Method and system for detecting vulnerabilities of IP multimedia subsystem
A multimedia subsystem and vulnerability detection technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of increased security vulnerabilities, signaling integrity, confidentiality, usability and authenticity, and the quality of developers. Unevenness and other problems, to achieve the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
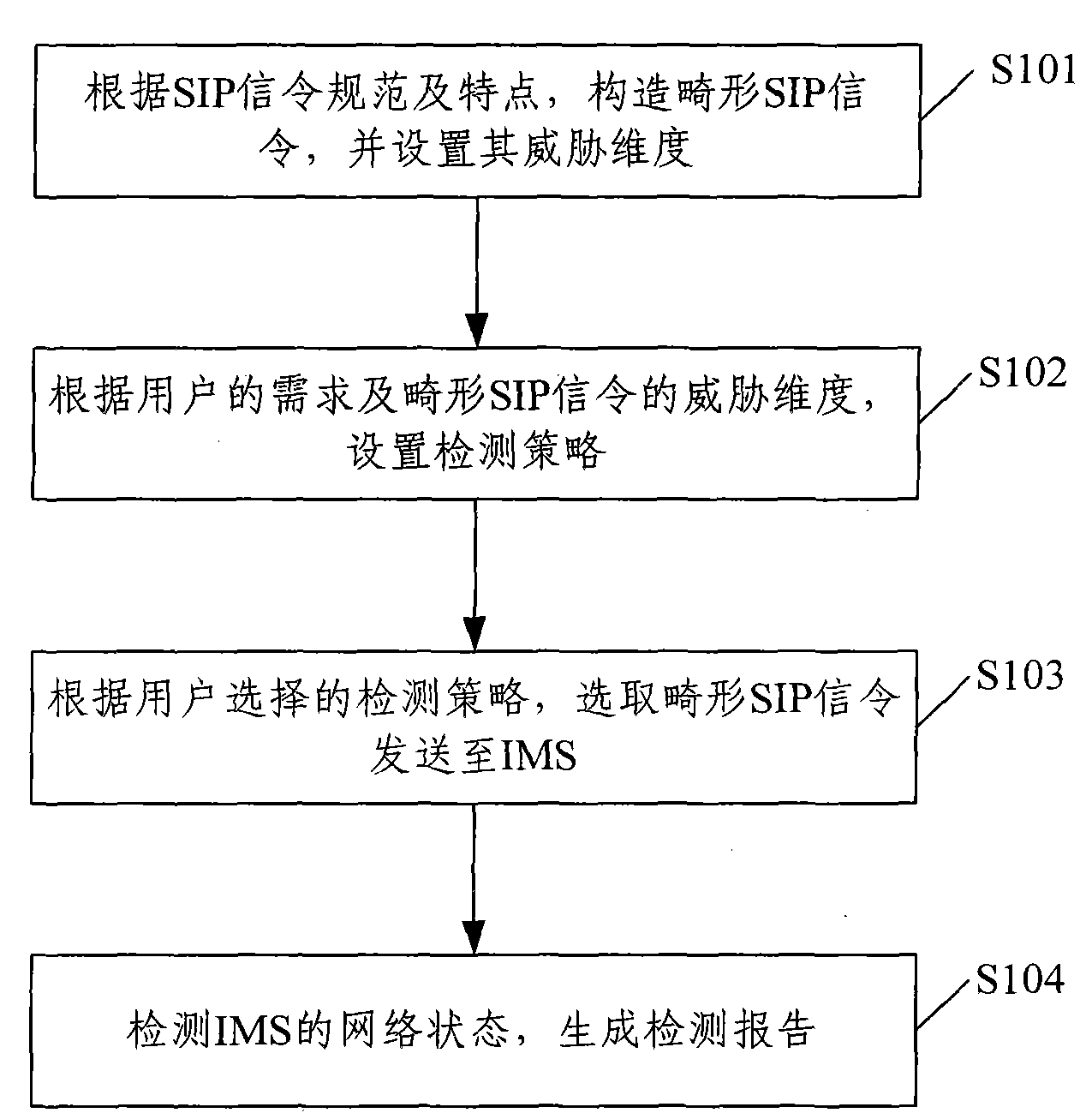
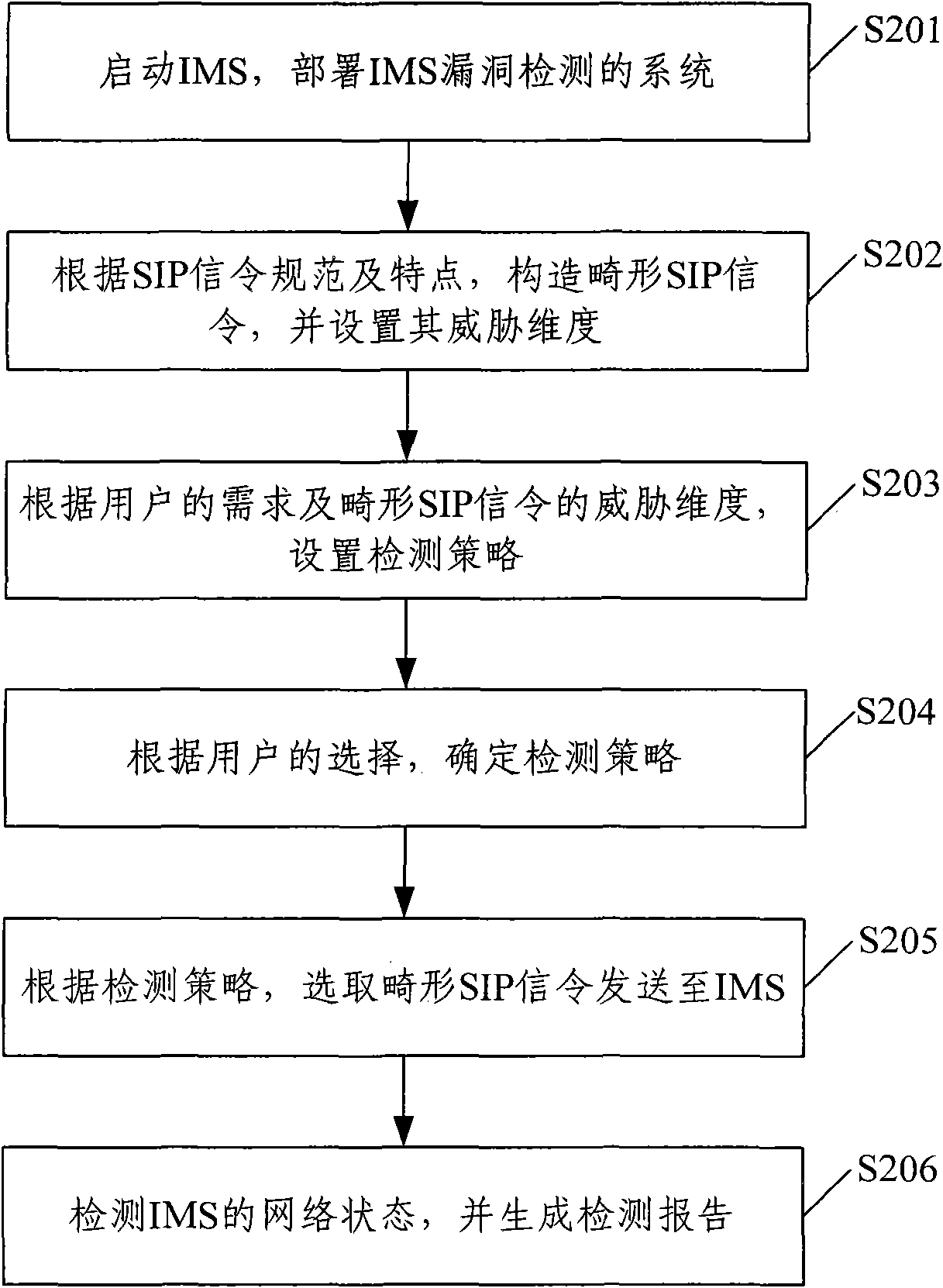
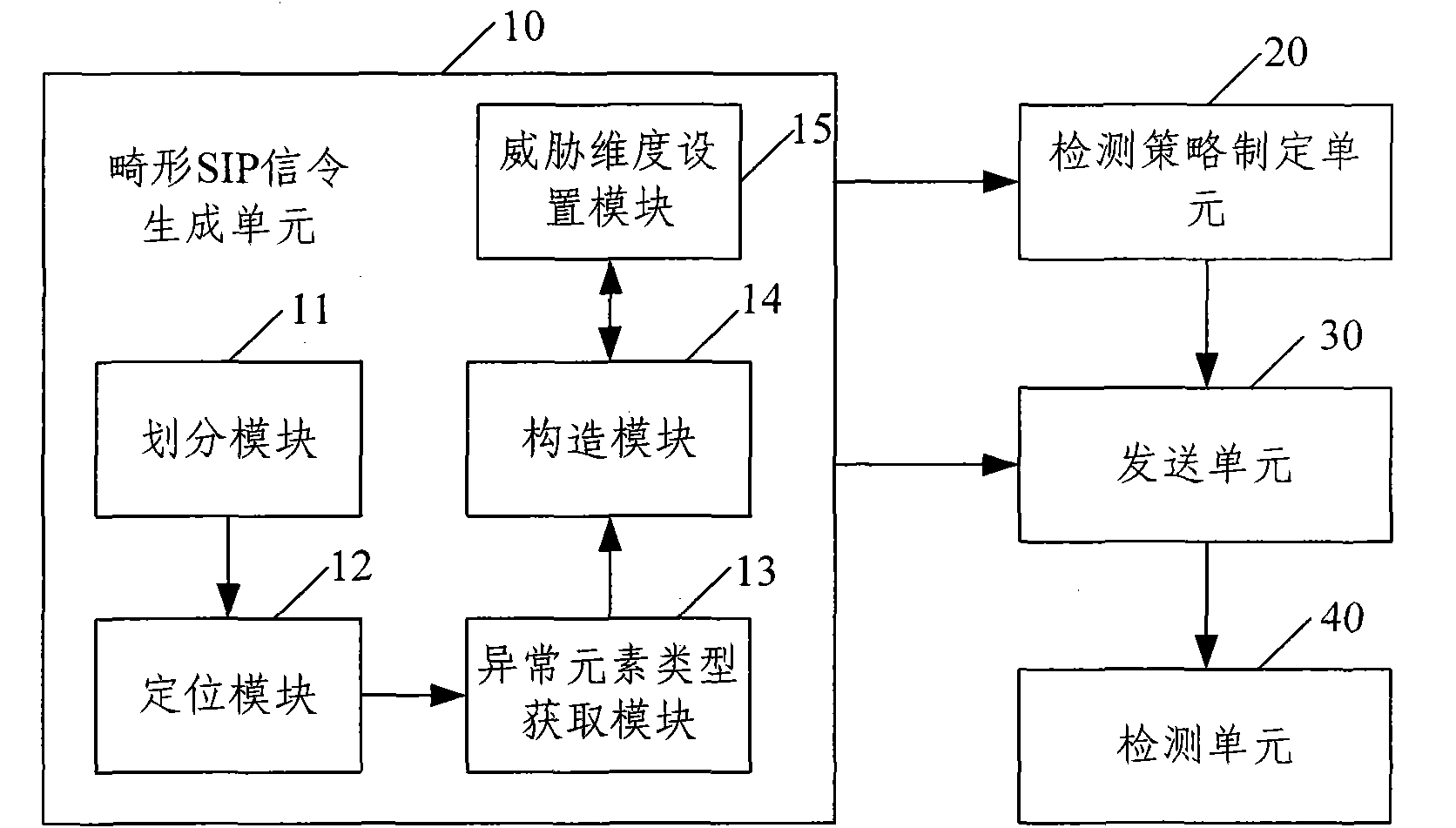
[0048] The basic idea of the present invention is: construct the malformed SIP signaling of IMS according to the SIP signaling specification and characteristics, and set the threat dimension and detection strategy of the malformed SIP signaling, and select according to the detection strategy selected by the user and the threat dimension of the malformed SIP signaling The malformed SIP signaling is sent to the IMS. After the transmission is completed, the network status of the IMS is detected and a detection report is generated to realize the vulnerability detection of the IMS.
[0049] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail by citing the following embodiments and referring to the accompanying drawings.
[0050] figure 1 Shows the implementation flow of the IMS vulnerability detection method of the present invention, as figure 1 Shown, the method that the prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com