Binary anti-counterfeiting printing method based on three-dimensional encrypted anti-counterfeiting information
A binary and binary information technology, applied in image communication, record carrier used by machines, instruments, etc., can solve the problems of inability to fundamentally prevent counterfeit products, difficult and effective anti-counterfeiting, and confusion between true and false products.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
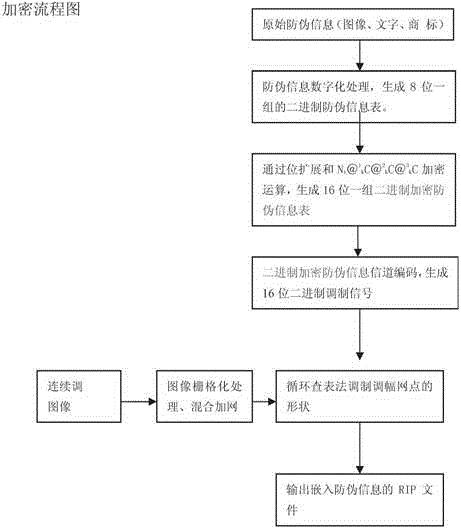
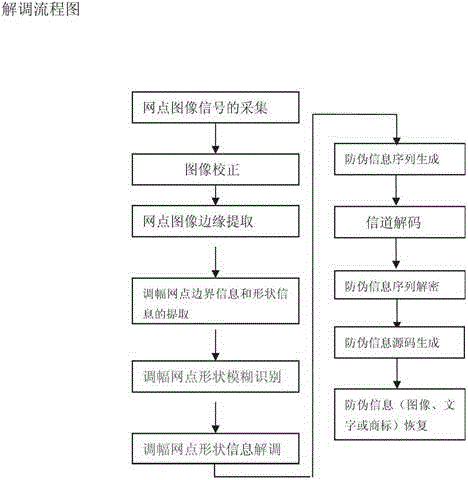
[0010] In the process of loading anti-counterfeiting information figure 1 Among them, the original anti-counterfeiting information (image, text) is digitized to generate an 8-bit binary anti-counterfeiting information table, and the 8-bit binary information in the binary anti-counterfeiting information table is expanded into a 16-bit binary information to generate a high 8 A 16-bit binary anti-counterfeiting information table whose bits are all 0, and the i-th group of 16-bit binary information in the 16-bit binary anti-counterfeiting information table is denoted as N i , i is a positive integer greater than 0, the eight-bit binary encryption parameter is denoted as C, the encryption parameter C is an integer of 0≦C Using +, -, ×, ÷ four, Using ×, -, +, ÷ four, Four types of ÷, -, ×, + are used, and when the operator control variable k=0 Defined as "+" operation, when the operator control variable k=1 Defined as "-" operation, when the operator control variable k=2 De...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com