ID (Identity) binding method and system
A technology of identity identification and binding, applied in the network field, can solve problems such as inability to enter web pages, inconvenience for users, etc., and achieve the effect of convenient login
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
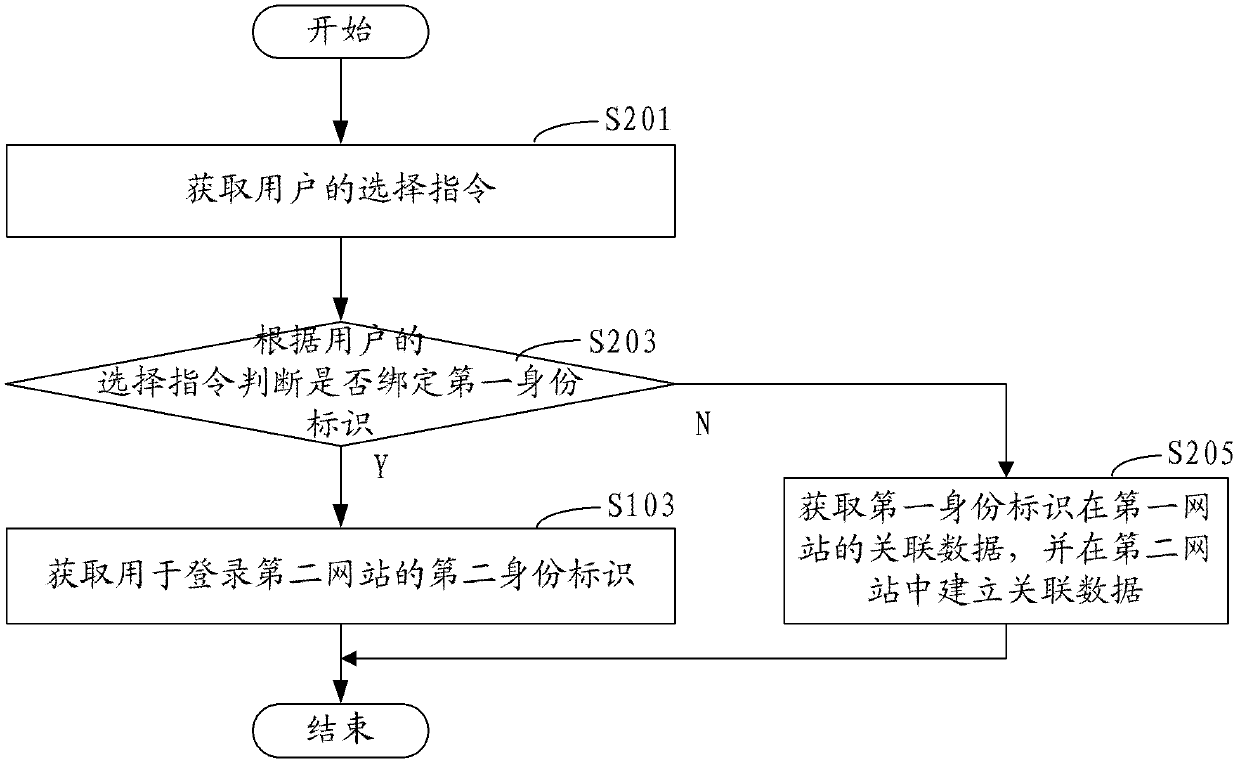
[0052] In the second embodiment, if figure 2 As shown, before the above step of obtaining the second identity for logging into the second website, it also includes:
[0053] Step S201, acquiring a user's selection instruction.
[0054] In this embodiment, the user can choose whether to bind the identity through the selection interface provided by the second website.
[0055] Step S203, judging whether to bind the first identity according to the user's selection instruction, if yes, go to step S103, if not, go to step S205.
[0056] In this embodiment, the judgment is made through the user's selection instruction. When it is judged that the first identity needs to be bound, enter step S103 to establish an association relationship between the first identity and the second identity. When the first identity is identified, the first identity is directly used as the user's identity in the second website. Specifically, after the user's identity verification is successful, the use...
Embodiment 3
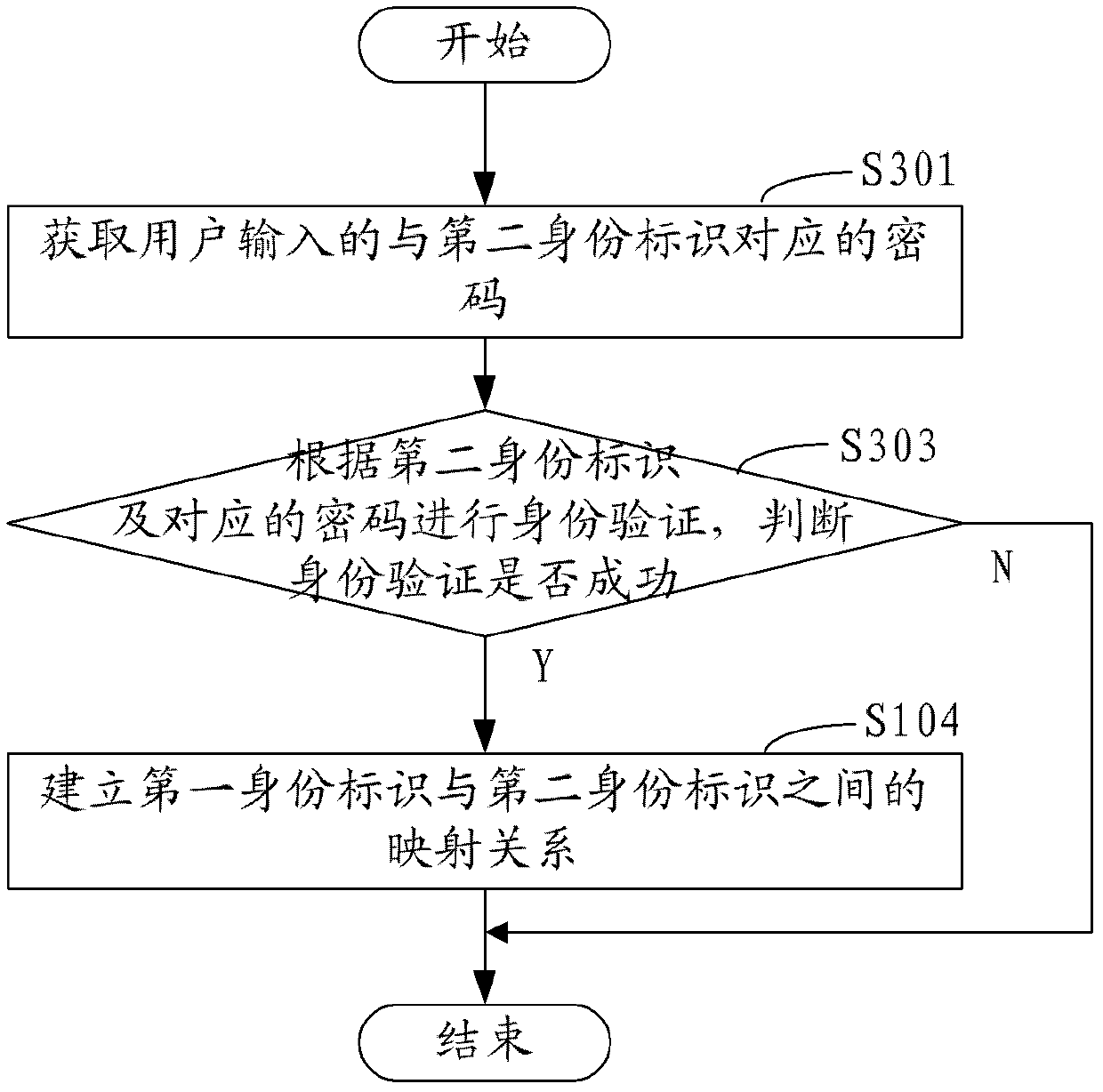
[0059] In the third embodiment, as image 3 As shown, after the above step of obtaining the second identity for logging into the second website, it also includes:
[0060] Step S301, acquiring the password input by the user and corresponding to the second identity.
[0061] Step S303, perform identity verification according to the second identity mark and the corresponding password, and judge whether the identity verification is successful, if yes, proceed to step S104, if not, end.
[0062] In this embodiment, in order to ensure the security of the system and prevent the second identity in the second website from being maliciously bound, it is necessary to perform identity verification according to the second identity and the corresponding password entered by the user to determine whether the user has the right to Bind the second identity with the first identity.
[0063] Step S104, establishing a mapping relationship between the first identity and the second identity.
[...
Embodiment 4
[0066] In the fourth embodiment, as Figure 4 As shown, in the above identity binding method, the following steps are also included before the step of obtaining the second identity used to log in to the second website:
[0067] Step S401, judge whether the user is logging in the second website for the first time according to the first identity, if yes, go to step S103, if not, go to step S403.
[0068] In this embodiment, after successfully logging in to the second website through the first identity, the user can inquire whether the user is using the first identity to log in to the second website for the first time. If so, it means that the user may need to use the first identity The identifier is bound to the user's original second identity in the second website. At this time, the user's original second identity in the second website is acquired, and if not, enter the second website.
[0069] Step S403, searching the mapping table whether there is a second identity that has ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com