Vulnerability detection method and system based on fuzzy technology
A technology of vulnerability detection and fuzzy technology, applied in the field of vulnerability detection based on fuzzy technology, it can solve the problems of low accuracy, complex operation, single vulnerability, etc., to achieve the effect of automation and intelligence, and improve vulnerability coverage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
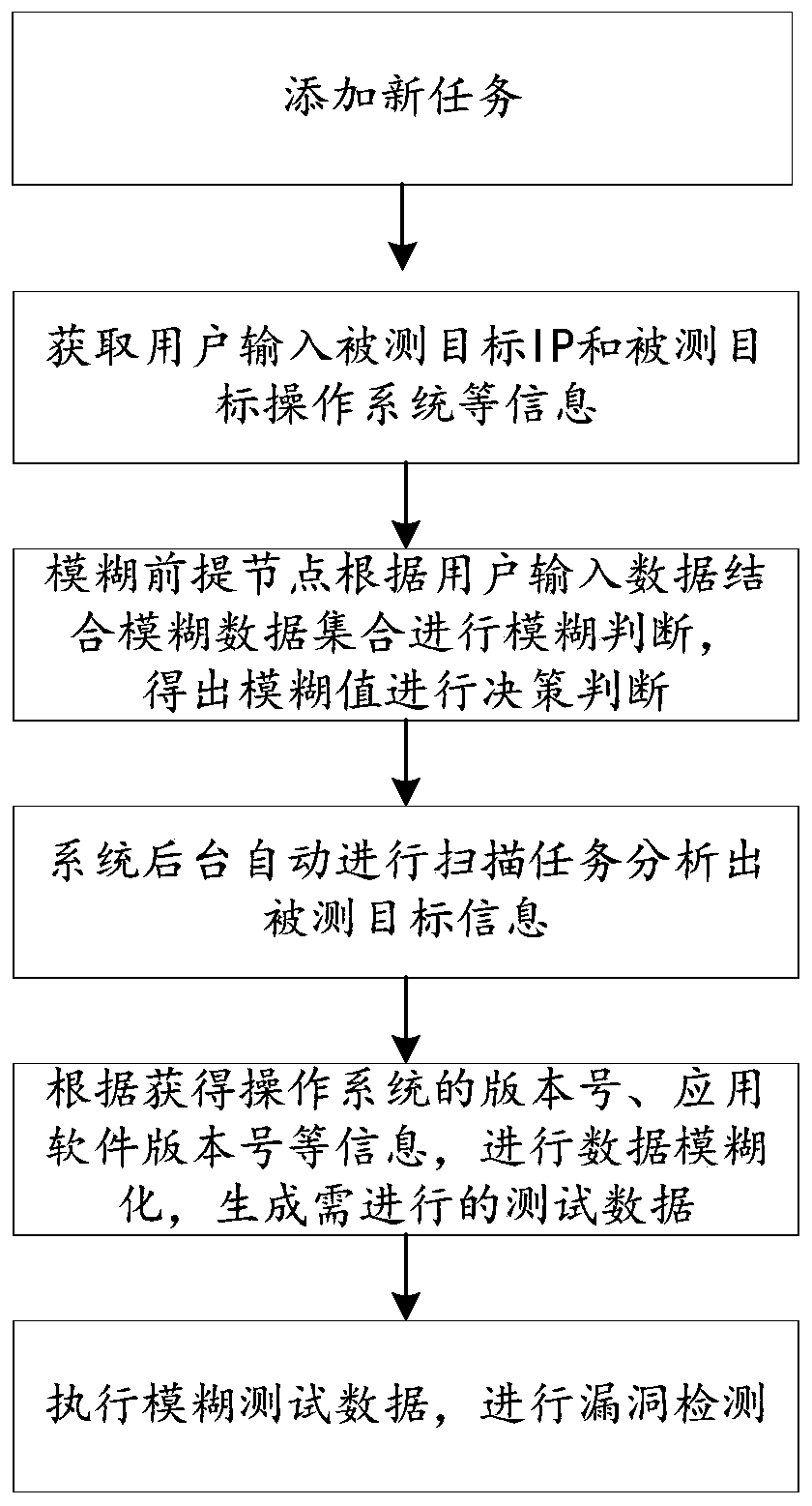
[0030] In the technical solutions disclosed in one or more embodiments, such as figure 1 As shown, a vulnerability detection method based on fuzzy technology includes the following steps:
[0031] Step 1, set up the fuzzy target decision tree model, adopt the fuzzy target decision tree model to formulate the rough data of target recognition scanning as the target recognition scanning strategy;
[0032] Step 2, determine the communication port number to communicate with the target host according to the target identification scanning strategy, obtain the information of the target host, and determine the detection target;
[0033] Step 3. According to the target host information, use a fuzzy algorithm to scan the detection target for vulnerabilities to determine whether there are vulnerabilities.
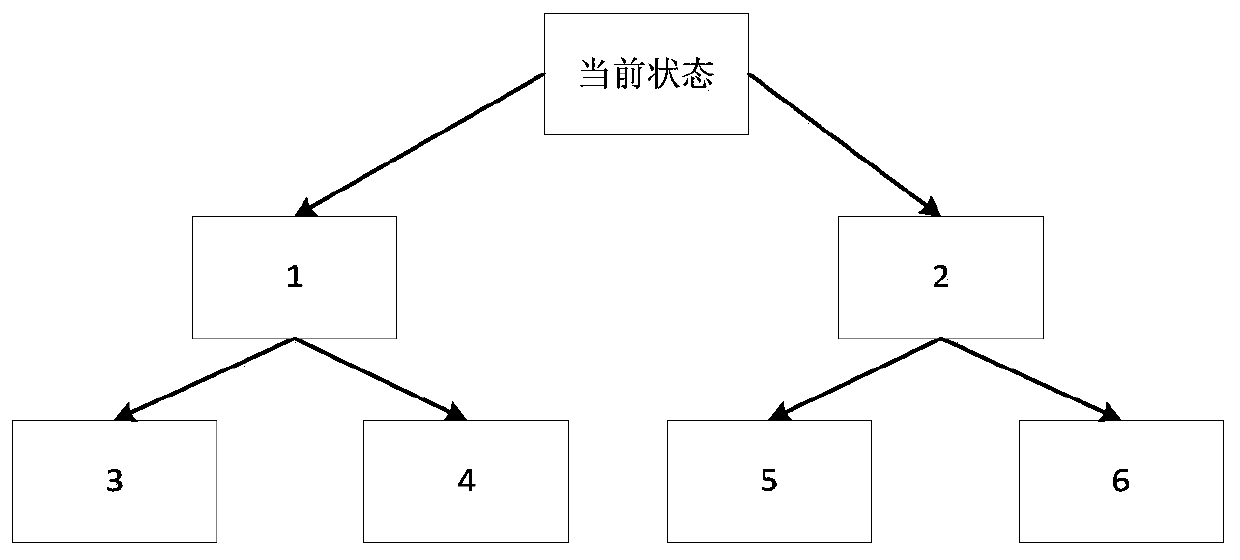
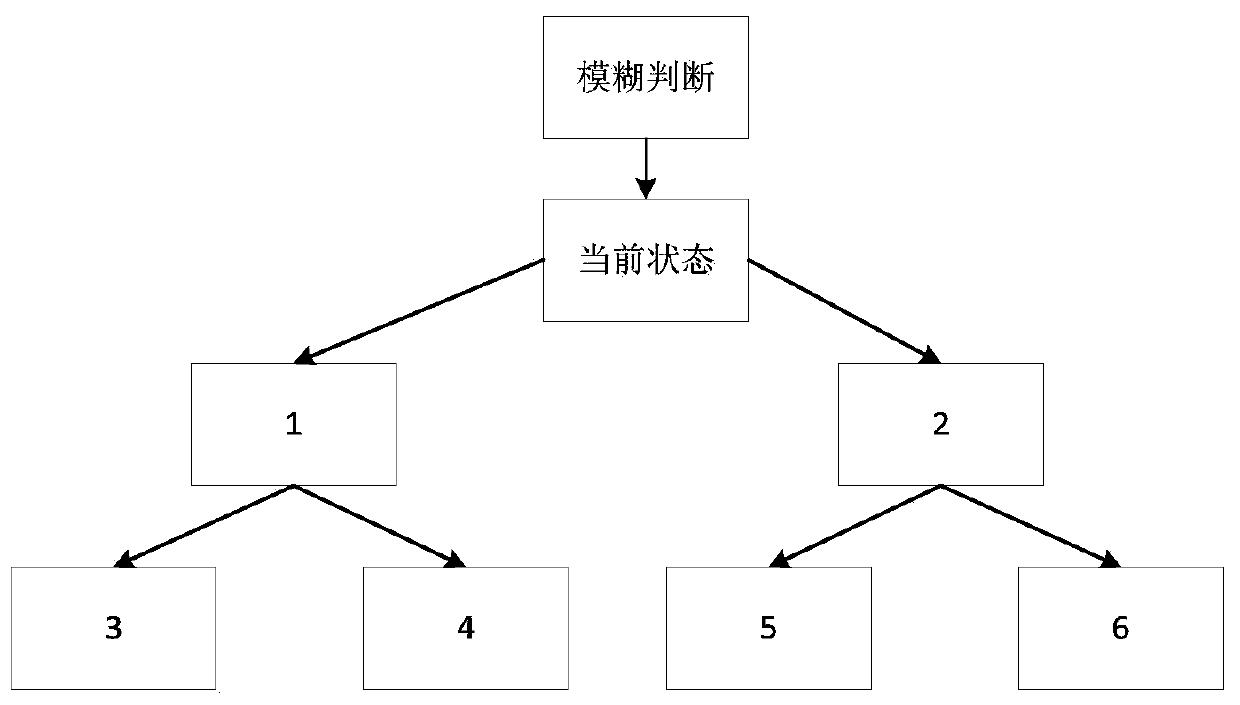
[0034] In step 1, a fuzzy target decision tree model is established, and the target identification scanning strategy of the fuzzy target decision tree model is adopted, including the ...
Embodiment 2
[0065] This embodiment provides a vulnerability detection system based on fuzzy technology, including:
[0066] A target recognition strategy formulation module; used to establish a fuzzy target decision tree model, and use the fuzzy target decision tree model to formulate the rough data of the target recognition scan as a target recognition scan strategy;
[0067] Detection target determination module: used to determine the communication port number to communicate with the target host according to the target identification scanning strategy, obtain the information of the target host, and determine the detection target;
[0068] Vulnerability Judgment Module: It is used to scan the detection target for vulnerabilities based on the information of the target host using a fuzzy algorithm to determine whether there is a vulnerability.
[0069] Further, the fuzzy target decision tree model includes a fuzzy judgment premise node and a decision tree node with an expected value; the f...
Embodiment 3
[0075] This embodiment provides an electronic device, including a memory, a processor, and computer instructions stored in the memory and executed on the processor. When the computer instructions are executed by the processor, the steps described in the method in Embodiment 1 are completed.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com