Method and device for processing user resources
A technology of user resources and processing methods, which is applied in the field of user resource processing methods and devices, can solve problems such as unreasonable distribution of wireless resources, and achieve the effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
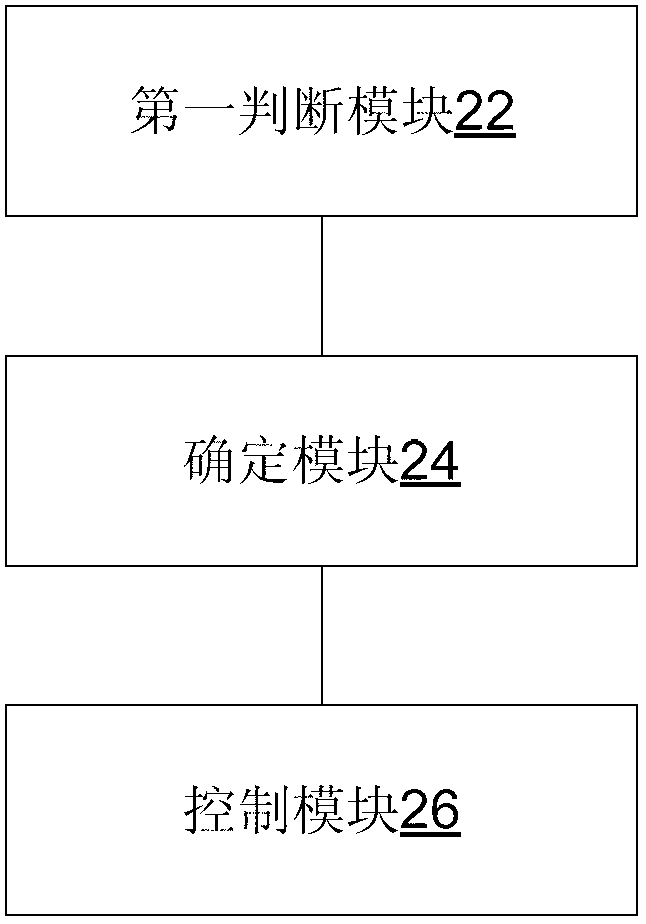
[0070] This embodiment provides a method for controlling user resources. In this embodiment, malicious users are identified and their resource occupation capabilities are limited to ensure reasonable distribution of wireless resources, increase network capacity, and improve user awareness. Compared with traditional methods such as capacity expansion, the input cost is low, and it is more direct and effective.
[0071] The characteristics of the malicious users in this embodiment are shown in Table 1. Such users consume too many wireless resources such as carrier scheduling time slots and wireless traffic, and have a long connection time, which leads to a decrease in the usage perception of other online users. According to the analysis of existing network resources, under normal circumstances, the connection times of malicious users only account for 1% of the total connection times, and the proportion of users does not exceed 10%, but it occupies more than 70% of scheduling reso...
Embodiment 2
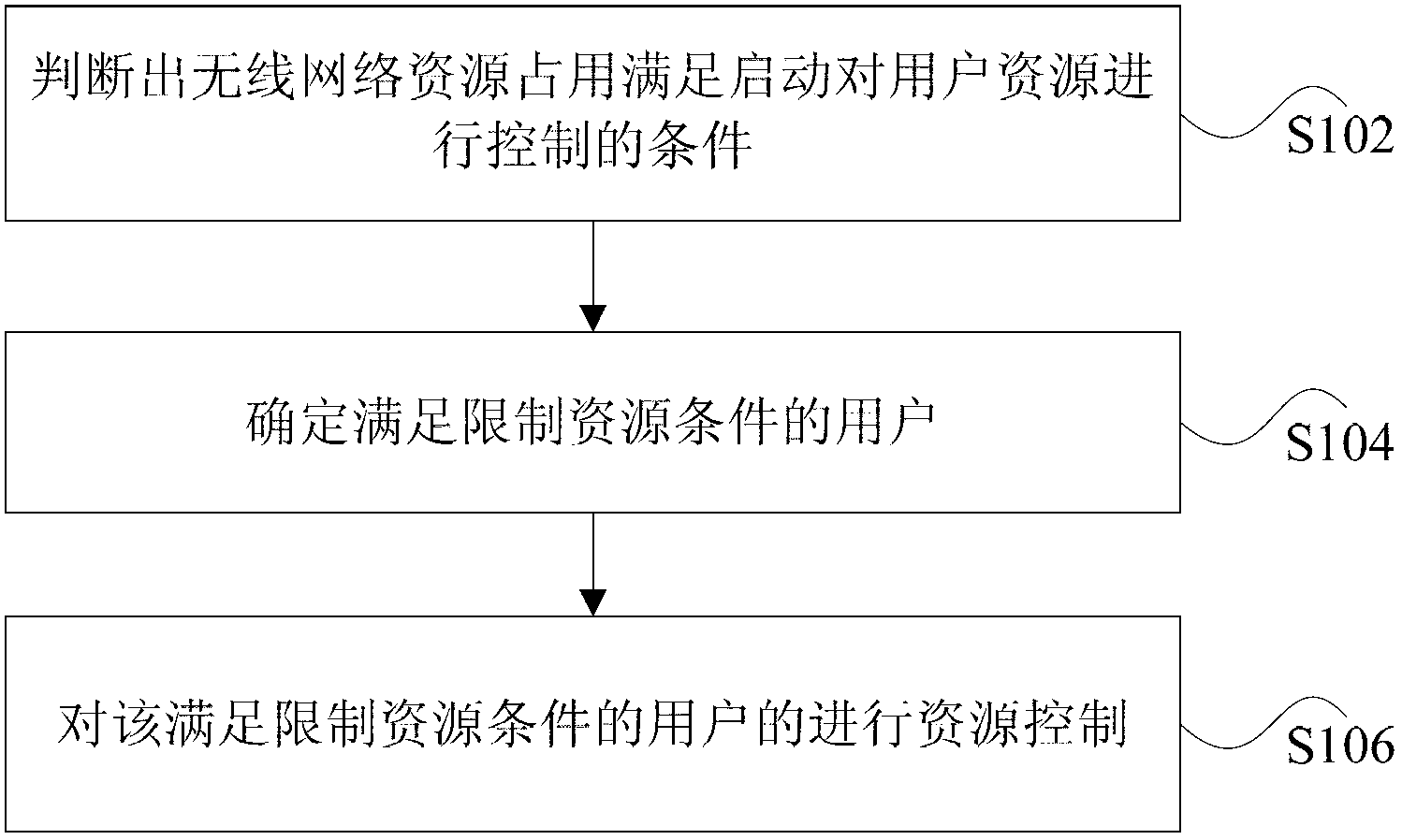
[0082] This embodiment provides a user resource control method, which includes the following steps S2 to S8.
[0083] Step S2: Monitor wireless network resource distribution.
[0084] Step S4: Judging whether the restriction strategy activation condition is satisfied.
[0085] Step S6: updating the malicious user list.
[0086] Step S8: reducing the ability of malicious users to occupy wireless resources.
[0087] The advantage of this preferred embodiment is that malicious users can be effectively identified, and whether to enable a restriction policy to weaken the ability of malicious users to occupy resources is selected according to the distribution of wireless resources. While improving the usage perception of most users, it also ensures the reasonable distribution of wireless resources and improves the wireless network capacity to a certain extent.
Embodiment 3
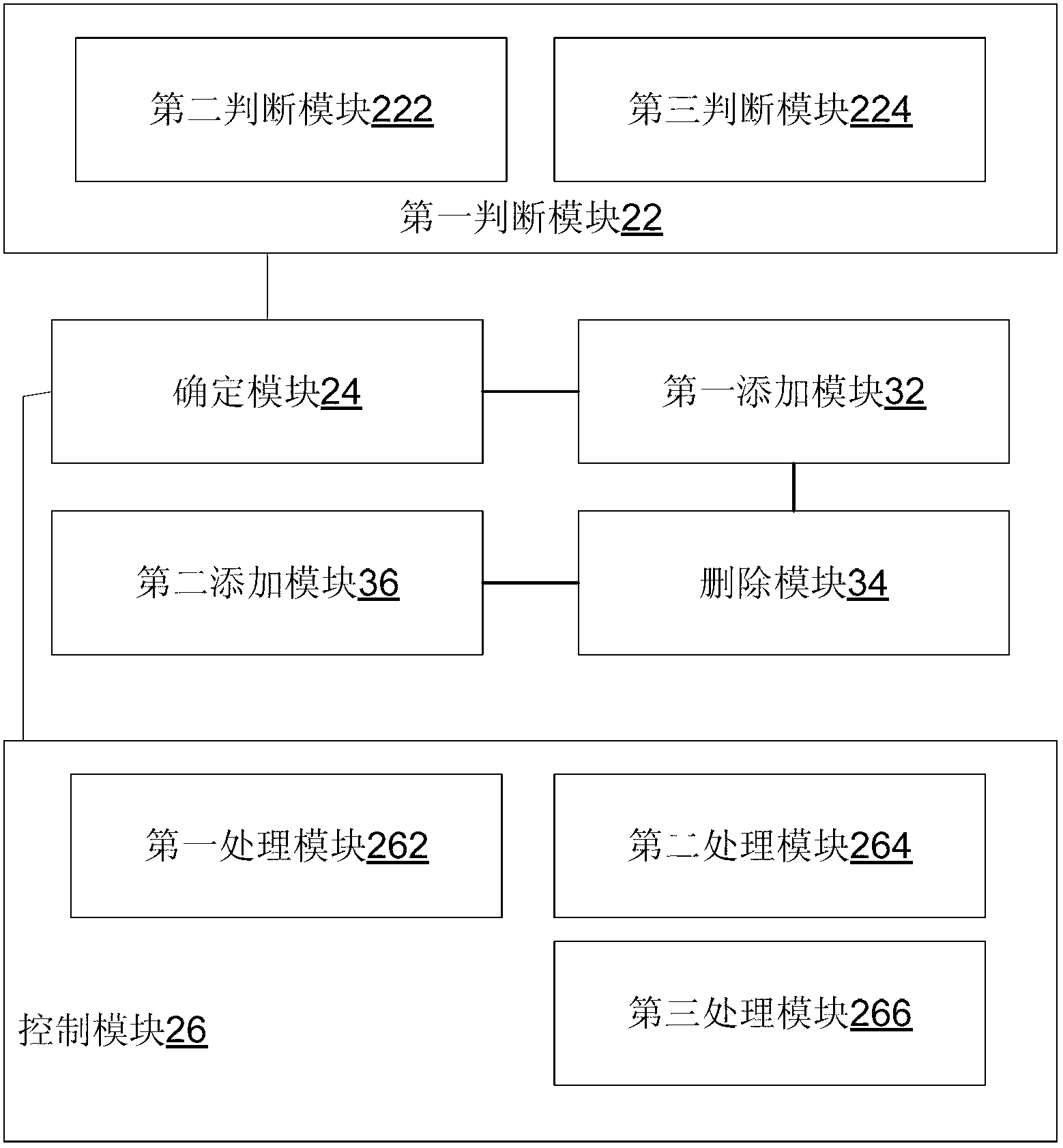
[0089] This embodiment provides a user resource control method, Figure 4 is a flowchart of a user resource processing method according to a preferred embodiment of the present invention, such as Figure 4 As shown, the method includes step S402 to step S416.
[0090] Step S402: Monitor wireless network resource occupancy, including the ratio of the number of bearer users to the bearer scheduling time slot, and the wireless resource occupancy, traffic, and connection duration of all users under the bearer.
[0091] Step S404: Judging whether to activate the vicious user restriction strategy, the restriction strategy is only activated when the number of carrier users is greater than 5 and the carrier scheduling time slot ratio is less than 80%, if the judgment result is yes, execute step S406, otherwise execute step S408.
[0092] Step S406: The processing branch belonging to the activation restriction strategy screens all users under the download fan, and locks malicious user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com