Countercheck method for automatically identifying speaker aiming to voice deception
A speaker recognition and speaker technology, applied in speech analysis, instruments, etc., can solve problems such as fragile confrontation capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The drawings are for illustrative purposes only, and should not be construed as limitations on this patent; in order to better illustrate this embodiment, some parts in the drawings will be omitted, enlarged or reduced, and do not represent the size of the actual product;
[0058] For those skilled in the art, it is understandable that some well-known structures and descriptions thereof may be omitted in the drawings. The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
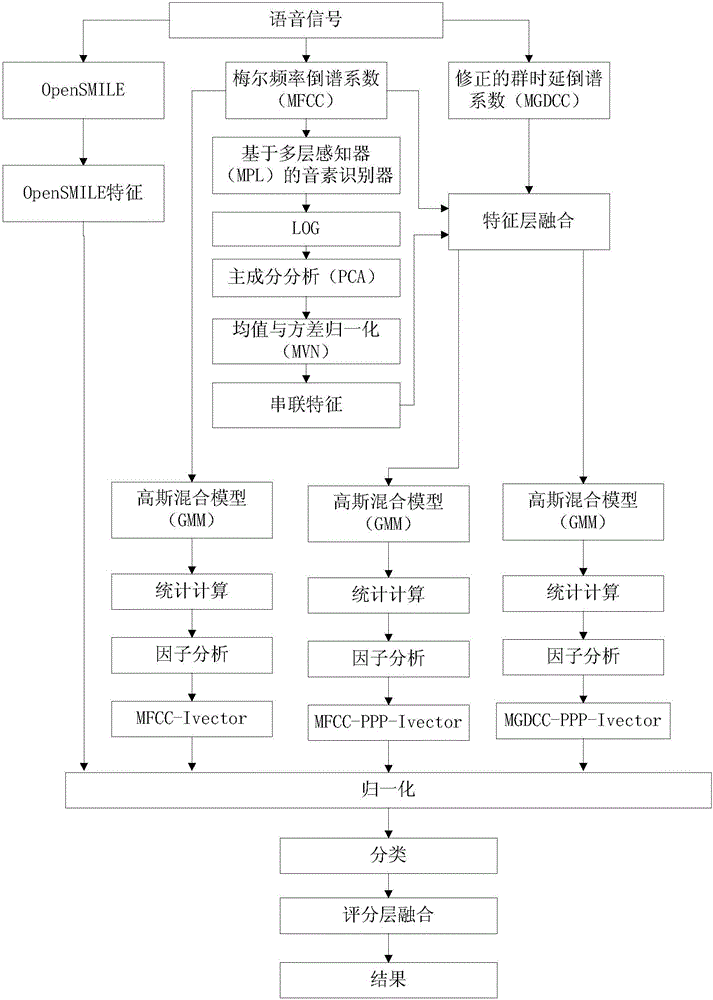
[0059] ⅣExperimental results
[0060] Table 1 shows the experimental results of the 4 subsystems on the development data. It can be observed that fusing PPP features at the feature level improves the performance. Compared with the MFCCi-vector subsystem (EER=6.63%), the error rate of MFCC-PPPi-vector is reduced by 1.06%. On the other hand, the results of the OpenSmile feature are better than those of the MFCCi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com