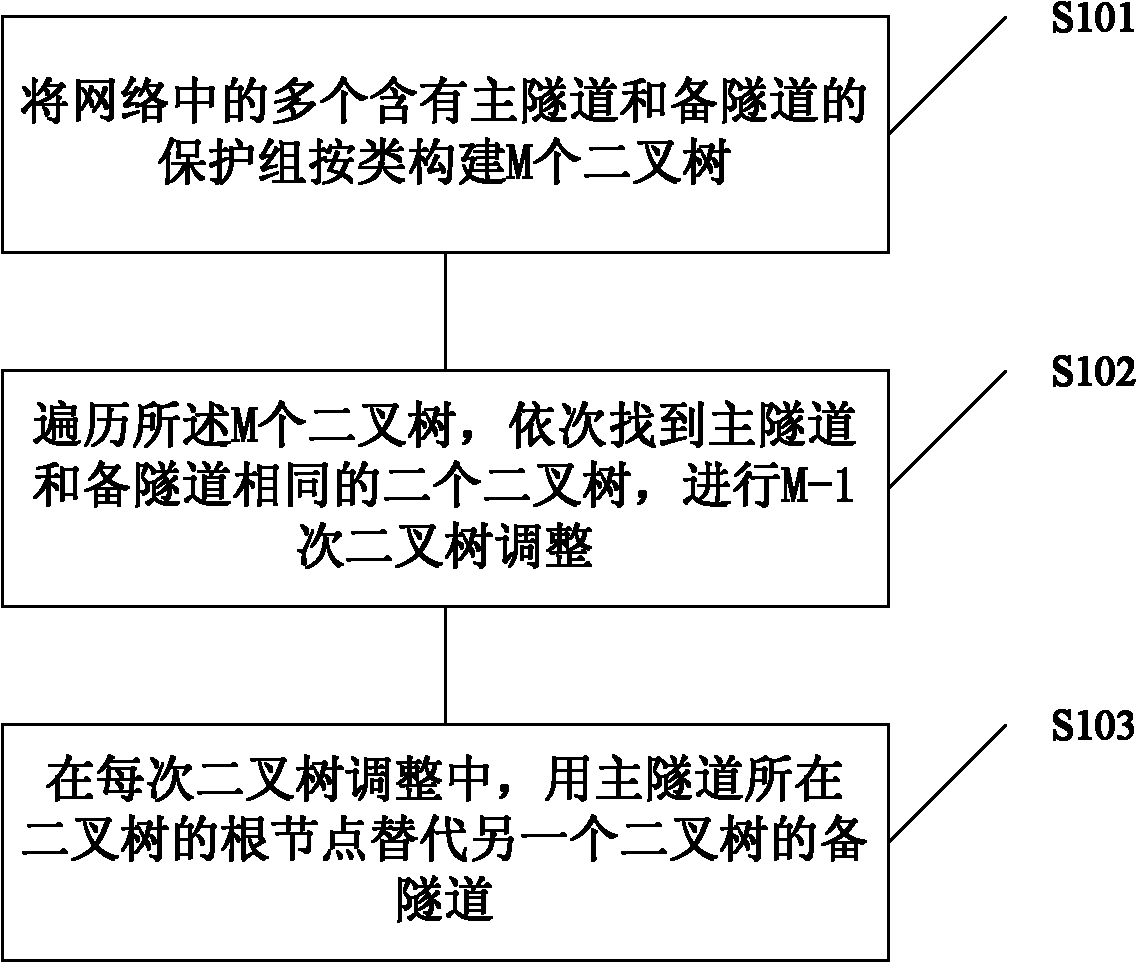
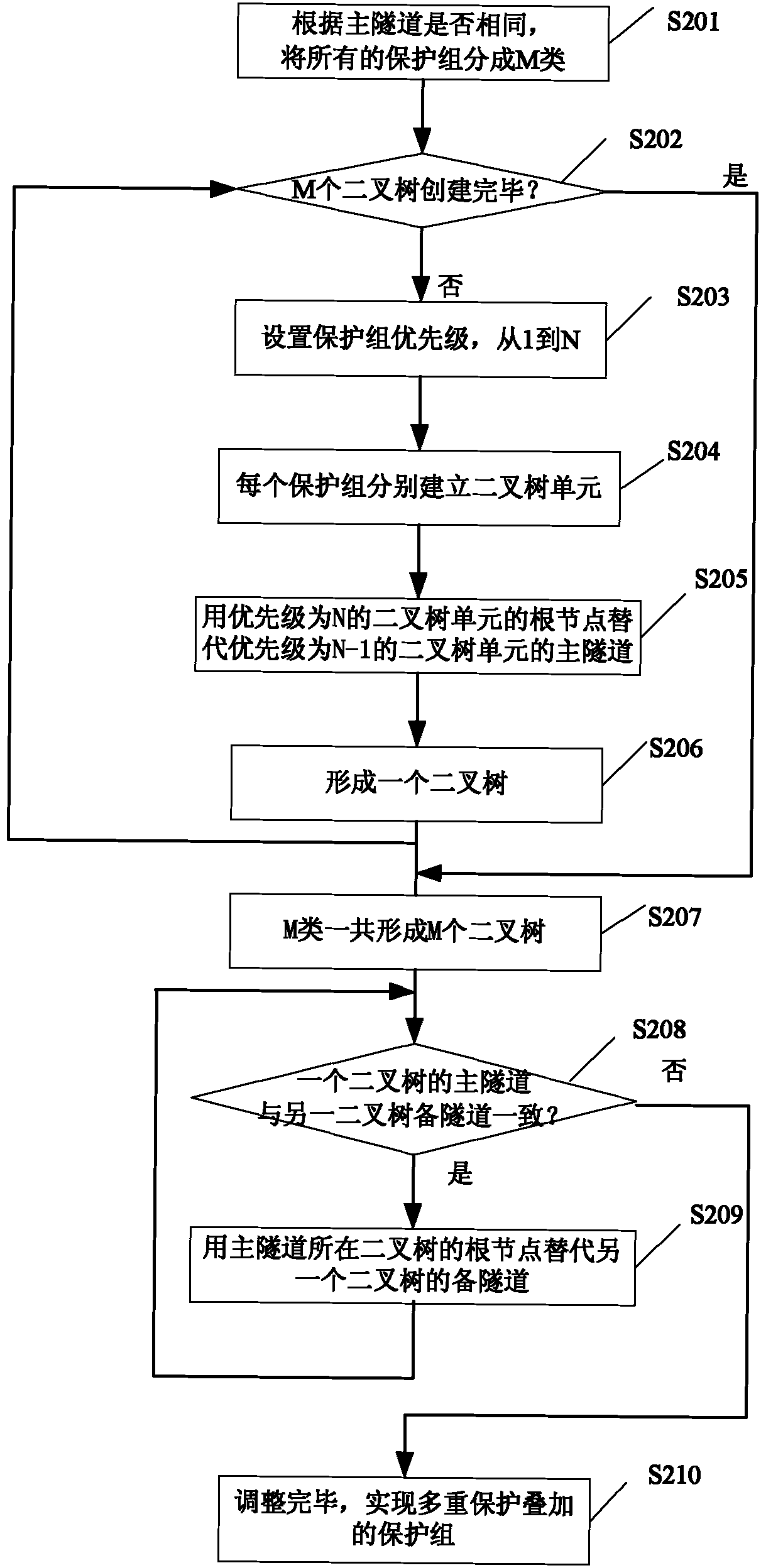
Multi-protection stacking protection group realization method and device
A technology of multiple protection and implementation methods, applied in the field of communication, to achieve the effect of timely service switching
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
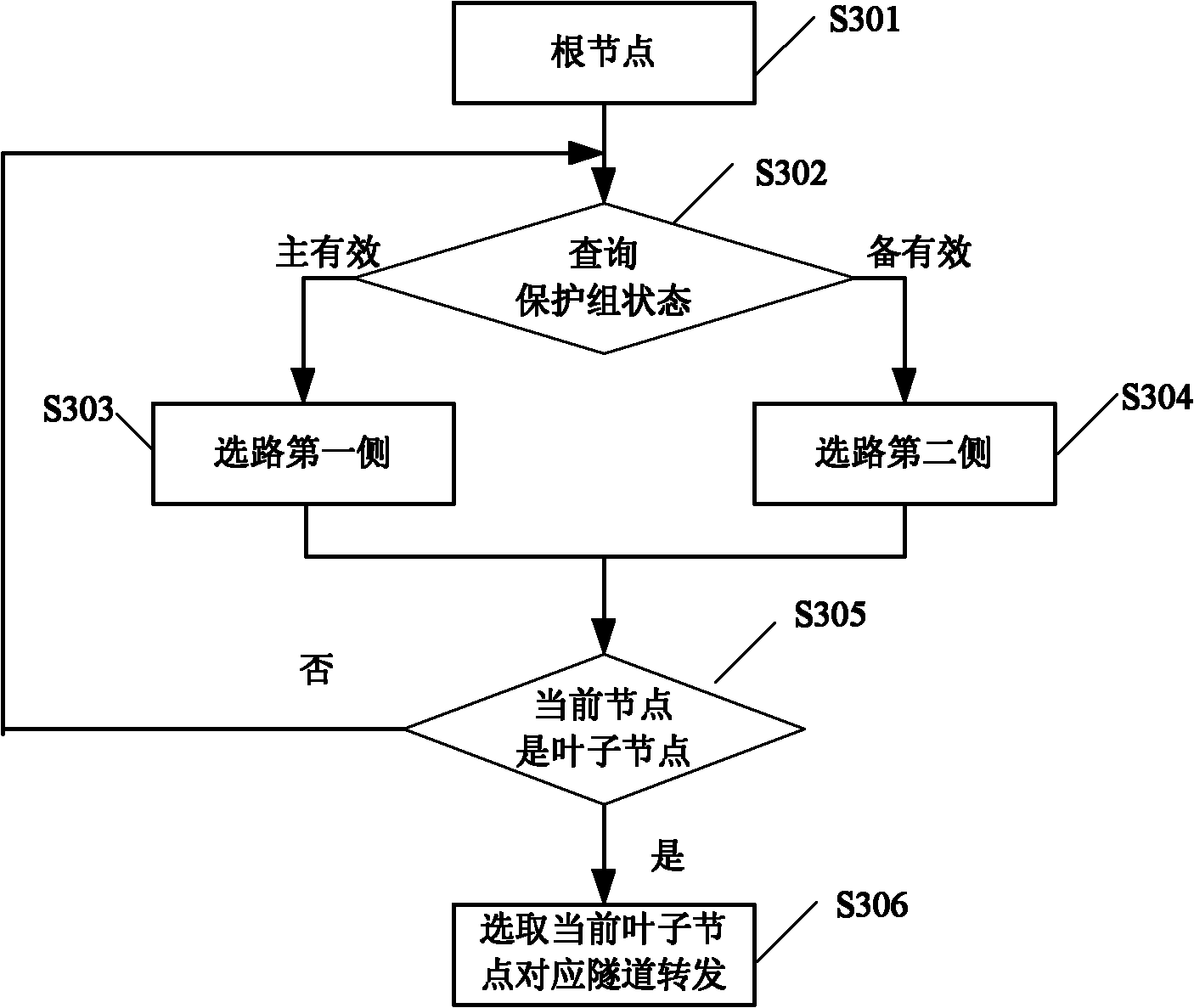
[0081] In the initial state, the leaf nodes are Tunnel 1, Tunnel 3, Tunnel 2, and Tunnel 4 from left to right. Up; for protection group 1, the status of tunnel 1 and tunnel 3 of all the leaf nodes on the first side is normal, so the status of protection group 1 is master.
[0082] From the root node protection group 1 downwards, for protection group 1, the state is on the master, then select the route to go to the first side to reach protection group 2; for protection group 2, the state is on the master, continue to select the route and go to the first side, Arrives at leaf node Tunnel 1; so network traffic is on Tunnel 1.
example 2
[0084] When it is detected that tunnel 1 is invalid and tunnel 3, tunnel 2, and tunnel 4 are normal, for protection group 2, the state of tunnel 1 of the first-side leaf node is invalid, and the state of tunnel 3 of the second-side leaf node is normal, so the state of protection group 2 is Standby; for protection group 1, the first side includes leaf node tunnel 1 and tunnel 3, and the status of tunnel 3 is normal, so the status of protection group 1 is on the active side.
[0085] From the root node protection group 1 downwards, for protection group 1, the state is on the master, then choose the route to go to the first side to reach protection group 2; for protection group 2, the state is on the standby, then continue to choose the route to go to the second side , reaches the leaf node tunnel 3; so the network traffic is on tunnel 3.
example 3
[0087] When both tunnel 1 and tunnel 3 are invalid, and tunnel 2 and tunnel 4 are normal, for protection group 2, the state of tunnel 1 of the leaf node on the first side and tunnel 3 of the leaf node on the second side are both invalid, so the current state of protection group 2 is invalid; For protection group 1, the status of all leaf node tunnels 1 and 3 on the first side is invalid, and the status of leaf node tunnel 2 on the second side is normal, so protection group 1 is switched to the standby server; for protection group 3, the status of the leaf node tunnels on the first side 2 is normal, and the second-side leaf node tunnel 4 is normal, then the protection group 3 is switched to the backup.
[0088] From the root node downwards, for protection group 1, the state is on standby, then choose the route to go to the first side, to reach protection group 3, for protection group 3, the state is on the master, then continue to choose the first side, to reach the leaf node T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com