Identity authentication system of network user and method
An identity authentication and network user technology, applied in the field of network user identity authentication, can solve problems such as user password insecurity, user confusion, and lack of intuition, and achieve the effects of improving security performance, easy operation of the method, and simple structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
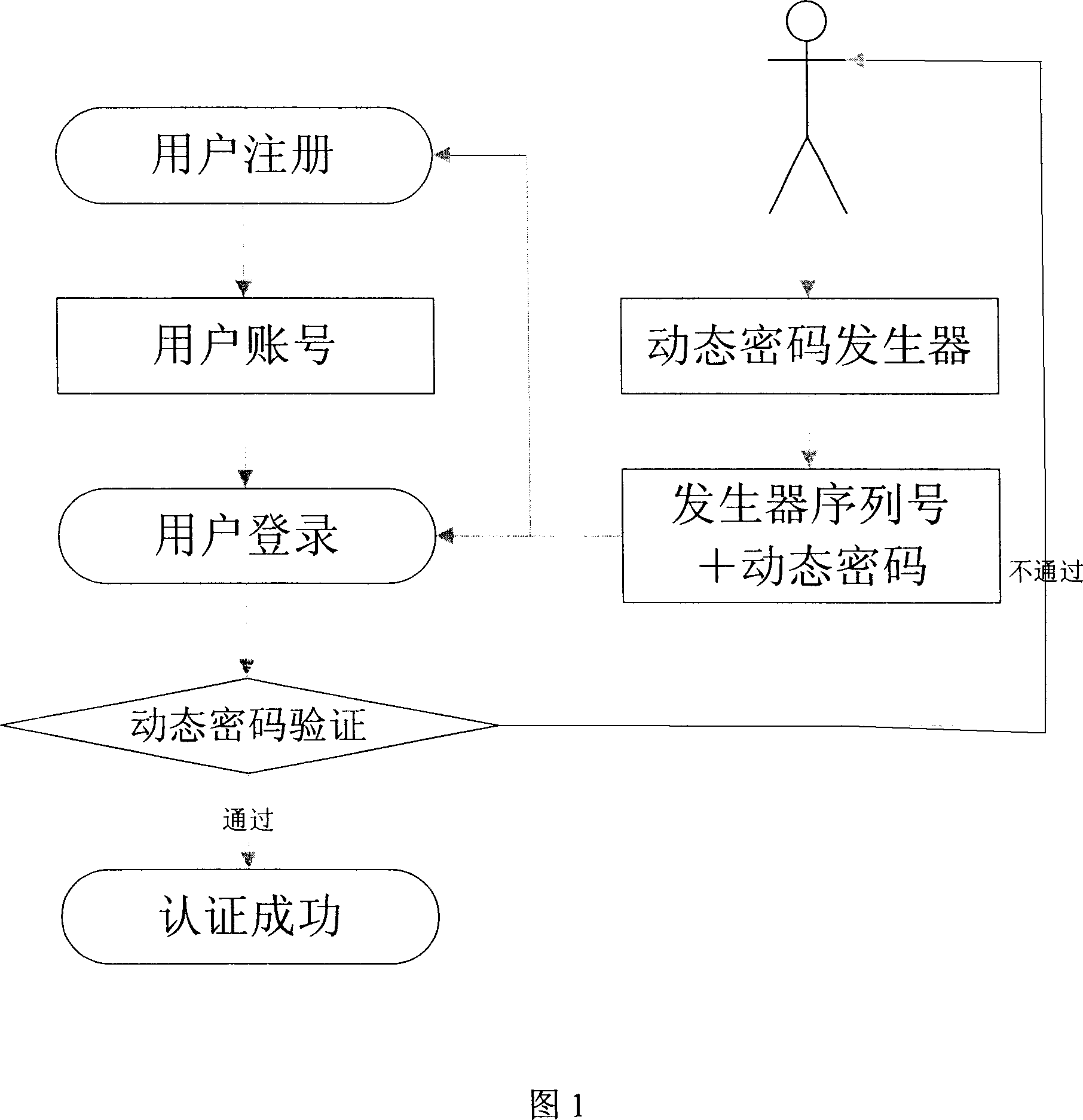
[0019] In order to solve many problems encountered in common authentication and login, the present invention provides users who are not familiar with computer and network technology with a convenient and safe registration and login authentication method, and this method can also be applied to electronic payment security authentication through the network and many other fields.
[0020] The network user identity authentication system of the present invention includes a client computer, a dynamic password generator and a server, the dynamic password generator is connected to the client computer, and a unique generator serial number is recorded on it and can generate a dynamic password; The client computer and the server are connected to each other through a communication network; the server is provided with a dynamic password verification module corresponding to the dynamic password generator, so as to ensure that the dynamic password generated by the dynamic password generator c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com