File unlocking method and device
A file unlocking and file technology, which is applied in the file unlocking device and file unlocking field, can solve the problems of lack of ability, weak resistance, single means of unlocking and shredding virus-infected files, etc., to achieve a safe shredding mechanism, enhance the ability to fight, high success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
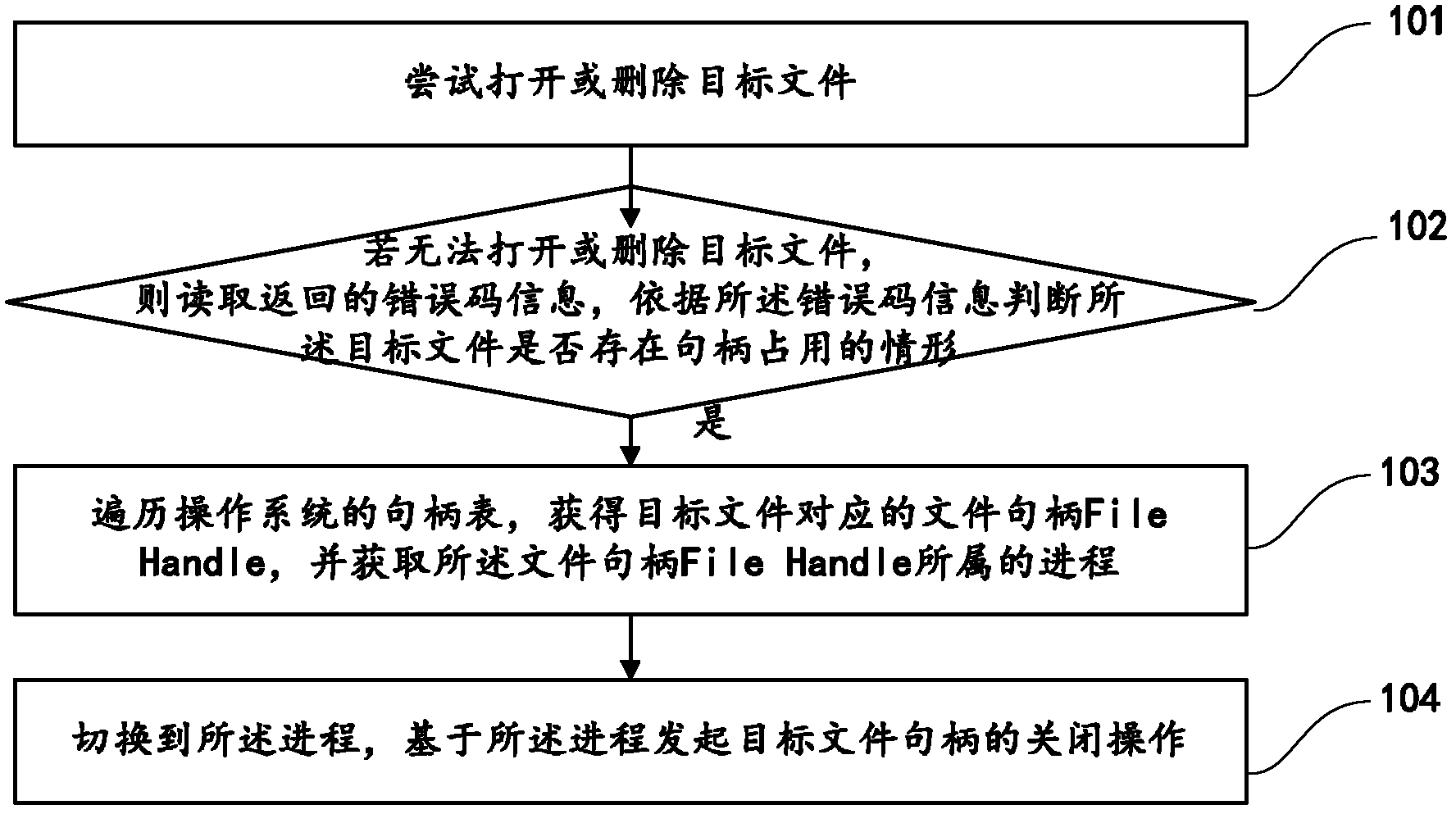
[0047] refer to figure 1 , which shows a flow chart of the steps of an embodiment of a file unlocking method of the present invention, which may specifically include the following steps:
[0048] Step 101, try to open or delete the target file;
[0049] It should be noted that, in the embodiment of the present invention, the files include files of a type supported by the WINDOWS operating system. Described file is not meant to open file (as *.exe, *.doc etc. type file) by trigger mode such as double-clicking mouse or pressing enter key; But refers to the application program of using operating system API or the self-definition of the present invention CreateFile () function etc. of the interface BAPI (application of the present i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com