Method and apparatus for an ephemeral trusted device
A technology of equipment and trust level, applied in computer security devices, instruments, digital data authentication, etc., can solve problems such as incompatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
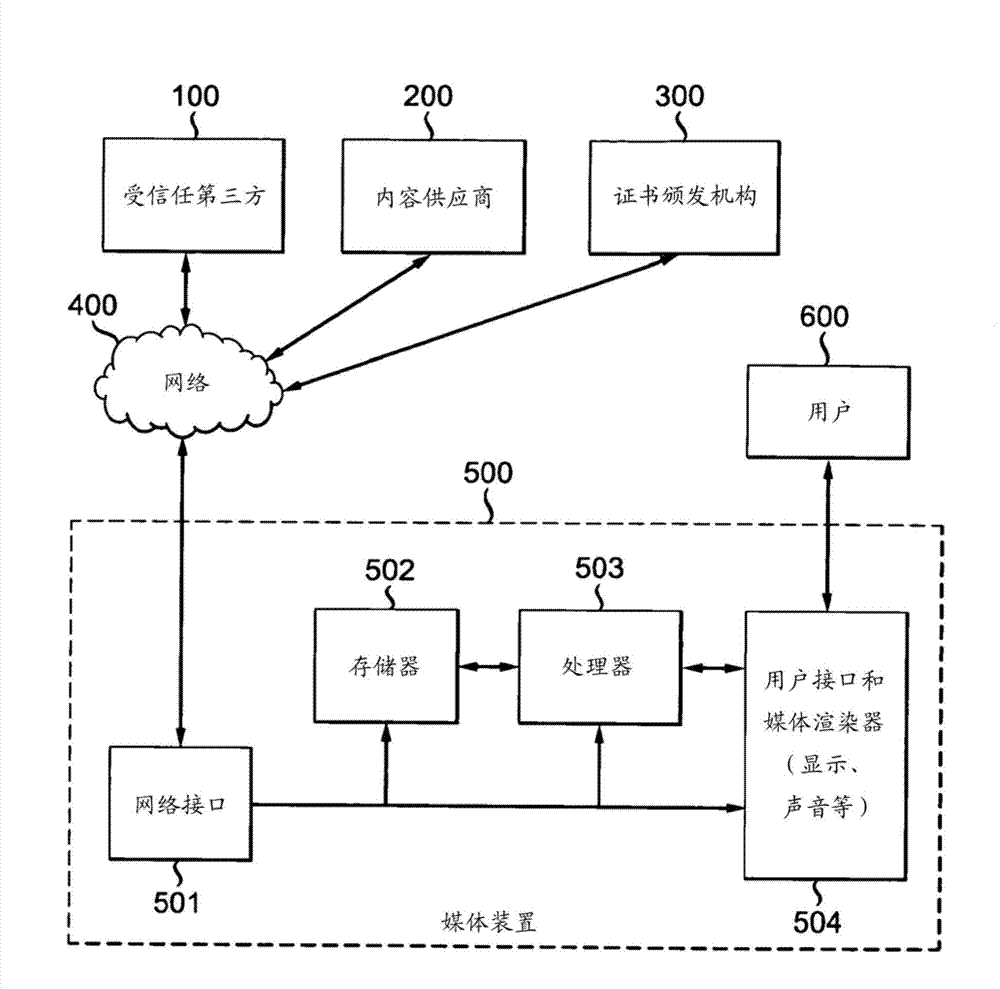
[0018] Temporal trust as used here is the concept that the security trustworthiness of a device will change over time and the level of trust will be assessed as required for a particular purpose. Trust of a device involves the design / implementation, configuration and loaded applications of the device. All of these items may change over time and / or be found to be exploitable.
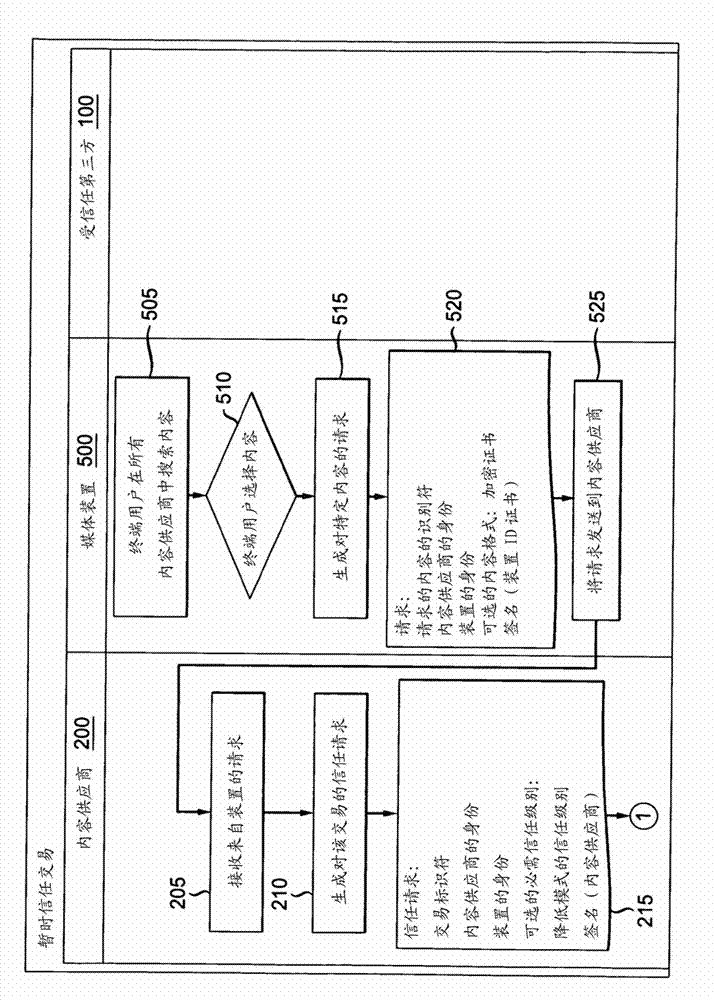
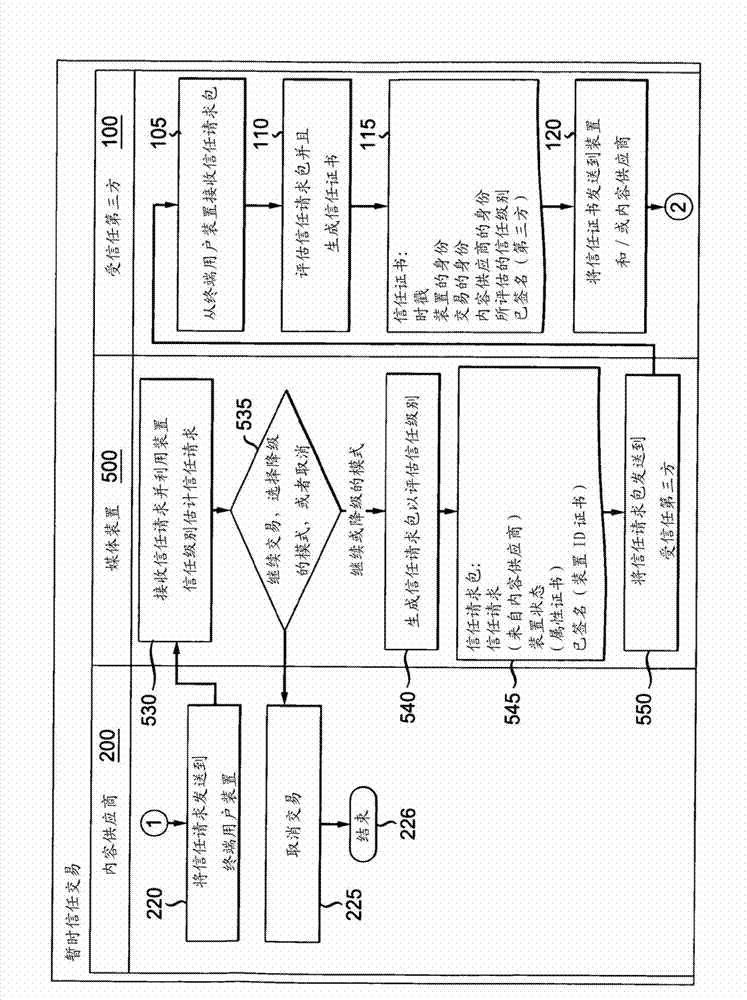
[0019] External content providers should have a way of assessing in real time whether a particular device is allowed to view and / or use their content based on the trust level assessed at that moment. Temporary trust provides a means for a trusted third party to assess the trust level of a device at any given moment, and thus, a decision can be made to allow or deny any type of content, or to allow a downgraded version of the content if it is available. Download to that device. So, for example, if a media device is requesting content from a content provider, the device will seek proof of trust for the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com