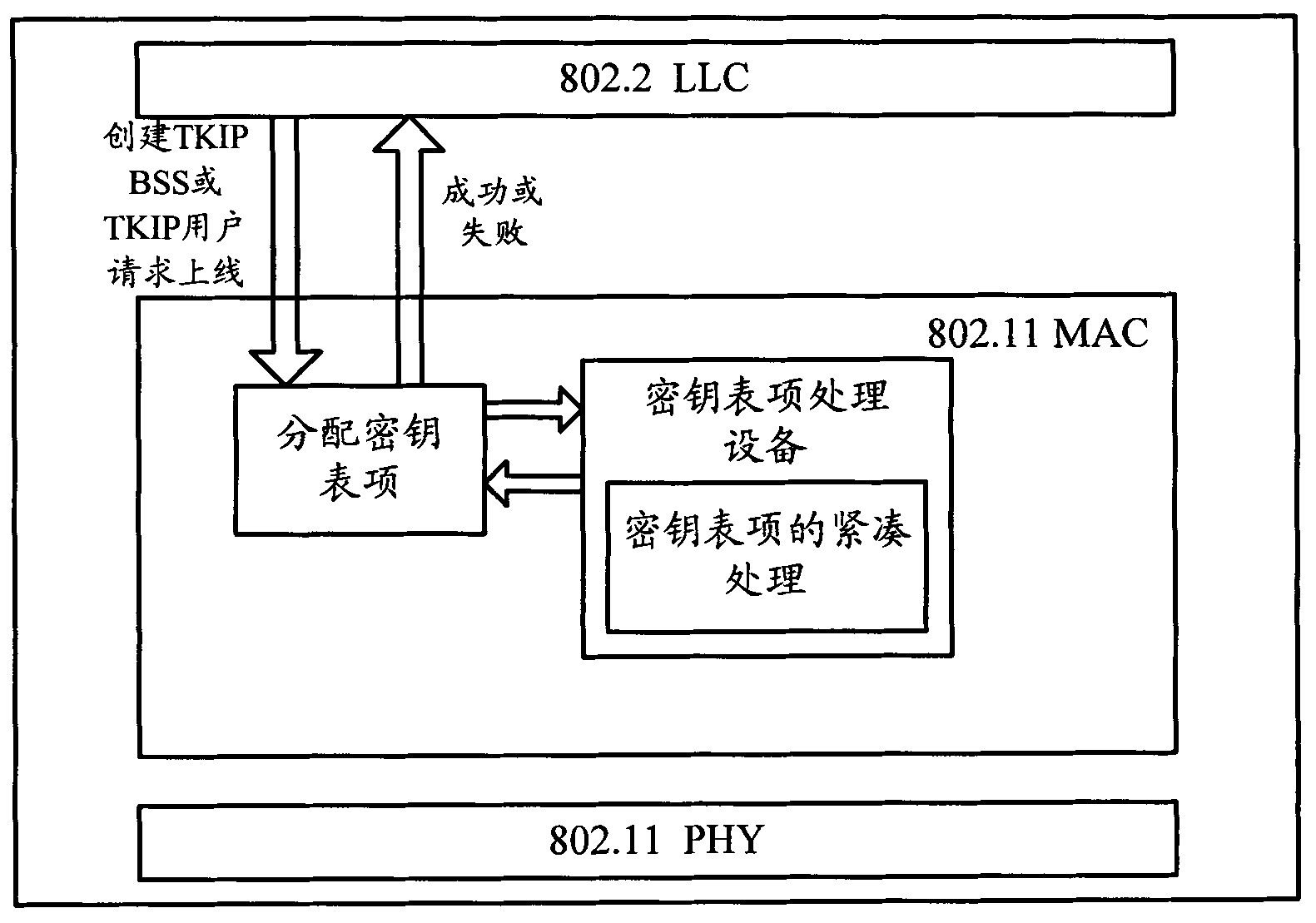
[0086] When multiple encrypted access methods are configured on the wireless service, and there are many online users and created BSSs, users frequently go online and offline, and BSSs are frequently created and deleted, some idle data will be generated in the hardware key table entries of the WMAC chip. The key is "empty", so that although the total number of idle key entries is sufficient, the distribution of idle key entries does not meet the requirements for the use of TKIP unicast or TKIP multicast keys and cannot be used by TKIP unicast and TKIP multicast keys. Multicast key to use.
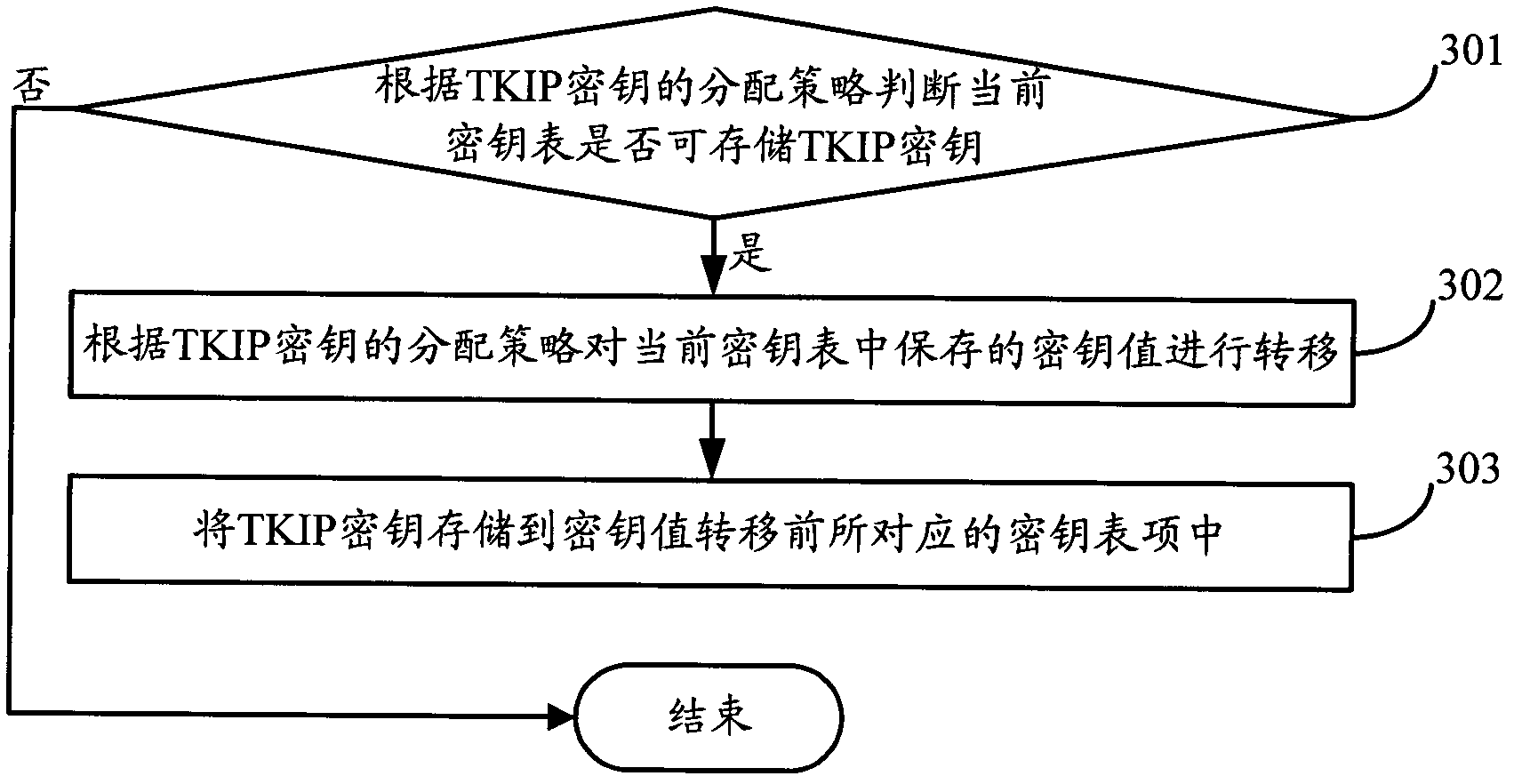
[0087] In view of the above problems, the present invention provides a method and device for processing key table items, so that according to the distribution characteristics of TKIP unicast or multicast keys, the idle key table items are arranged to meet the requirements of TKIP by moving the key table items. Unicast or TKIP multicast key distribution requirements, so that more TKIP users ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com