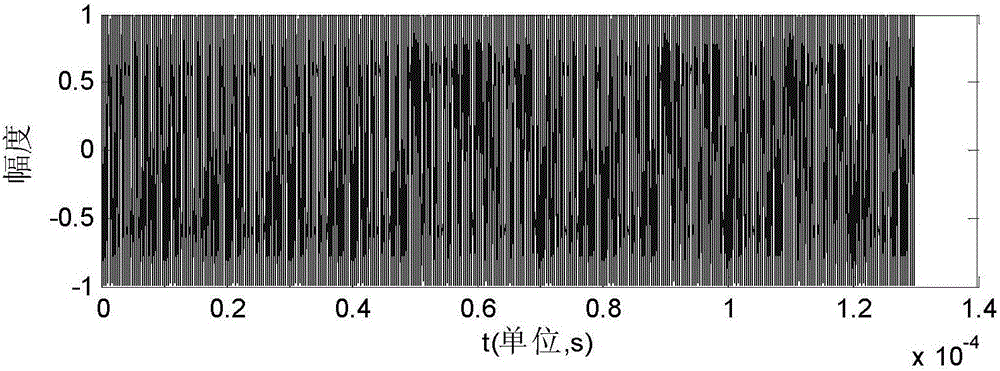
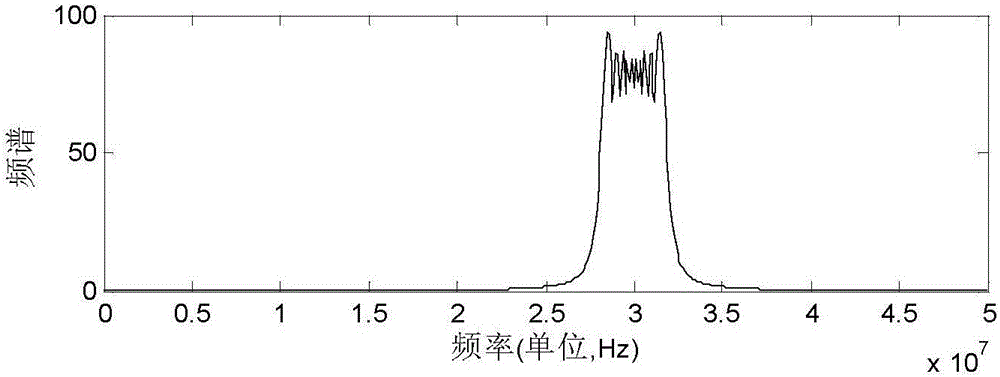
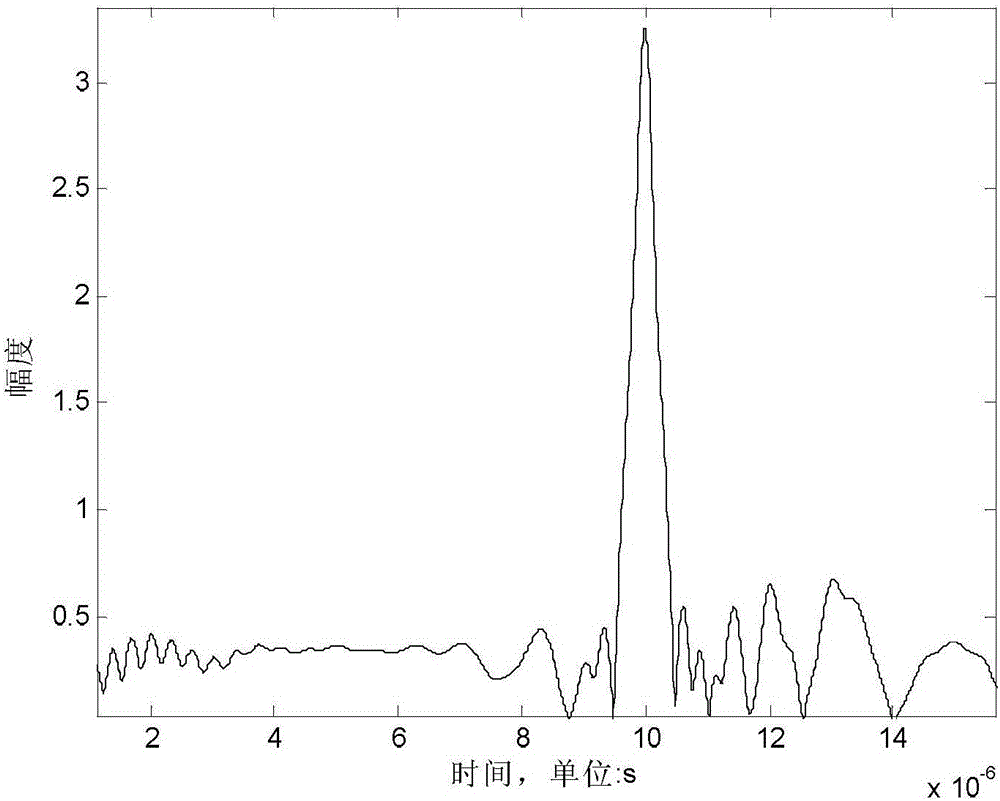
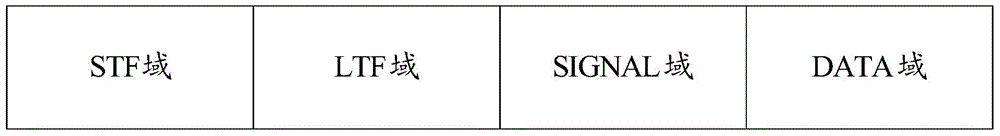
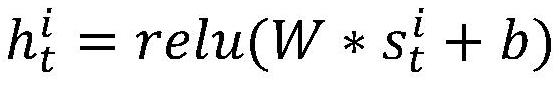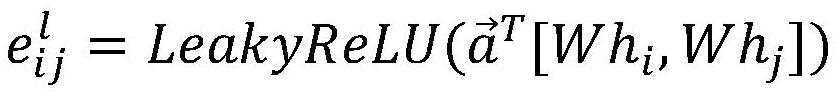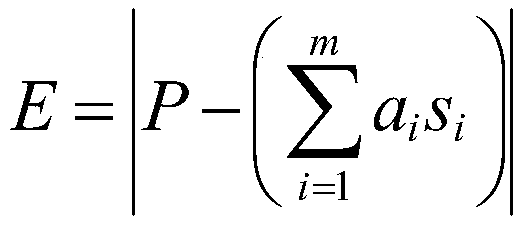Patents
Literature
101results about How to "Enhanced confrontation ability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
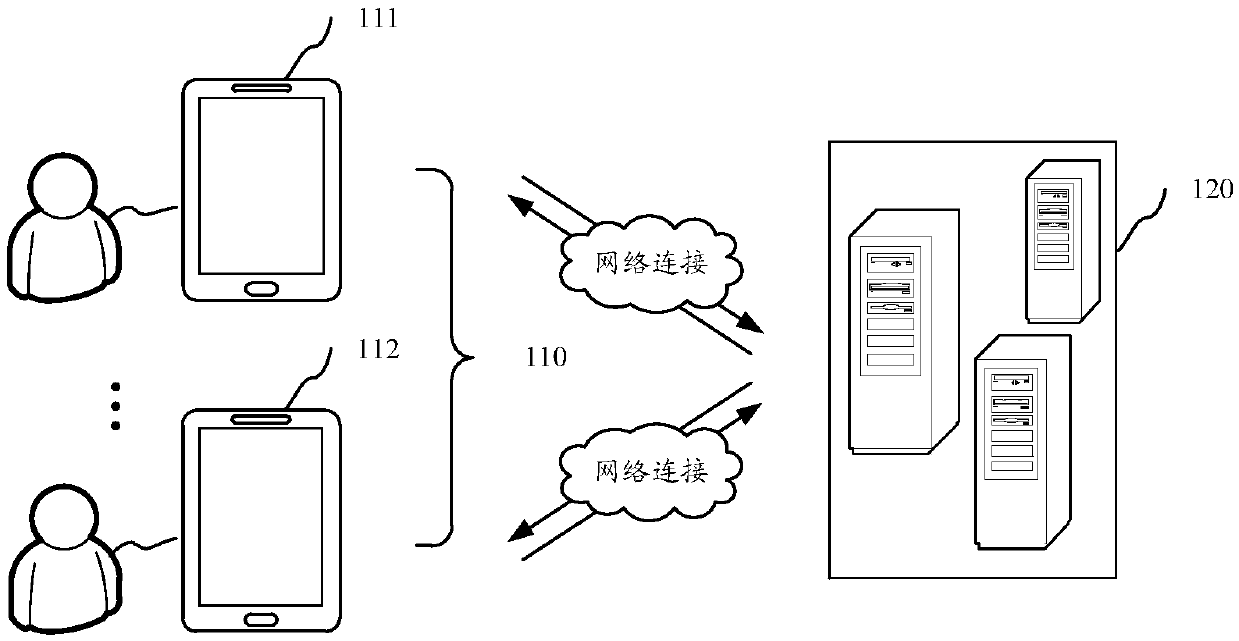
Resource acquiring method and apparatus and resource processing method, apparatus and system
ActiveCN105389117AEnhanced confrontation abilityFast operationTransmissionInput/output processes for data processingUser identifier
The invention relates to a resource acquiring method and apparatus and a resource processing method, apparatus and system. The resource acquiring method comprises: displaying an operation page for acquiring a resource; detecting a touch operation acting on the operation page; recording an operation frequency of the detected touch operation; sending a resource acquiring request which carries a user identifier of a current login user and the operation frequency to a server, and making the server adjust a randomly selected probability according to the operation frequency to randomly acquire a decision result whether resources are allocated for the user identifier; and receiving a resource acquiring result fed back after the server performs a corresponding operation according to the decision result. According to the resource acquiring method and apparatus provided by the invention, the capability of resistance to plug-in users is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
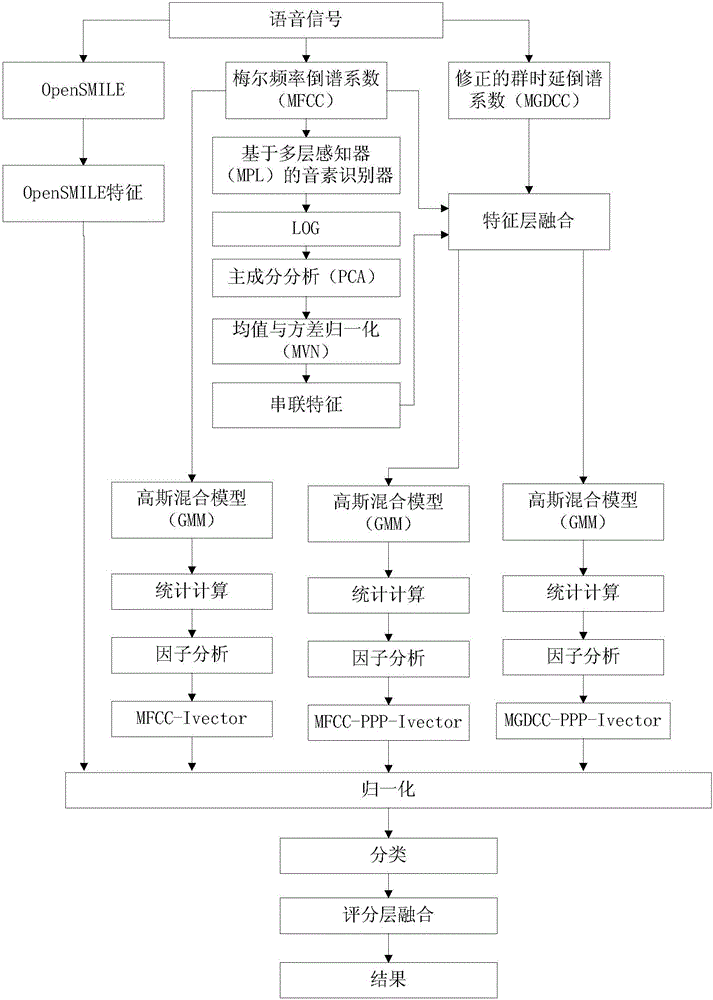
Countercheck method for automatically identifying speaker aiming to voice deception
ActiveCN105139857ACountermeasures work wellEnhanced confrontation abilitySpeech analysisCosine similaritySupport vector machine
The invention provides a countercheck method for automatically identifying a speaker aiming to voice deception, which is a voice anti-spoofing technology based on a method combining various features and a plurality of sub-systems. According to the invention, the serial features of the posterior probability of a phoneme in the phonological level and the MFCC features of voice level or MFDCC features of phase level are combined, thus the performance of the system is significantly enhanced. By combining the provided i-vector sub-system and OpenSMILE (open Speech and Music Interpretation by Large Space Extraction criterion containing voice and rhythmic information, the final presentation of the system is further enhanced. To a back-end model, the development datum are used; and under the situation of knowing deceptive attacks, a two-level support vector machine has better performance compared with one-level cosine similarity or PLDA evaluations, while the one-level evaluation approach has better robustness under the situation without seeing the test datum and knowing the deceptive conditions.
Owner:SUN YAT SEN UNIV +1
Internet game contest method and service system thereof
InactiveCN1862547ALimit the number of times a match can be repeatedPrevent biased selectionSpecial data processing applicationsThe InternetInterconnection
The present invention relates to an interconnection network game service correlation technique, and discloses an interconnection network game competition method and its service system. It can make interconnection game competition more have fairness, more can reflect real level of players and can effectively prevent players from adopting cheat act. Said invention also provides its game method and concrete competition rule, and also provides the composition portions of said game service system.
Owner:HUAWEI TECH CO LTD
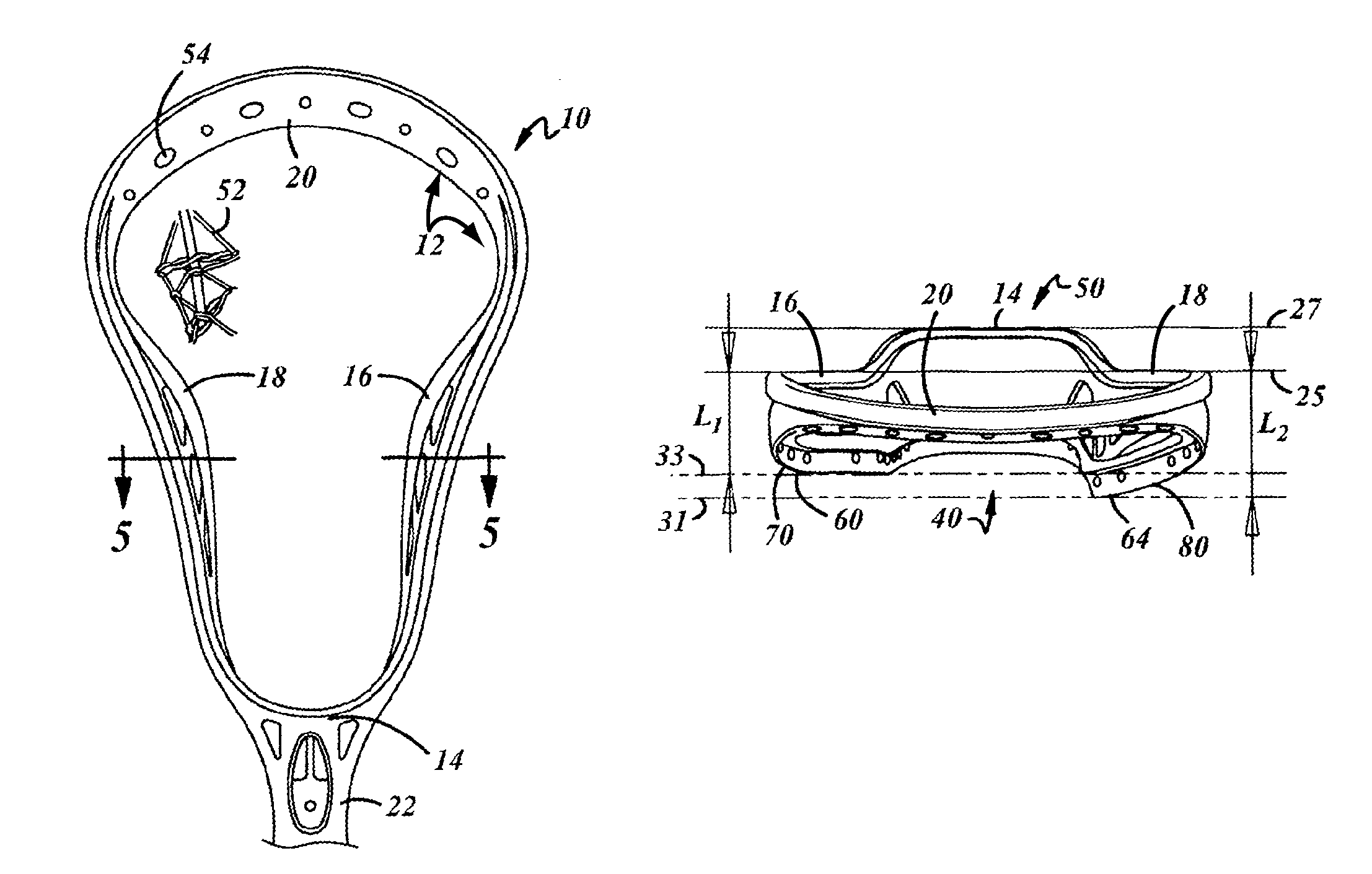
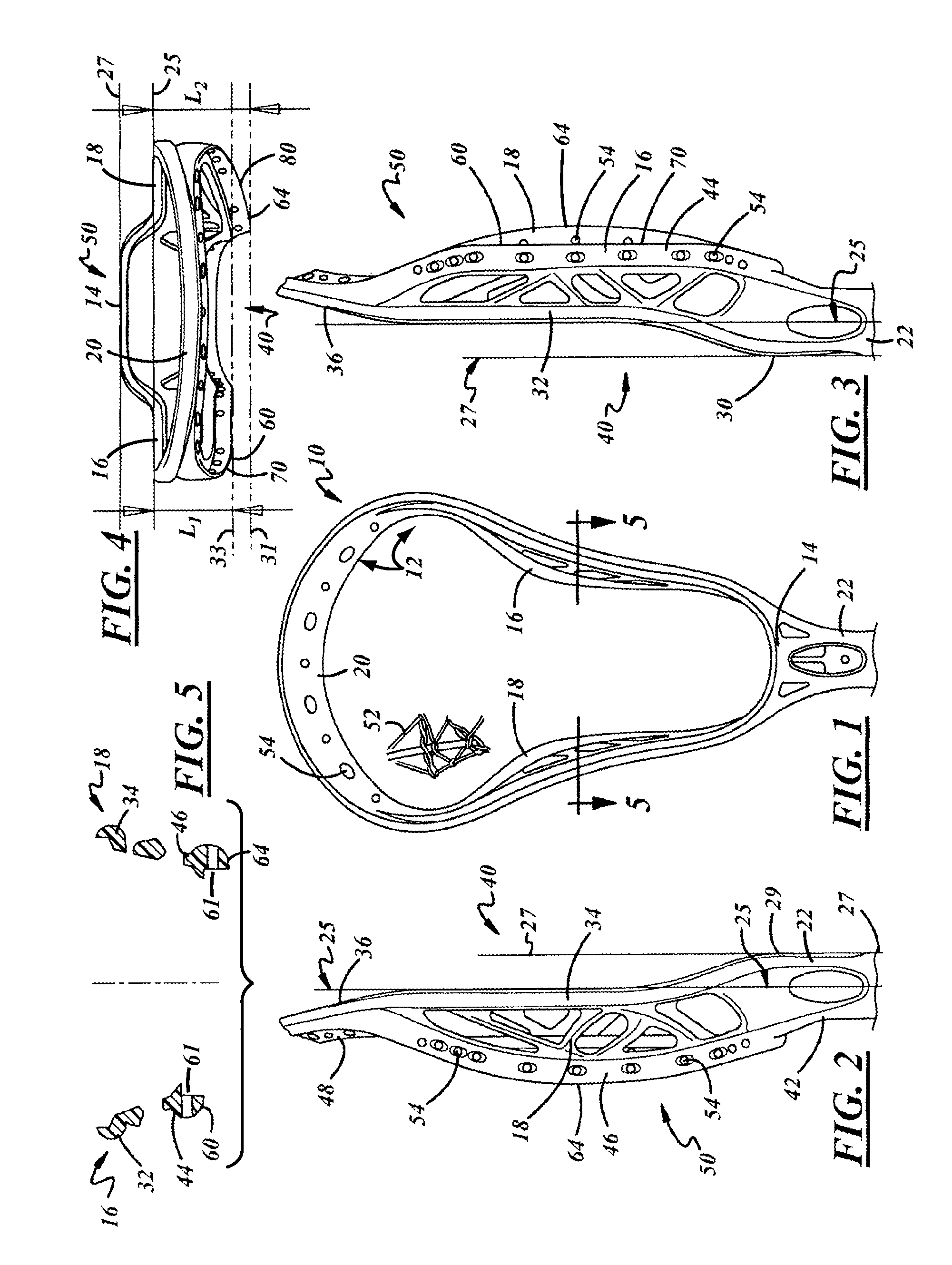
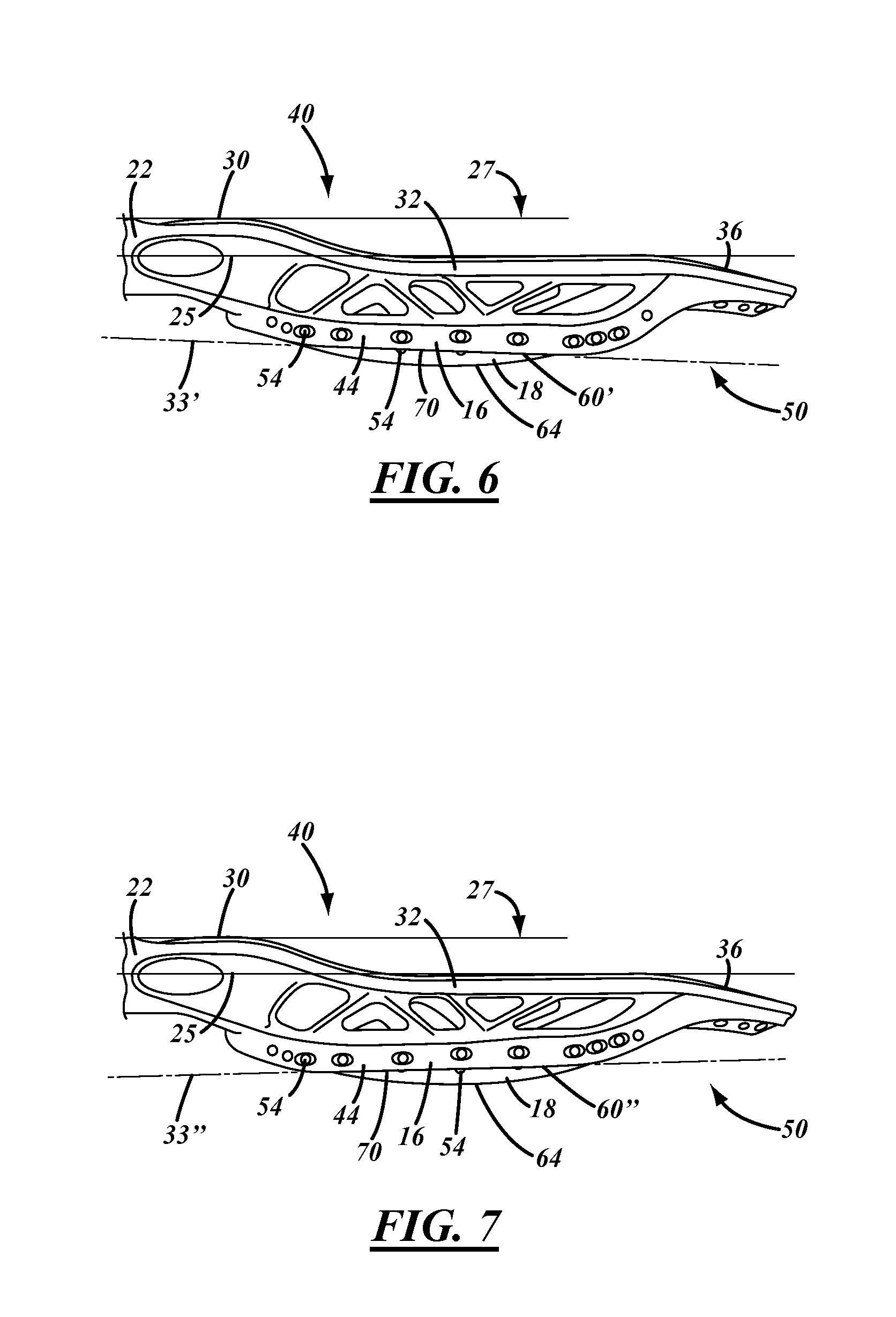
Lacrosse head with sidewalls of asymmetrical height
Owner:WARRIOR SPORTS INC
Smart jamming noise signal design method based on velocity pull-off
ActiveCN105929376AEnhanced deceptionEnhanced inhibitory effectWave based measurement systemsAnti jammingRadar
The invention provides a smart jamming noise signal design method based on velocity pull-off and relates to the smart jamming noise signal design method. The smart jamming noise signal design method based on the velocity pull-off is put forward to solve the problem that false target track is easy to be cancelled by radar anti-interference when uncorrelated, so that the effect of suppression jamming cannot be achieved, and the effect of anti-jamming measures, such as echo sidelobe cancellation, is not good enough. The method is realized through the following steps: 1) calculating time delay tau; 2) calculating Doppler frequency shift fd obtained after an electromagnetic signal is reflected back to a radar antenna through secondary scattering of a target; 3) calculating the amplitude value At of a target echo signal at the time t after the electromagnetic signal is reflected back to the radar antenna through secondary scattering of the target; 4) calculating the target echo signal sr(t); and 5) increasing offset of the Doppler frequency shift fd. The method is applied to the smart jamming noise signal design field.
Owner:HARBIN INST OF TECH
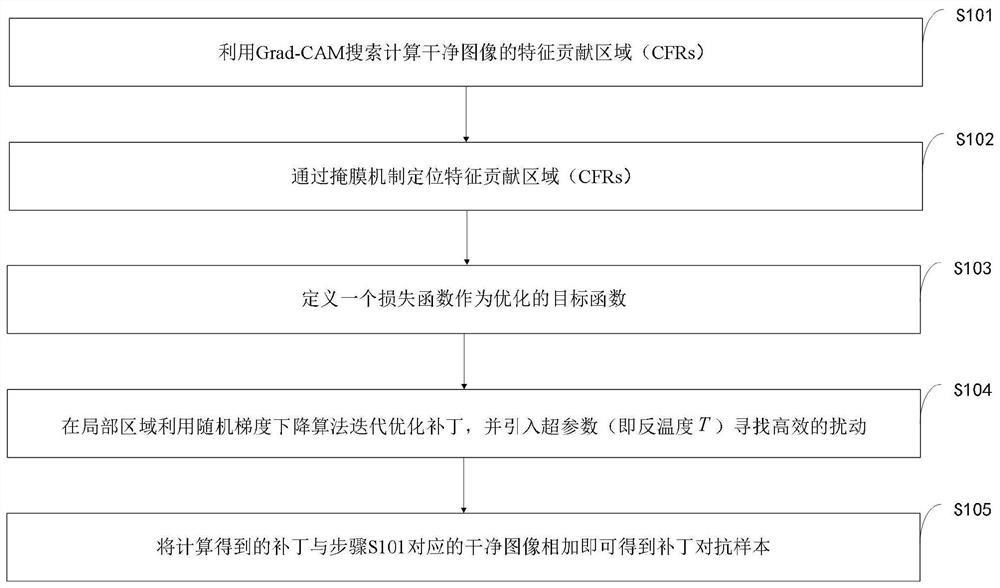
Imperceptible adversarial patch generation method and application
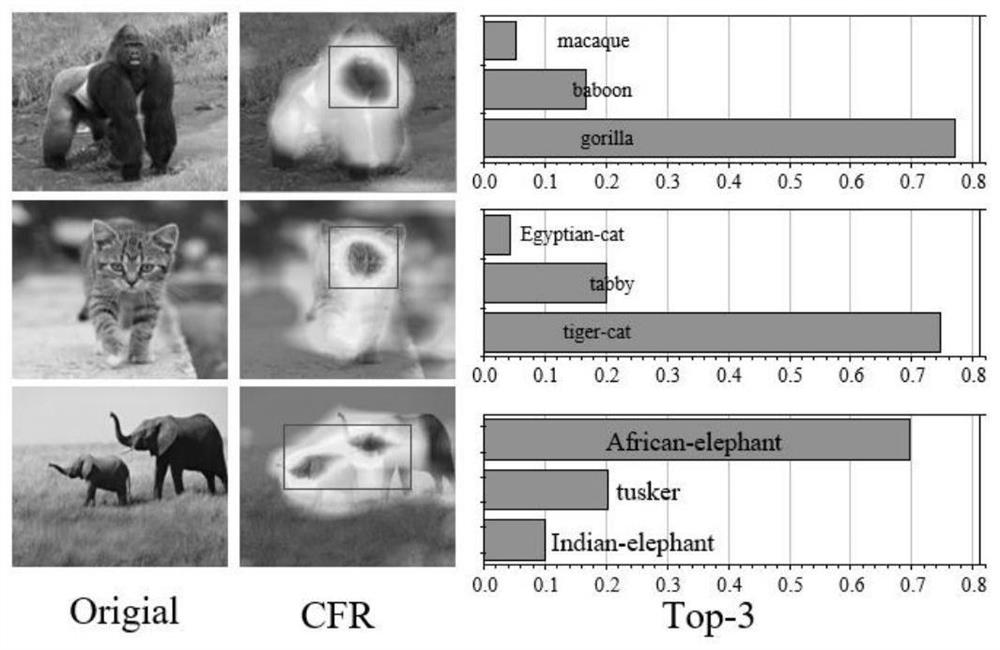
PendingCN112364915AReduce sizeImprove balanceCharacter and pattern recognitionNeural architecturesStochastic gradient descentData set
The invention belongs to the technical field of artificial intelligence security, and discloses a high-strength adversarial patch sample generation method and application, and the method comprises thesteps: firstly calculating an area, which greatly affects a CNNs classification decision, in an image through Grad-CAM, and using the area as a feature contribution area (CFRs) of the image; and positioning the region by using a mask mechanism so that scrambling can be completed in the determined feature contribution area. According to the method, a loss function is redefined to serve as an optimized objective function, then a stochastic gradient descent optimization algorithm is utilized, hyper-parameters are introduced to search for efficient disturbance, and then the adversarial sample based on CFRs can be obtained. According to the method, good balance between countermeasure strength and imperceptibility is realized by only scrambling in a feature contribution area and limiting a disturbance range within a micro range which is difficult to perceive by human eyes, and experimental verification is performed on CIFAR-10 and ILSVRC2012 data sets. The adversarial sample generated by the method is applied to adversarial training, and the deep learning defense capability can be effectively improved.
Owner:ZHEJIANG UNIVERSITY OF SCIENCE AND TECHNOLOGY
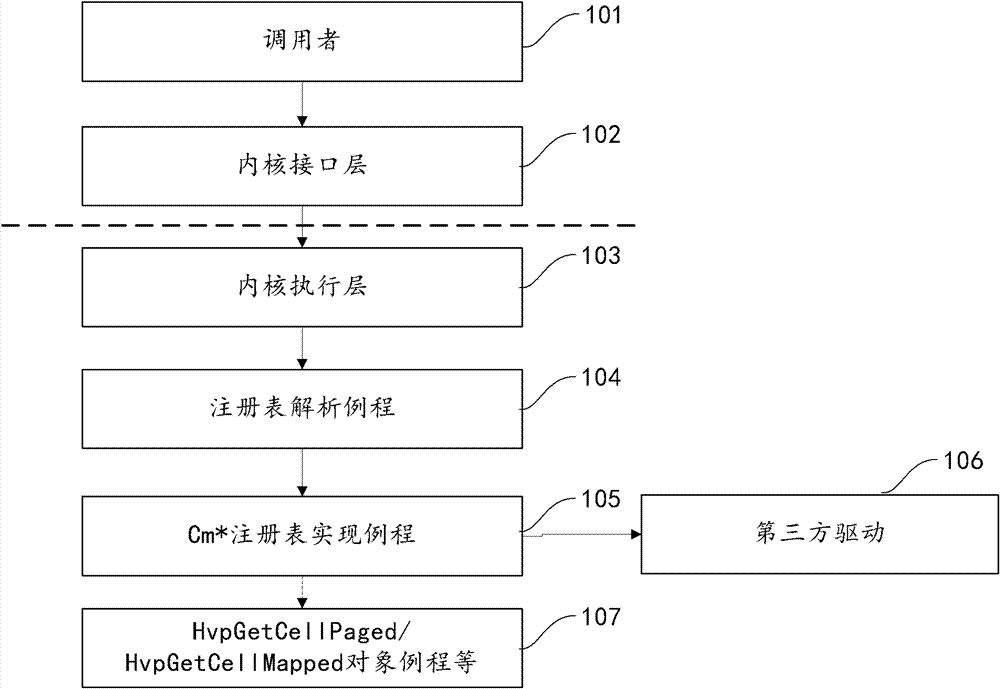
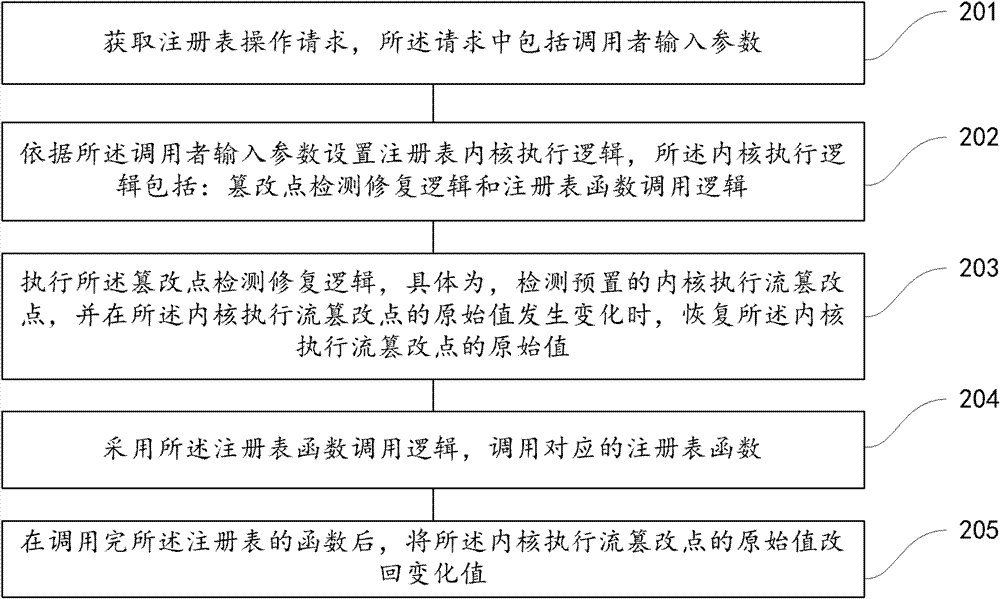
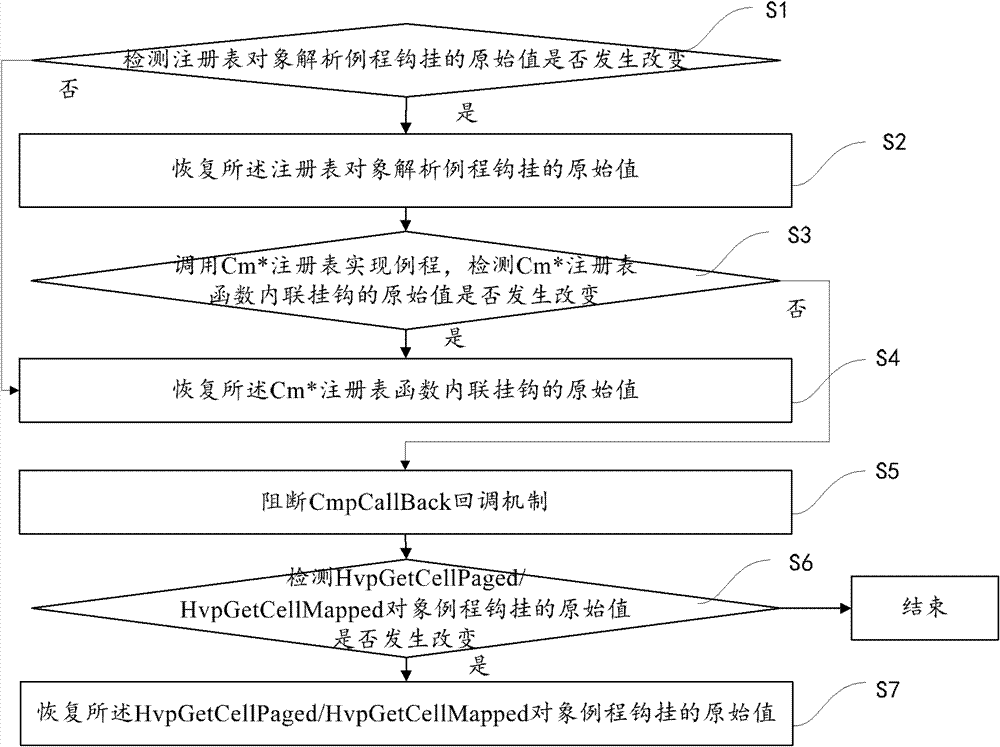
Execution method and device for registry operation
ActiveCN102779030AAvoid the potential for incompatibilitiesEnhanced confrontation abilityComputer security arrangementsSpecific program execution arrangementsSecurity softwareWindows Registry
The invention provides an execution method for registry operation, which comprises the steps that a registry operation request is acquired, wherein the request comprises a caller input parameter; kernel executing logics of a registry are set according to the caller input parameter, wherein the kernel executing logics include a tampering point detecting and restoring logic and a registry function calling logic; the tampering point detecting and restoring logic is executed, more specifically, a preset kernel executing flow tampering point is detected, and the original value of the kernel executing flow tampering point is restored when the original value of the kernel executing flow tampering point is changed; and a corresponding registry function is called by the registry function calling logic. According to the method and the device disclosed by the invention, the counterforce of defending a driving stage malicious program can be enhanced, and potential possibility of incompatibility of security software caused by registry operation interference is avoided.
Owner:三六零数字安全科技集团有限公司
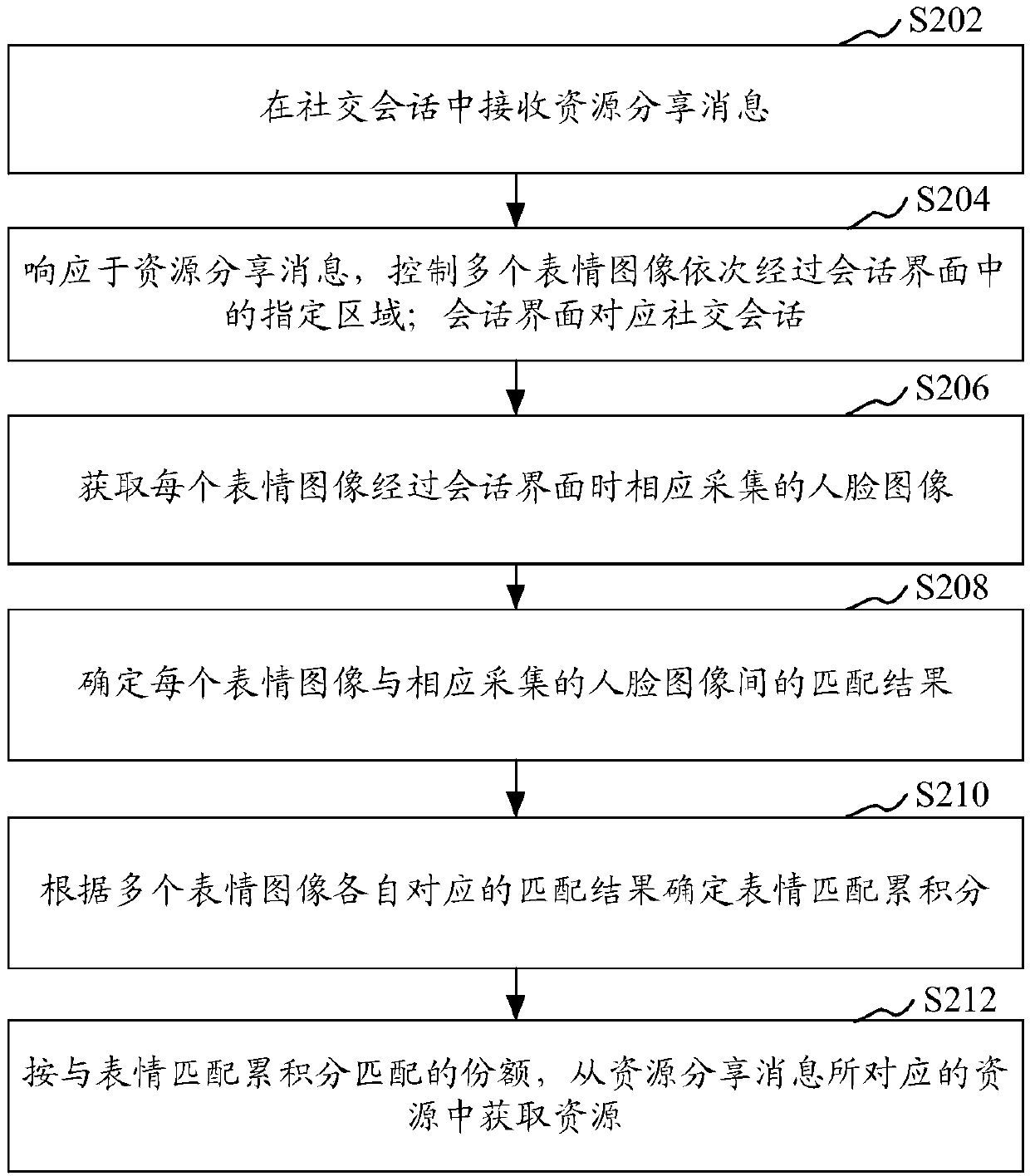
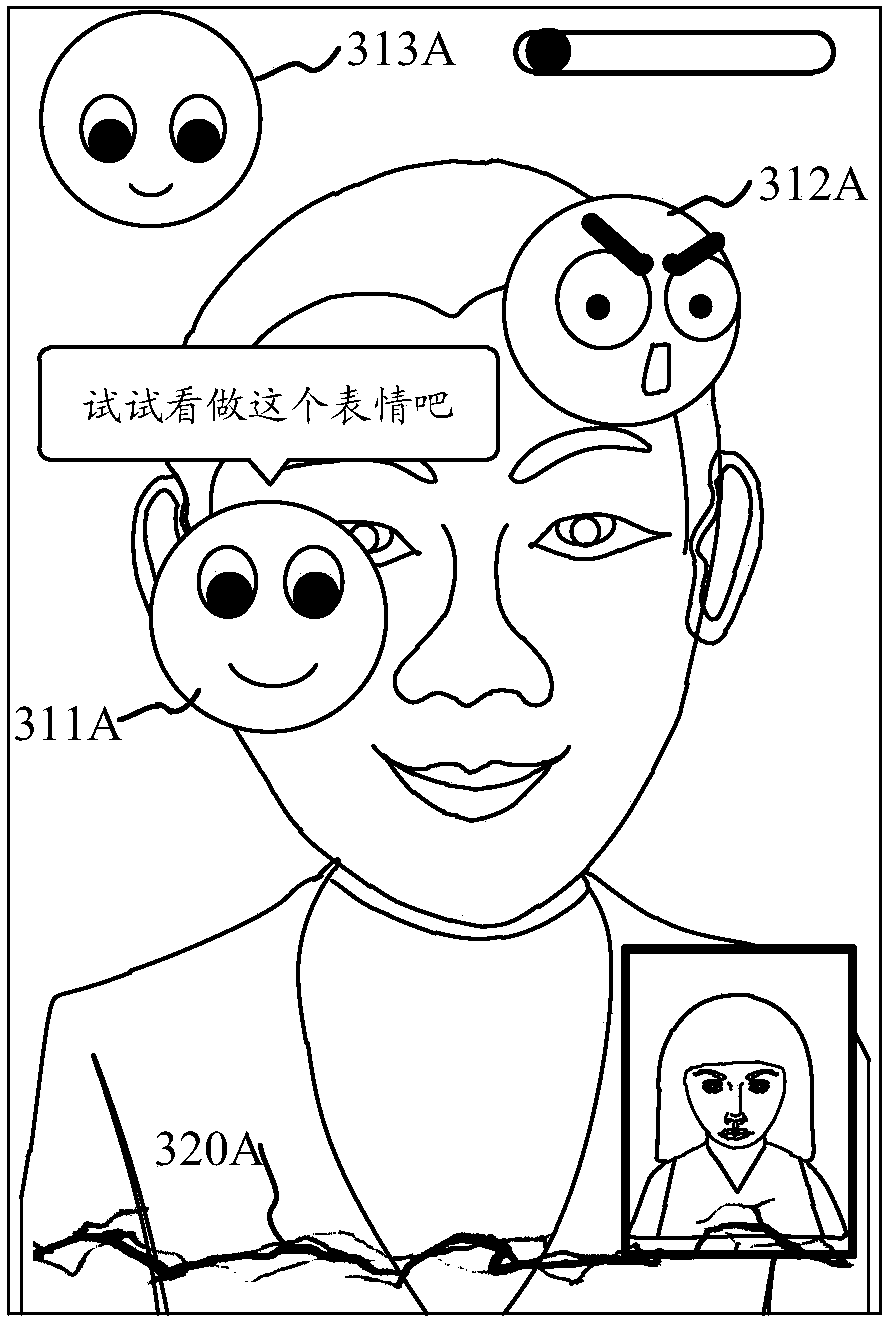
Resource acquisition method and device, resource sharing method and device, resource processing method and device, storage medium and equipment
ActiveCN109858215AEnhanced confrontation abilityCharacter and pattern recognitionDigital data authenticationCountermeasureDistributed computing
The invention relates to a resource acquisition method and device, a resource sharing method and device, a resource processing method and device, a storage medium and equipment. The resource acquisition method comprises the following steps: receiving a resource sharing message in a social session; in response to the resource sharing message, controlling a plurality of expression images to sequentially pass through a designated area in a session interface; wherein the session interface corresponds to the social session; obtaining a face image correspondingly collected when each expression imagepasses through the session interface; determining a matching result between each expression image and a corresponding collected face image; determining expression matching cumulative scores accordingto matching results corresponding to the plurality of expression images; and obtaining resources from the resources corresponding to the resource sharing message according to the share matched with the expression matching accumulation score. According to the scheme provided by the invention, the countermeasure capability of the external user is greatly improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
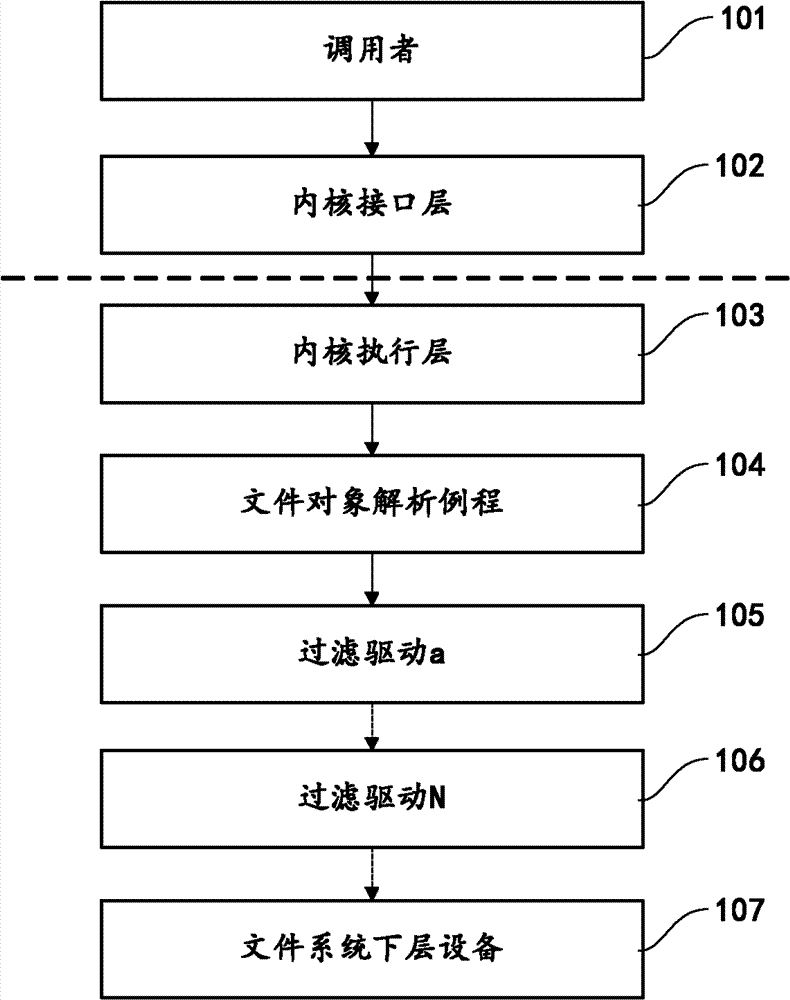
Method and device for carrying out file operation
ActiveCN102779244AFight against hijackingAvoid the potential for incompatibilitiesComputer security arrangementsFile systemComputer science
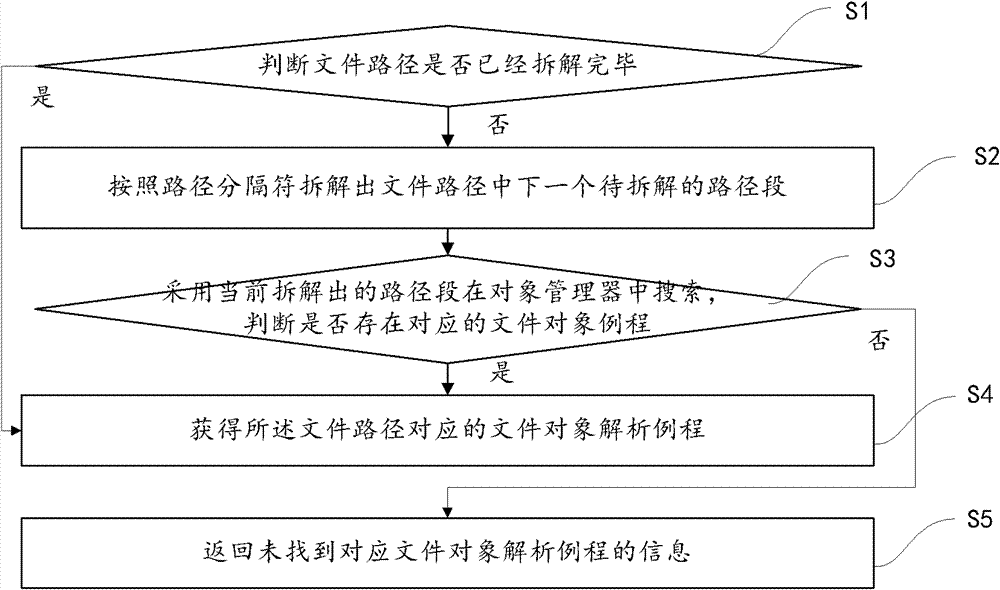
The invention provides a method for carrying out a file operation. The method comprises the following steps of: acquiring a file operation request including invoker input parameter, wherein the input parameter comprises file paths; searching a relative file object analysis routine in an object manager according to the file path; generating an I / O request packets according to the file object analysis routine if the relative file object analysis routine is found out, and transmitting the packets to an original address of the lower layer device of the preset file system. The method in the invention can increase and drive the counterforce capability of a rogue program and avoid potential probability of incompatibility among safe software due to interference of file operation.
Owner:BEIJING QIHOO TECH CO LTD
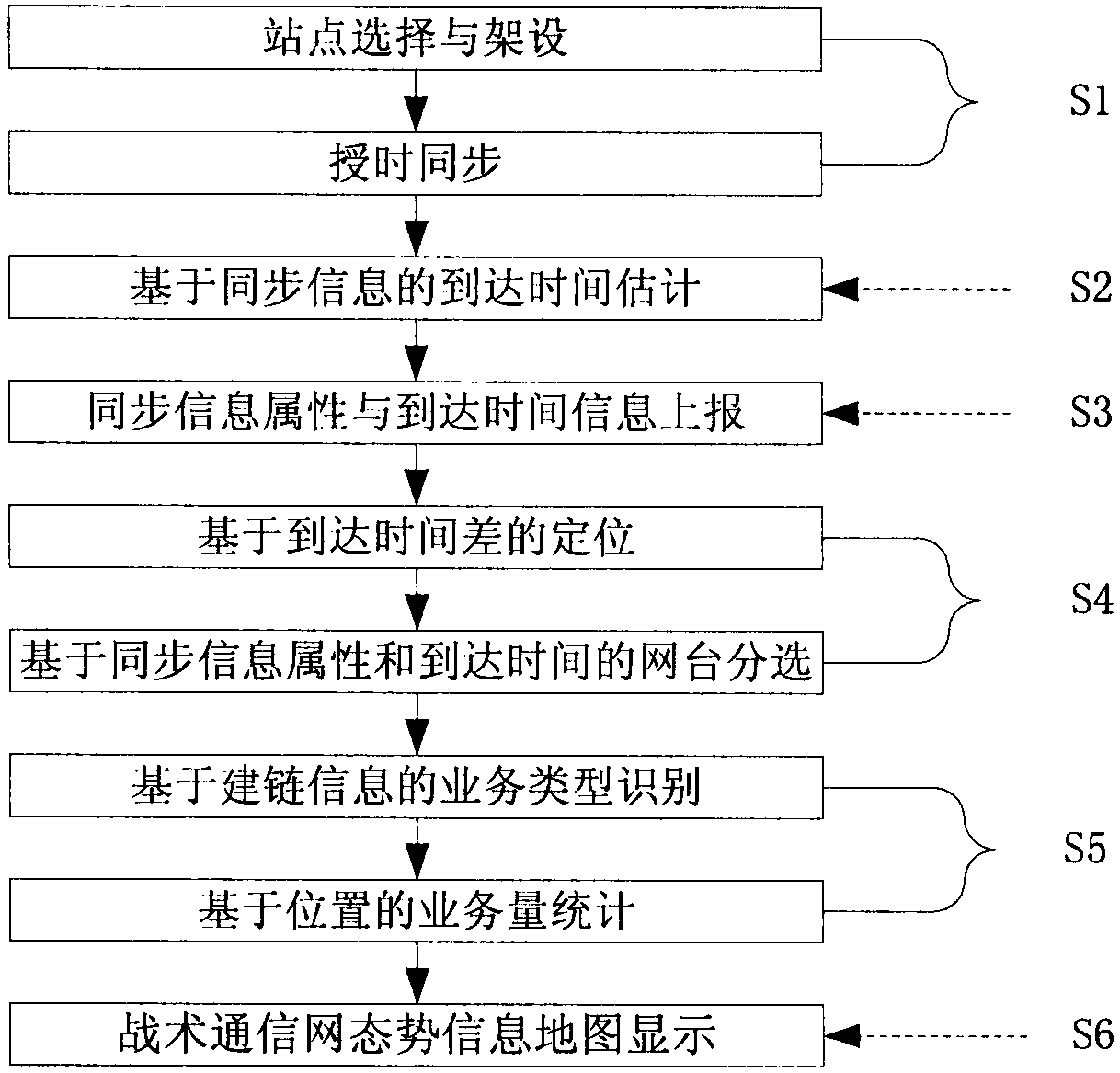
Tactical communication network countermeasure method based on signal recognition and network reconnaissance
InactiveCN109286945AAvoid the problem of not being "realistic"Guaranteed SNRSynchronisation arrangementNetwork traffic/resource managementTactical communicationsDecoy
The invention provides a tactical communication network countermeasure method based on signal recognition and network reconnaissance. The method comprises the steps of tactical communication network comprehensive situation awareness, tactical communication target attribute recognition based on time-frequency-space characteristics, detection of the specific tactical communication target based on synchronization characteristics, time-division multi-target jamming based on network key information and tactical communication network countermeasure based on synchronization decoy. The core of the method is to recognize the target attributes, locate the network node, analyze the traffic type and perform statistics of the traffic volume by using the signal time-frequency spatial domain characteristic and network characteristic information so as to realize communication signal recognition and network comprehensive situation analysis under the complex battlefield electromagnetic environment. Time-sharing jamming is performed by using the sparsity of the network key information for different target networks to improve the multi-target jamming capacity, and synchronization decoy jamming is performed by using the vulnerability of the synchronization mechanism to effectively counter the ad hoc encrypted communication network characterized by multi-hop routing and forwarding and high-speed frequency hopping.
Owner:BEIJING HAIGE SHENZHOU COMM TECH
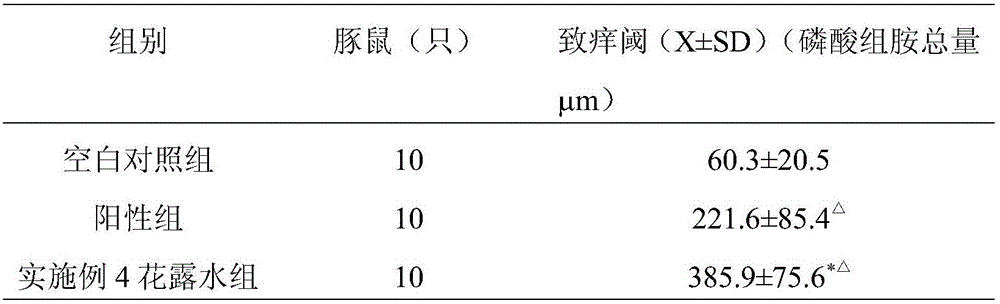
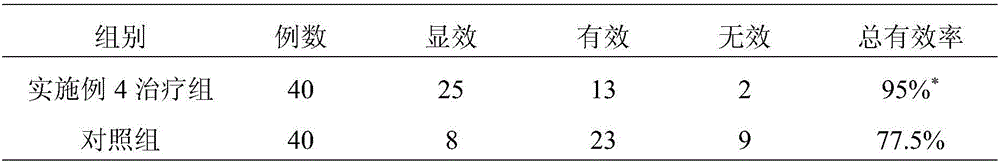
Traditional Chinese medicine composition for relieving itching and diminishing swelling after mosquito bites and preparation method thereof
ActiveCN106138241AIncrease contentRaise the itch thresholdCosmetic preparationsToilet preparationsSide effectMosquito bite
The invention discloses a traditional Chinese medicine composition for relieving itching and diminishing swelling after mosquito bites and a preparation method thereof. The composition is prepared from the following medicinal raw materials in parts by weight: 30-80 parts of astragalus membranaceus, 1-10 parts of calculus bovis, 20-60 parts of scutellariae barbatae, 30-60 parts of licorice roots, 30-70 parts of fructus kochiae, 20-60 parts of sophora flavescens, 30-60 parts of cinnamon and 20-60 parts of clove. The traditional Chinese medicine composition is scientific in prescription; and traditional Chinese medicine preparations and floral water prepared from the traditional Chinese medicine composition do not have toxic or side effect, are prepared by using purely natural formulae, and have strong pertinence. The floral water and other preparations prepared from the traditional Chinese medicine composition have a total effective rate of 95 percent, can be used for eliminating itching and heat-pain symptoms caused by mosquito bites after being applied for 5 minutes on average and eliminating swelling after 30 minutes, have reliable and rapid curative effect, can be used by adults and children, and are safe and reliable.
Owner:雷允上药业集团有限公司
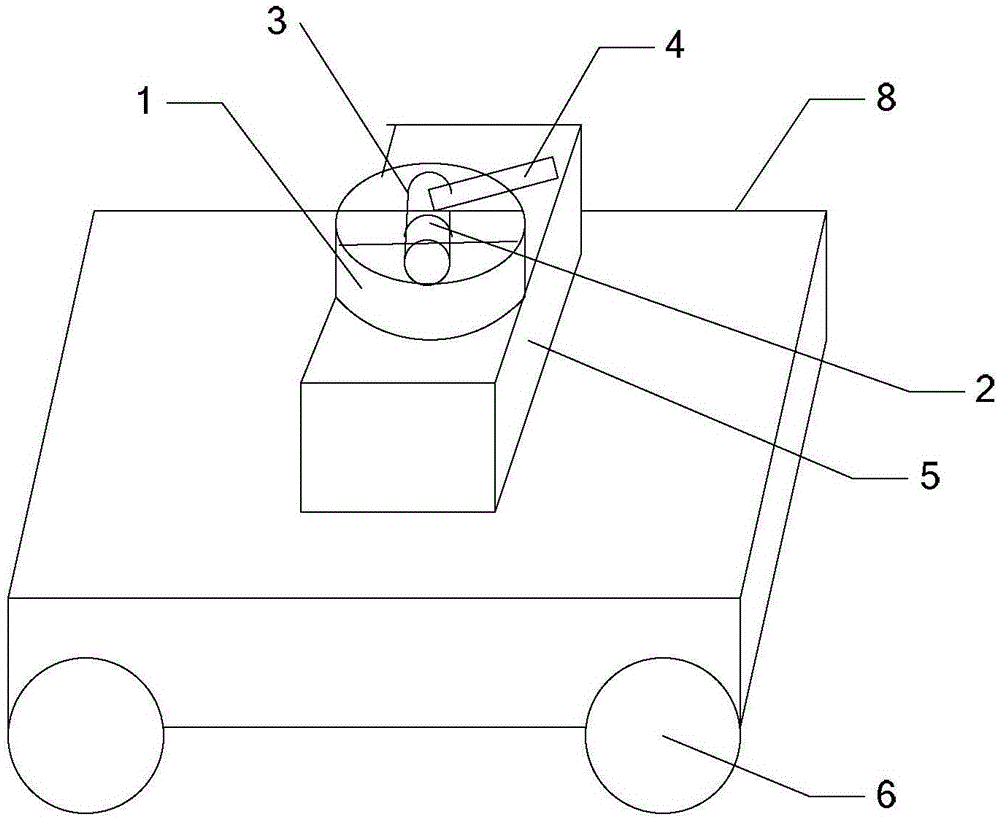
Laser shoot vehicle, and countermeasure system and countermeasure method based on vehicle
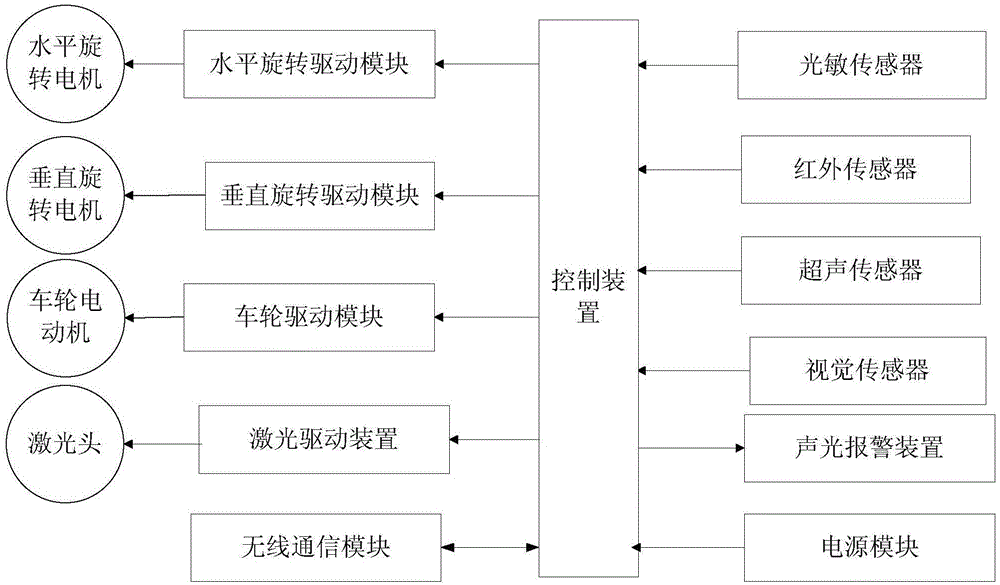
InactiveCN105137850AVersatileImprove shooting performanceProgramme control in sequence/logic controllersCountermeasureAutomatic control
The invention discloses a laser shoot vehicle, and a countermeasure system and a countermeasure method based on the vehicle, which belongs to the field of automatic control fire countermeasure robots, and aims at solving the problems of single functions and poor countermeasure in the existing intelligent vehicle. The laser shoot vehicle comprises a vehicle body, a shoot device, a walking device, a rotation device, a sensing device, a sound-light alarming device and a control device, wherein the outer wall of the front side of the vehicle body is distributed with sensors for detecting obstacles and other laser shoot vehicles in front of the vehicle body; the top part of the vehicle body is provided with a shot area and a light sensor; signals acquired by the sensing device are sent to the control device; and the control device controls the shoot device, the walking device, the rotation device and the sound-light alarming device. The laser shoot vehicle countermeasure method comprises steps: a control instruction is inputted manually to drive the laser shoot vehicle to perform moving, rotation and shooting actions or an instruction is generated through automatic operation to complete all actions. A network management module can be used for playing a role of judgment. The laser shoot vehicle, the system and the method are used in intelligent vehicle countermeasure.
Owner:HEILONGJIANG UNIV
Virtual object display method and device in virtual environment, terminal and storage medium
The invention discloses a virtual object display method and a virtual object display device in the virtual environment, a terminal and a storage medium. The method comprises the following steps: at the initial position selecting stage during game playing, displaying an initial position selecting interface, wherein the initial position selecting interface comprises m initial positions selected frompreset n initial positions; receiving a selecting instruction corresponding to a target selecting position in the m initial positions, wherein the selecting instruction is used for indicating that the initial position of a first virtual object participating in game playing is determined as the target initial position; and displaying the virtual environment, and displaying the first virtual objectat the target initial position of the virtual environment. All the virtual objects participating in game playing only can start game playing at initial positions with the limited quantity, at the earlier stage of game playing, the distribution of the virtual objects is more concentrated, so that the game playing time can be shortened, and then the occupying demand for processing resources of theterminal and the server by game playing is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Man-machine adversarial action prediction method and device, electronic equipment and storage medium
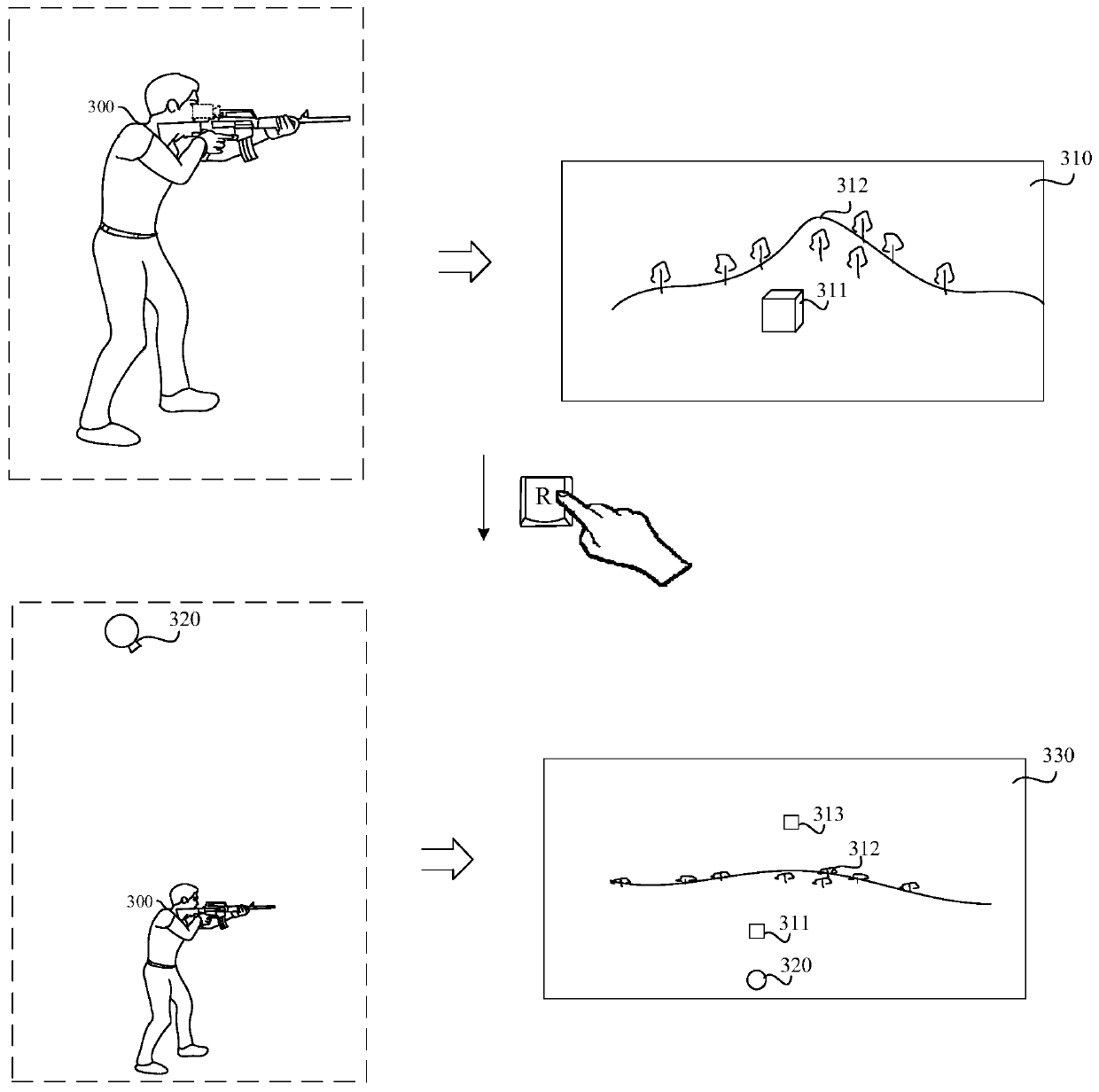
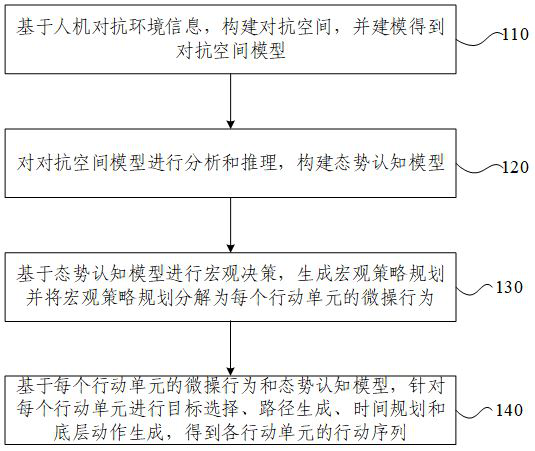
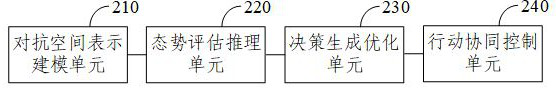
ActiveCN112633519AEnhanced confrontation abilityAbundant space for confrontationMachine learningMan machinePath generation
The invention provides a man-machine adversarial action prediction method and device, electronic equipment and a storage medium, and the method comprises the steps: constructing an adversarial space based on man-machine adversarial environment information, and carrying out the modeling to obtain an adversarial space model; analyzing and reasoning the adversarial space model to construct a situation cognition model; performing macroscopic decision based on the situation cognition model, generating a macroscopic strategy plan, and decomposing the macroscopic strategy plan into microoperation behaviors of each action unit; and on the basis of the micro-operation behavior of each action unit and the situation cognition model, performing target selection, path generation, time planning and underlying action generation on each action unit to obtain an action sequence of each action unit. According to the invention, the man-machine adversarial capability of the intelligent agent is improved.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
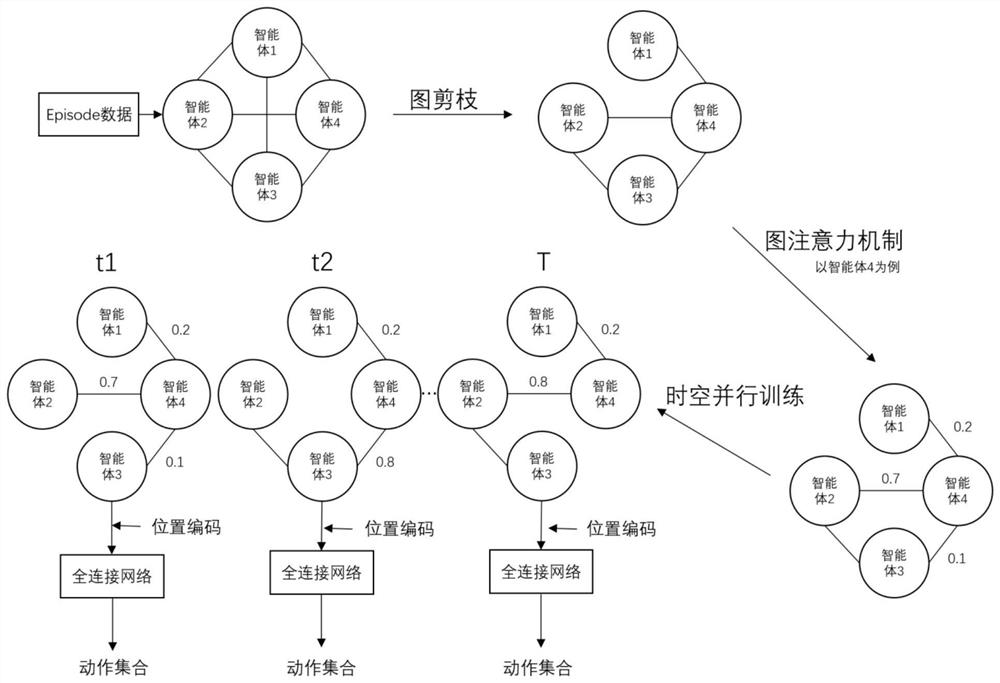
Multi-agent confrontation method and system based on dynamic graph neural network
PendingCN113627596AReal graph relationshipImprove efficiencyNeural architecturesNeural learning methodsFeature vectorMulti-agent system
The invention belongs to the field of reinforcement learning of a multi-agent system, particularly relates to a multi-agent confrontation method and system based on a dynamic graph neural network, and aims at solving the problems that an existing multi-agent model based on the graph neural network is low in training speed and low in efficiency, and much manual intervention is needed in graph construction. The method comprises the following steps: obtaining an observation vector of each agent, and carrying out linear transformation to obtain an observation feature vector; calculating a connection relationship between adjacent agents, and constructing a graph structure between the agents; carrying out embedded representation on a graph structure between the intelligent agents in combination with the observation feature vectors; performing network space-time parallel training on the action prediction result of the action network and the evaluation of the evaluation network by using the embedded representation; and performing action prediction and action evaluation in multi-agent confrontation through the trained network. According to the method, a more real graph relationship is established through pruning, space-time parallel training is realized by utilizing the full-connection neural network and position coding, the training efficiency is high, and the effect is good.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI +1
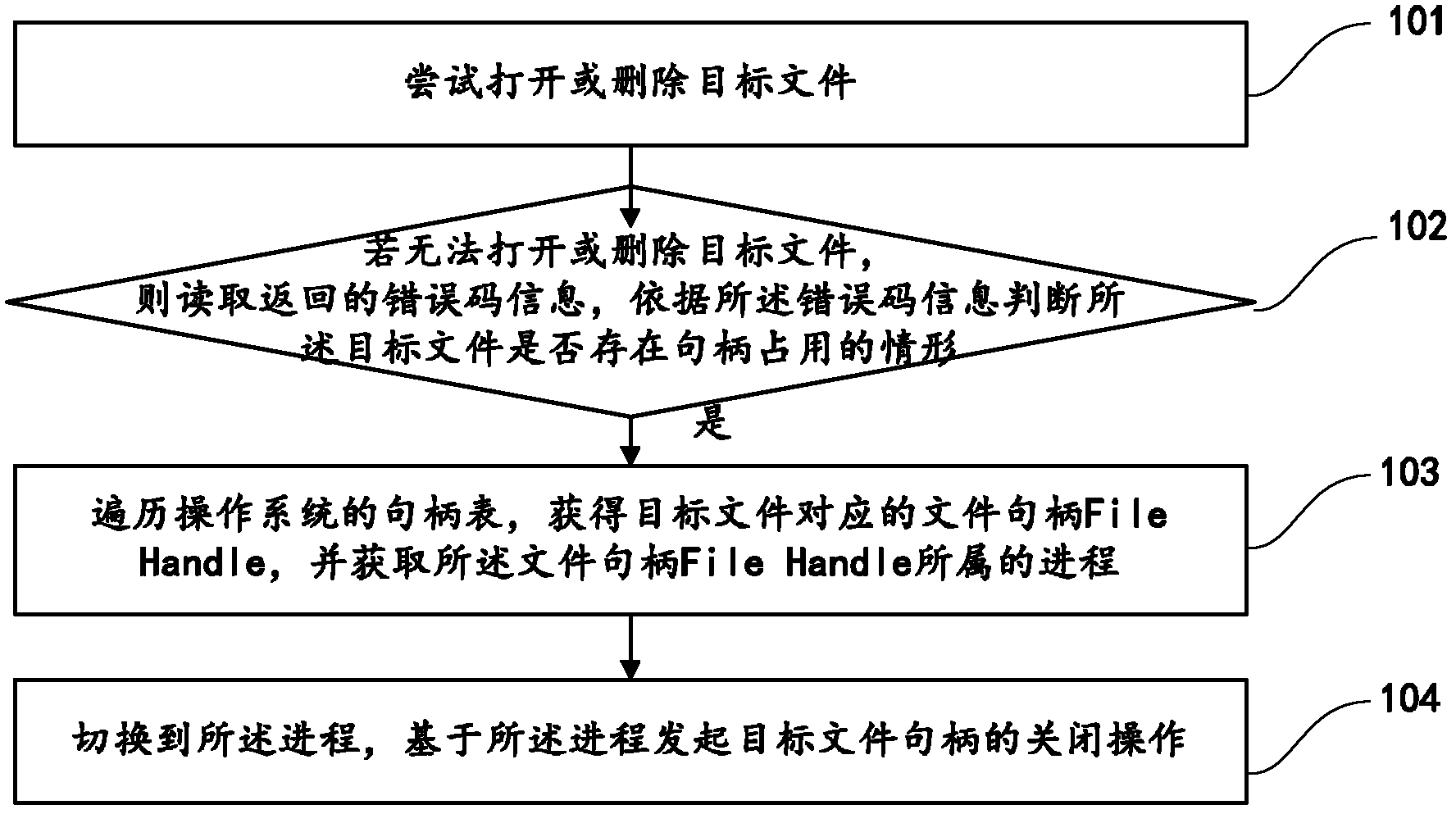
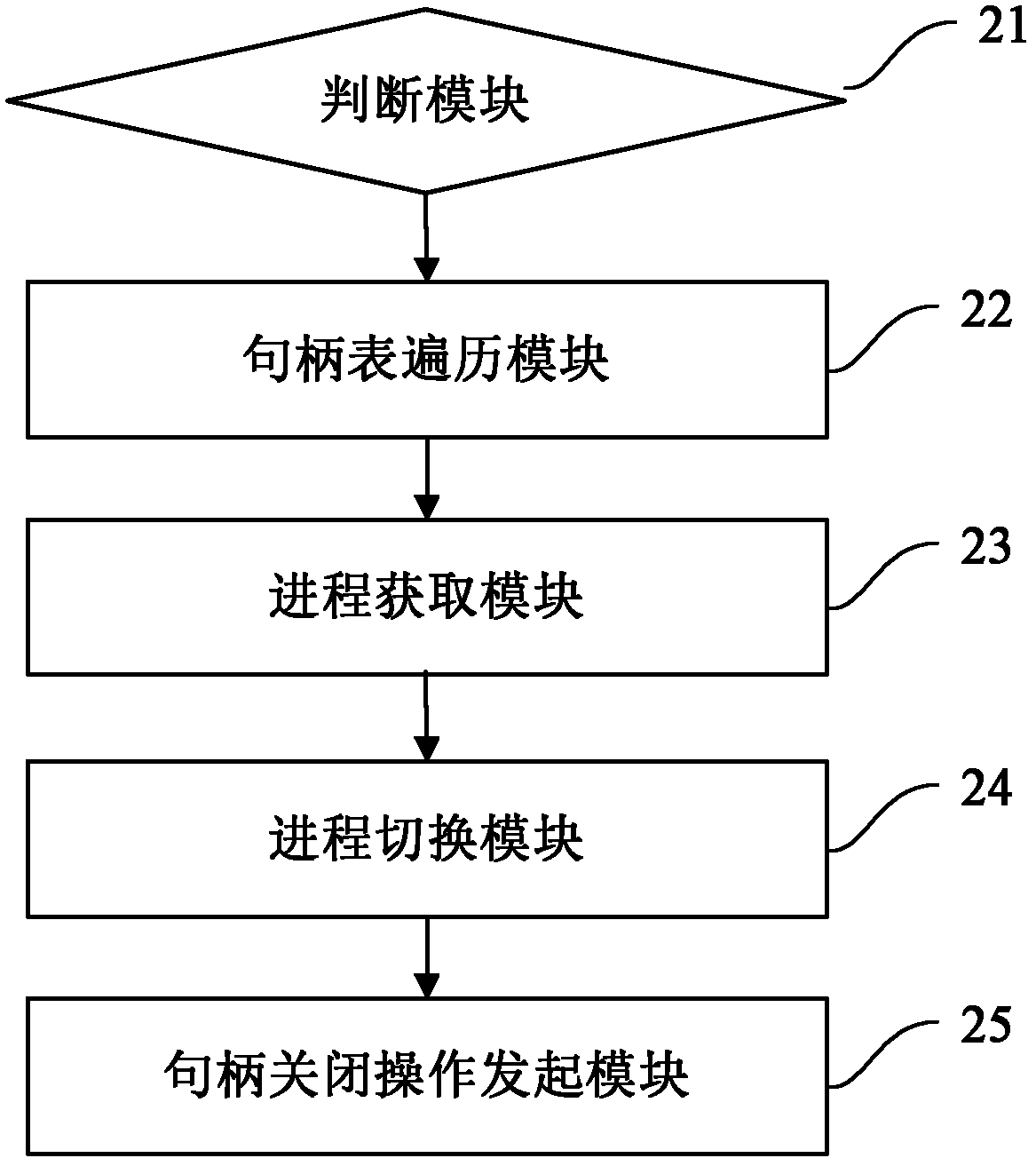
File unlocking method and device
ActiveCN102855437AAchieve unlockAchieve smashPlatform integrity maintainanceOperational systemSelf protection
The invention provides a file unlocking method and device. The method comprises the following steps of: judging whether an object file has the condition of handle occupation; if so, traversing a handle table of an operating system to obtain a file handle corresponding to the object file and obtain the process to which the file handle belongs; and switching to the process and initiating close operation of the object file handle based on the process. The file unlocking and shredding mechanism provided by the invention not only is safe and reliable and has high success rate but also can distinguish and counter the self-protection behaviors of the files with malicious programs in the complex client environments, thus enhancing the counterforce of attacking and defending the drive stage malicious programs.
Owner:360 TECH GRP CO LTD
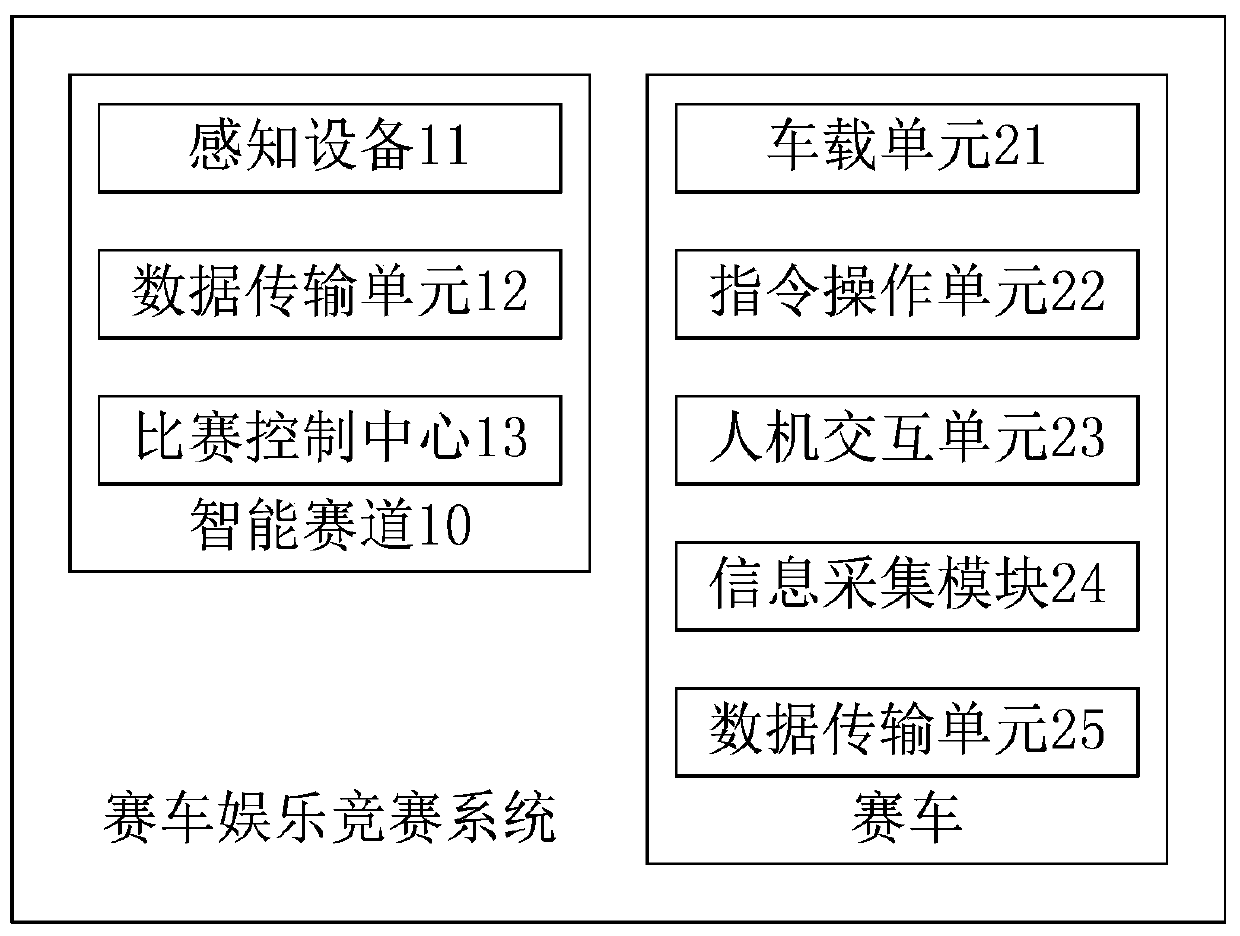
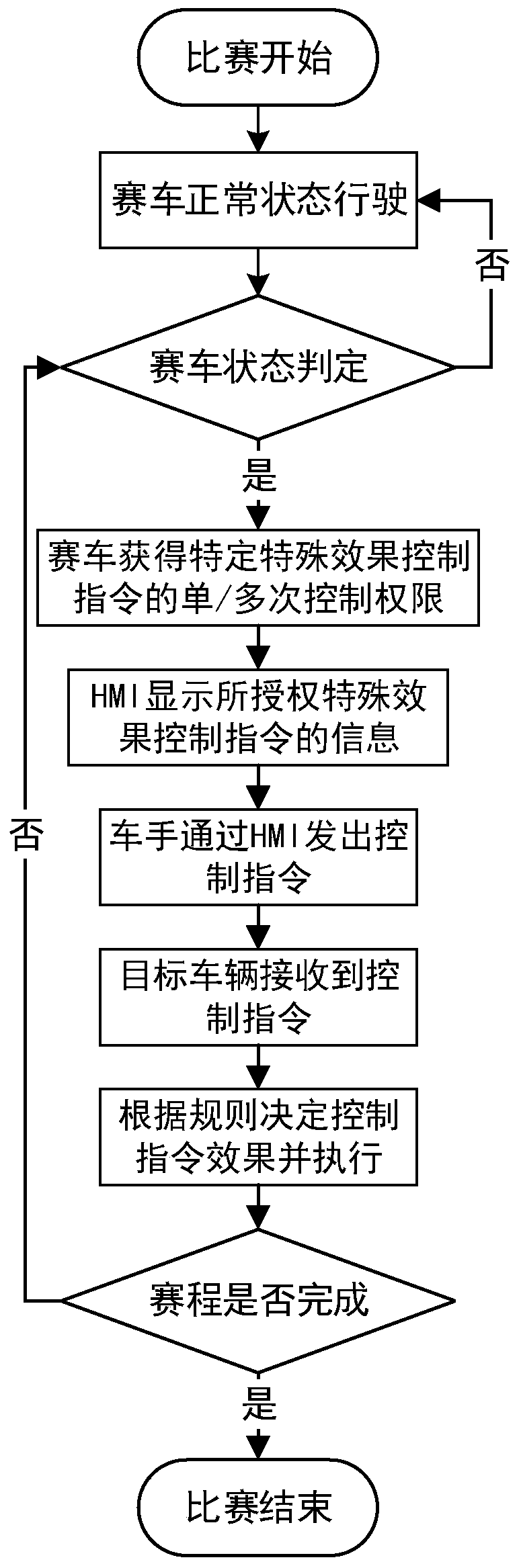
Racing vehicle entertainment competition system based on Internet of Vehicles
The application discloses a racing vehicle entertainment competition system based on the Internet of Vehicles. According to the racing vehicle entertainment competition system, a sensing device, a data transmission unit and a competition control center are arranged on an intelligent racing track. The sensing device is used for acquiring driving information when racing vehicles pass through the sensing range of the sensing device, the data transmission unit is used for sending the driving information to the competition control center, and the competition control center is used for calculating evaluation scores of the corresponding racing vehicles according to the driving information and judging that the racing vehicle with the minimum evaluation score obtains instruction control authority.The racing vehicle comprises a vehicle-mounted unit and an instruction operation unit. The instruction operation unit is used for determining a controlled racing vehicle according to a received effectselection instruction and controlling the competition control center to send a control instruction to a vehicle-mounted unit of the controlled racing vehicle according to the instruction control authority, and the vehicle-mounted unit is used for adjusting the driving state of the racing vehicle according to the received control instruction. According to the technical scheme, through the Internetof Vehicles technology, the interestingness and the resistance of racing vehicle sports are improved.
Owner:HUNAN UNIV
File unlocking method and file unlocking device
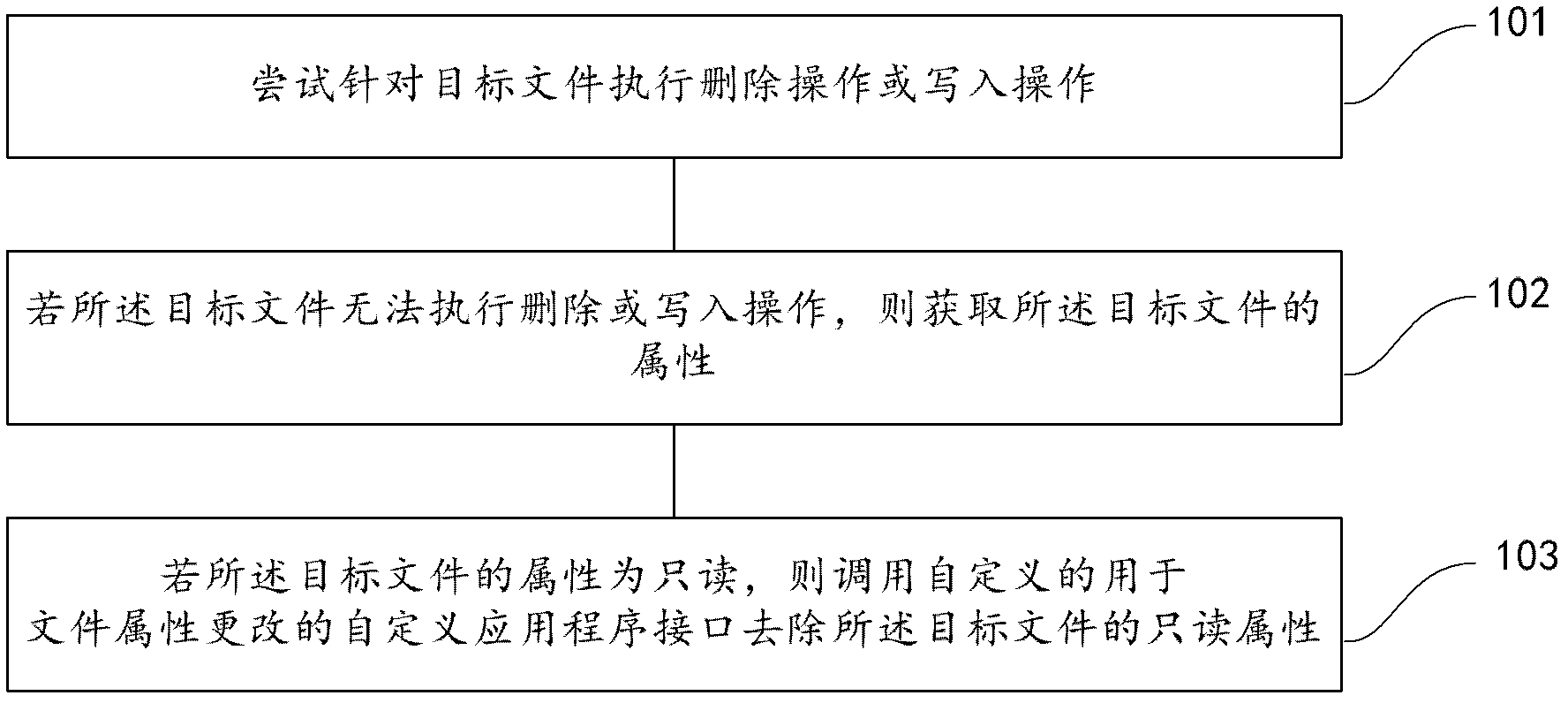
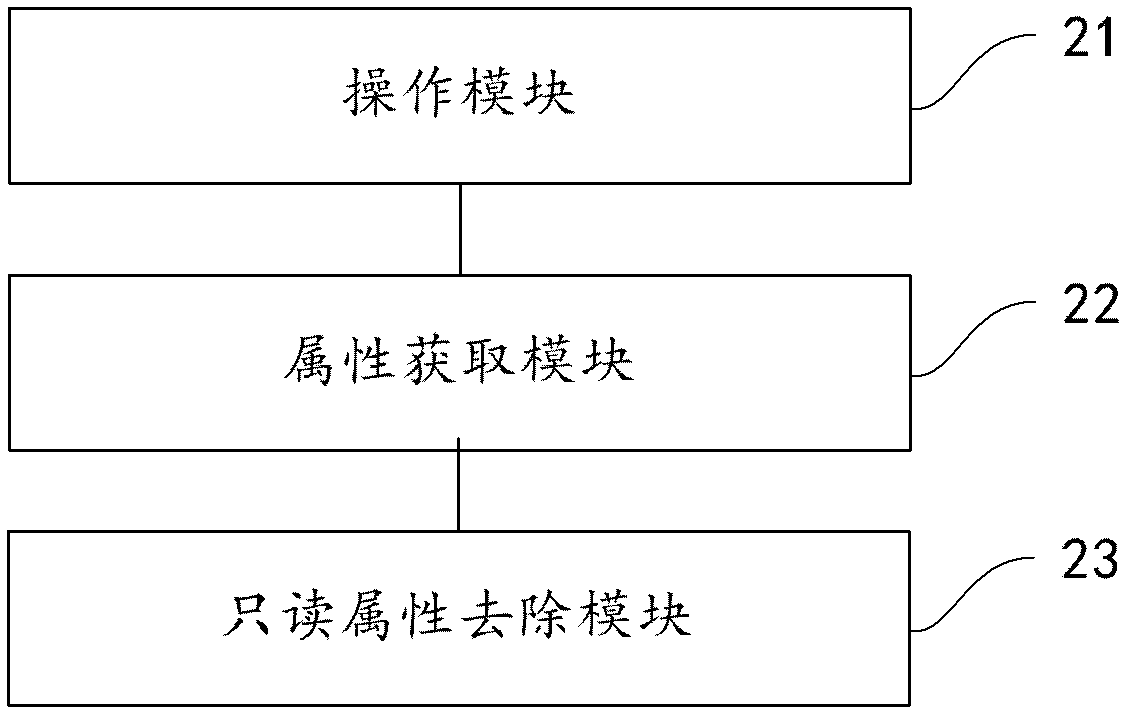
ActiveCN102855436ASafe and reliable unlockingReliable unlockPlatform integrity maintainanceClient-sideApplication software
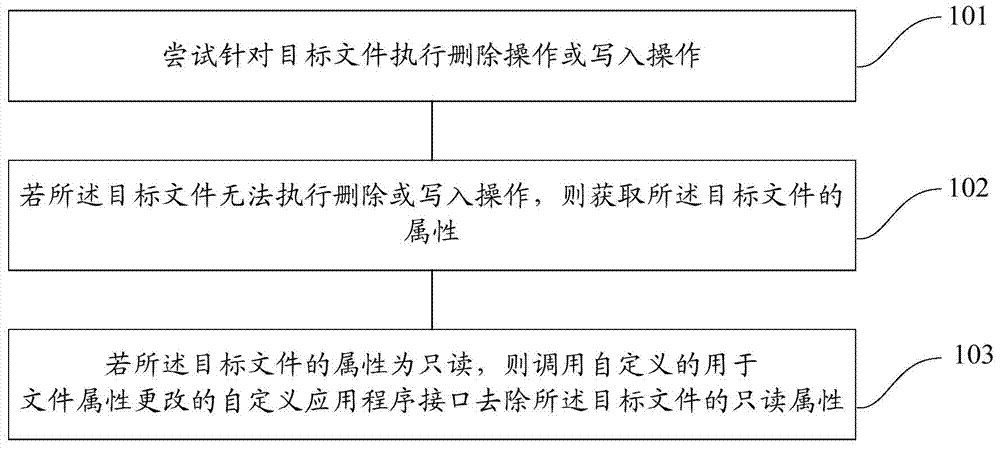
The invention provides a file unlocking method and a file unlocking device. The method includes: attempting to execute a delete operation or a write operation aiming at a target file; if the delete or write operation cannot be executed for the target file, obtaining the attribute of the target file; and if the attribute of the target file is read-only, invoking a user-defined application program interface for file attribute change to remove the read-only attribute of the target file. A file unlocking and shredding mechanism is safe, reliable and high in success rate and is capable of recognizing and confronting file self-protection behaviors of malicious programs in the complex client-side environment, and accordingly the capability of the mechanism in confronting attack and defense of the drive-level malicious programs is enhanced.
Owner:三六零数字安全科技集团有限公司
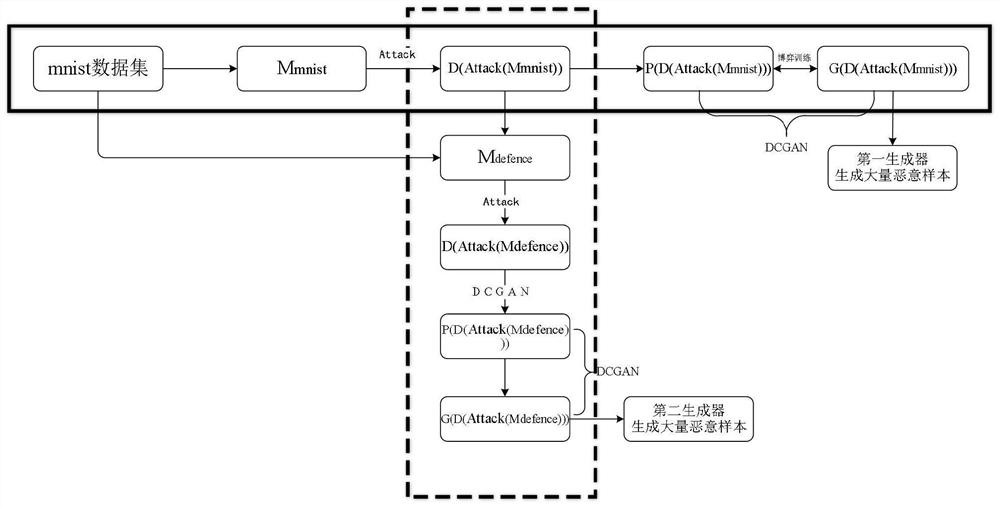
Adversarial sample generation method and system, storage medium and device
InactiveCN112116026AIncrease aggressivenessIncrease resistanceCharacter and pattern recognitionNeural architecturesEngineeringAlgorithm
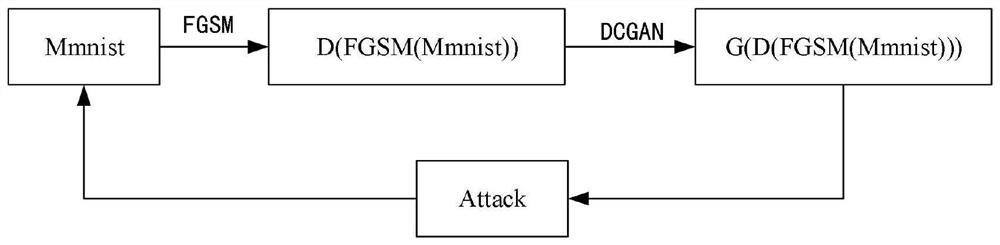
The invention discloses an adversarial sample generation method and system, a storage medium and a device. The method comprises the following steps: training a data set to obtain an initial model; attacking the initial model by using an attack algorithm, and calculating to obtain an initial adversarial sample; putting the initial adversarial sample into a first DCGAN network for training to obtaina first generator corresponding to the initial model, and generating an unprotected attack sample by the first generator; performing AND operation on the initial adversarial sample and the data set to obtain a protection model with protection adversarial capability; attacking the protection model by using an attack algorithm, and calculating to obtain a protection confrontation sample; and putting the protection confrontation sample into a second DCGAN network for training to obtain a second generator corresponding to the protection model, and generating a protection attack sample by the second generator. According to whether an original model has protection or not, a new confrontation sample generation method is provided by utilizing the GAN, and malicious samples with new features can be produced in batches.
Owner:SOUTHWEST PETROLEUM UNIV
Motion determination model training method and device for virtual object, equipment and medium
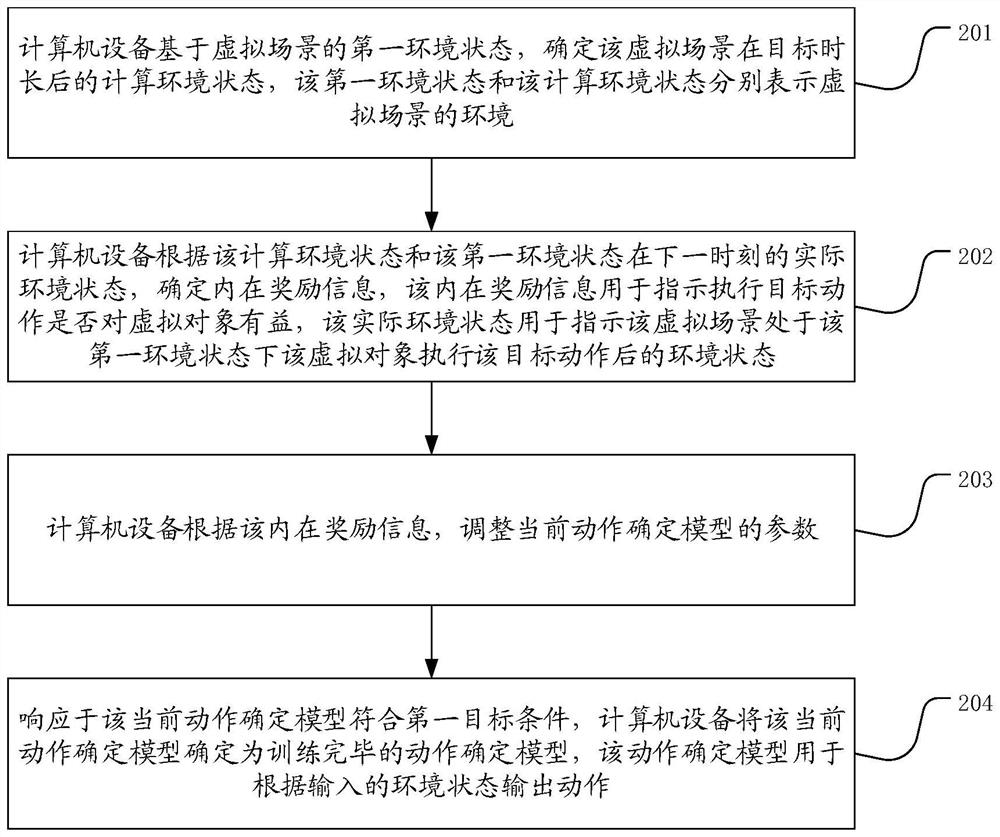
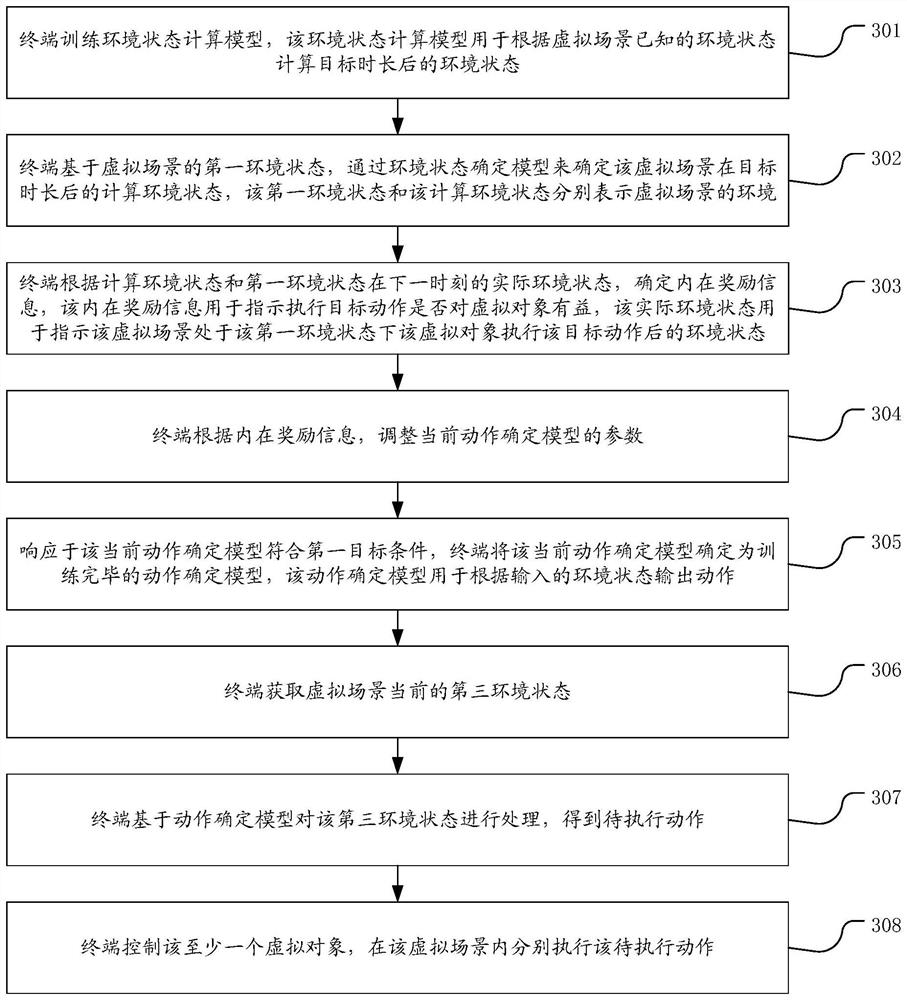
PendingCN112221140AEnhanced confrontation abilityImprove robustnessVideo gamesSimulationMachine learning
The invention provides a motion determination model training method and device for a virtual object, equipment and a medium, and belongs to the technical field of artificial intelligence. The method comprises the steps of determining a computing environment state of a virtual scene after a target duration based on a first environment state of the virtual scene; determining internal reward information according to the calculation environment state and the actual environment state of the first environment state at the next moment; adjusting parameters of the current action determination model according to the internal reward information; and in response to the fact that the current action determination model meets the first target condition, determining the current action determination modelas a trained motion determination model. According to the scheme, the motion output by the motion determination model can correspond to different game strategies, and the confrontation capacity and robustness of the virtual object on the game strategies are improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
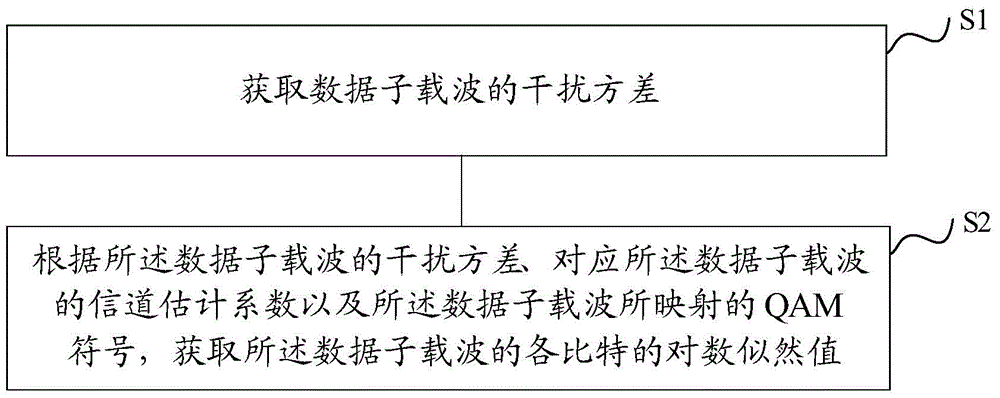
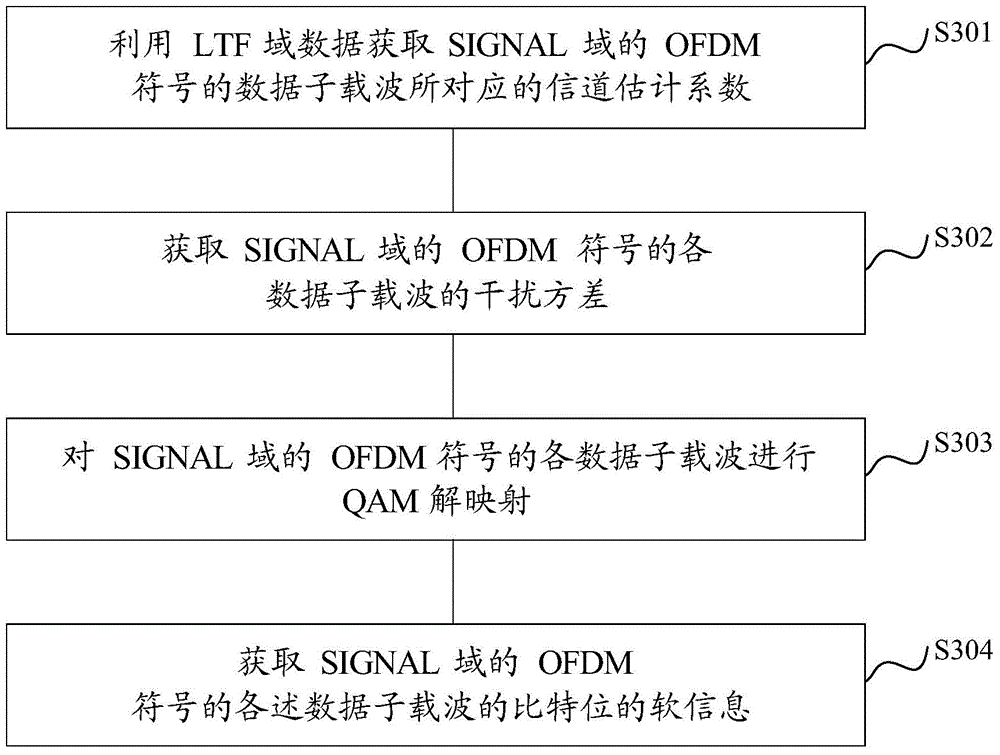
Method and device for obtaining log-likelihood ratio
ActiveCN105337918AImprove reception performanceEffective againstMulti-frequency code systemsCarrier signalLikelihood-ratio test
The invention relates to a method and device for obtaining a log-likelihood ratio, and aims to obtain log-likelihood values of various bits of a data sub-carrier in an OFDM modulation signal frame. The method comprises the following steps: obtaining an interference variance of the data sub-carrier; and obtaining the log-likelihood values of various bits of the data sub-carrier according to the interference variance of the data sub-carrier, a channel estimation coefficient corresponding to the data sub-carrier and a QAM symbol mapped by the data sub-carrier. By means of the method, same-adjacent-frequency interference signals can be effectively resistant when an OFDM signal is received; and thus, the receiving performance of a receiver can be improved.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Method and system for unlocking and deleting file and folder
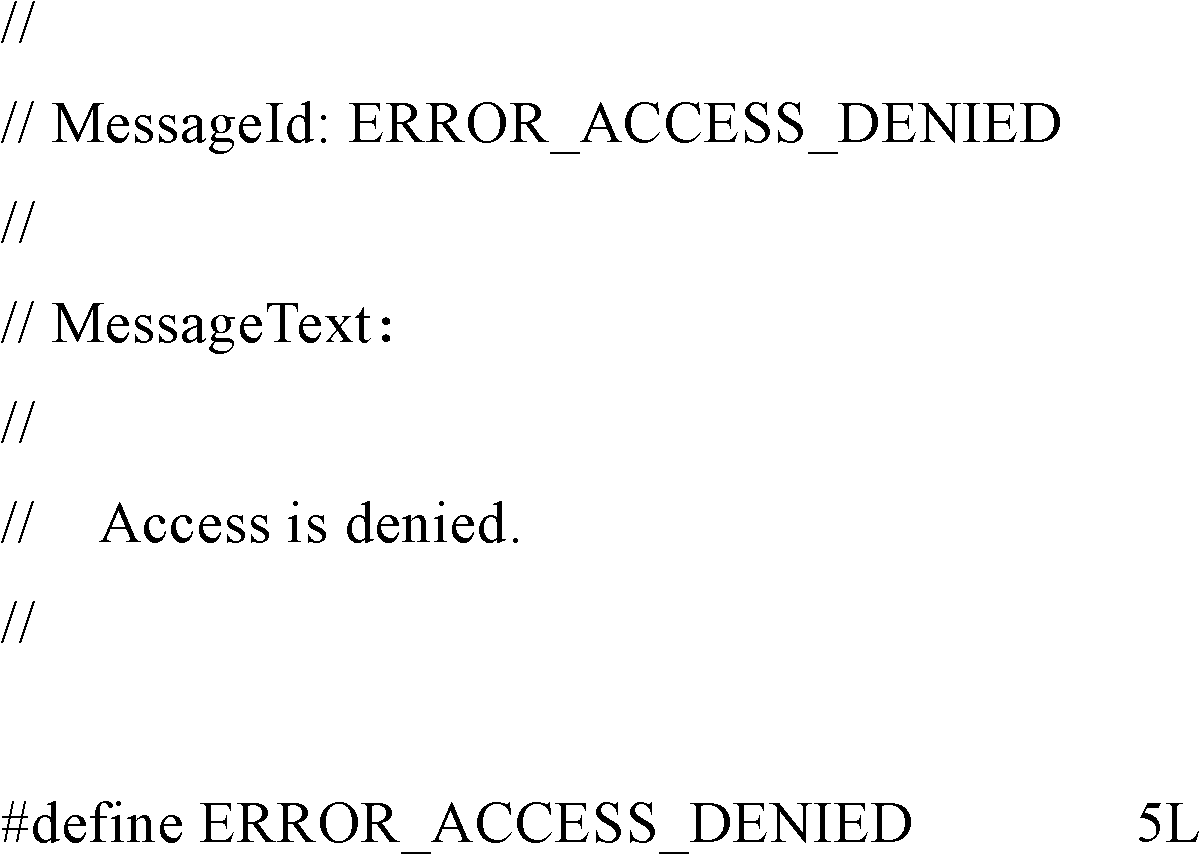
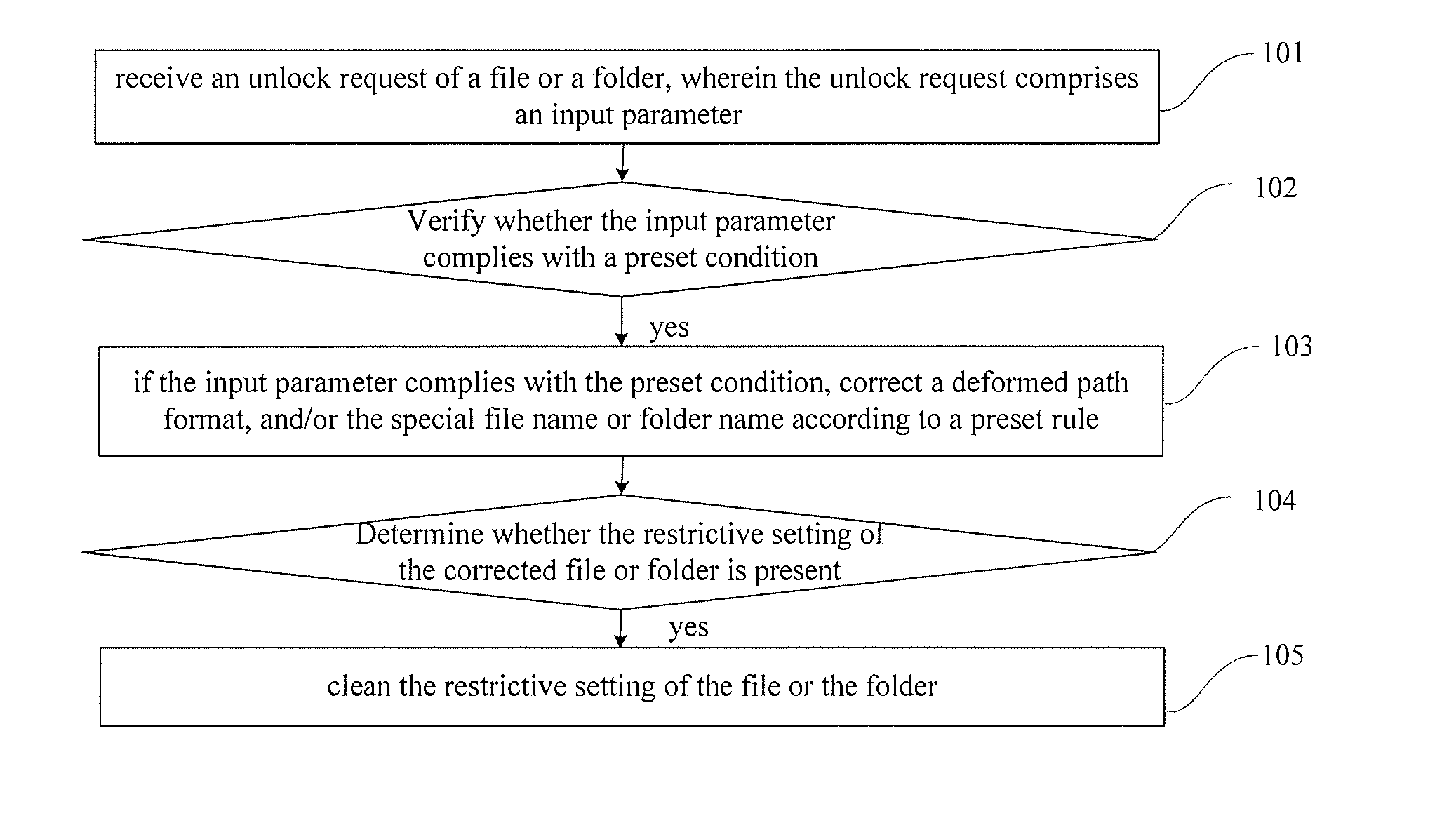
ActiveUS20140137252A1Enhanced confrontation abilityClear reference countMemory loss protectionError detection/correctionSecurity softwareVirus
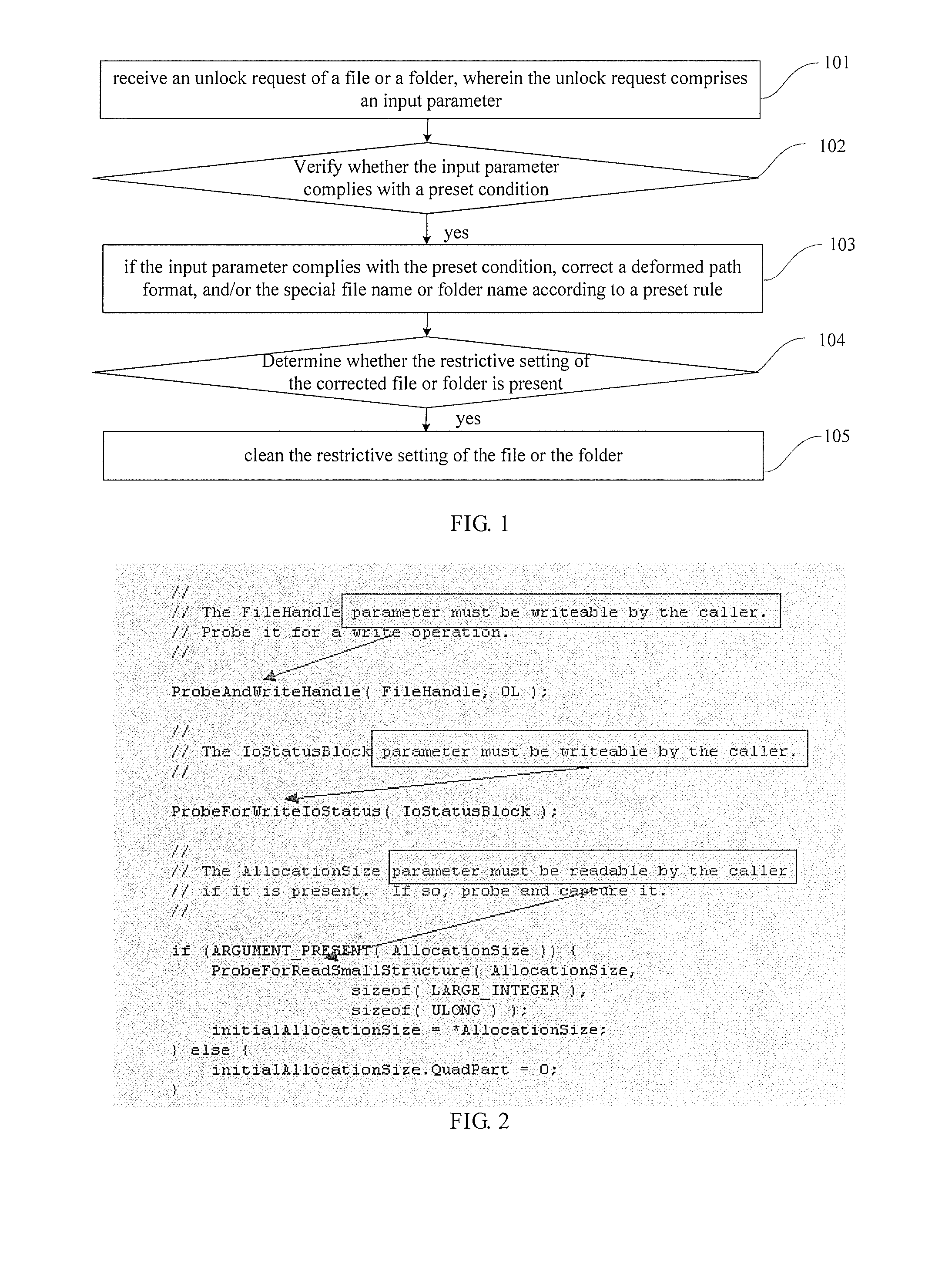
A method and system for unlocking and deleting a file or a folder. The method for unlocking the file or the folder comprises: receiving an unlock request of a file or a folder, wherein the unlock request includes an input parameter; verifying whether the input parameter complies with a preset condition; if the input parameter complies with the preset condition, correcting a deformed path format of the file or the folder and / or the special file name of the file or the special folder name of the folder according to a preset rule; determining whether restrictive setting of the corrected file or folder is present; and if yes, cleaning the restrictive setting of the file or the folder. The embodiments of the present invention relieves layer by layer the protections arranged by files infected with a virus by employing a plurality of means such as removing the read-only lock, removing the routine lock, adding the authority and closing the handle, thereby increasing the confrontation capacity of a security software against a malignant program.
Owner:BEIJING QIHOO TECH CO LTD
Method and device for unlocking file
ActiveCN104732142ASafe and reliable unlockingReliable unlockPlatform integrity maintainanceApplication softwareClient-side
The invention provides a method and device for unlocking a file. The method comprises the steps that deletion operation or write operation tries to be carried out on the target file; if the deletion or write operation cannot be executed on the target file, the attribute of the target file is obtained; if the attribute of the target file is read only, a user-defined application program interface for changing the file attribute is called to remove the read only attribute of the target file. A provided file unlocking and shredding mechanism is safe, reliable and high in success rate, a file self-protection behavior of a rogue program can be recognized in a complex client side environment and can be resisted, and the resisting capacity to the attack and defense of a driving-level rogue program is enhanced.
Owner:北京鸿享技术服务有限公司
Adversarial sample generation method and system for laser radar
InactiveCN113361565AEnhanced confrontation abilityReduce in quantityCharacter and pattern recognitionPoint cloudOriginal data
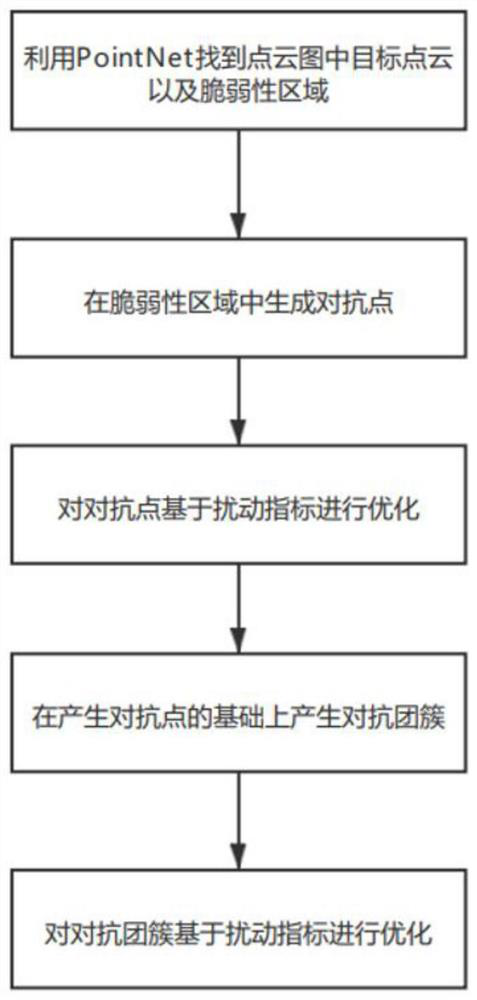
The invention discloses an adversarial sample generation method for a laser radar. The method comprises the following steps: 1) finding out a target needing to be attacked and a fragile region of the target in a point cloud picture; (2) generating independent points of antagonism in the target area in the step (1); (3) optimizing the antagonistic independent points generated in the step (2) based on a disturbance index; 4) on the basis of the step 3, generating antagonistic clusters based on the antagonistic points; and 5) optimizing the adversarial cluster generated in the step 4 based on a disturbance index, and finally generating an adversarial sample. The invention further provides a system for implementing the adversarial sample generation method for the laser radar. The system is formed by connecting a target detection and screening module, an adversarial point generation module, an adversarial point optimization module, an adversarial point cluster generation module and an adversarial cluster optimization module. The laser radar point cloud adversarial sample generated by the invention is high in confrontation, the loss is small relative to the original data, and the basic features of the original data can be better reserved.
Owner:ZHEJIANG UNIV OF TECH
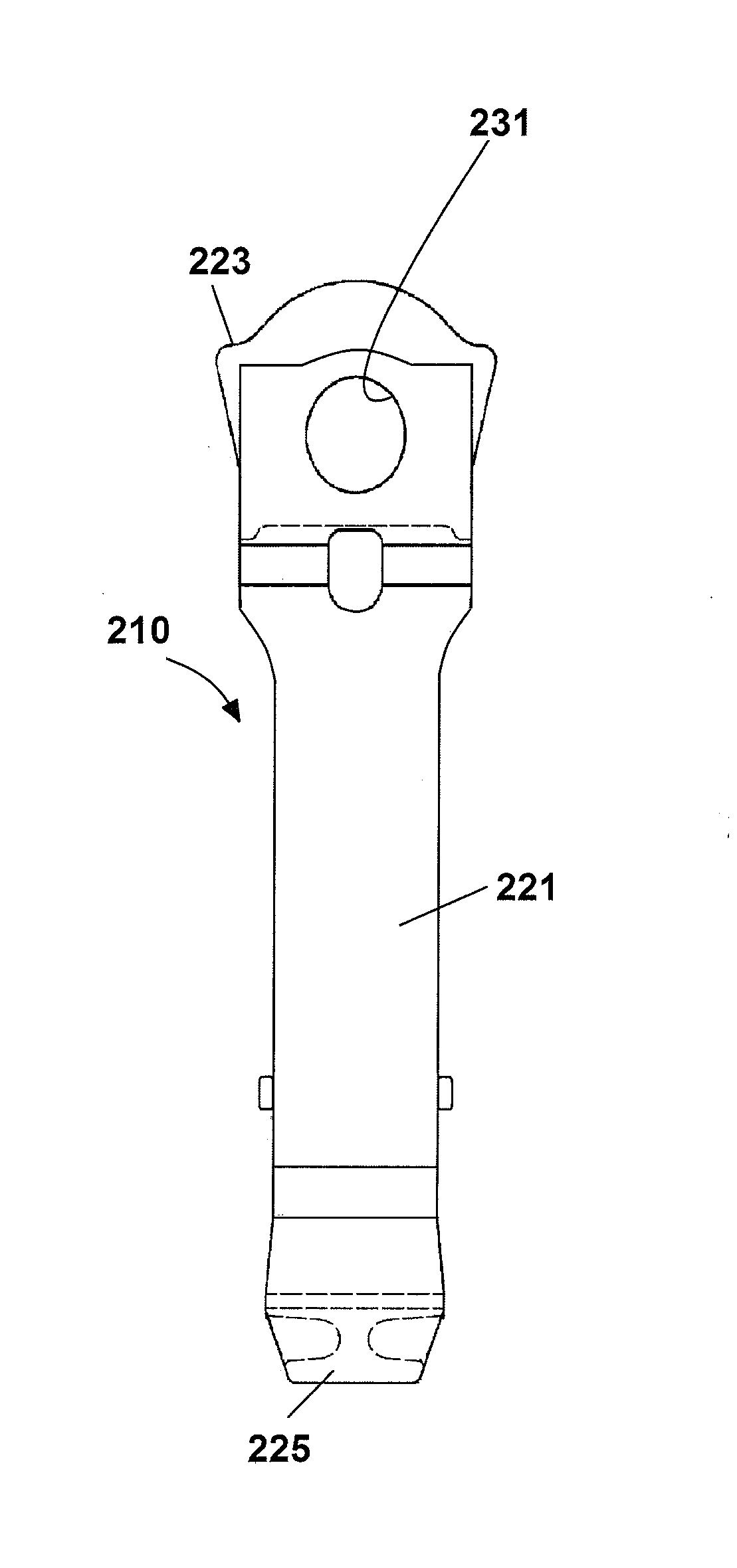
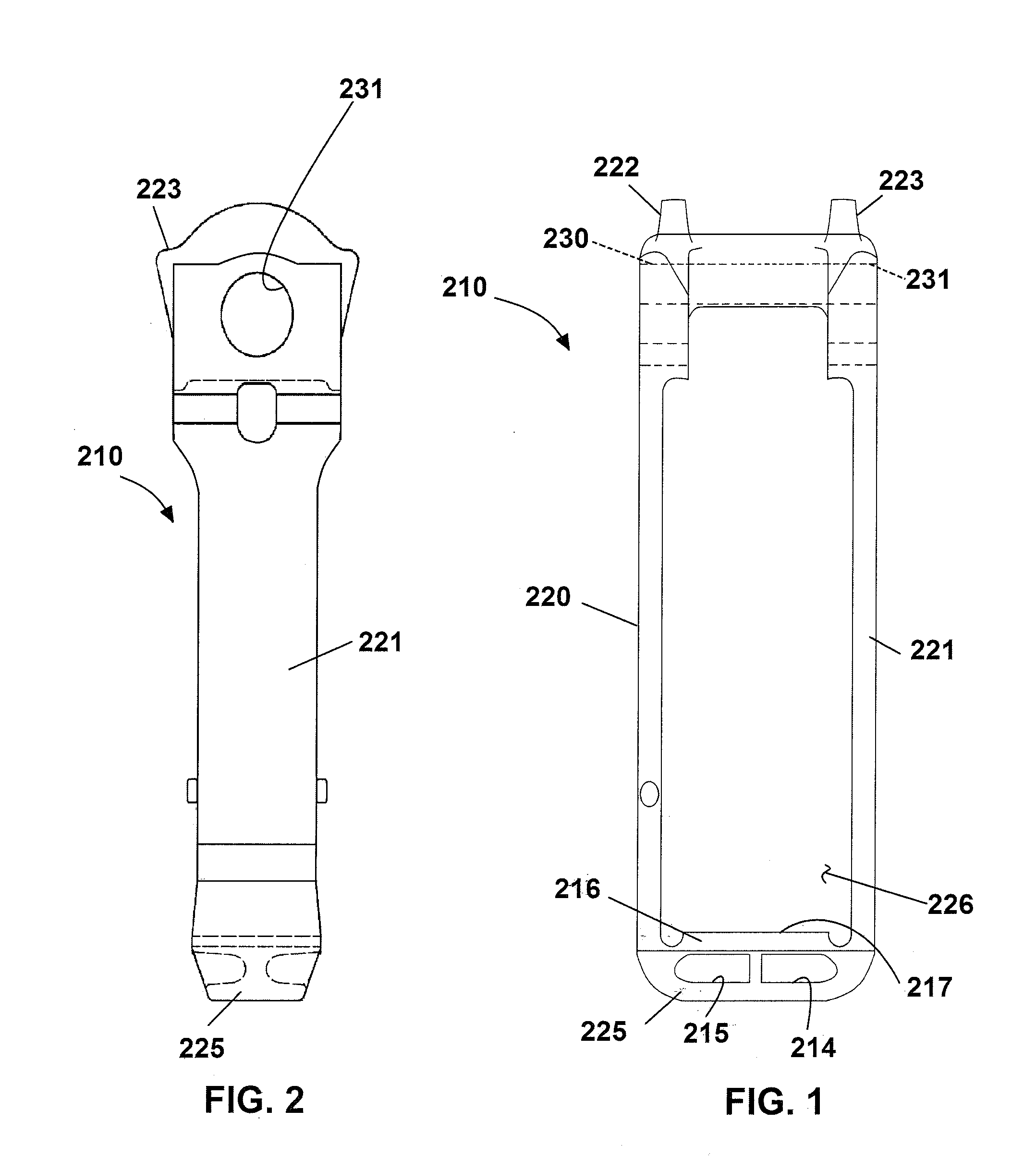
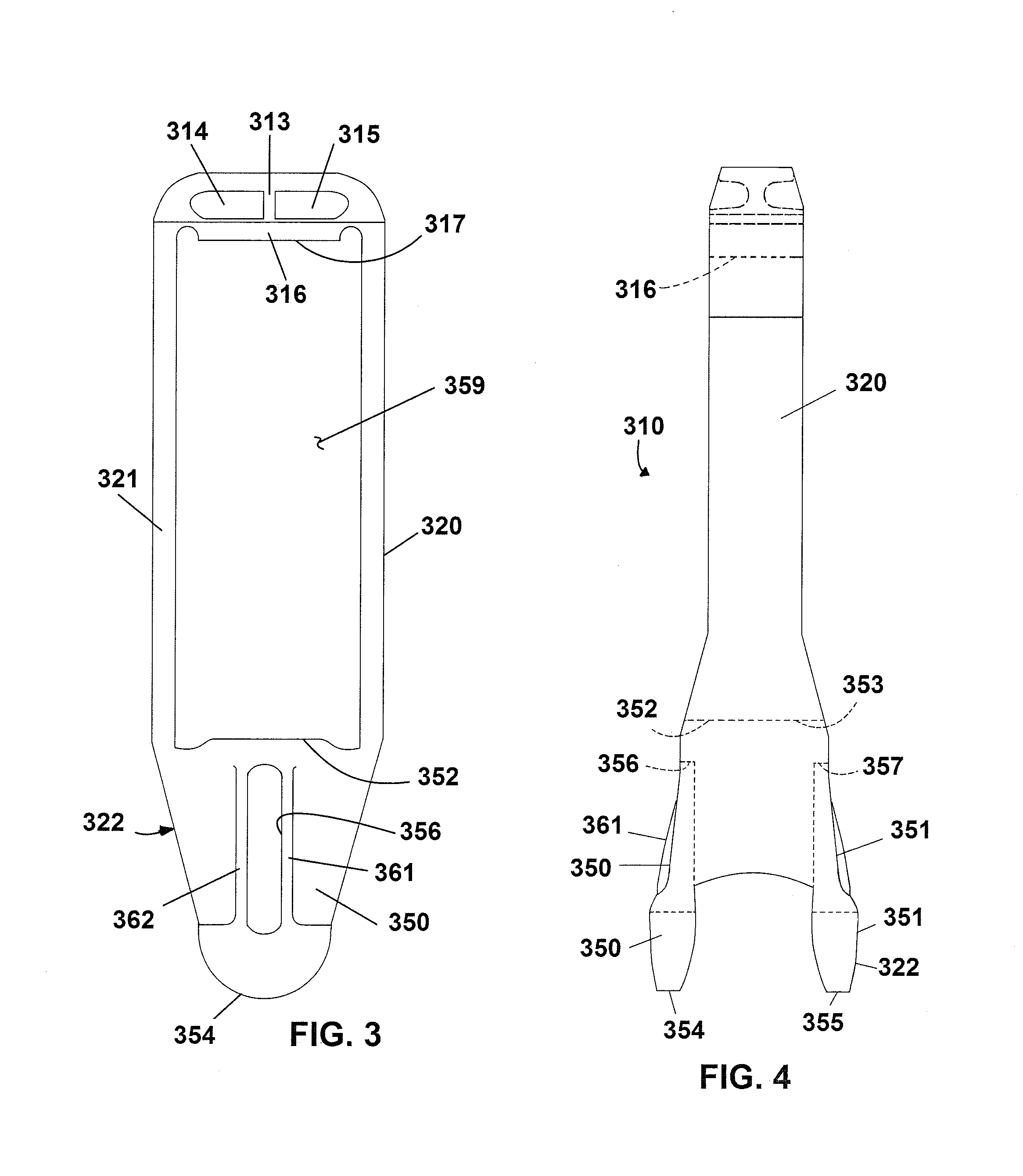
Lightweight yoke for railway coupling
ActiveUS20140360965A1Improve payload to weight ratioReduce thicknessDraw-gearRailway couplingsAustemperingCoupling
Lightweight yokes are provided. According to some embodiments, the basic overall appearance of the yoke may be maintained, but the actual material of which it is constructed is changed. According to other embodiments, the yoke is provided with an improved lightweight construction, and, yet other embodiments the yoke may be provided with an improved construction and formed from a preferred material. Yokes may be constructed from cast austempered ductile iron; whereas cast iron has a density, 0.26 lbs / in̂3, which is approximately 8% less than steel, 0.283 lbs / in̂3, thereby allowing for a reduction in weight over steel. A suitable austempering process is used to produce the austempered metal yoke. Yokes have improved configurations which may require less metal to produce the yoke. Both, the lightweight material and improvements in configuration of the yoke structure may combine to provide a lighter weight yoke.
Owner:PENNSY CORP
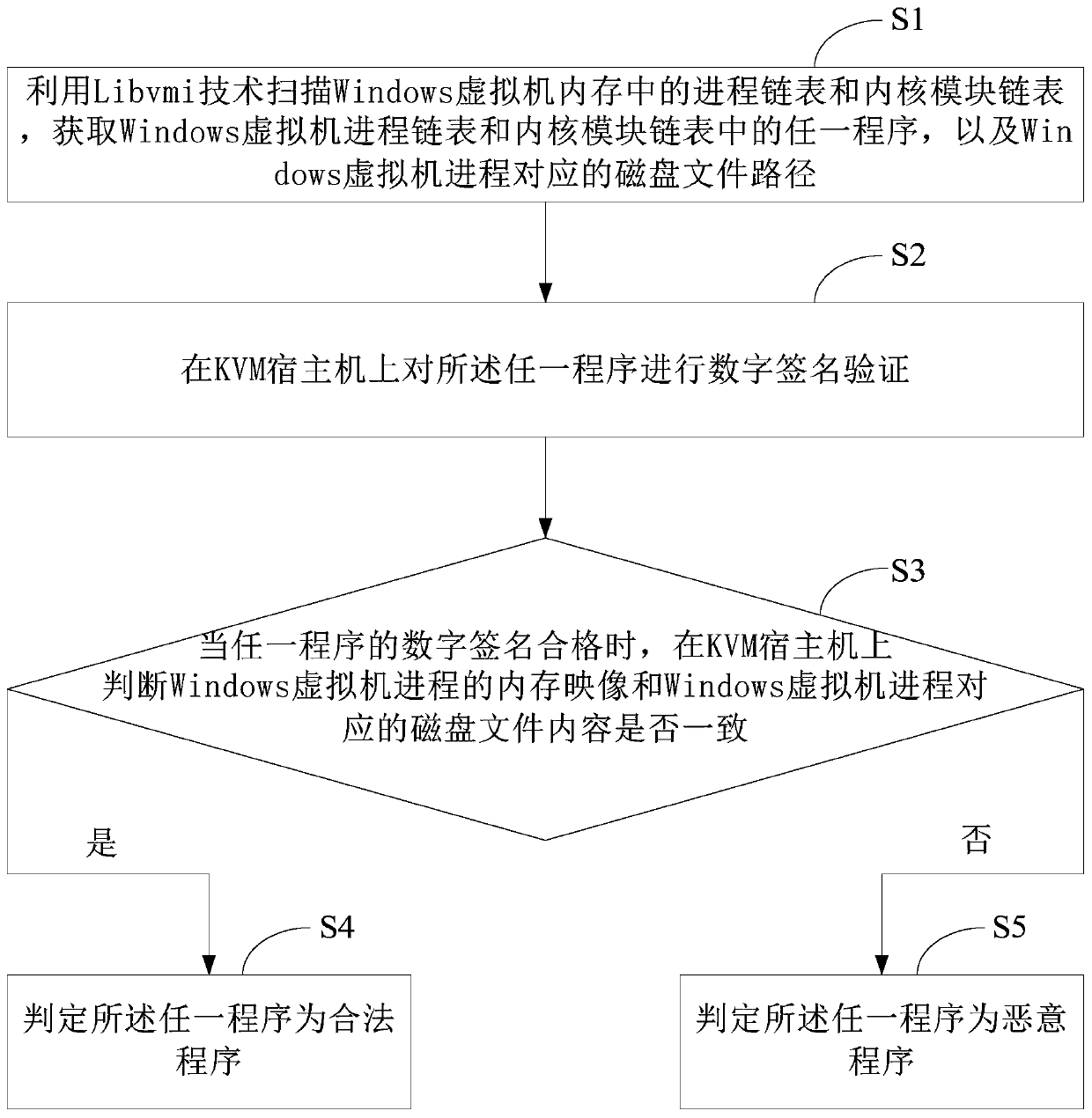
Method and system for detecting Windows malicious programs on KVM virtualization platform
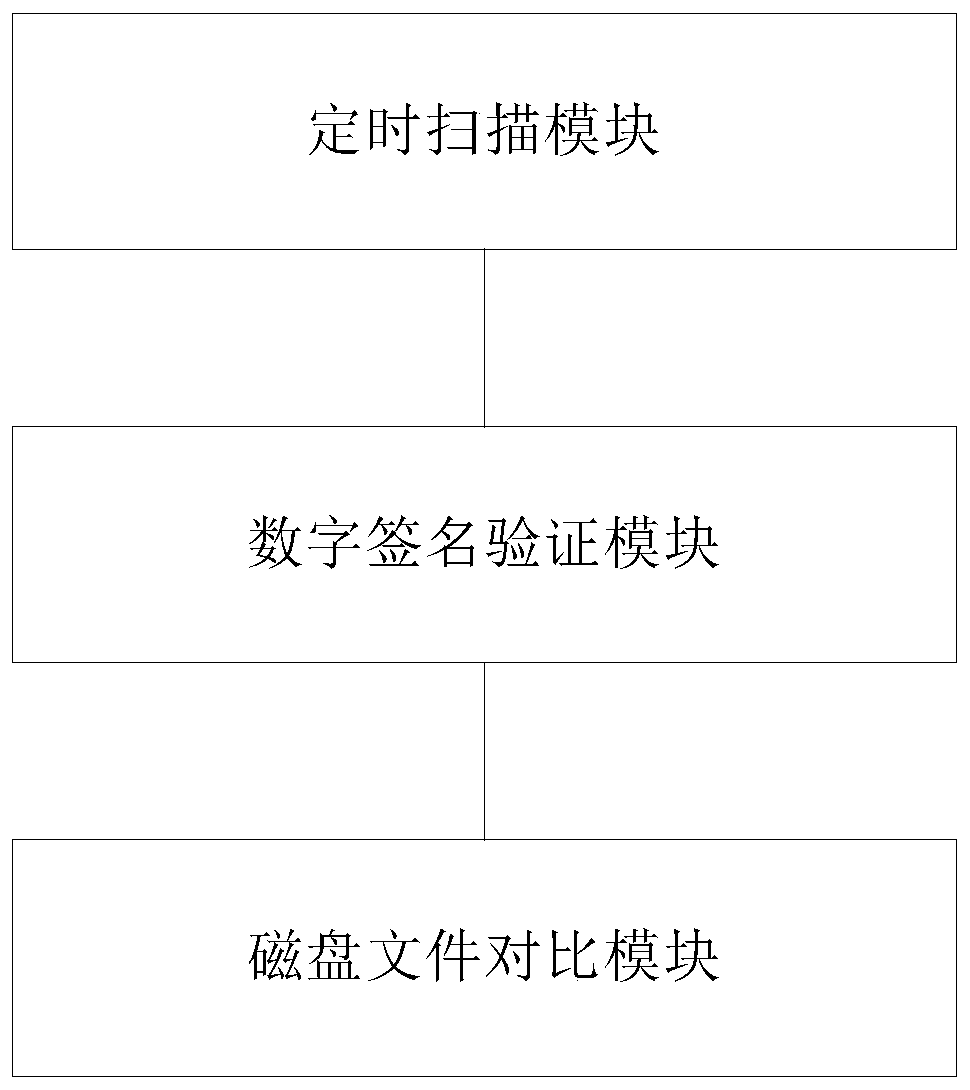
InactiveCN110362998AImprove accuracyEnhanced confrontation abilityPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationDigital signature
The invention discloses a method and system for detecting a Windows malicious program on a KVM virtualization platform. The method comprises: adopting a Libvmi technology to scan a process linked listand a kernel module linked list in a Windows virtual machine memory, and obtaining any program in the Windows virtual machine process linked list and the kernel module linked list and a disk file path corresponding to a Windows virtual machine process; performing digital signature verification on any program on the KVM host machine; when the digital signature of any program is qualified, judgingwhether the memory image of the Windows virtual machine process is consistent with the disk file content corresponding to the Windows virtual machine process or not on the KVM host machine; and if so,determining that any program is a legal program, otherwise, determining that the program is a malicious program. The system comprises a scanning module, a digital signature verification module and adisk file comparison module. According to the method and the device, the resistance to the malicious programs and the accuracy of malicious program detection can be greatly improved, so that the safety and stability of a virtual machine system are improved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Game ball system
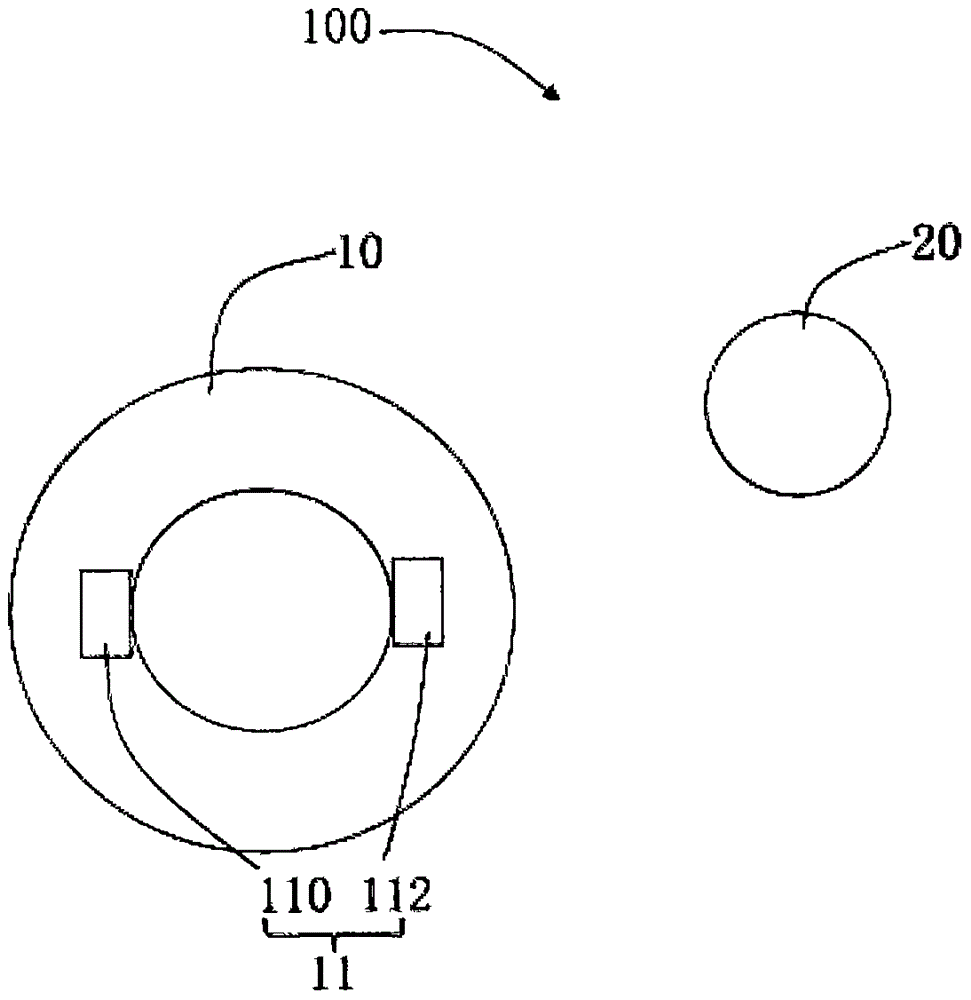
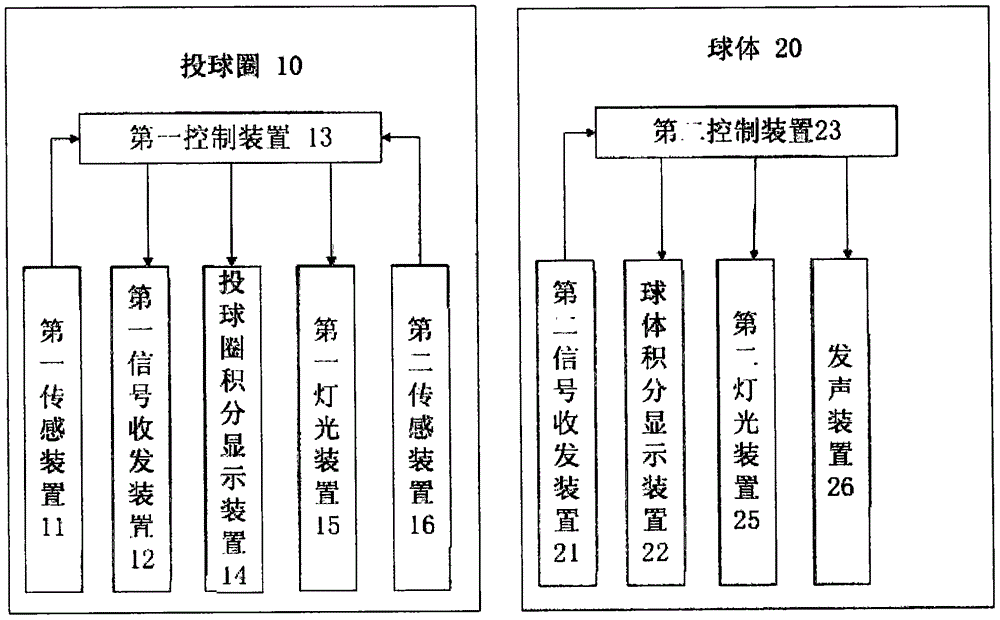
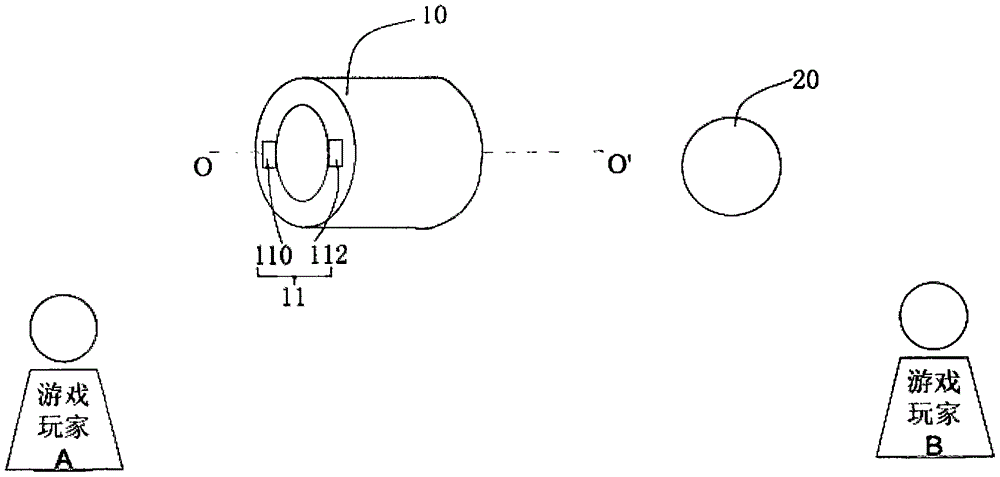
InactiveCN106039681AAdd funEnhanced confrontation abilityNon-electrical signal transmission systemsGymnastic exercisingDisplay deviceGame machine
The invention relates to a game ball system. The game ball system comprises a ball and a ball throw ring matched with the ball for use, wherein the ball throw ring is provided with a first sensing device for sensing that whether the ball passes through the ball throw ring or not; the game ball system further comprises a first signal transmitting and receiving device arranged on the ball throw ring, as well as a second signal transmitting and receiving device and a ball integral display device arranged on the ball, when the first sensing device senses that the ball passes through the ball throw ring, the first signal transmitting and receiving device sends a signal to the second signal transmitting and receiving device, and when the second signal transmitting and receiving device receives the signal from the first signal transmitting and receiving device, the ball integral display device displays the ball throw integral. While realizing the functions of the traditional shooting game machine, the game ball system also supports the automatic integration of the playing methods including one ball shooting multiple baskets, multiple balls shooting one basket, and multiple balls shooting multiple baskets, therefore, the interestingness and competition of the game are enhanced, and the diversified entertainment demands of people are satisfied.
Owner:SUZHOU GUYUEFENG INFORMATION TECH CO LTD
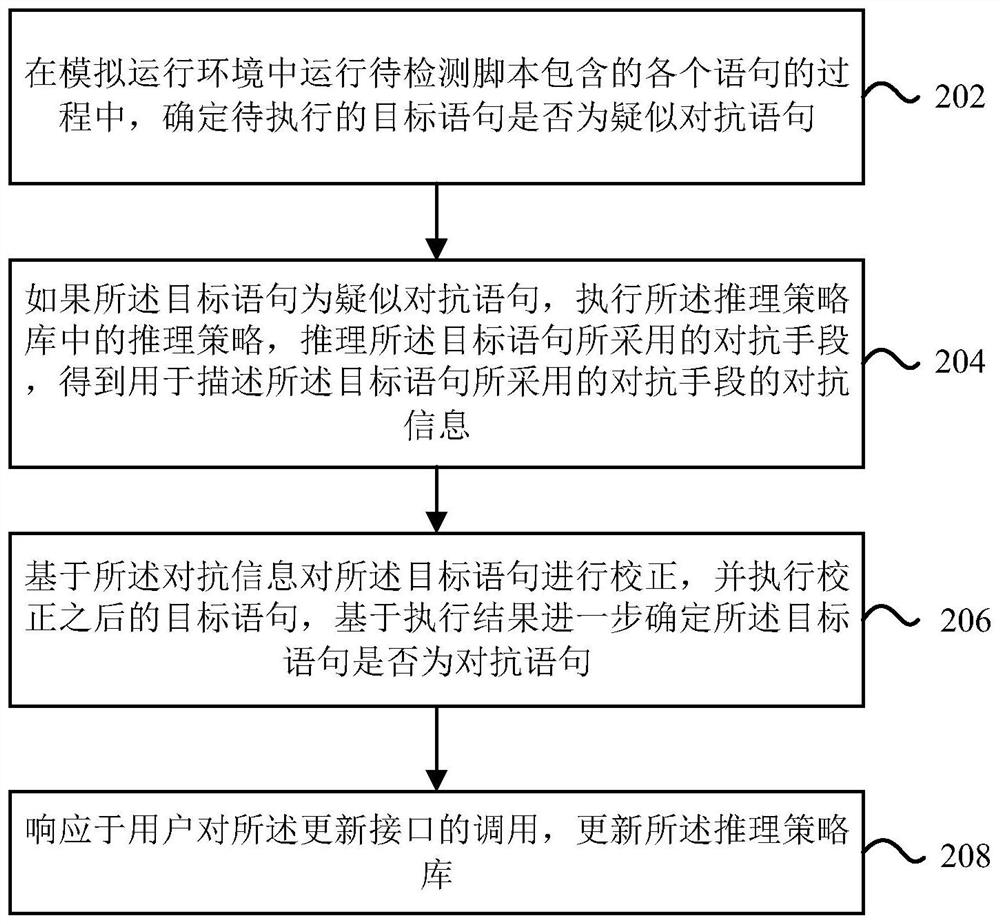
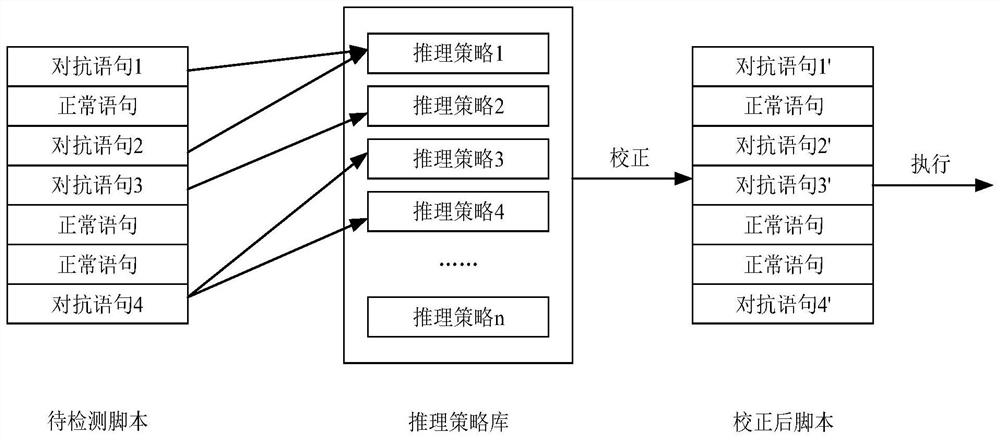
Script detection method and device
PendingCN114880667AEnhanced confrontation abilityAccurate identificationPlatform integrity maintainanceInference methodsTheoretical computer scienceEngineering
The invention provides a script detection method and device. The script detection method and device are applied to a security detection engine adopting a reasoning framework. The safety detection engine is pre-loaded with an inference strategy library; the reasoning strategy library comprises a plurality of reasoning strategies used for reasoning confrontation means adopted by confrontation statements used for confrontation detection and contained in the script to be detected. The method comprises the steps of determining whether a target statement to be executed is a suspected adversarial statement or not in a process of running each statement contained in a script to be detected in a simulated running environment; and if the target statement is the suspected adversarial statement, executing an inference strategy in an inference strategy library, and inferring an adversarial means adopted by the target statement to obtain adversarial information used for describing the adversarial means adopted by the target statement. And correcting a target statement based on the confrontation information, executing the corrected target statement, and further determining whether the target statement is a confrontation statement or not based on an execution result.
Owner:ALIBABA CLOUD COMPUTING LTD
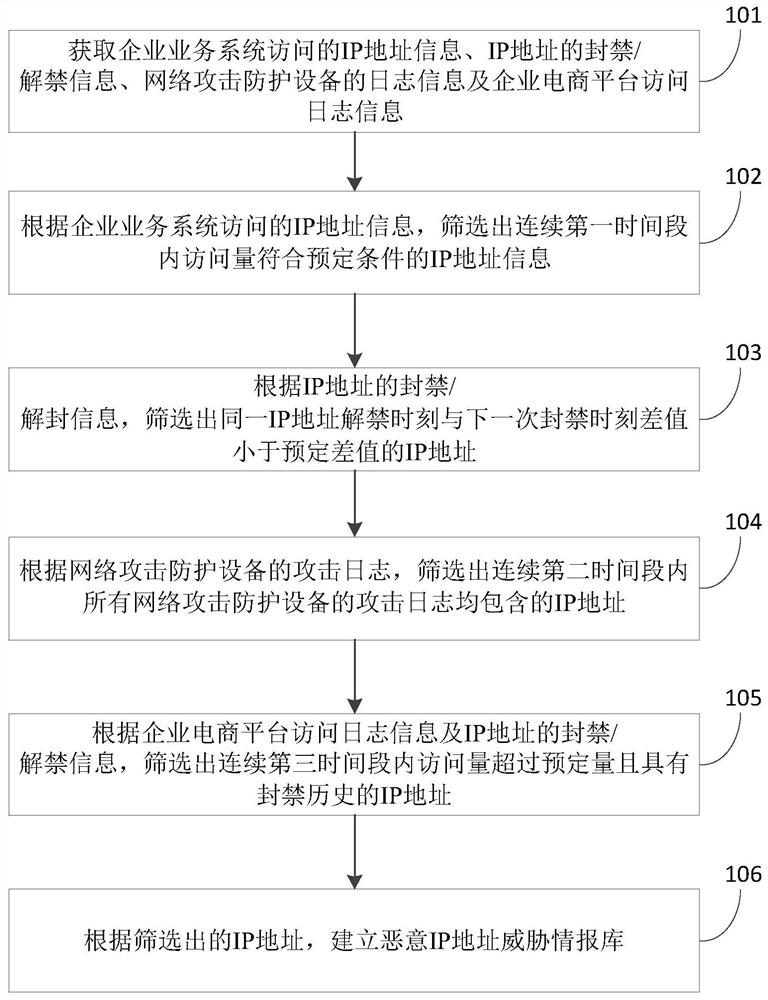
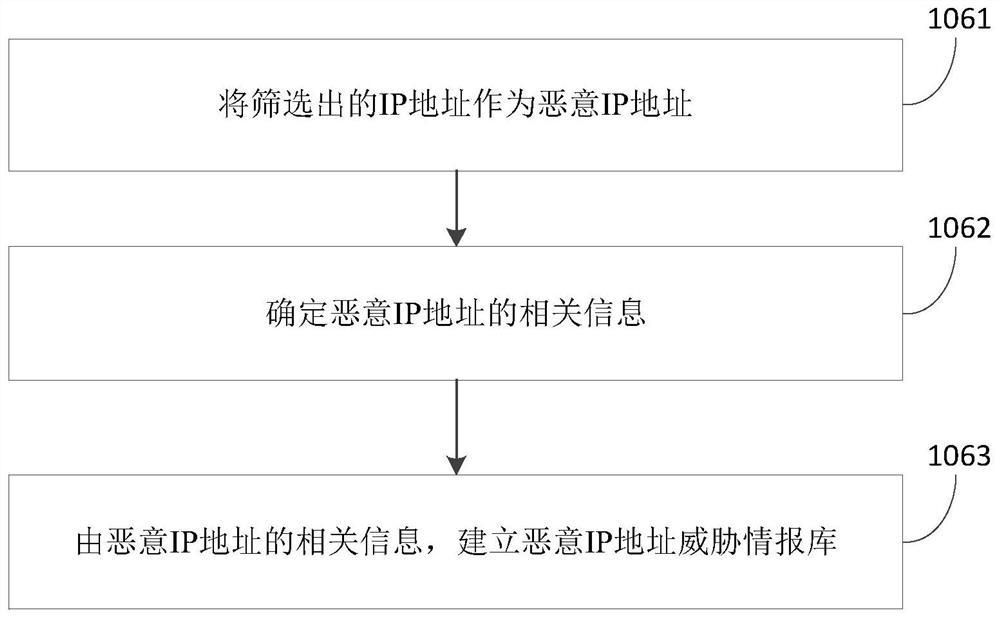
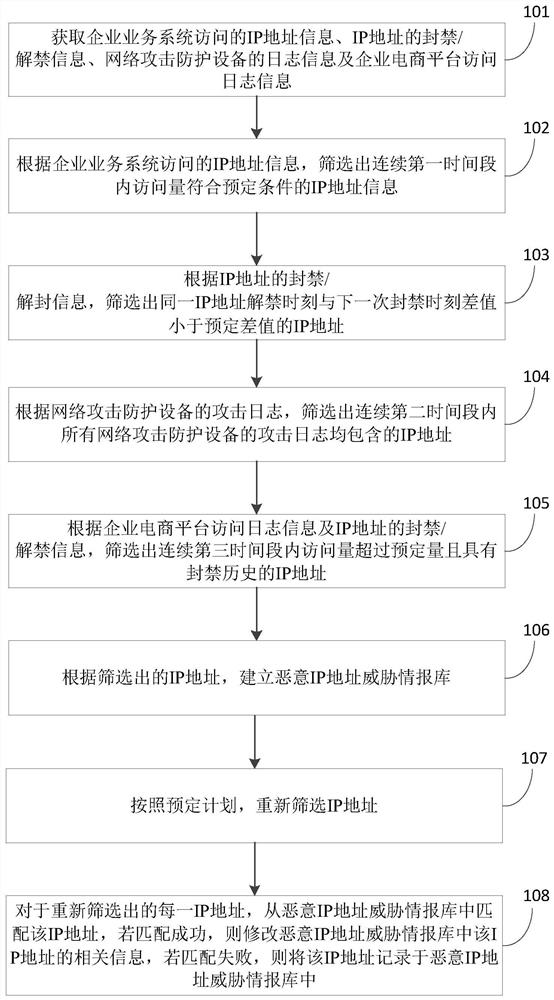
Method and device for establishing malicious IP address threat intelligence library and preventing malicious attack
ActiveCN113225349AEnhanced confrontation abilityReduce riskTransmissionIp addressThreat intelligence
The invention provides a method and device for establishing a malicious IP address threat intelligence library and preventing a malicious attack, and the method comprises the steps: screening out IP address information of which the page view meets a preset condition in a continuous first time period according to IP address information accessed by an enterprise business system; according to the banning / unbanning information of the IP addresses, screening out the IP addresses of which the difference between the banning moment of the same IP address and the banning moment of the next time is smaller than a preset difference; according to the attack logs of the network attack protection devices, screening out IP addresses contained in the attack logs of all the network attack protection devices in a continuous second time period; according to the access log information of the enterprise e-commerce platform and the banning / unbanning information of the IP addresses, screening out the IP addresses of which the access amount exceeds a predetermined amount in a continuous third time period and which have banning history; and establishing a malicious IP address threat intelligence library according to the screened IP addresses. According to the invention, passivity can be changed into active, the network attack resisting capability of enterprises is improved, and the risk is reduced.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Water gun toy and using method thereof
InactiveCN109059634ATo achieve the purpose of sprayingEasy to carryLiquid ejecting gunsFuselageClean water
The invention discloses a water gun toy and a using method thereof. The water gun toy comprises a machine body, a first cavity arranged in the machine body and a second cavity arranged in the machinebody, a first rotating shaft which extends front and back and a second rotating shaft which is position on the right side of the first rotating shaft are rotationally arranged in the second cavity, the tail ends of the front side and the rear side of the first rotating shaft penetrate through the front end wall and the rear end wall of the second cavity and extend out of the machine body to be fixedly provided with first rolling wheels, and first belt wheels which are symmetrical front and back are fixedly installed on the outer surface of the second rotating shaft in the second cavity. According to the water gun toy and the using method thereof, the water gun toy is simple in structure and convenient to operate, through pedaling by an operator, the water gun toy is driven to move, meanwhile, a liquid needing to be sprayed is pressurized, so that the purpose of spraying through the water gun is achieved, meanwhile, a large amount of clean water can be carried by the water gun toy in amore labor-saving mode, the countervailing power of the water gun toy is improved, the water gun toy is convenient to move, moreover, all the working procedures cooperate with one another and do not influence one another, and the practical performance of the water gun toy is improved.
Owner:杭州力松电子科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com