Group-based authentication method of machine type communication (MTC) devices
A technology of machine-type communication and authentication method, which is applied in the Internet of Things scenario and the authentication field of communication equipment, which can solve problems such as link congestion and signaling data increase, so as to reduce congestion, prevent illegal access, and optimize signaling data Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
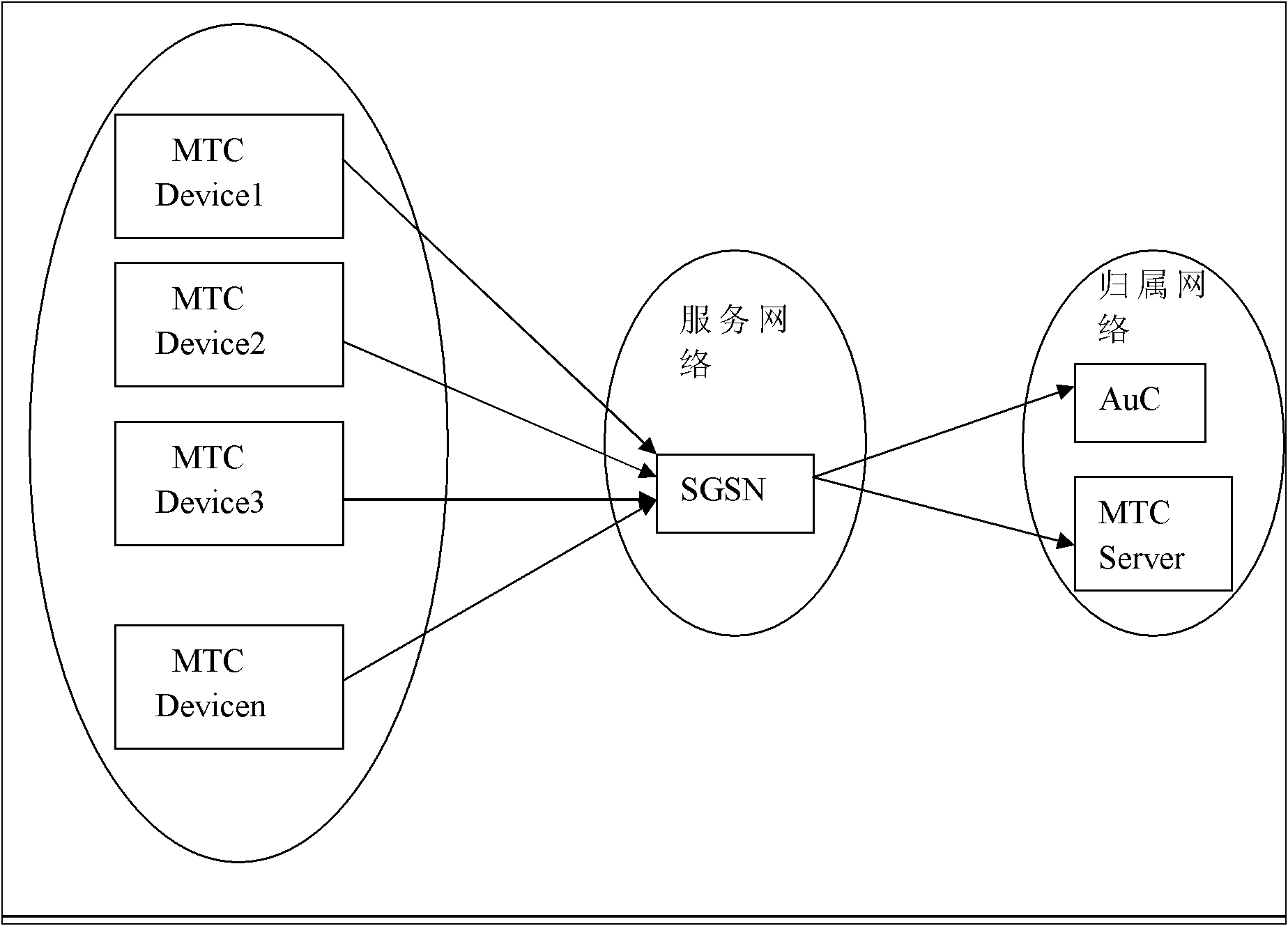
[0021] This method adopts a group-based authentication method for machine-type communication devices, and the network structure diagram is as follows figure 1 shown.
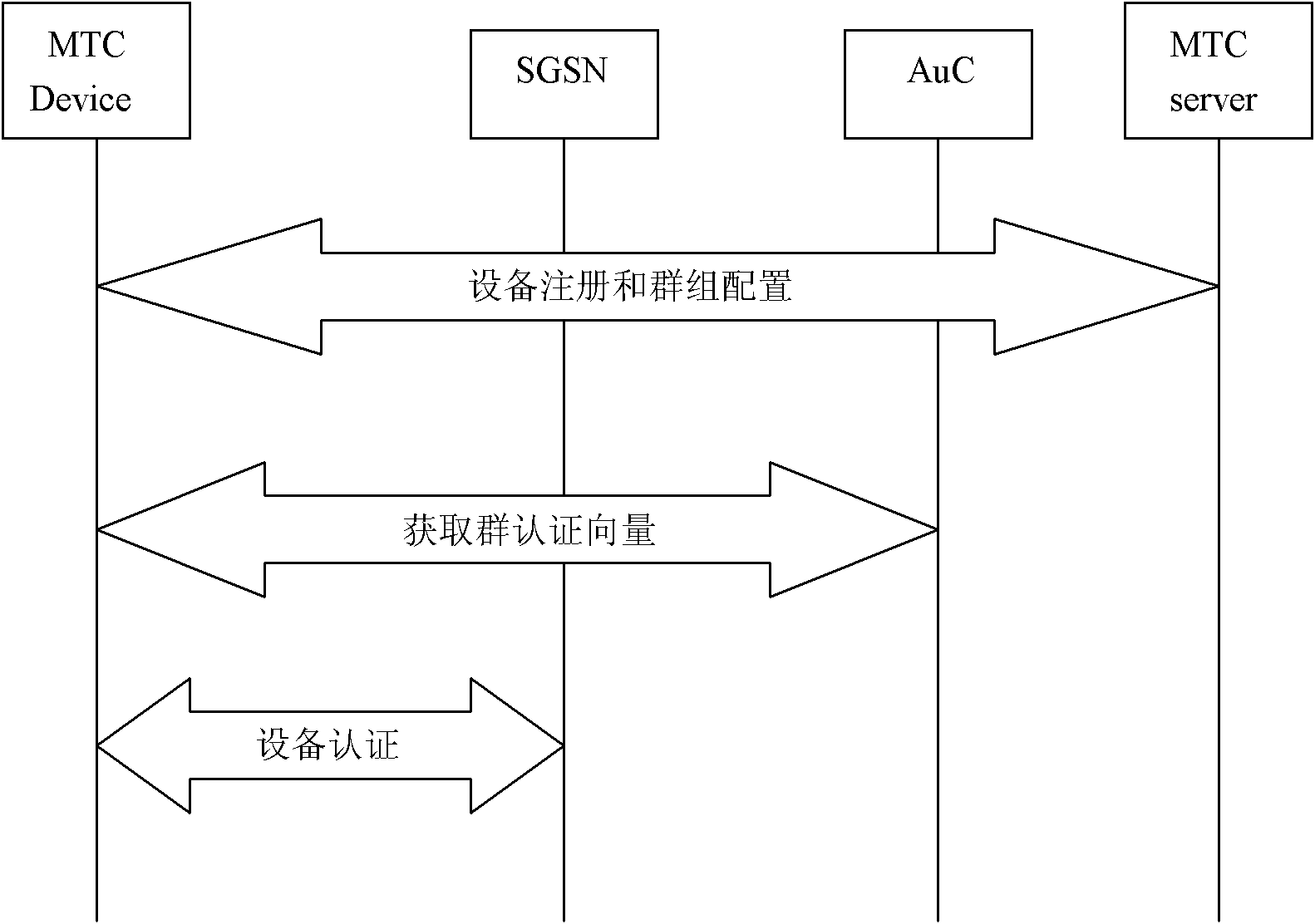
[0022] refer to figure 2 , the present invention is based on the authentication of the group-based machine type communication device, comprising the following steps:
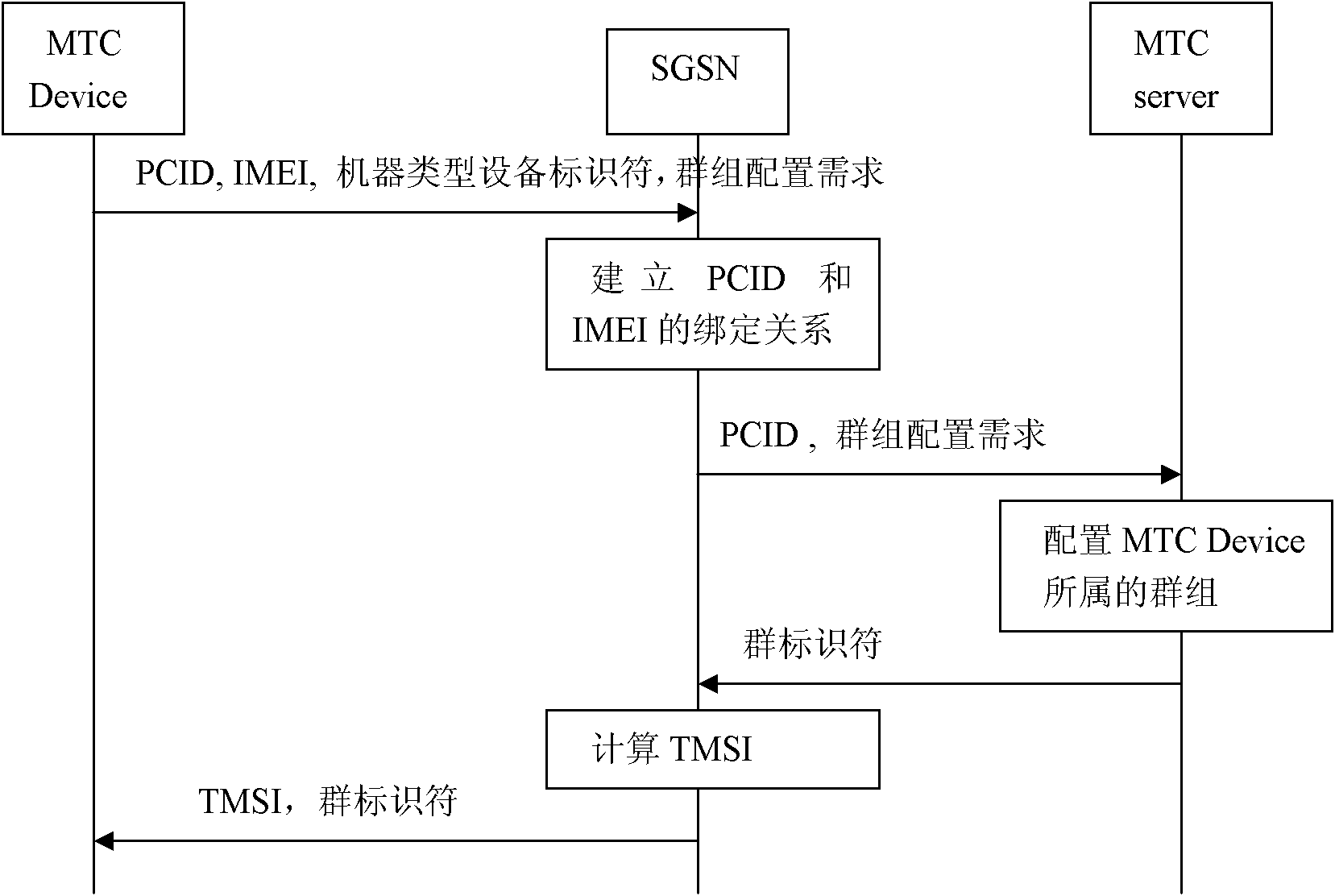
[0023] Step 1, registration and group configuration of MTC devices.
[0024] Such as image 3 As shown, the specific implementation of this step is as follows:
[0025] (1.1) When leaving the factory, the equipment manufacturer saves the same permanent key K in the machine-type communication equipment MTC Device and the authentication center AuC respectively;
[0026] (1.2) When leaving the factory, the device manufacturer sets the policy for MTC Device group configuration on the machine type communication device MTC Device and the machine type communication device server MTC Server respectively, and sets a same temporary connection identity ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com