Distributed denial of service (DDOS) attack protection method, device and system for cloud computing system
A distributed denial and cloud system technology, applied in the computer field, can solve problems such as inapplicable DDOS attacks, achieve the effect of improving security and reliability, and protecting against DDOS attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] An embodiment of the cloud system distributed denial of service attack protection method of the present invention may include: the protection node in the cloud computing system monitors the data flow injected into the virtual machine; if it detects that the data flow injected into the virtual machine is abnormal, extract the For the data stream of the virtual machine, the extracted data stream is sent to the traffic cleaning device for traffic cleaning; the data stream after the traffic cleaning is received by the traffic cleaning device; and the cleaned data stream is injected into the virtual machine.
[0057] see image 3 , the specific steps may include:
[0058] 310. The protection node in the cloud computing system monitors the data flow injected into the virtual machine;
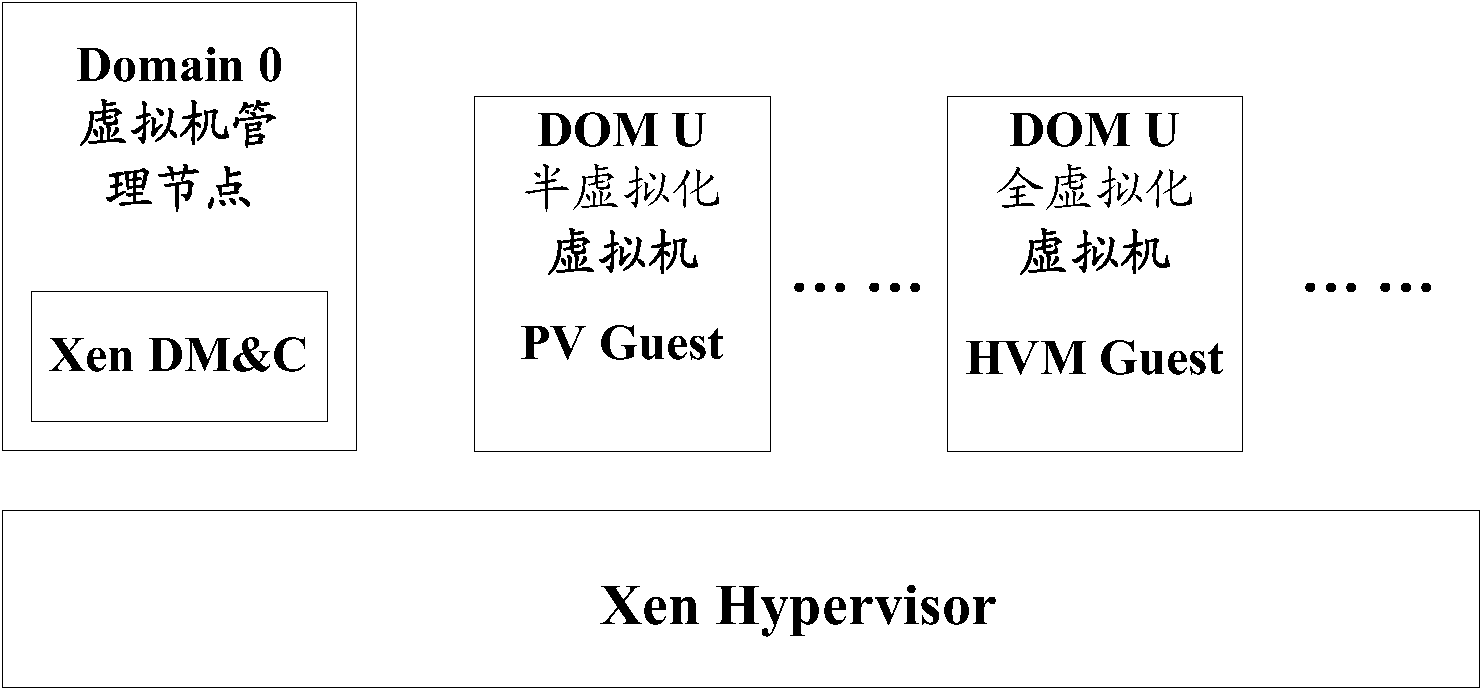
[0059] Wherein, the cloud computing system includes a guard node and a plurality of virtual machines, and the data flows exchanged between each virtual machine pass through the guard node.
...
Embodiment 2
[0071] In order to better understand the technical solutions of the embodiments of the present invention, the process of DDOS attack protection of a virtual machine Ai in the cloud computing system by the virtual machine management node in the cloud computing system is taken as an example to describe in more detail below.
[0072] see Figure 4 , which can include:
[0073] 401. The virtual machine management node in the cloud computing system monitors the data flow injected into the virtual machine Ai;
[0074] In one application scenario, the virtual machine management node in the cloud computing system can manage one or more virtual machines (including the virtual machine Ai) located on the same or different physical hosts in the cloud computing system.
[0075] The data traffic between the external network and the virtual machines in the cloud computing system, and the data traffic between the virtual machines in the cloud computing system pass through the virtual machine...
Embodiment 3
[0099] Referring to Fig. 5 , a protection node 500 in a cloud computing system provided by an embodiment of the present invention, wherein the cloud computing system includes a protection node and a plurality of virtual machines, and the data flow interacted between each virtual machine passes through the protection node, and the cloud computing system The internal protection node 500 may specifically include: a monitoring module 510 , an extracting and sending module 520 , a receiving module 530 and an injecting module 540 .
[0100] Wherein, the monitoring module 510 is used to monitor the data flow injected into the virtual machine;
[0101] In one application scenario, the protection node 500 in the cloud computing system can be a virtual machine management node in the cloud computing system (the virtual machine management node in the cloud computing system can manage one or more physical The virtual machine on the host computer) may also be a device deployed between the v...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap