Page loophole detection device and page loophole detection method
A vulnerability detection and page technology, which is applied in the field of webpage security, can solve problems such as insufficient coverage path, failure to achieve test results, insufficient PHP page source code path, etc., to achieve the effect of reducing false alarm rate and improving vulnerability coverage rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
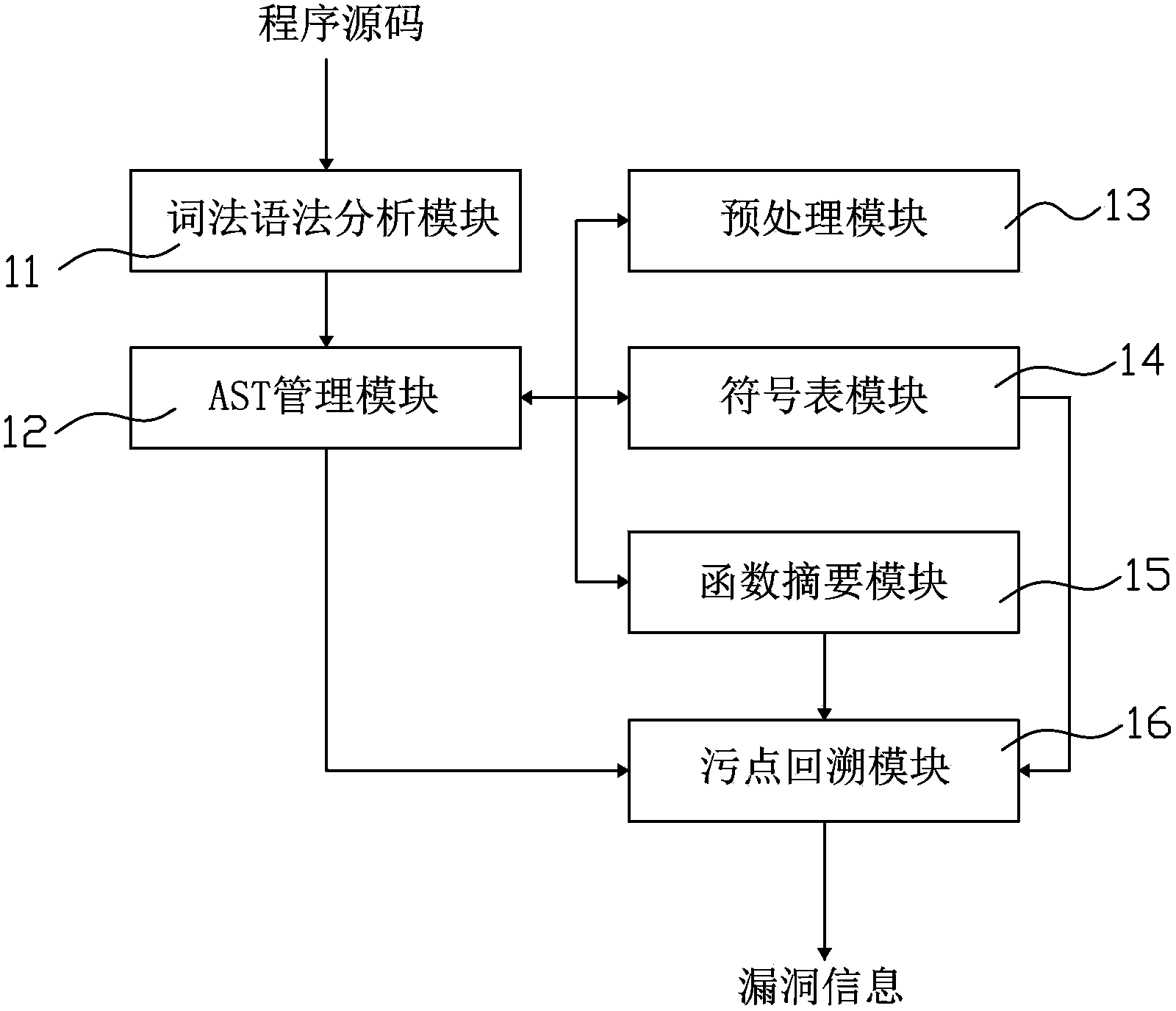
[0038] refer to figure 1 , the first embodiment provides a page vulnerability detection device 100, which includes: a lexical syntax analysis module 11, an abstract syntax tree (Abstract Syntax Tree, AST) management module 12, a preprocessing module 13, a symbol table module 14, a function summary module 15 and the stain backtracking module 16.
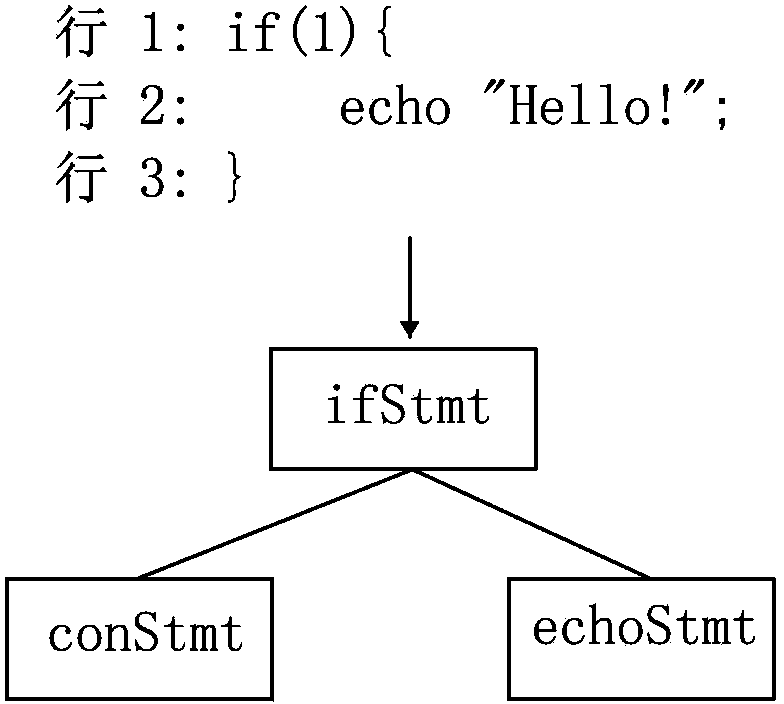
[0039] The lexical and grammatical analysis module 11 is used to read in the program source code, convert the source code into AST through the lexical and grammatical analysis process of the compiling principle, and hand it over to the AST management module for management. For example, each statement in the program source code will correspond to a node converted into AST. refer to figure 2 , such as if(){} will be converted into an ifStmt node, and the corresponding source code information (such as row information) can be saved in the node. The conditional judgment statement (the part inside the parentheses in the first line) and ...
no. 2 example
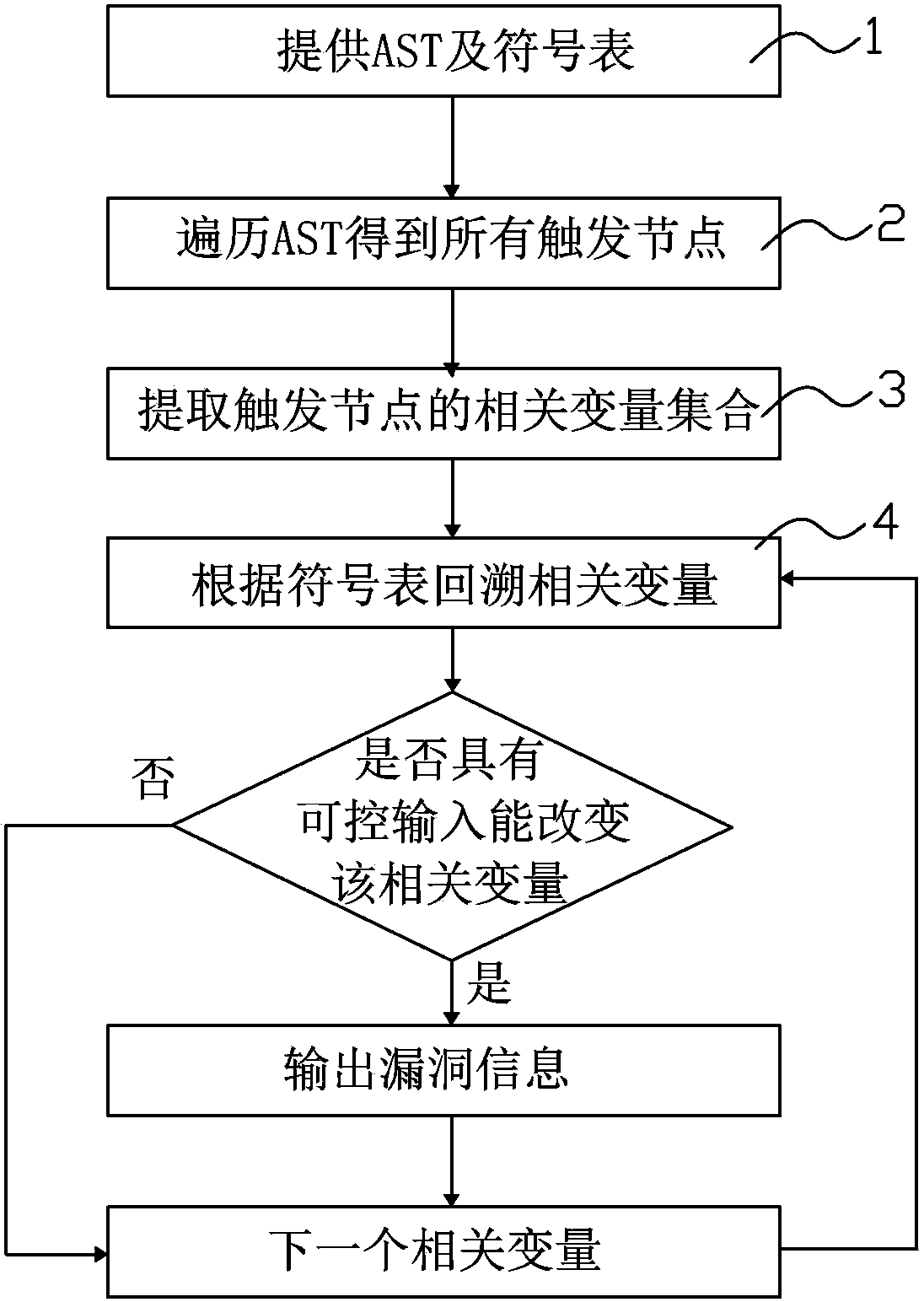
[0055] refer to image 3 , the second embodiment provides a method for detecting page vulnerabilities, which includes the following steps:
[0056] Step 1. Provide the abstract syntax tree and symbol table information of the source code of the detected program;
[0057] Step 2, traversing the abstract syntax tree to obtain all trigger nodes;
[0058] Execute for each trigger node:
[0059] Step 3, extracting the set of all related variables according to the symbol table information; and
[0060] Step 4. Backtracking each related variable, if it is found that the related variable can be changed by an input controllable by the attacker, it is regarded as finding a vulnerability and outputting the vulnerability information.
[0061] The abstract syntax tree and symbol table information in step 1 can be prepared before step 1 is performed, or the abstract syntax tree and symbol table information that has been processed by other external programs can be directly used. The speci...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com