Vulnerability detection method and system
A vulnerability detection and to-be-detected technology, applied in the field of vulnerability detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
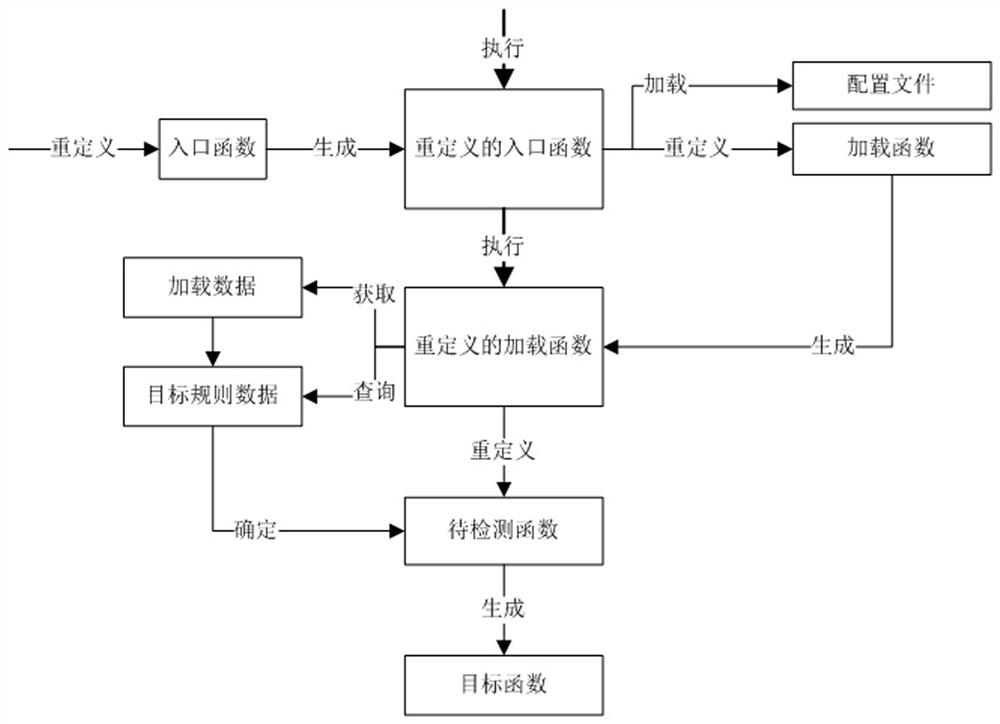
[0071] Embodiment 1. A method for detecting vulnerabilities, which is used to detect vulnerabilities in node.JS applications, comprising the following steps:
[0072] S100, start-up phase:
[0073] Weave agent vulnerability detection logic code into the application to be detected;
[0074] The agent vulnerability detection logic code includes the first logic code, the second logic code and the detection code, wherein the detection code is used for vulnerability detection, refer to figure 1 , the specific weaving method includes the following steps:
[0075] S110. Weaving into the first logic code:
[0076] S111. Add a plug-in startup parameter when the application to be detected is started, and load an agent tool;
[0077] The plug-in startup parameter is used to indicate that the application to be detected starts with a plug-in;
[0078] The agent tool is an agent tool.
[0079] S112. The agent tool redefines the entry function of the application to be detected;
[0080...
Embodiment 2
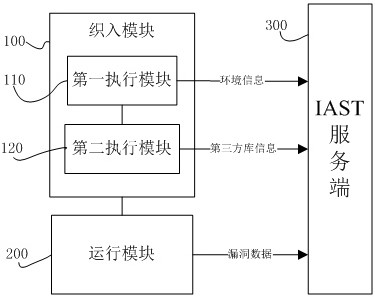
[0121] Embodiment 2, a kind of vulnerability detection system, is used for carrying out vulnerability detection to node.JS application, and it comprises Agent end and IAST service end 300, such as figure 2As shown, the Agent side includes:
[0122] Weaving module 100, for weaving detection code in the application to be detected;
[0123] The running module 200 is configured to run the application to be detected woven with the detection code, and generate corresponding vulnerability data when the detection code is executed.
[0124] The weaving module 100 includes a first execution module 110 and a second execution module 120:
[0125] The first execution module 110 is configured to load a configuration file, the configuration file includes several pieces of rule data mapped with a third-party library;
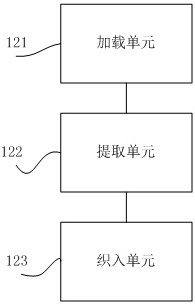
[0126] refer to image 3 , the second execution module 120 includes:
[0127] A loading unit 121, configured to acquire loading data, the loading data is used to indicate ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com