Method and device for carrying out file operation
A technology of file operation and execution method, which is applied in the direction of computer security devices, instruments, computing, etc., can solve the problems of weak resistance to driver-level malicious programs, lack of ability, and incompatibility of security software, so as to avoid the potential possibility of incompatibility , enhance the ability to resist, and have a wide range of effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0076] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
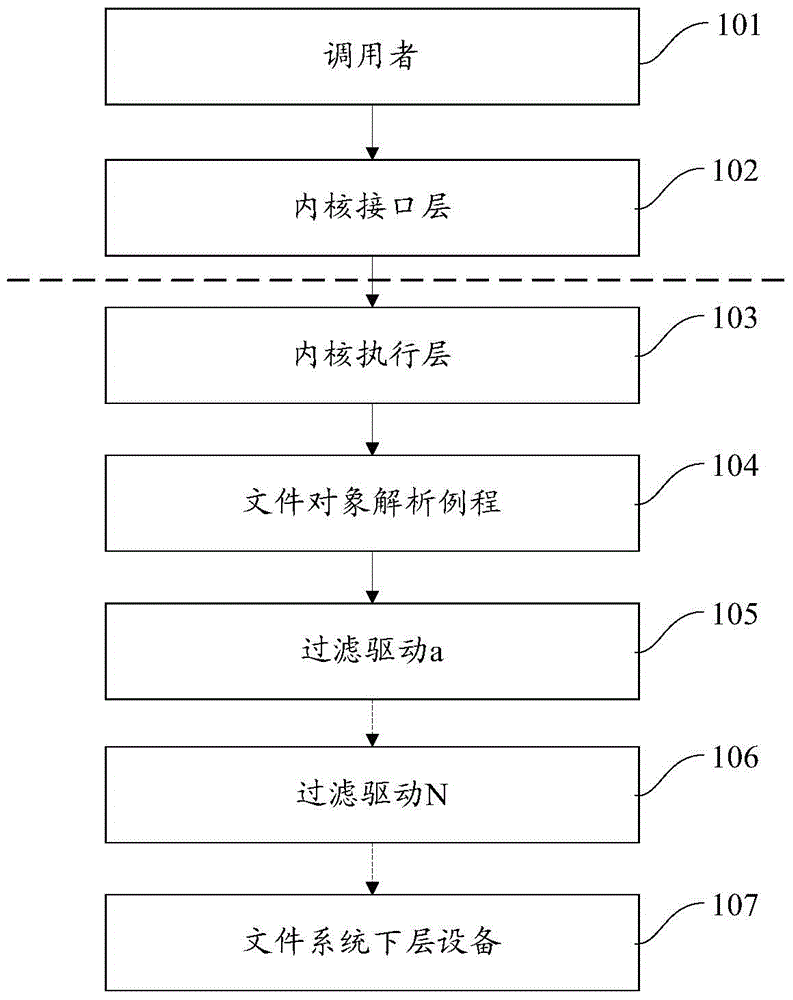
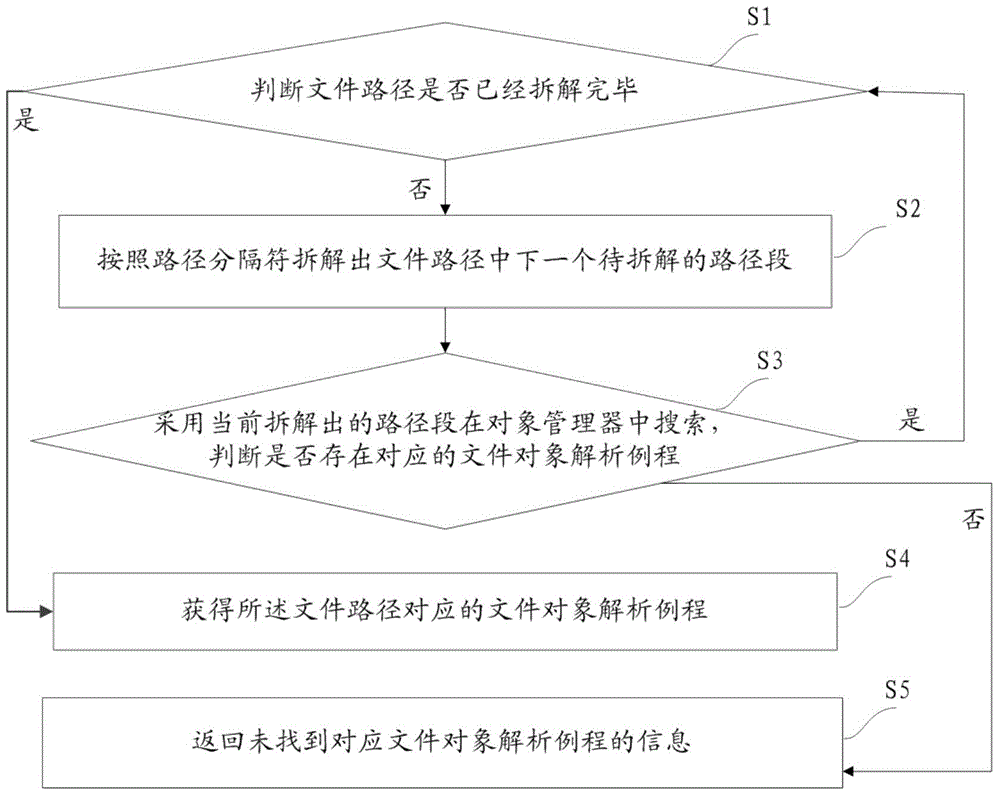
[0077] One of the core concepts of the embodiment of the present invention is to completely implement a set of file operation calling library in the user mode interface of the operating system, the caller initiates a file operation request, calls the corresponding file operation interface routine, and the operating system kernel mode driver obtains and corrects the library. Verify the request from the user mode, build a query data structure to analyze the incoming file path, and finally find the object type maintained in the object manager. This process effectively resists the internal risk of hijacking in the kernel mode. Thereafter, the operating system kernel mode driver builds and fills the IRP request packet, and sends it to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com