Device and method for implementing AES encryption and decryption
An encryption and decryption technology to be encrypted, applied in the field of encryption and decryption, it can solve the problems of inability to realize resource sharing and huge hardware overhead, and achieve the effect of reducing scale and saving hardware resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
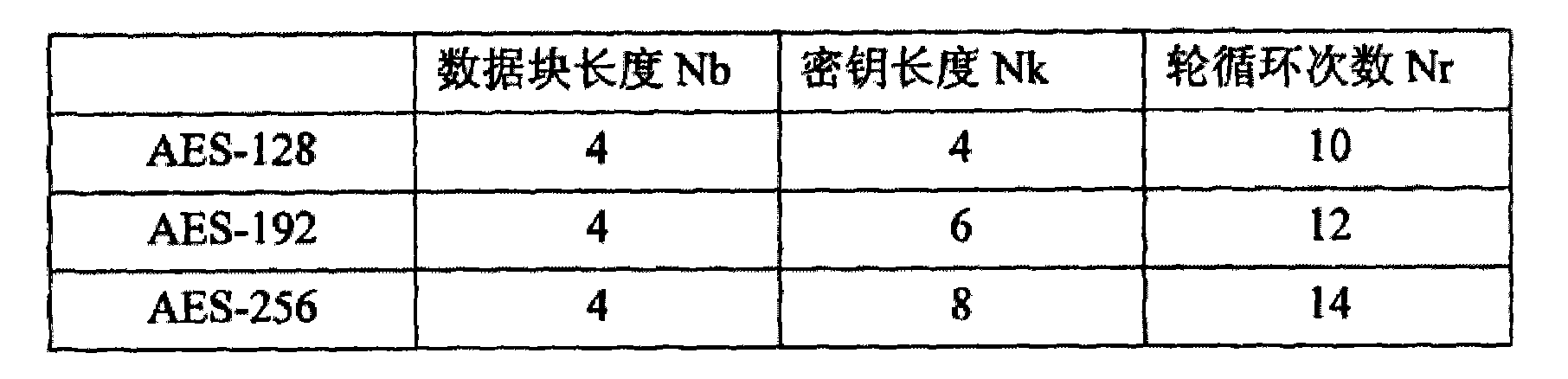
[0028] The Rijndael algorithm is a block encryption algorithm with variable block length and variable key length. The block length and key length can be independently set to any integer multiple of 32 bits, and the minimum value is 128 bits. The maximum value is 256 bits, that is, both the data length and the key length can be 128 bits, 192 bits and 256 bits.
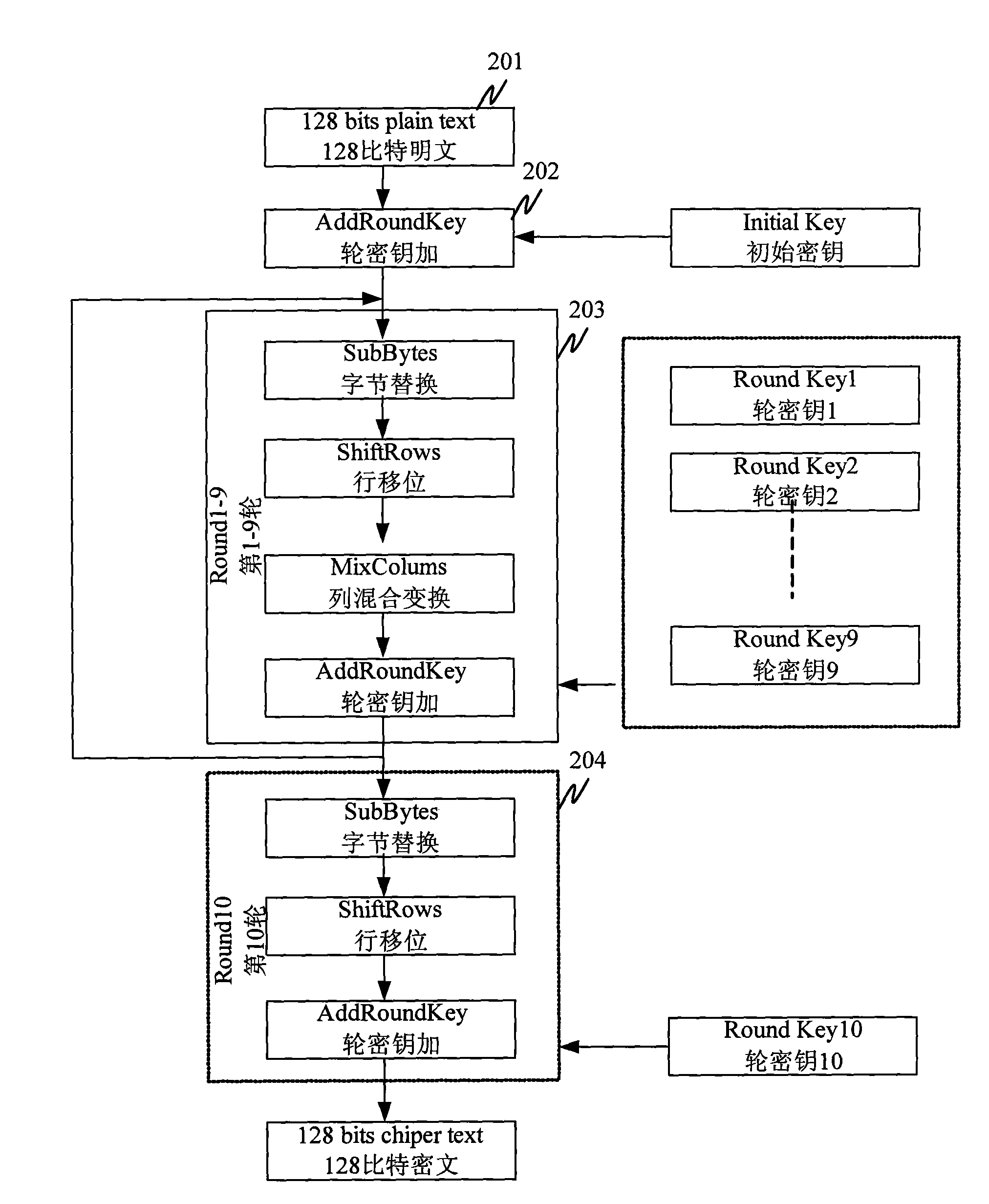
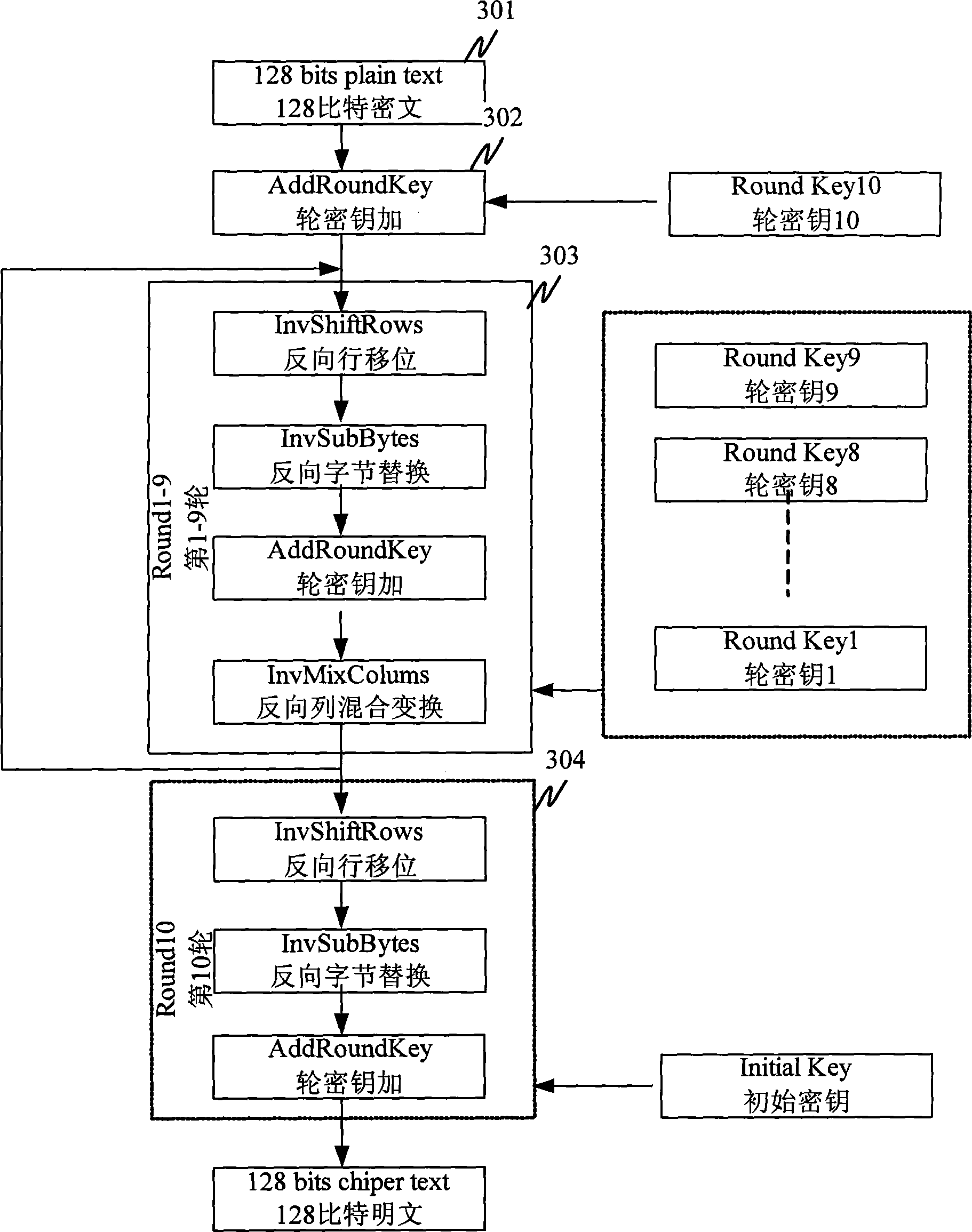
[0029] AES is actually a special case of Rijndael. In its specification standard, it is clearly defined that the data packet length is fixed at 128 bits, and the key length can be 128 bits, 192 bits or 256 bits, which are called "AES-128", " AES-192" and "AES-256". The present invention is described by taking "AES-128" as an example.
[0030] The input and output of AES can be regarded as a one-dimensional array in bytes. The intermediate value obtained by data processing in the pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com