Using aggregated DNS information originating from multiple sources to detect anomalous DNS name resolutions
A technology for detecting anomalies and name resolution, applied to electrical components, transmission systems, data exchange through path configuration, etc., can solve problems such as difficult addressing, inappropriate DNS attacks, and difficult detection of client DNS record control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
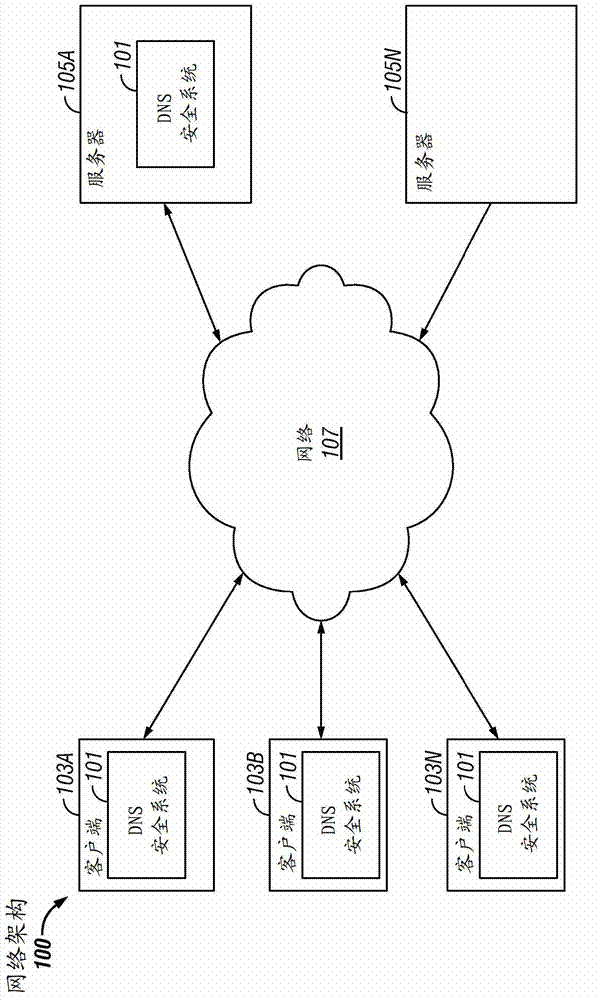
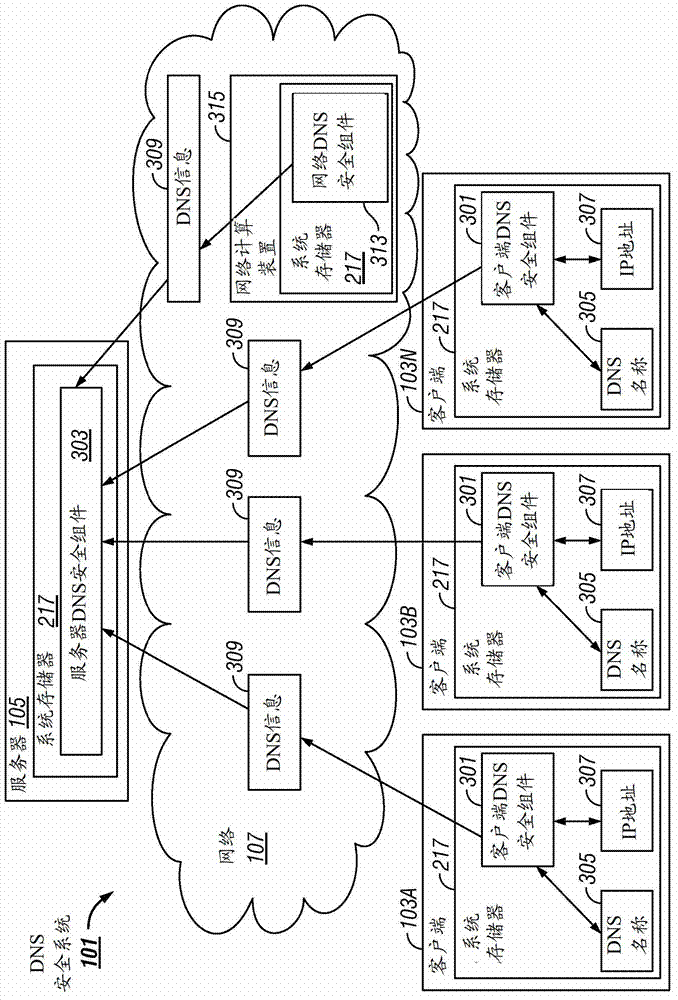
[0014] figure 1 The block diagram of , illustrates an exemplary network architecture 100 in which a DNS security system 101 can be implemented. The illustrated network architecture 100 includes multiple clients 103A, 103B, and 103N, and multiple servers 105A and 105N. exist figure 1 , DNS security system 101 is shown residing on server 105A and clients 103A, 103B, and 103N. It should be understood that this is only one example, and that in various embodiments the various functions of the system 101 can be instantiated on the client 103, the server 105, the network computing device 313, or can be distributed among as many clients 103 as desired and / or server 105.
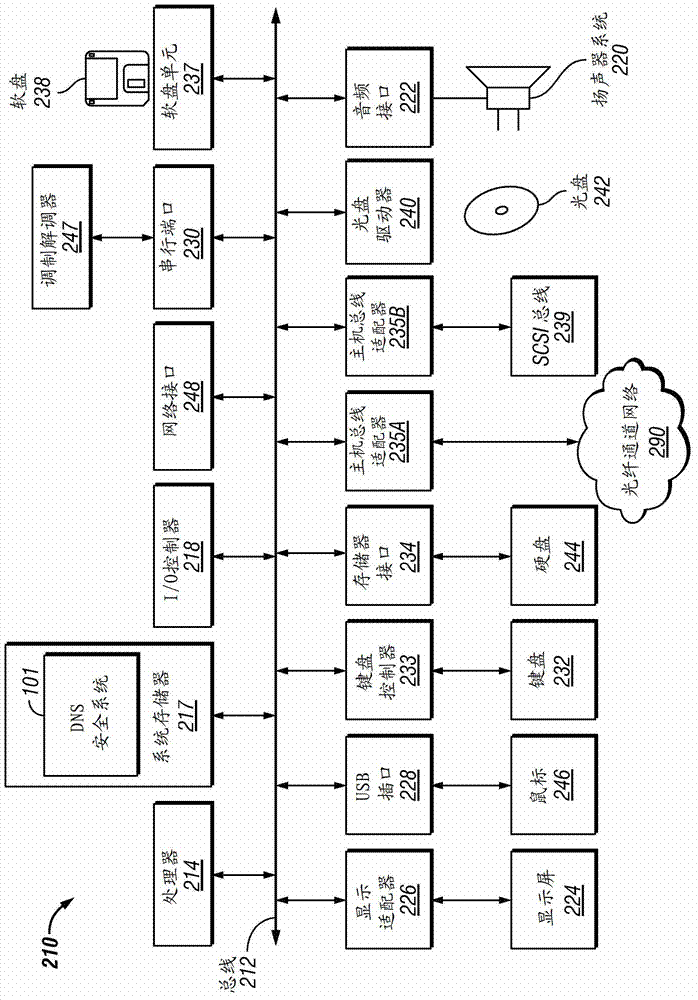
[0015] as in figure 2 Computer system 210 shown in and described below may be used to implement client 103 and server 105 . The client 103 and the server 105 are communicatively connected to the network 107, for example through a combination of figure 2 A network interface 248 or modem 247 is depicted. Clien...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com