Method and authentication device for unlocking administration authority
A technology for authenticating equipment and managing authority, applied in user identity/authority verification, digital data authentication, electronic digital data processing, etc., can solve the problems of inability to unlock management authority, poor processing flexibility, etc., to achieve the effect of improving processing flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
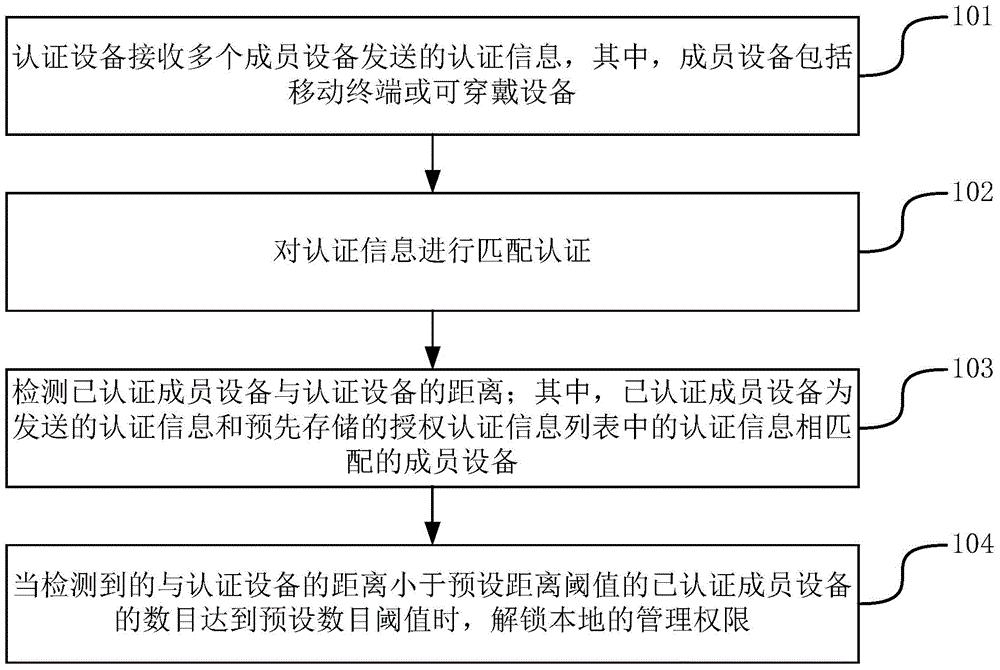
[0066] The embodiment of the present disclosure provides a method for unlocking management rights, such as figure 1 As shown, the processing flow of the method may include the following steps:
[0067] In step 101, the authentication device receives authentication information sent by multiple member devices, where the member devices include mobile terminals or wearable devices.
[0068] In step 102, matching authentication is performed on the authentication information.
[0069] In step 103, the distance between the authenticated member device and the authentication device is detected; wherein the authenticated member device is a member device whose authentication information sent matches the authentication information in the pre-stored authorized authentication information list.
[0070] In step 104, when the detected number of authenticated member devices whose distance to the authentication device is smaller than the preset distance threshold reaches the preset number thre...
Embodiment 2
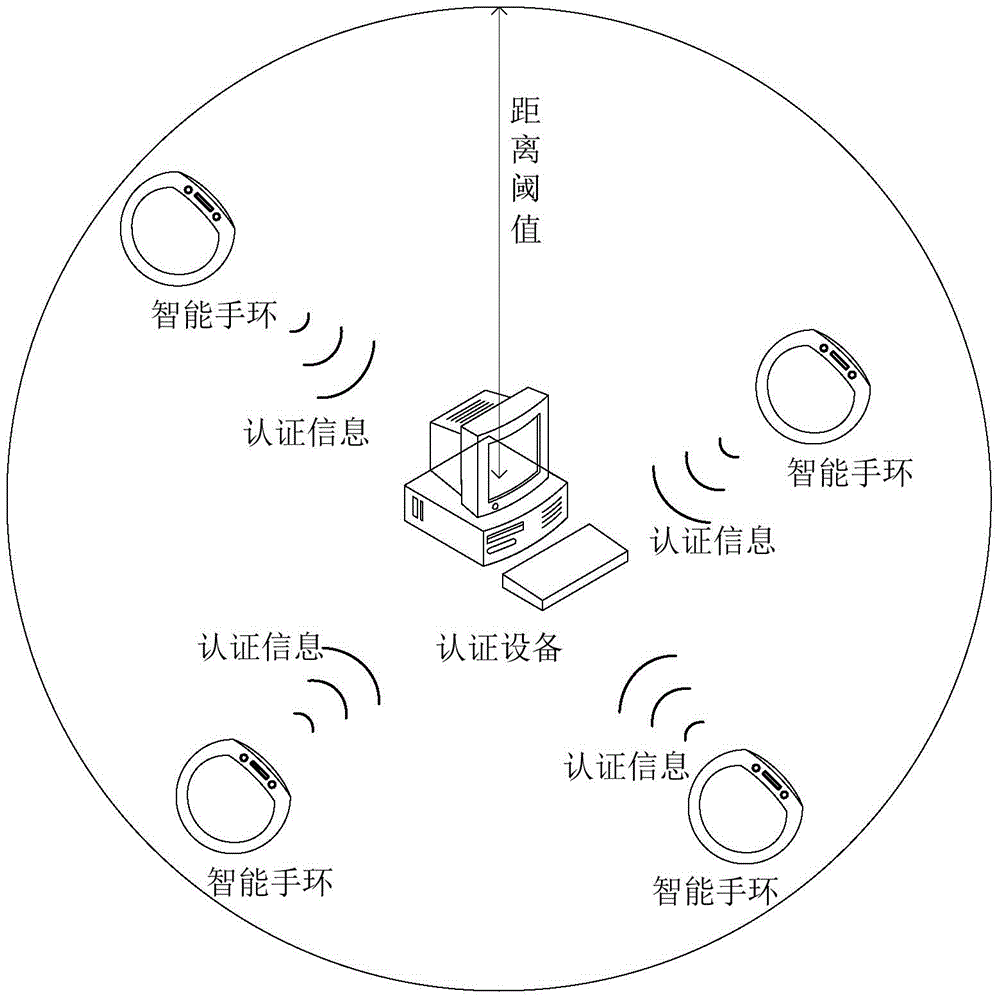
[0073] The embodiment of the present disclosure provides a method for unlocking management rights, which can be used in any device with data management capabilities (called an authentication device), where the authentication device can be a desktop computer, or can be a mobile phone or a tablet computer Such as mobile terminal, also can be server group etc. The member devices in this method may be mobile terminals (such as mobile phones), wearable devices, etc., and wearable devices are electronic devices that can be worn, such as smart bracelets, smart watches, smart collars, and the like. In this embodiment, the authentication device is a management terminal of a company as an example, and the member device is a smart bracelet as an example for detailed description of the solution. Other situations are similar, and this embodiment will not repeat them.
[0074] The following will be combined with the implementation mode, and the figure 1 The processing flow shown is describ...
Embodiment 3
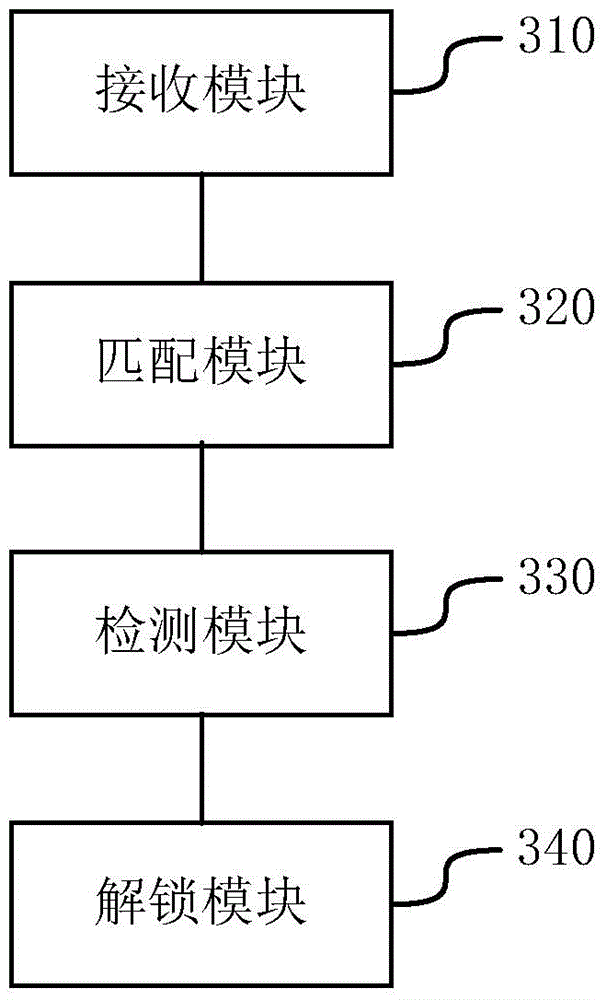
[0104] Based on the same technical idea, the embodiment of the present disclosure also provides an authentication device, such as image 3 As shown, the authentication device includes: a receiving module 310 , a matching module 320 , a detecting module 330 and an unlocking module 340 .
[0105] The receiving module 310 is configured to receive authentication information sent by multiple member devices; wherein the member devices include mobile terminals or wearable devices;
[0106] A matching module 320, configured to perform matching authentication on the authentication information;
[0107] A detection module 330, configured to detect a distance between an authenticated member device and the authenticated device; wherein the authenticated member device is a member device whose authentication information sent matches the authentication information in the pre-stored authorized authentication information list;
[0108] The unlocking module 340 is configured to unlock the loca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com