Multi-domain security management method for network management system
The technology of a network management system and management method is applied in the field of SDH/MSTP/PTN transmission network to achieve the effect of reducing maintenance work time and reducing work time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
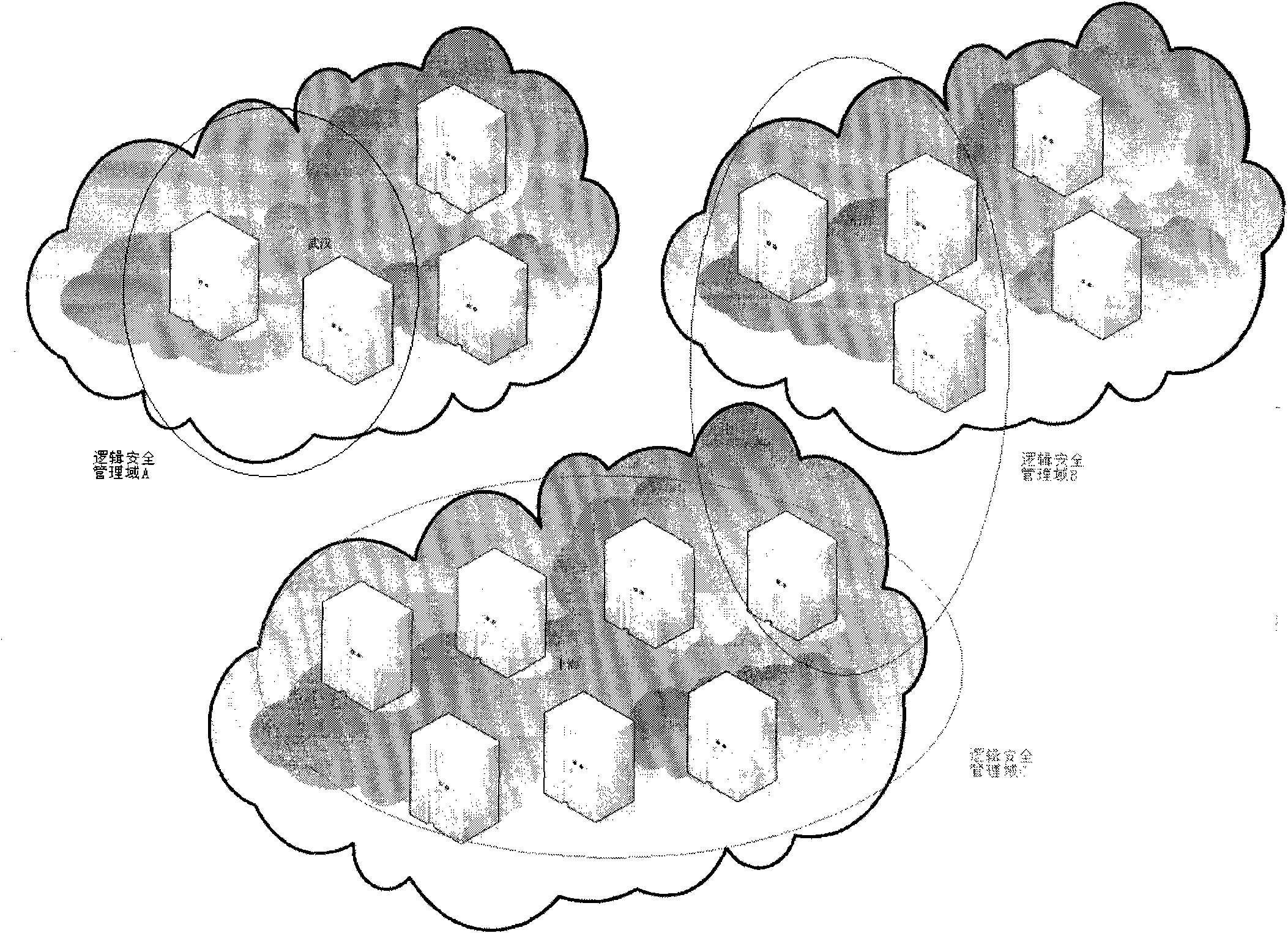
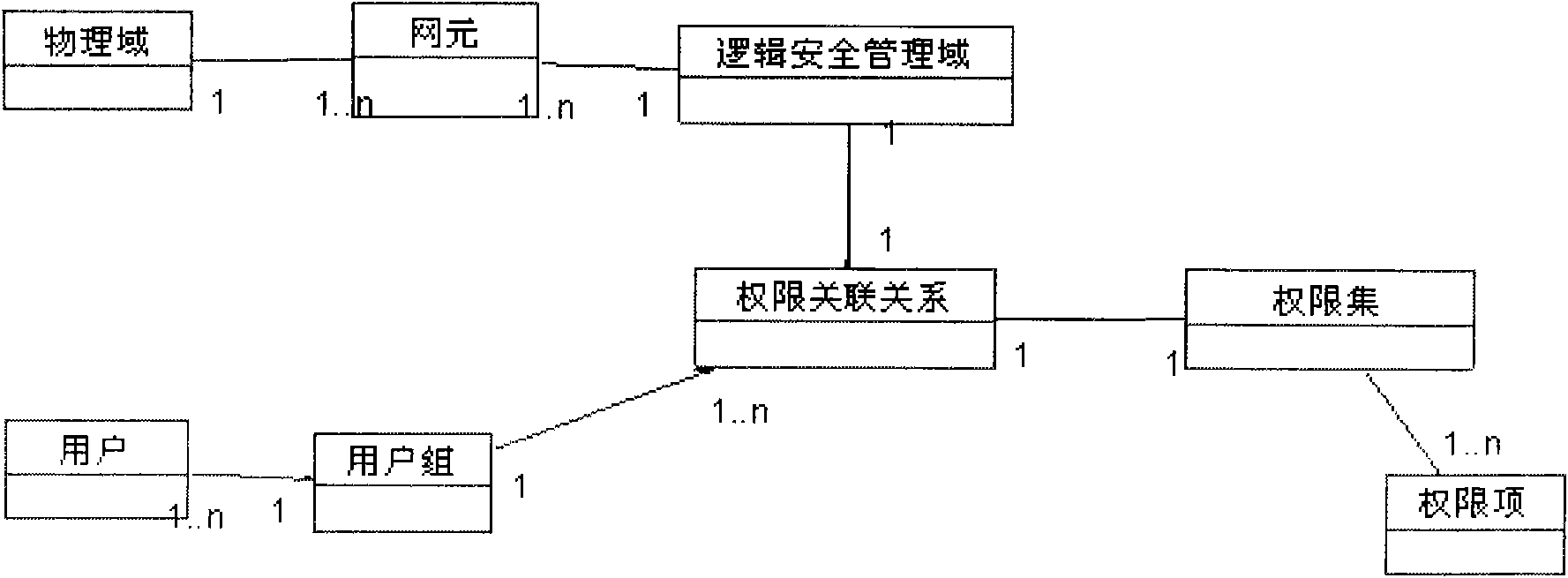
[0037] Example: logical domain = {NE 1, NE 24, ...}
[0038] 4. User: real user.
[0039] 5. User group: A group of users with the same logical security management domain and the same authority.
[0040] Example: Usergroup = {administrators, system operators, ...}
[0041] By default, user groups include administrator user group, operator user group, observer user group, etc., and users can also customize user groups.
[0042] 6. Permission item: a collection of operation permissions, which can be configured according to the granularity of functions.
[0043] Example: NE operation permission item = {create NE, delete NE, modify NE, ...}
[0044] 7. Permission set: a collection of functional permission items assigned to users.
[0045] Example: administrator operation permission set = {network element operation permission item, business operation permission item, ...}
[0046] Among them, the operation item is customized by the system, and the operation item is a collectio...
Embodiment
[0065] In order to provide a network management rights management method, the method solves the domain-specific rights control problem in the network management system, and flexibly assigns different rights of different management domains to users.
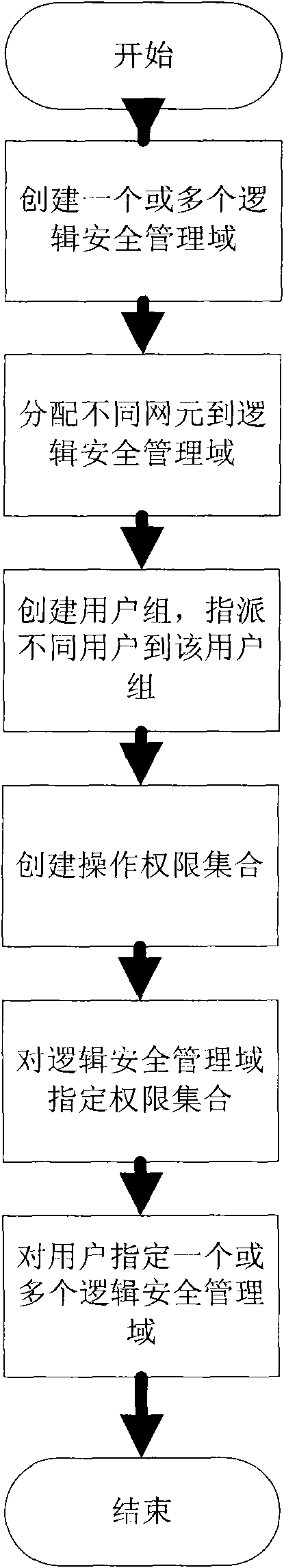
[0066]The normal flow process of the present invention is as follows:
[0067] Step 1: Create a logical security domain.
[0068] Step 2: Assign network elements to logical security domains.
[0069] Step 3: Create a collection of operation permissions.
[0070] Step 4: Formulate a permission set for the virtual domain.
[0071] Step 5: Specify the virtual domain and permission set for the user.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com