Method and device for establishing malicious IP address threat intelligence library and preventing malicious attack
An IP address and establishment method technology, applied in the field of network security, can solve problems such as high risk, poor ability to resist network attack behavior, and enterprises cannot predict malicious attack behavior, so as to reduce losses, improve the ability to resist, and reduce risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
other Embodiment approach
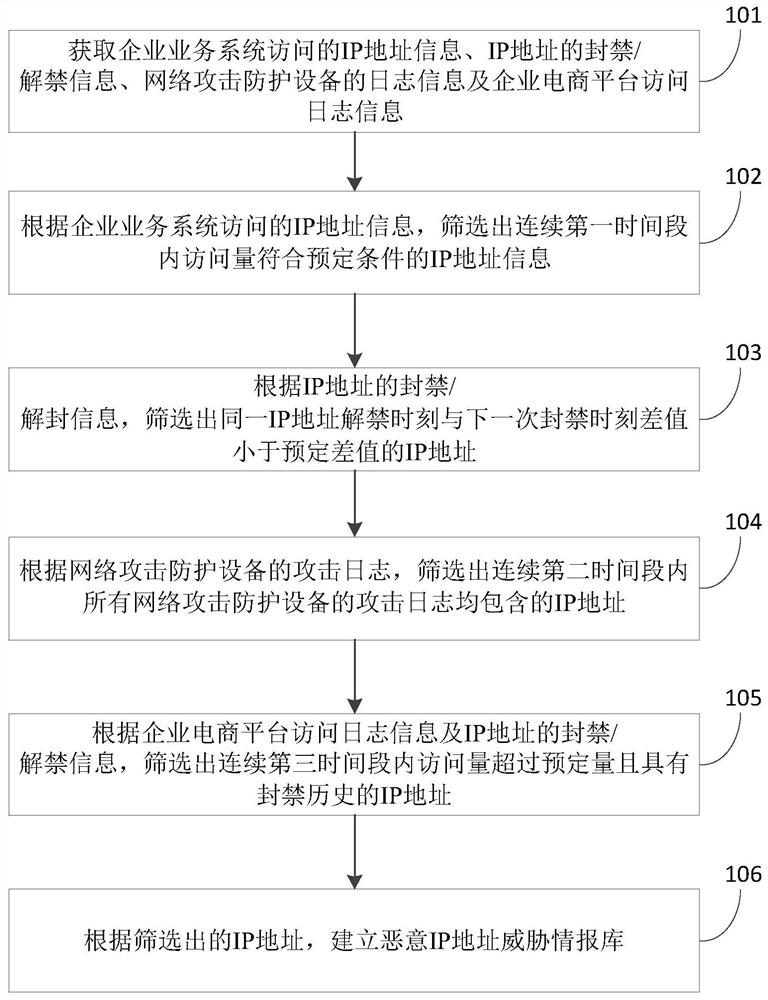
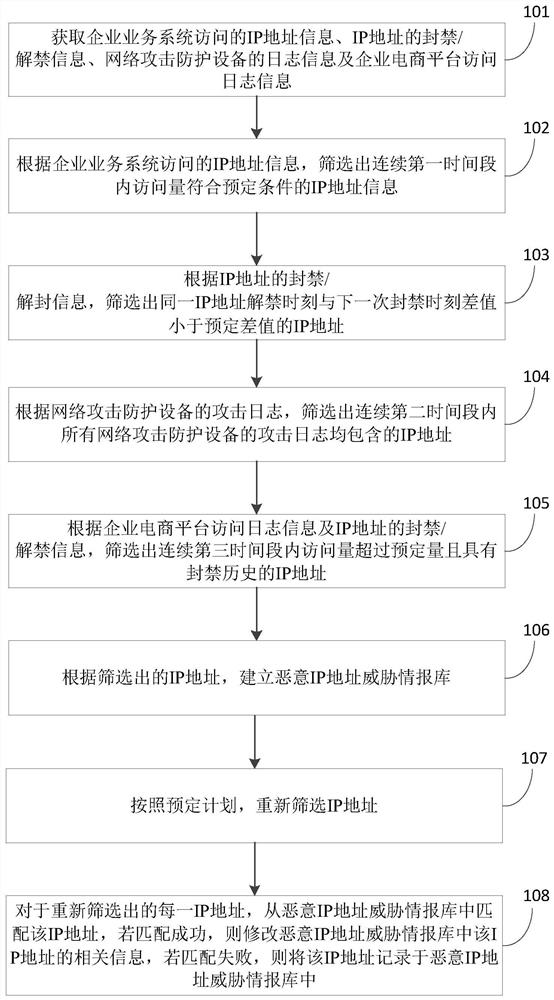
[0099] In other implementation manners, the first time period may also be determined from the perspectives of day and night. Among them, the daytime refers to 7:00 to 22:00 in the area where the enterprise is located, which is the main business hours of the enterprise. Night is from 22:00 to 7:00 the next day in the time zone where the enterprise is located, and it is a non-main business period of the enterprise. Correspondingly, the first time period is, for example, daytime and / or nighttime of N days, and the predetermined condition is that there are attacks during daytime and / or nighttime of N consecutive days, and the average number of daily attacks exceeds 3000 times.
[0100] During specific implementation, the first time period and predetermined conditions may be adjusted according to actual conditions, and specific values thereof are not limited herein.
[0101] The banning of IP addresses refers to the prohibition of access to the IP address that initiates the atta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com