Execution method and device for registry operation
A registry and execution logic technology, applied in the direction of program control devices, computer security devices, program control design, etc., can solve problems such as incompatibility of security software, weak resistance to driver-level malicious programs, and lack of kernel mode capabilities of the operating system. Achieve the effect of avoiding the potential possibility of incompatibility and enhancing the confrontation ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0084] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
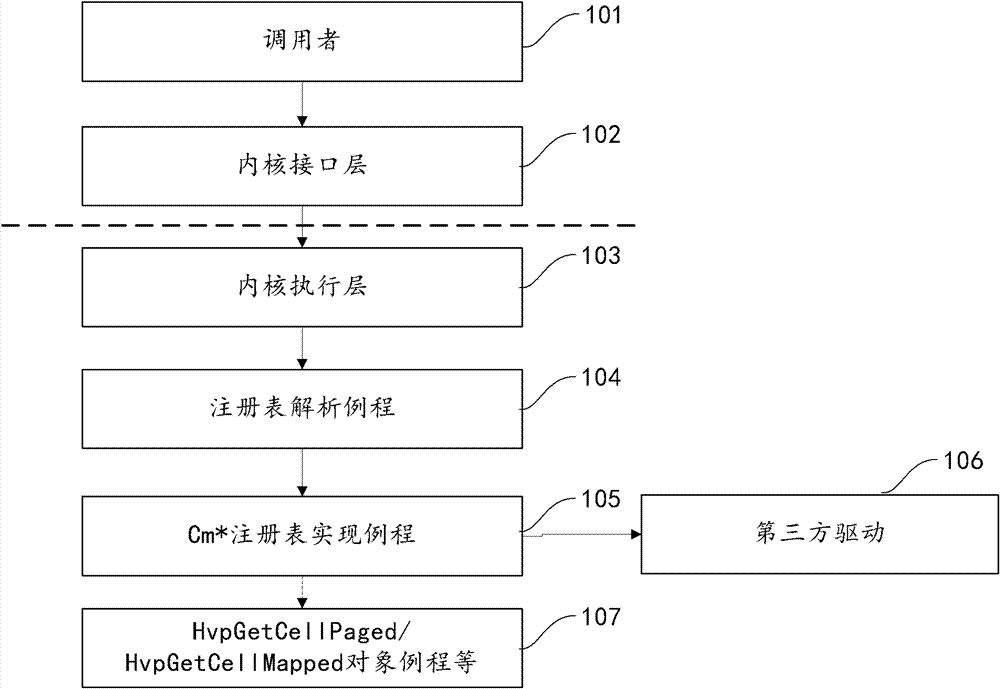
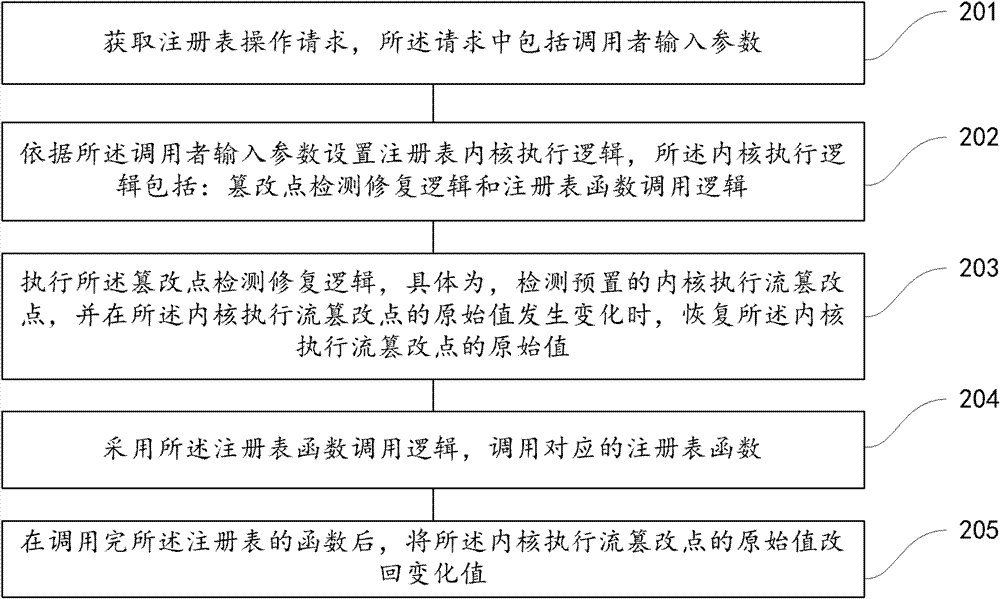
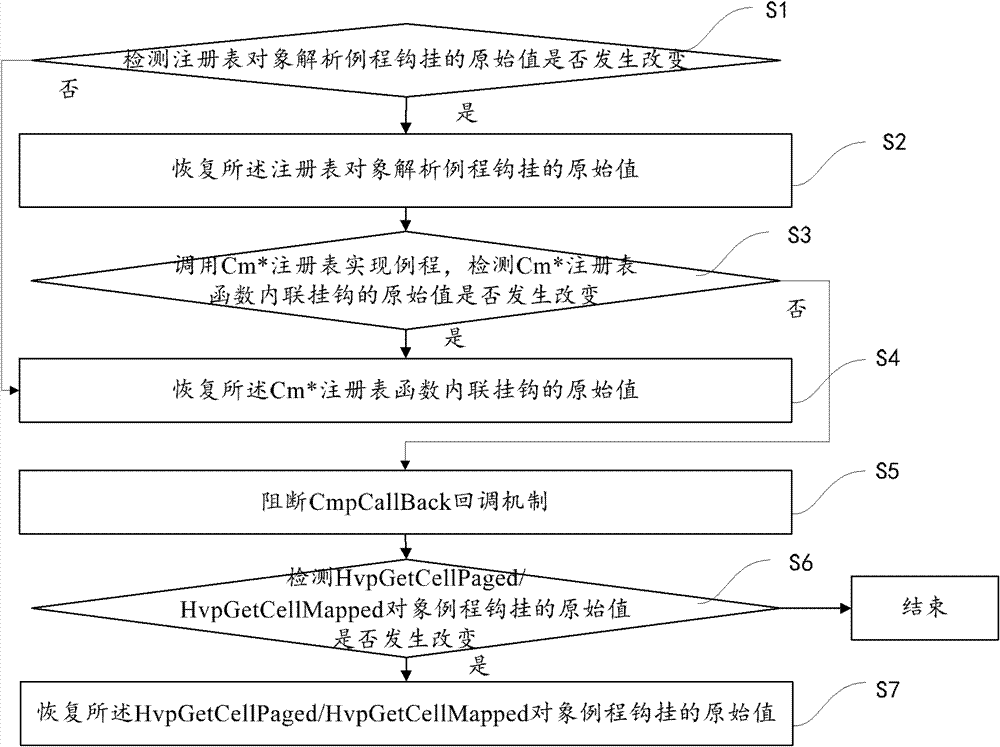
[0085] One of the core concepts of the embodiments of the present invention is to build a trusted environment for registry operations based on the entire life cycle of registry behaviors, and implement a set of registry operation call libraries in the user mode interface of the operating system. Inspect the request from the user state, simulate the behavior of the kernel execution layer, detect / recover the object resolution hook, block the kernel registry callback mechanism, etc., so that the third-party driver can be penetrated (or called bypass, bypass) , so as to ensure the authenticity and credibility of the registry operation request environment. Moreover, the kernel synchronous call returns the user mode handle information a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com