Blind identification method for coding parameter of hamming code
A technology of encoding parameters and Hamming codes, applied in the field of intelligent communication and non-cooperative communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
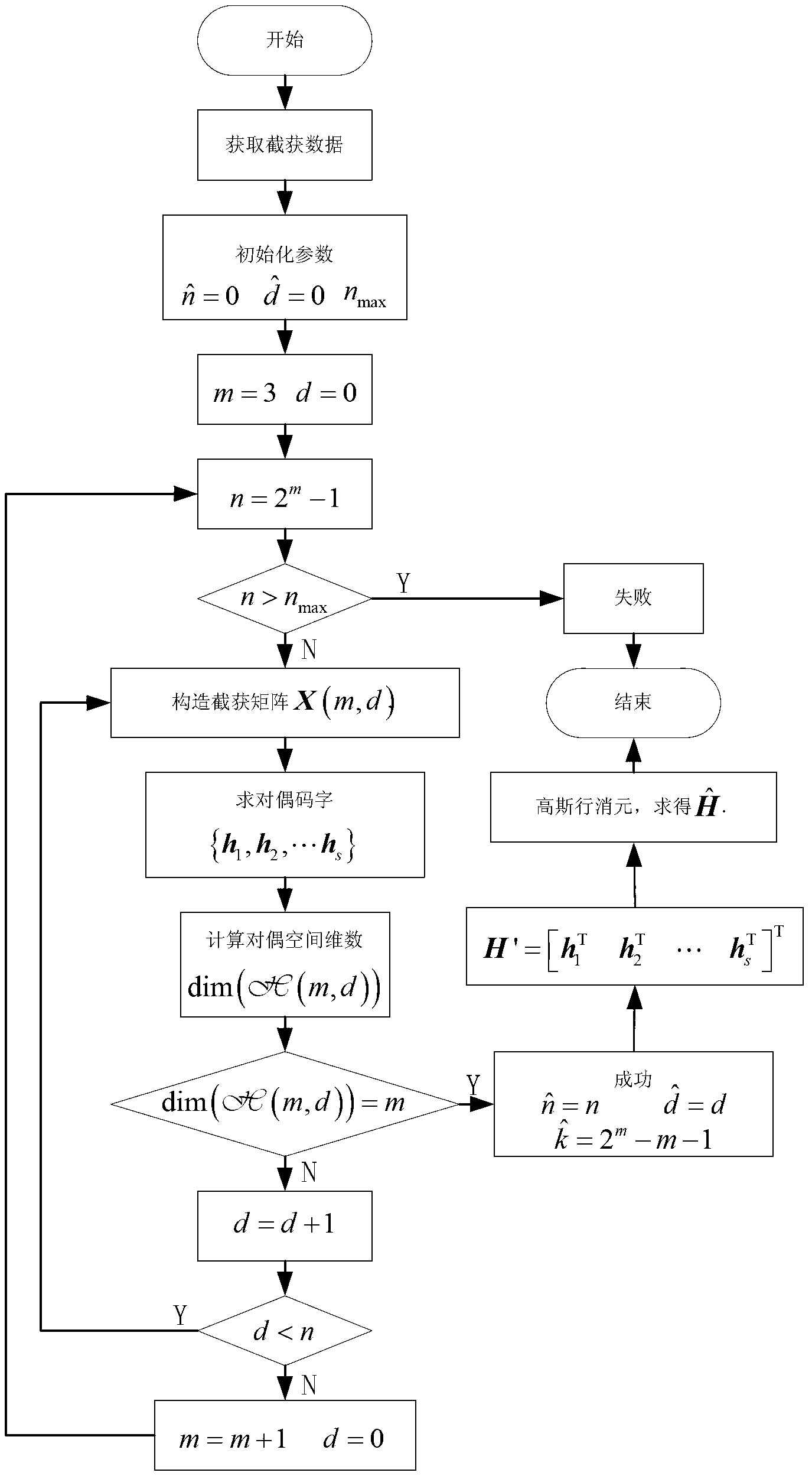
[0030] Such as figure 1 shown, including the following steps:
[0031] Step 1: Initialize parameters: set code length n=0, synchronization time d=0, maximum recognition length n max . Let the outer loop control variable initialize m=3, let the inner loop control variable initialize d=0, 0≤dm -1, go to step 2.
[0032] Step 2: Let n=2 m -1 if n>n max , the loop terminates; otherwise, go to step 3.
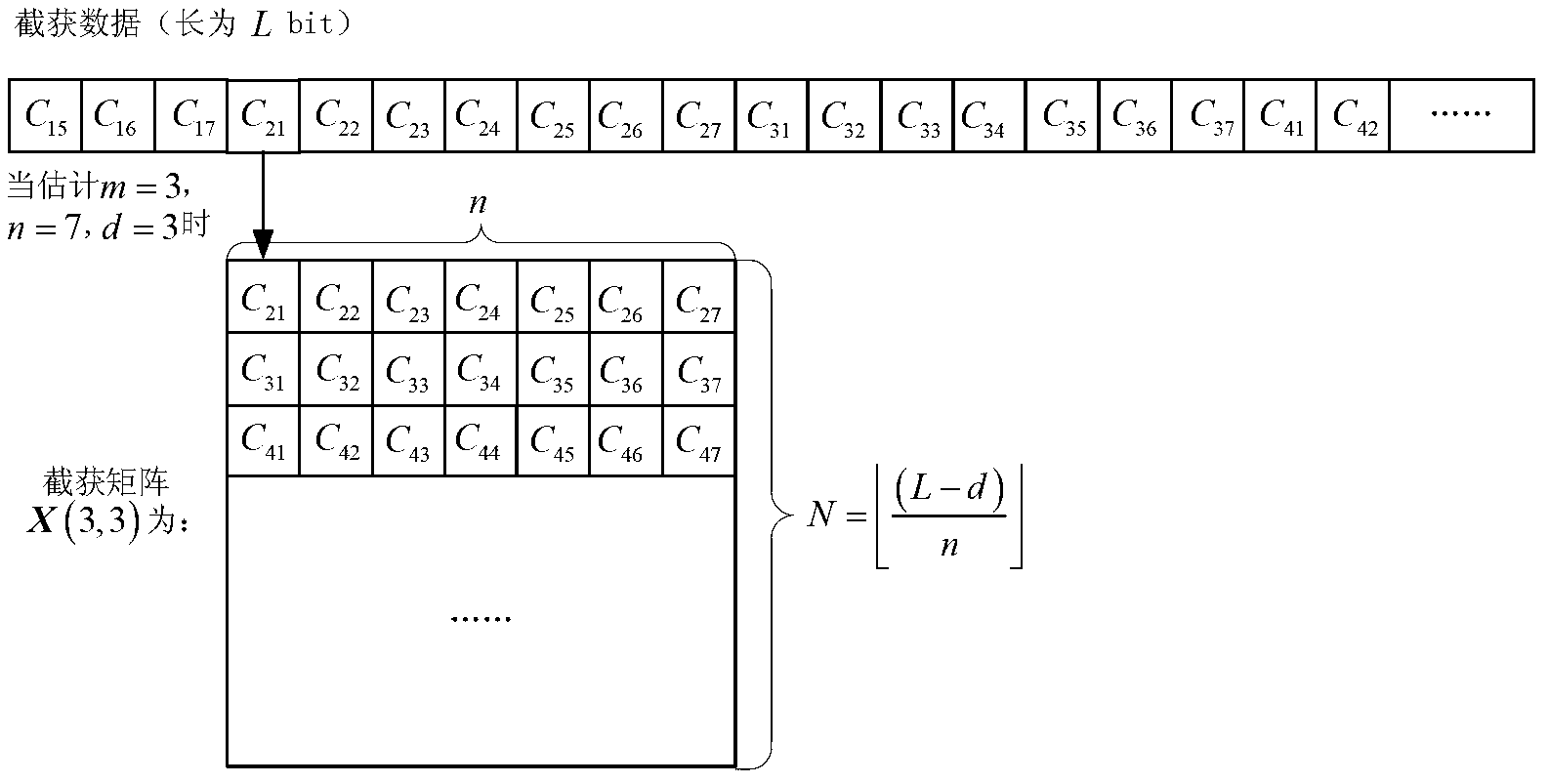
[0033] Step 3: Assume that the dual space dimension of the Hamming code is m and the synchronization time is d, then the code length n=2 m -1, the information bit length is k=2 m -m-1. For the intercepted data with a length of L bits, remove the first d bits, and then divide the remaining (L-d) bit data according to the length of n into codewords, Represents rounding down, and each codeword is used as each row of the matrix X(m,d) to form an N×n interception matrix X(m,d), such as figure 2 As shown, C in the figure ij Represents the j-th bit of the i-th codeword.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com