Authentication card, card authentication terminal, card authentication server, and card authentication system
An authentication server and authentication system technology, applied in transmission systems, user identity/authority verification, electrical components, etc., can solve the problems of increasing authentication burden and destroying the convenience of credit cards.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
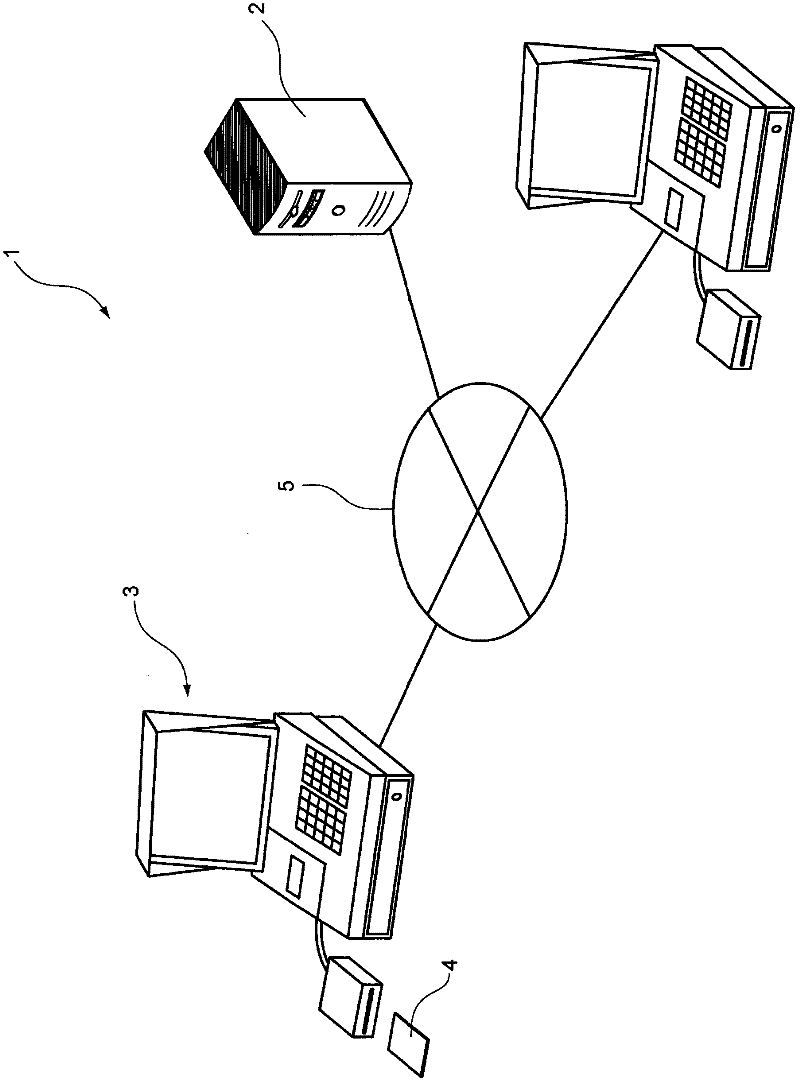
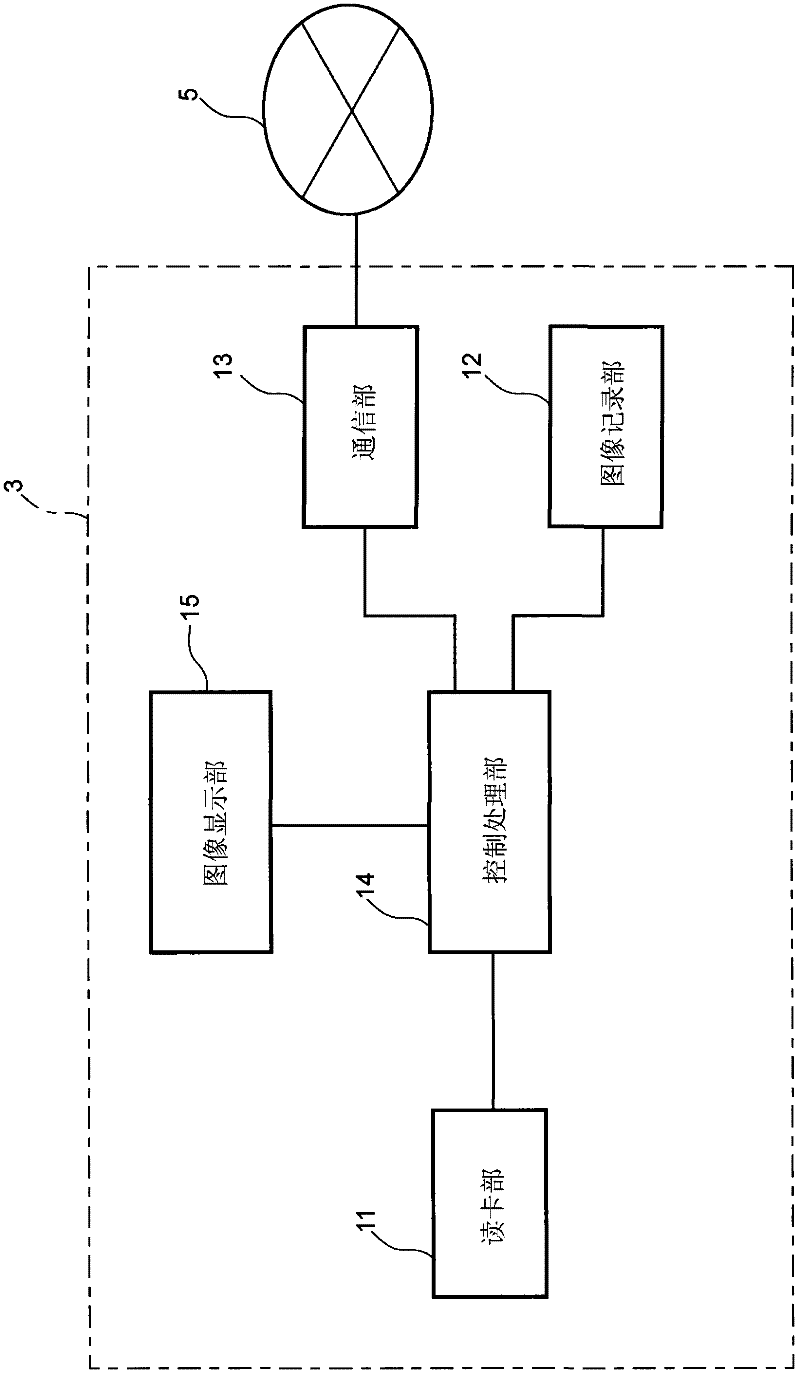
[0113] Next, a card authentication system as an example of the technical means according to the present invention will be shown and described with reference to the drawings.
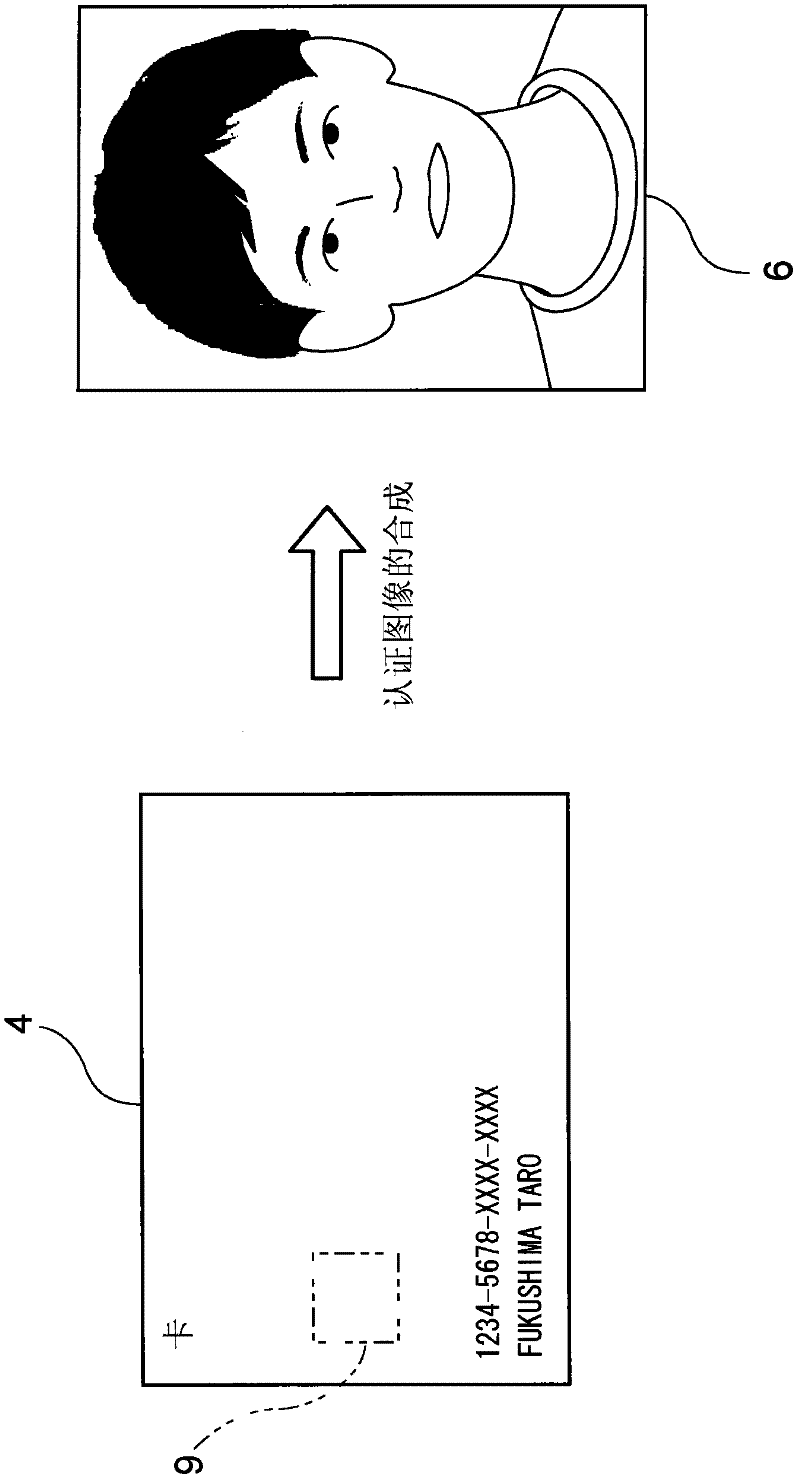
[0114] First, a method of synthesizing authentication images for judging the legitimacy of a card user in the card authentication system according to this embodiment will be described. Here, judging the legitimacy of the card user refers to judging whether the card user is registered as the legal owner (or legal user, holder) of the card. For ordinary cards, card issuing companies and the like often limit the users of the cards to the holders. However, sometimes a person other than the holder uses a legitimate card (not a forged card) pretending to be the holder, and if the card is used in this way, unpredictable losses may be brought to the holder. Therefore, it becomes very important to judge whether the user of the card is the holder.
[0115] Here, the card to be judged as legality refers to a card...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com