Method for session initiation protocol (SIP) terminal to pass through firewall
A firewall and terminal technology, applied in the direction of electrical components, transmission systems, etc., can solve problems such as incompatibility, not fully suitable for the current situation, unsuitable, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
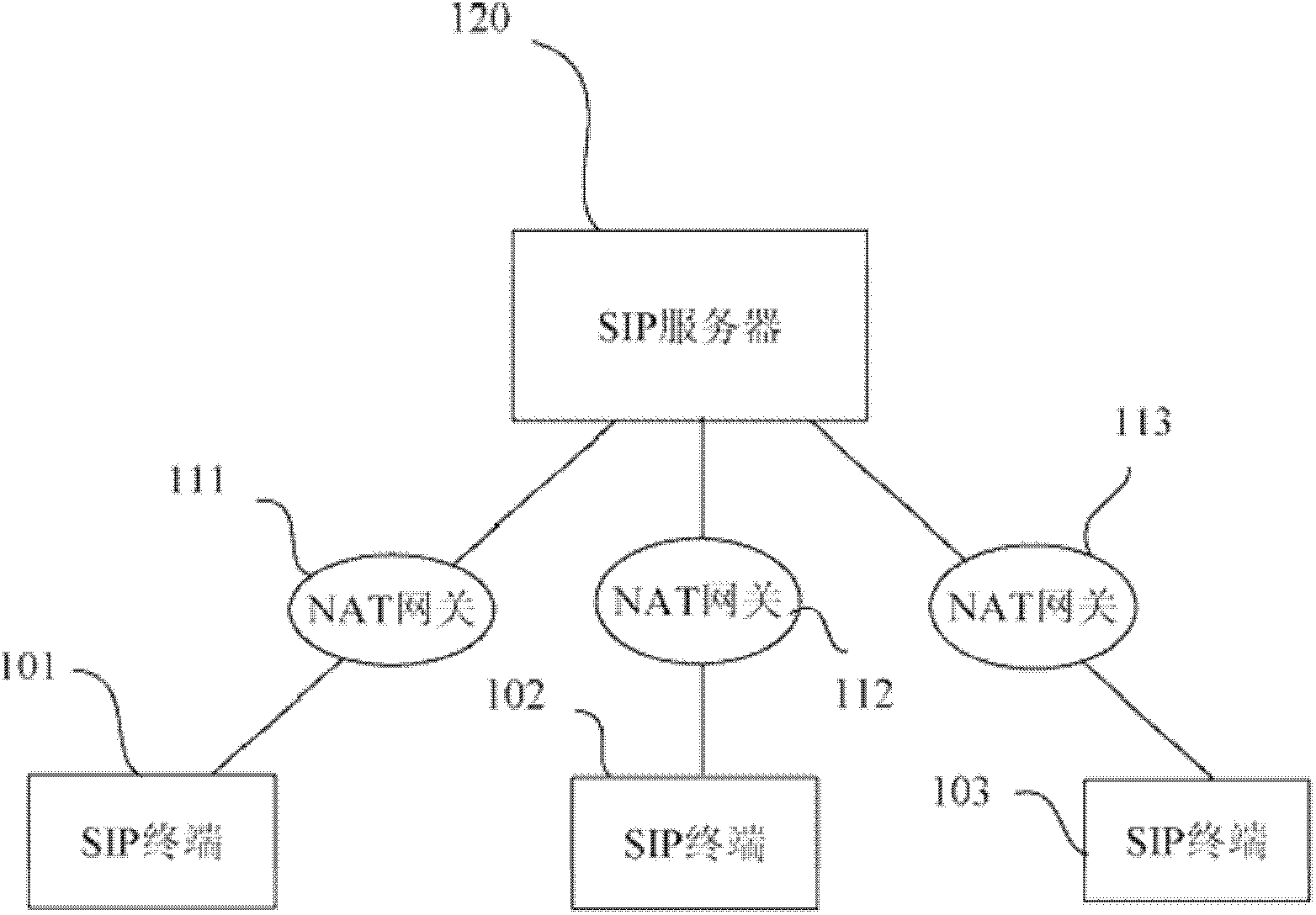
[0014] figure 1 An exemplary implementation environment for embodiments of the invention is shown. refer to figure 1 As shown, the environment includes a SIP server 120 and a plurality of SIP (Session Initiation Protocol) terminals 101-103. These SIP terminals 101 - 103 are connected to the server 120 . Here, a plurality of NAT gateways 111-113 exist between the connection network of each SIP terminal 101-103 and the SIP server 120. Therefore, the communication from the outside of each NAT gateway 111-113 to each SIP terminal 101-103 needs to pass through the NAT gateway and the firewall configured therein. Each NAT gateway 111-113 may have multiple SIP terminals, and only one of them is shown here as an example. In one embodiment, the SIP terminal may be an IP phone.
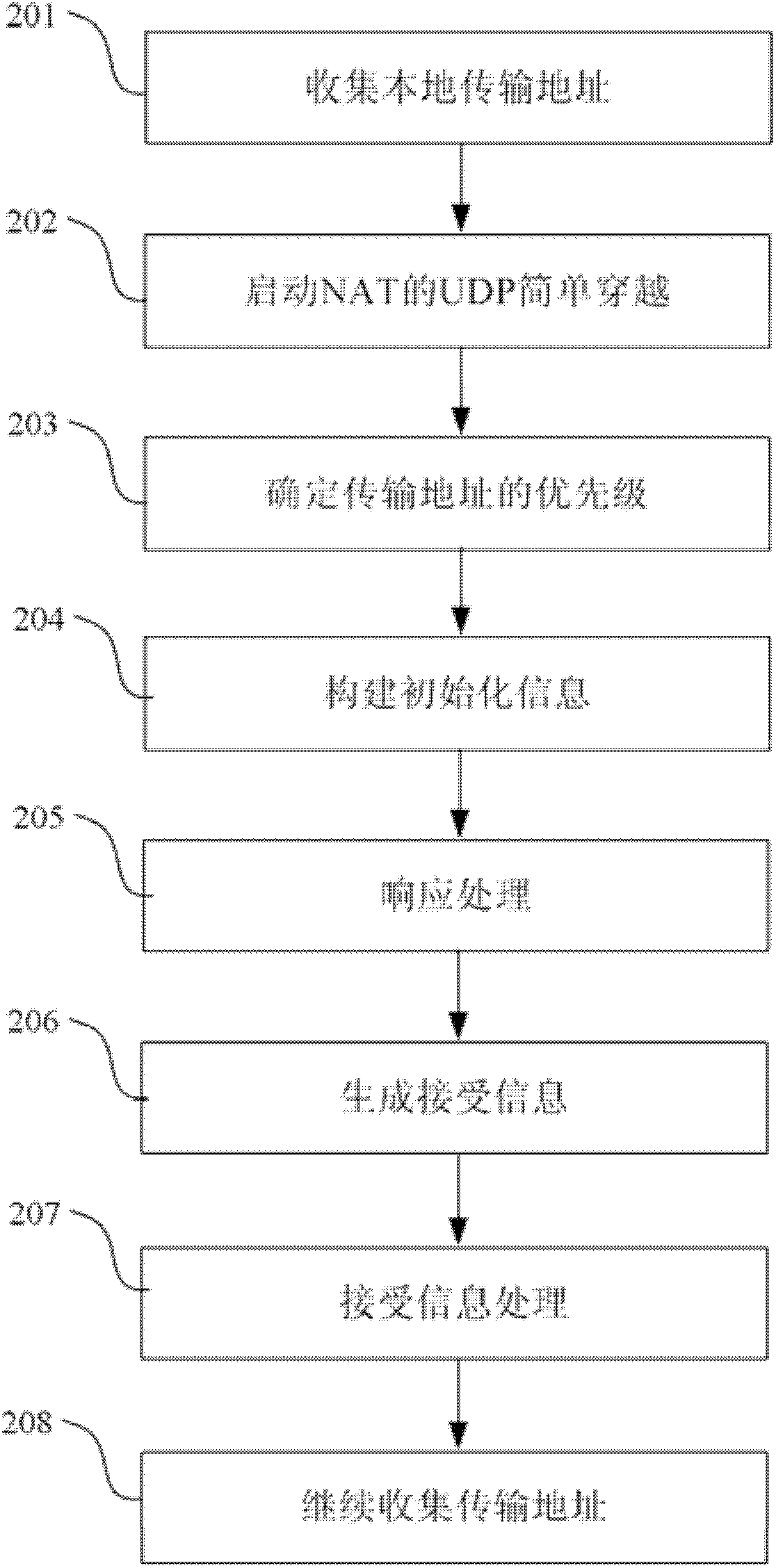
[0015] figure 2 A flow chart of a traversal method according to an embodiment of the present invention is shown. refer to figure 2 As shown, the method includes the following steps:
[0016] Step 201...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com