Consultation method and system for security policy in next generation network (NGN)
A security policy and policy query technology, applied in the field of communication security, to meet the needs of management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The technical solutions of the present invention will be further elaborated below in conjunction with the accompanying drawings and specific embodiments.
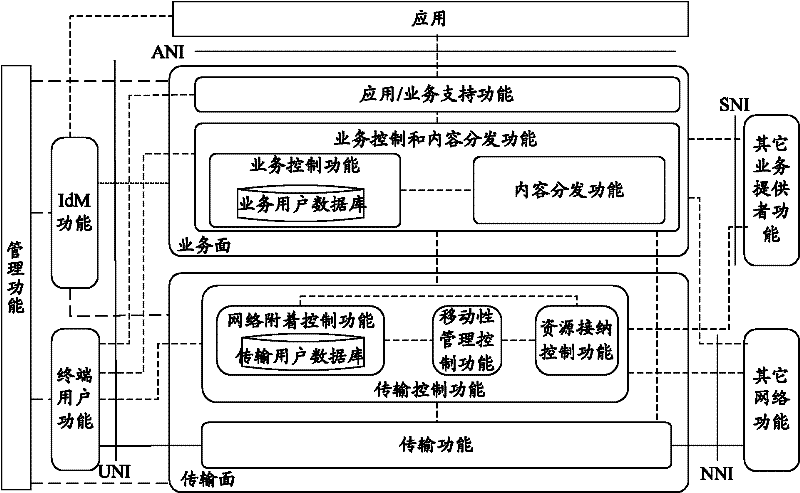
[0035] The present invention aims to provide a method and system for negotiating security policies in NGN. By extending the existing NGN architecture, adding security policy-related network elements and standardizing security policy negotiation and execution procedures, so as to meet the requirements of security policy management in NGN need.
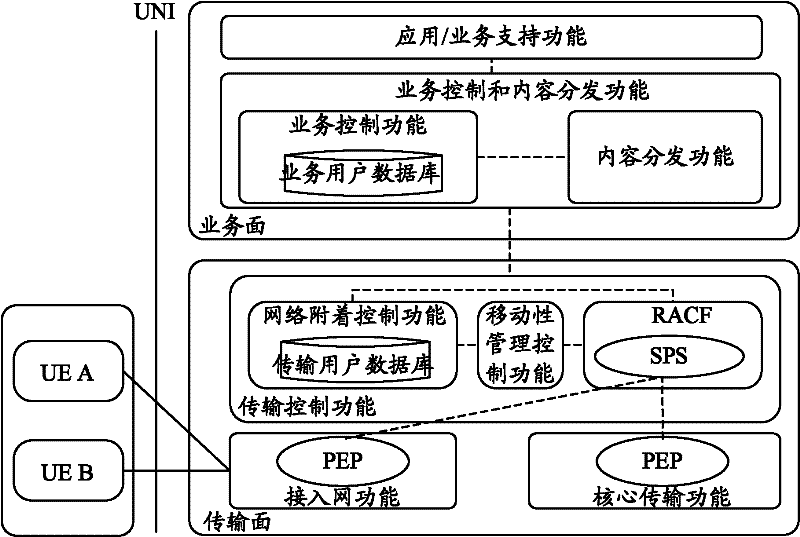
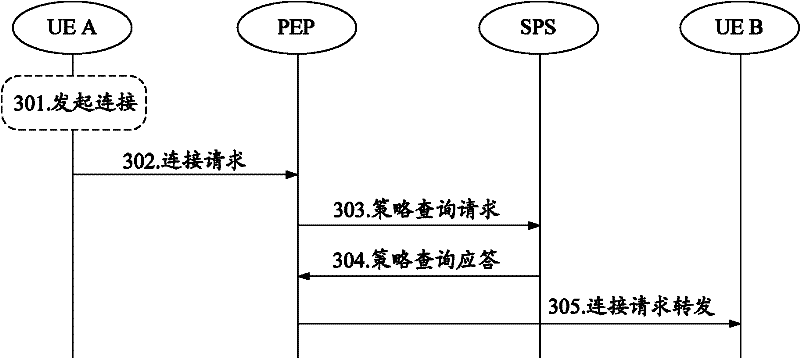
[0036] A security policy management framework in the NGN domain provided by the embodiment of the present invention, such as figure 2 As shown, a Security Policy Server (SPS, Security Policy System) and a Security Policy Enforcement Point (PEP, Policy Enforcement Point) are added to the transmission plane of the existing NGN architecture to implement decision-making and execution of security policies. SPS is mainly used to store and distribute security policies, and PEP is u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com