A secure mobility management method under the identity and location separation system
A management method and mobility technology, applied in the field of computer networks, can solve problems such as not considering the safety of mobile handover of mobile nodes, affecting the scalability of the mapping system, and increasing the burden on the mapping server, so as to reduce the authentication delay and handover delay , small authentication delay, and the effect of preventing man-in-the-middle attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
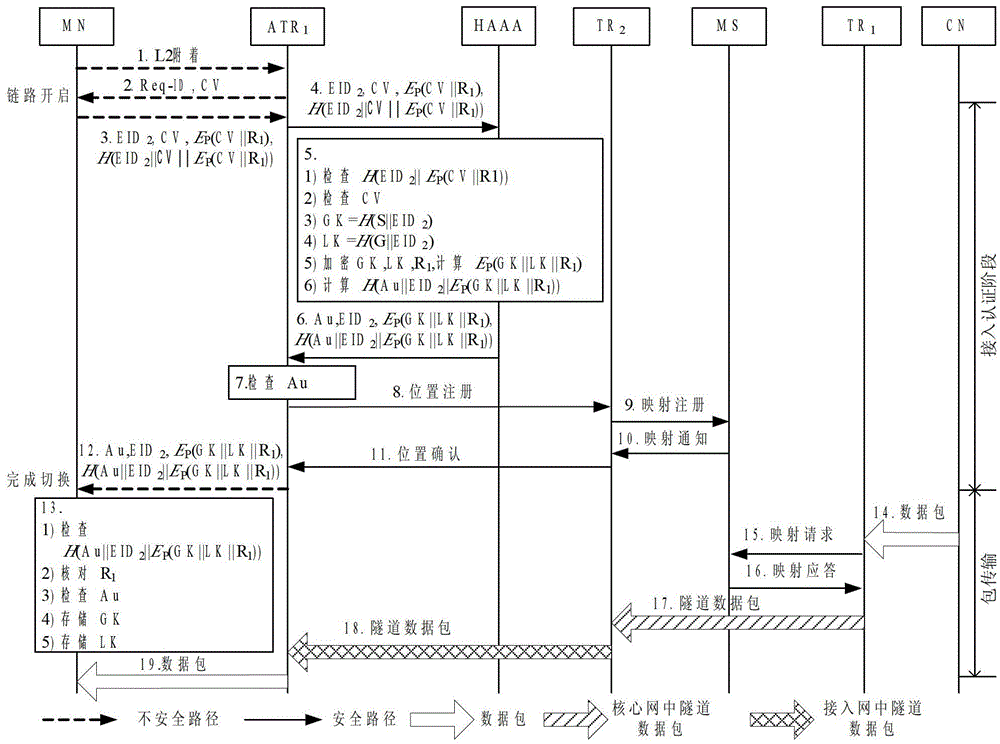
[0036] The initial security access process of the mobile node in the home domain is as follows: figure 1 As shown, the steps are as follows:
[0037] Step 1. MN attaches to ATR 1 ;
[0038] Step 2, ATR 1 Send identity request and challenge value CV (Challenge Value) to MN;
[0039] Step 3. MN generates random number R 1 , use the MN and HAAA pre-shared key P to encrypt CV and R 1 , calculate E P (CV||R 1 ), calculate the message hash value H(EID 2 ||CV||E P (CV||R 1 )), then ATR 1 Send an access authentication request, the message includes: MN's terminal identification EID 2 , challenge value CV, encrypted information E P (CV||R 1 ) and hash value H (EID 2 ||CV||E P (CV||R 1 )). where E k(m) indicates the ciphertext after encrypting information m with key k, H() is a hash function, and "||" is a string connection character;
[0040] Step 4, ATR 1 Send the access authentication request message to HAAA;
[0041] Step 5, HAAA first checks the hash value H(EID...
Embodiment 2
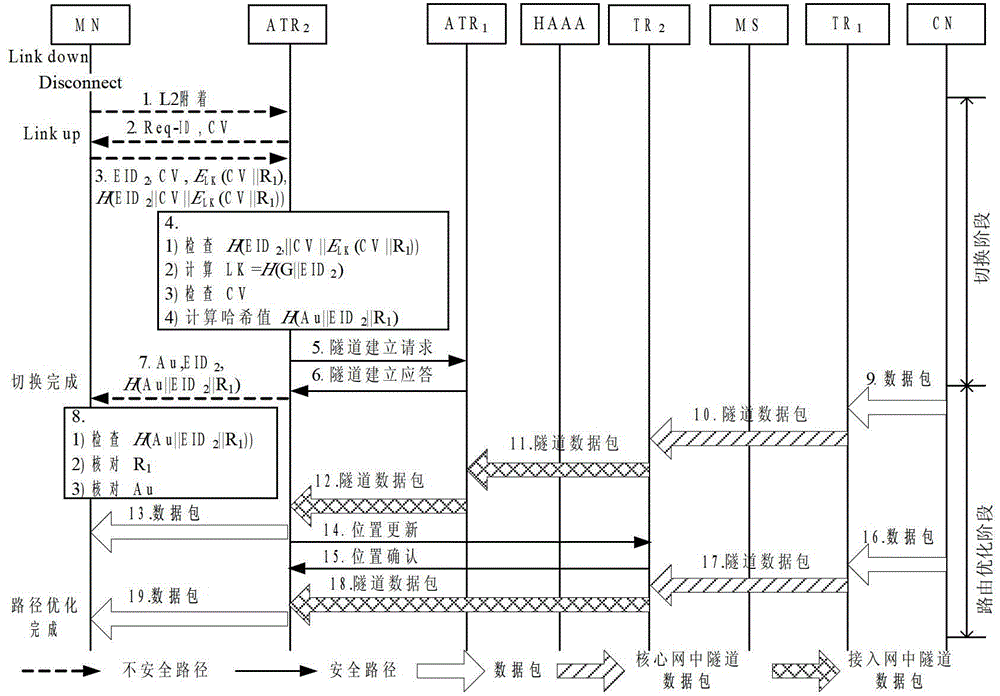
[0057] When the mobile node is handed over within the area, the AAA server does not need to participate, such as figure 2 shown. The safe handover steps of the mobile node in the domain are as follows:
[0058] Step 1, MN and ATR 1 disconnected, attached to ATR 2 ;
[0059] Step 2, ATR 2 Send identity request and challenge value CV (Challenge Value) to MN;
[0060] Step 3. MN generates random number R 1 , using the intra-domain switching key LK, encrypted CV and R obtained during access 1 , calculate E LK (CV||R 1 ), calculate the hash value H(EID 2 ||CV||E LK (CV||R 1 )), then ATR 2 Send a handover access request message, including: MN's terminal identification EID 2 , challenge value CV, encrypted information E LK (CV||R 1 ) and hash value H (EID 2 ||CV||E LK (CV||R 1 ));
[0061] Step 4, ATR 2 Check H(EID 2 ||CV||E LK (CV||R 1 )), using the group key G pre-shared with HAAA to calculate the MN's intra-domain switching key LK=H(G||EID 2 ). Decrypt E ...
Embodiment 3
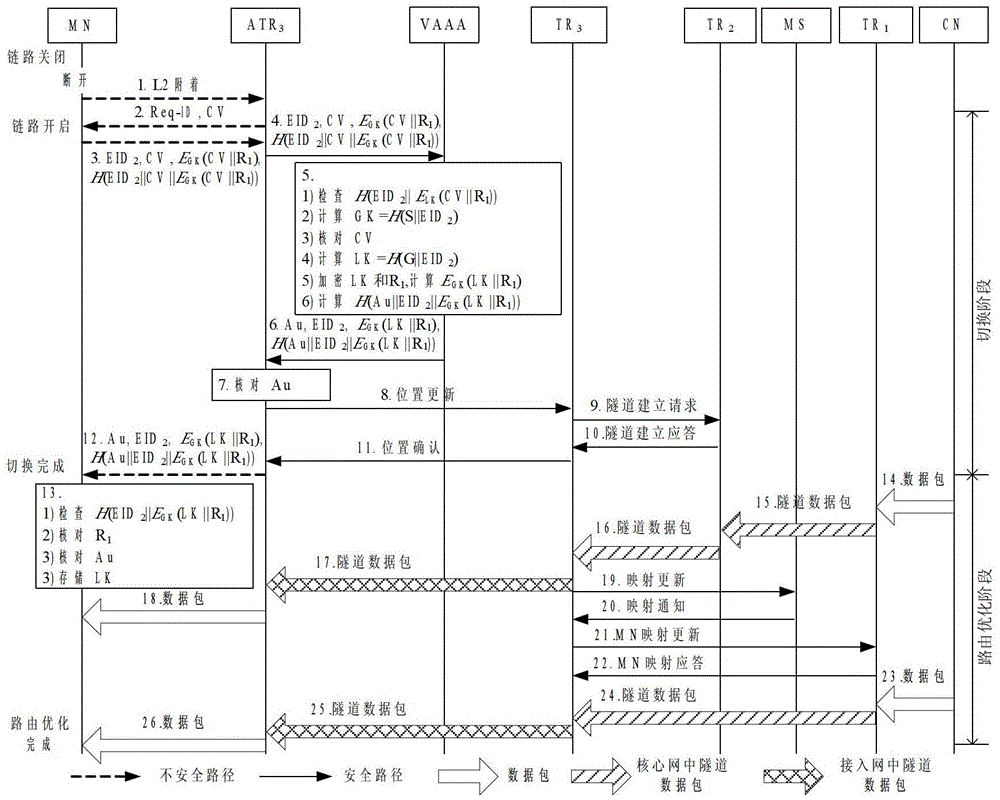
[0078] During the secure handover process of the mobile node between areas, the identity authentication of the mobile node does not require the interaction between VAAA and HAAA, such as image 3 shown. The safe handover steps of the mobile node between areas are as follows:
[0079] Step 1, MN and ATR 2 disconnected, attached to the ATR 3 ;
[0080] Step 2, ATR 3 Send identity request and challenge value CV (Challenge Value) to MN;
[0081] Step 3. MN generates random number R 1 , using the inter-domain switching key GK, encrypted CV and R obtained during access 1 , calculate E GK (CV||R 1 ), calculate the message hash value H(EID 2 ||CV||E GK (CV||R 1 )), then ATR 3 Send a mobile handover access request message, including: MN's terminal identification EID 2 , challenge value CV, encrypted information E GK (CV||R 1 ) and hash value H (EID 2 ||CV||E GK (CV||R 1 ));
[0082] Step 4, ATR 3 Forwarding the mobile handover access request message to VAAA;
[008...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com