Method and system for detecting Windows malicious programs on KVM virtualization platform
A virtualization platform and malicious program technology, applied in the field of computer virtualization and operating system security, can solve the problems of poor detection accuracy and weak confrontation of malicious programs, and achieve strong confrontation, improved security, and guaranteed stability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
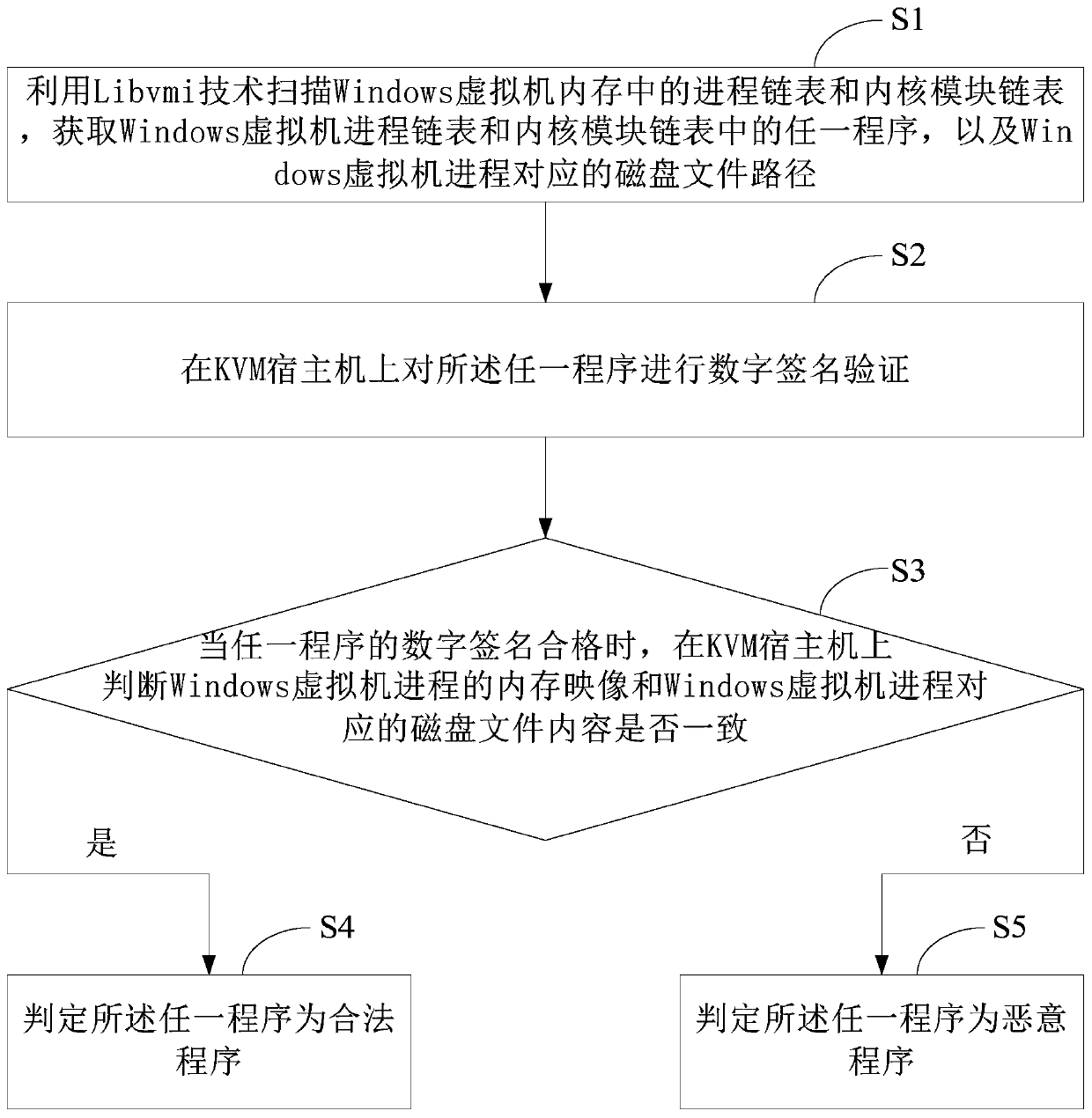
[0061] see figure 1 , figure 1 It is a schematic flowchart of a method for detecting Windows malicious programs on the KVM virtualization platform provided by the embodiment of the present application. Depend on figure 1 As can be seen, the method for detecting Windows malicious programs on the KVM virtualization platform in the present embodiment mainly includes the following steps:
[0062] S1: Use Libvmi technology to scan the process linked list and kernel module linked list in the memory of the Windows virtual machine to obtain any program in the Windows virtual machine process linked list and kernel module linked list, as well as the disk file path corresponding to the Windows virtual machine process. Wherein, the Windows virtual machine process matches any program, and the process is a program running in the system, and once the program is running, it is a process.
[0063] Libvmi technology is used by the KVM host to monitor the running underlying virtual machine. L...
Embodiment 2
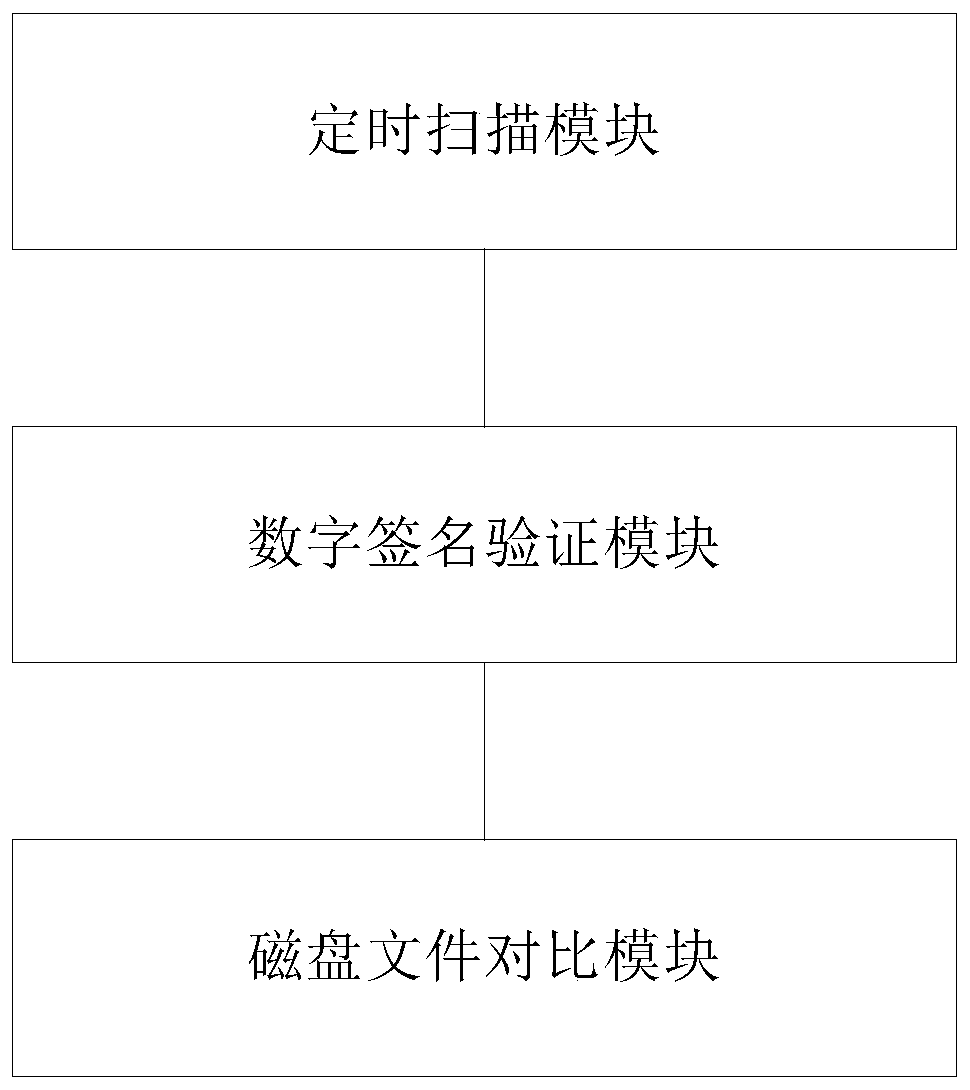
[0105] exist figure 1 On the basis of the illustrated embodiment see figure 2 , figure 2 It is a schematic structural diagram of a system for detecting Windows malicious programs on a KVM virtualization platform provided by an embodiment of the present application. Depend on figure 2 It can be seen that the system for detecting Windows malicious programs on the KVM virtualization platform in this embodiment mainly includes three parts: a scanning module, a digital signature verification module and a disk file comparison module. The system is set on the KVM host machine. Among them, the scanning module is used to scan the process linked list and kernel module linked list in the Windows virtual machine memory by using Libvmi technology, and obtain any program in the Windows virtual machine process linked list and the kernel module linked list, as well as the disk file path corresponding to the Windows virtual machine process , where the Windows virtual machine process mat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com