Method and device for unlocking files
A file unlocking and target file technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of lack of ability, weak confrontation ability, single means of unlocking and shredding infected files, etc., to enhance confrontation ability and avoid potential incompatibility. effect of possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
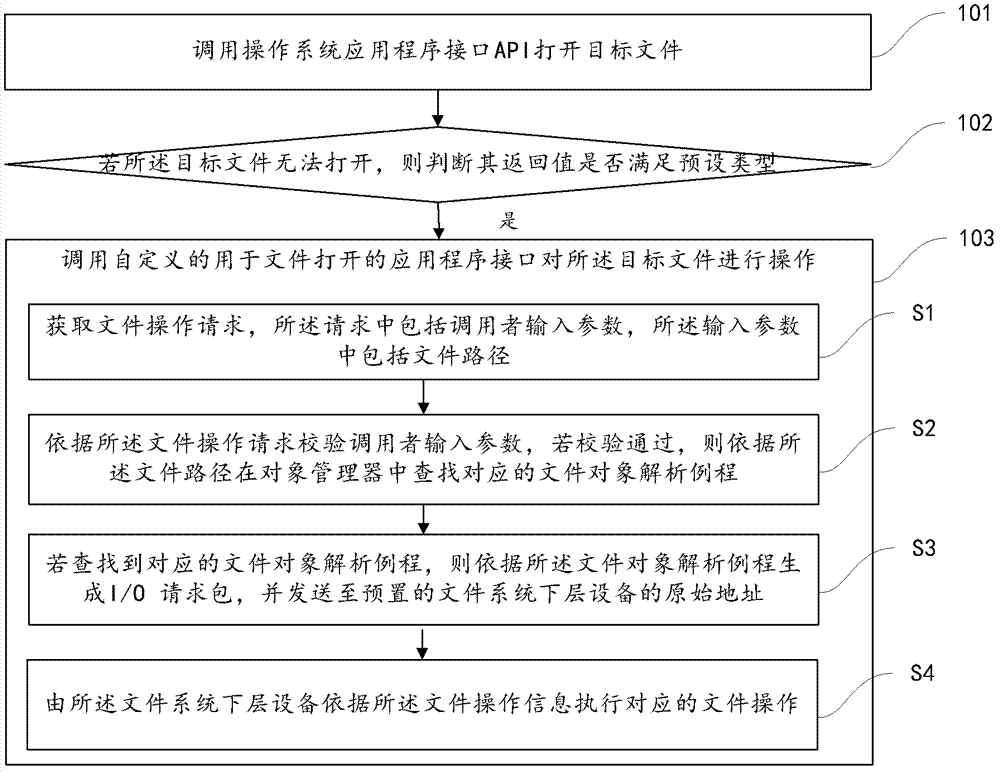
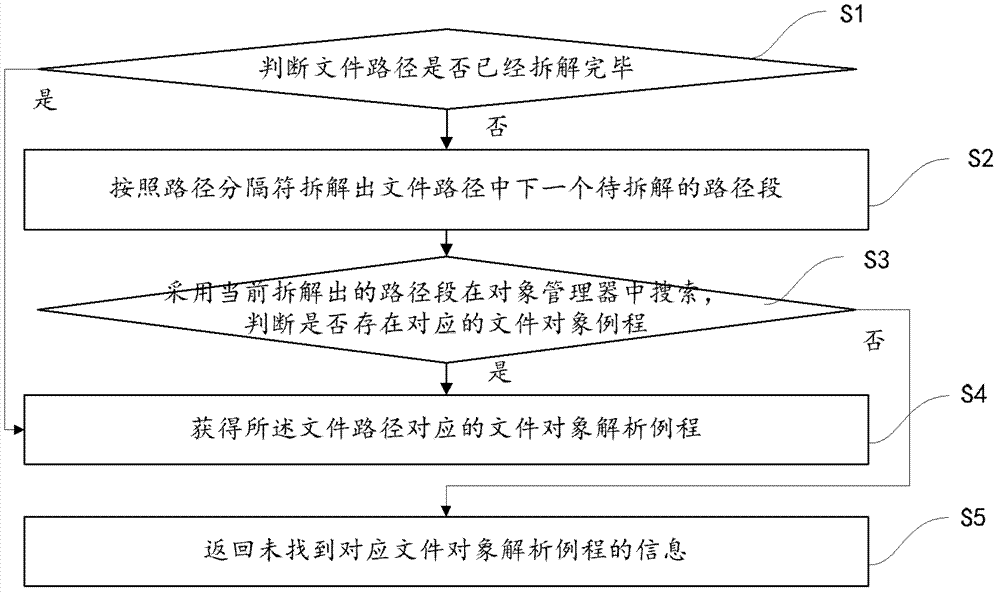
[0059] One of the core concepts of the embodiments of the present invention is to completely implement a set of file operation call libraries in the user mode interface of the operating system. When the target file cannot be opened by calling the application program interface API of the operating system, the return value is exclusive to the file sharing attribute. Or, in the case of file permission and owner restrictions, call the custom application program interface BAPI realized by the present invention to perform file unlocking and shredding operations on the target file.
[0060] refer to figure 1 , which shows a flow chart of the steps of an embodiment of a file unlocking method of the present invention, which may specificall...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com