Permission configuring method, device and system
A permission configuration and permission technology, applied in the field of network communication, can solve problems such as hidden dangers of UPnP device management security, and achieve the effect of improving management security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
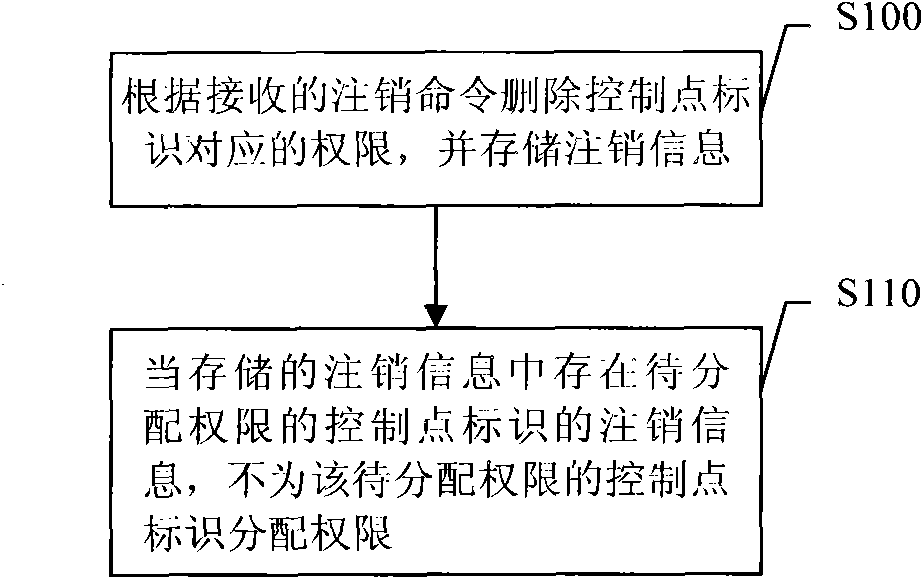
[0037] Embodiment 1, a rights configuration method. The flow of the method is attached figure 1 shown.
[0038] figure 1 , S100. Delete the authority corresponding to the control point identifier according to the received logout command, and store the logout information of the control point identifier. Storing the logout information identified by the control point means adding the logout information identified by the control point to the stored logout information. Before the logout information identified by the control point is added to the stored logout information, the stored logout information may be empty, or may contain logout information identified by other control points.
[0039] The logout command in S100 may be sent by the control point. Moreover, the control point identifier may be a self-signed certificate generated by the control point corresponding to the identifier, or may be a value obtained by calculating the self-signed certificate using a predetermined a...
Embodiment 2
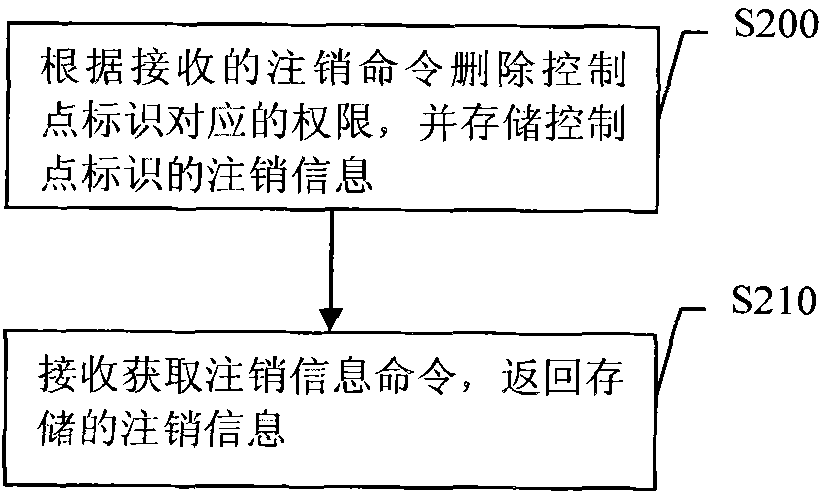
[0056] Embodiment 2, a rights configuration method. The flow of the method is attached figure 2 shown.
[0057] figure 2 In S200, delete the authority corresponding to the control point identifier according to the received logout command, and store the logout information of the control point identifier. The control point identifier here may be referred to as a control point identifier to be canceled. Storing the logout information identified by the control point means adding the logout information identified by the control point to the stored logout information. Before the logout information identified by the control point is added to the stored logout information, the stored logout information may be empty, or may contain logout information identified by other control points.
[0058] A specific example of S200 is: the logout command carries information to be logged out and verification information, and the stored logout message includes the information to be logged out...
Embodiment 3
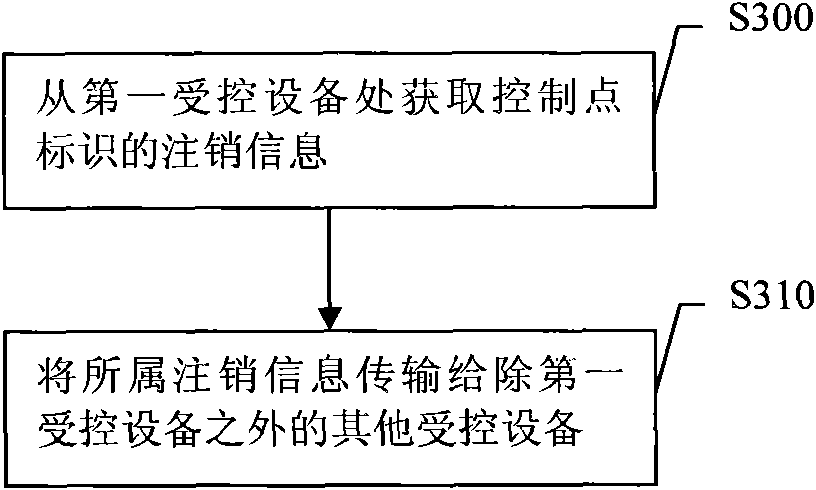
[0067] Embodiment 3, a rights configuration method. The following describes this embodiment by taking the execution subject as a control point as an example. The flow of the method is attached image 3 shown.
[0068] image 3 In S300, the control point acquires logout information of the control point identifier from the first controlled device. The cancellation information includes information to be canceled and verification information, and the verification information may include signature information of the information to be canceled.
[0069] A specific example for the control point to obtain the logout information identified by the control point from the first controlled device is: the control point sends a command to obtain logout information to the first controlled device, and after the first controlled device receives the command to obtain logout information, Obtain the logout information of the control point from the stored information, and return the logout info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com