Defense Method of Routing Query Flooding Attack in Ad Hoc Networks
A wireless ad hoc network and flood attack technology, which is applied in the defense of route query flood attacks in wireless ad hoc networks. Query flood attack, easy to deploy effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the accompanying drawings.
[0029] In a general on-demand routing protocol, data packets and routing control packets (including routing query packets, routing reply packets, etc.) share a first-in first-out FIFO buffer area, and routing control packets have a higher priority. In the method of the present invention, the node needs to establish an independent priority-based buffer area for routing query messages, and take out routing query messages from the buffer area at a set rate for processing.
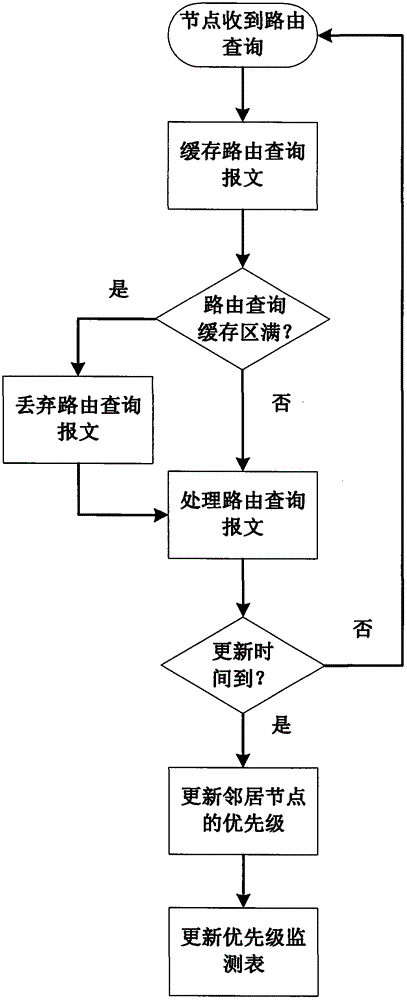
[0030] Attached below figure 1 The specific steps of the present invention are further described as follows.
[0031] Step 1, cache the route query message.
[0032] After the node receives the routing query message, it will first put the routing query message into the routing query cache.
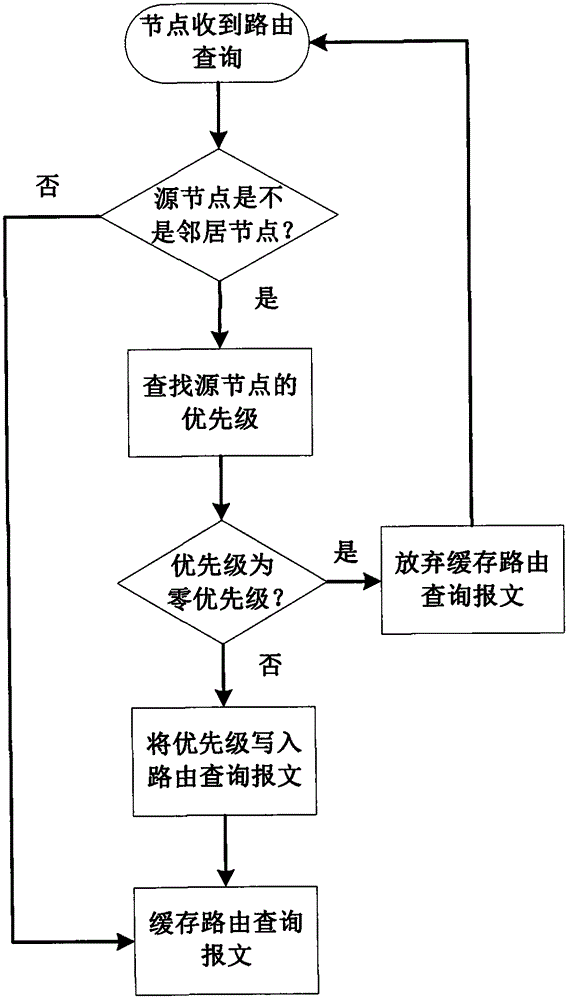
[0033] For caching steps, refer to the attached figure 2 ,details as follows:
[0034] In the first step, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com