Key exporting method for non key system entry and start of automobile
A technology for keyless entry and start system, which is applied in the field of keyless entry and start system key derivation of automobiles, can solve problems such as hidden dangers of PEPS system security, and achieve the effect of improving management security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
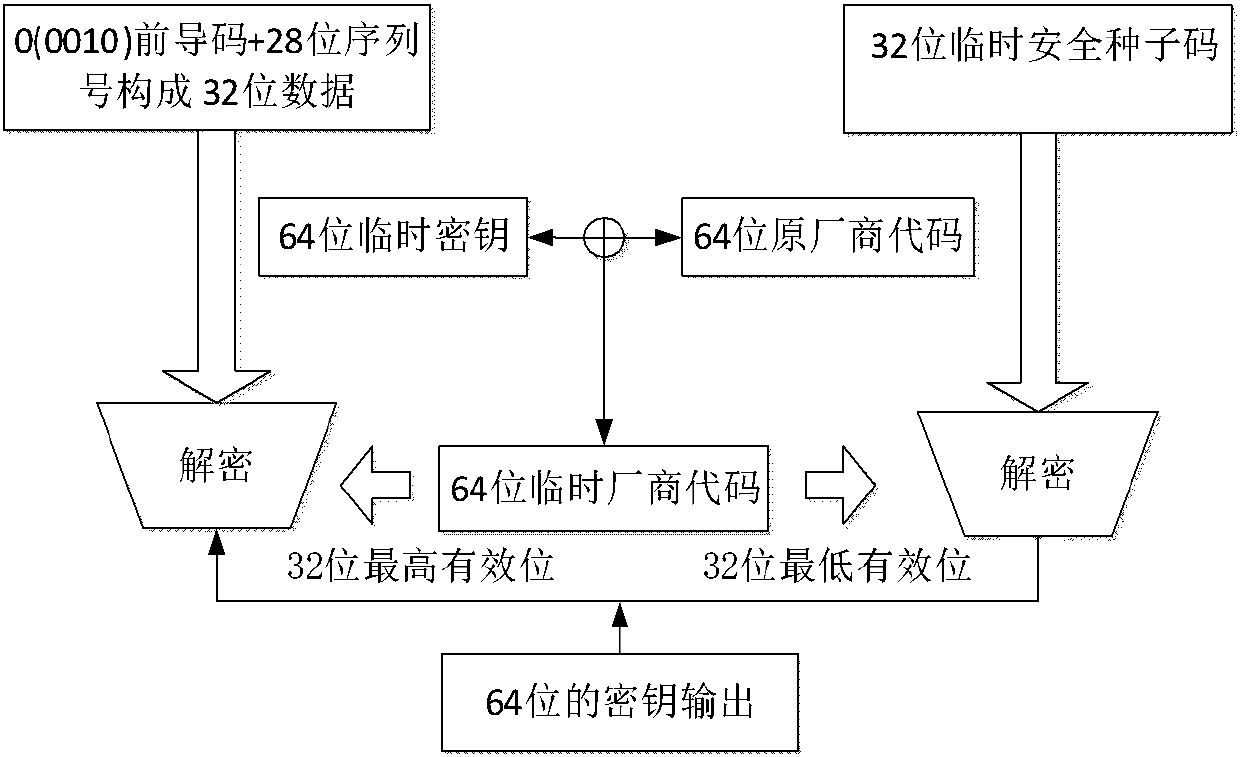
[0024] (1) Key negotiation process:
[0025] ① The on-board side uses the counter function of the single-chip microcomputer to generate x. After the single operation is completed, the counter of the single-chip microcomputer keeps counting, and stops when the outside world operates it again or sends data;
[0026] ②The vehicle terminal sends two large random numbers signed with the vehicle terminal private key (pk_S) to the key terminal and At the same time, a timestamp (Time) is added to the signature of the message to avoid replay attacks;
[0027] ③ After the key terminal receives the information, use the public key of the vehicle terminal to verify the validity of the information. If it is legal, proceed to step ④, otherwise, the identity authentication will not be passed and repeat step ②;
[0028] ④ The key end generates two large random numbers and The generation method of y is the same as that of x, and then generate a 64-bit temporary key (Tempkey) equal to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com