Hash table entry addition, deletion, search method and hash table storage device
A table entry and sub-table technology, applied in the field of communication, can solve the problems of space utilization reduction, occupation, unfavorable hardware implementation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
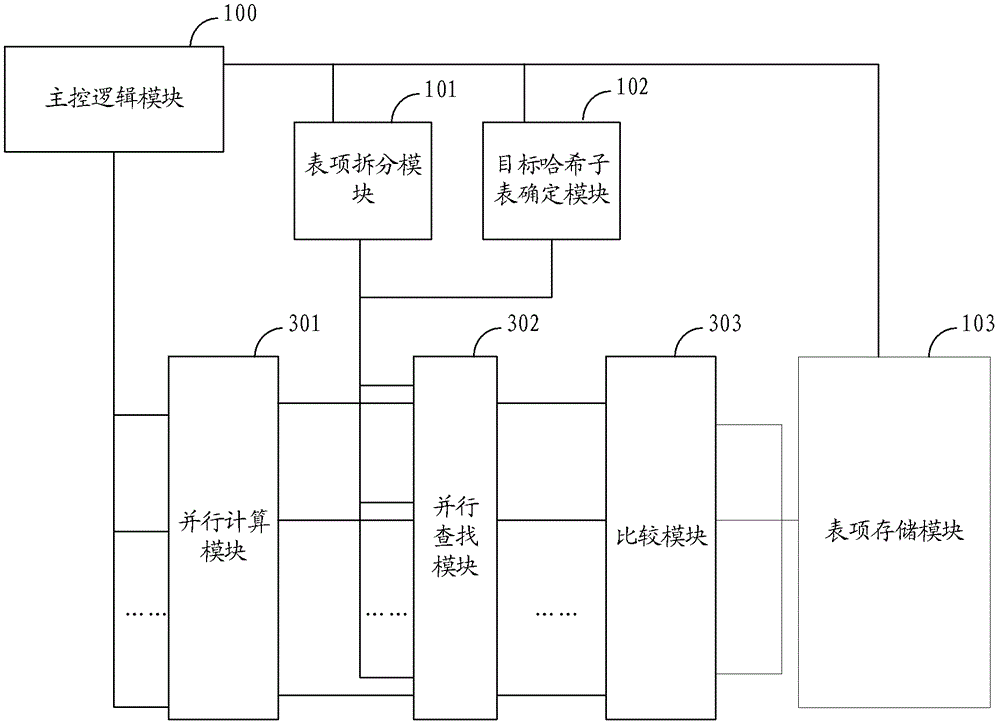
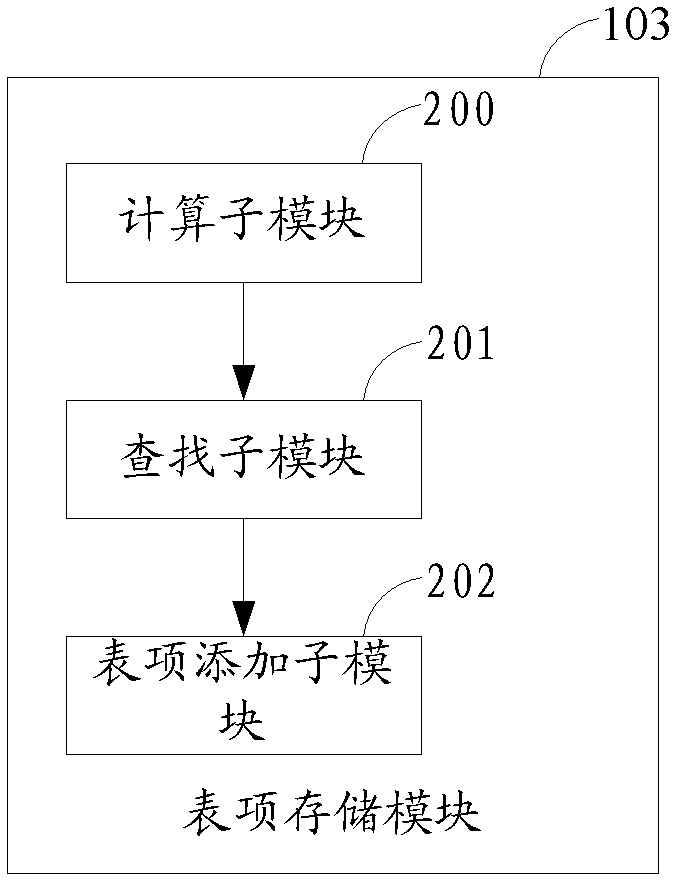
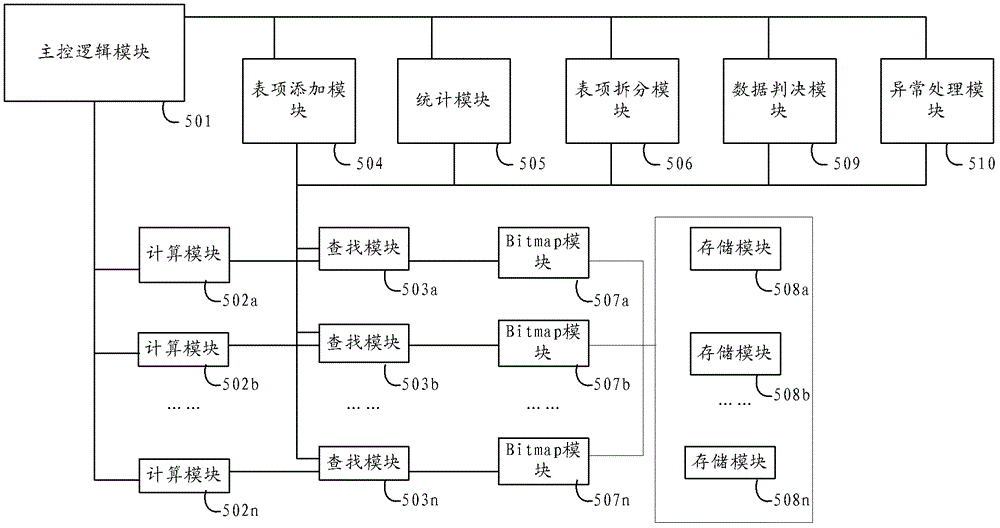
[0088] Please refer to image 3 , is a schematic structural diagram of an embodiment of the hash table storage device in this embodiment. The hash table storage and search system in this embodiment includes a main control logic module 505, a plurality of calculation modules 502a-502n, a plurality of search modules 503a-503n, a table entry adding module 504, a statistics module 505, and a table entry splitting module 506, A plurality of bitmap modules 507a-507n, a plurality of entry storage modules 508a-508n, a data judgment module 509 and an exception processing module 550. The internal connection of the hash table storage device in this embodiment is divided into a data line and a control line. On the data line, the main control logic module 501 is coupled to a plurality of calculation modules 502a-502n, a data judgment module 509; a plurality of calculation modules 502a-502n 502n is respectively coupled to multiple search modules 503a-503n; multiple search modules 503a-503n...
Embodiment 2
[0157] see Figure 9 , this figure is a logical structure diagram of an embodiment of the hash table of the present embodiment, each hash sub-table corresponds to a bitmap and a hash function, wherein the input key value is input to the hash table of the present embodiment through the input interface In the sub-table, the hash value of the input key value is calculated by the hash table storage device, and the hash value is used as an index to find and fill in the vacancy in the bitmap and the hash sub-table; among them, bitmap0~9 are 10 of the same size, A state table with a storage depth of m, hash sub-tables 0 to 9 are 10 memories with the same size and a storage depth of m.
[0158] The hash table storage device in this embodiment is used to complete all operations on input key values according to user requests, including adding, searching, monitoring, exception handling, and the like. Please refer to image 3 , when the hash key value is input into the main control lo...
Embodiment 3
[0176] see Figure 9 , which is a logical structure diagram of an embodiment of the hash table in this embodiment, wherein the input key value is input into the hash sub-table of this embodiment through the input interface, and the input key value is calculated by the hash table controller Hash value, use the hash value as an index to find and fill in the vacancy in the hash subtable; among them, hash subtable 0~9 are 10 memories, representing 10 hash subtables, bitmap0~9 are 10 state tables, However, the storage depth of the first 4 of the 10 memories in this embodiment is m, and the storage depth of the last 6 is m / 2.
[0177] The logical structure of the hash table controller in this embodiment, the storage and search process of the hash table, and the logical structure of the lookup table items are completely consistent with those in the second embodiment.
[0178] Compared with the second embodiment, the space utilization rate of the third embodiment is higher.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com