Concealed anonymous communication method based on peer-to-peer network
An anonymous communication and peer-to-peer network technology, applied in the field of information security, can solve the problems of peer-to-peer node monitoring, inability to hide, inability to provide user concealment, anonymous file sharing, etc., to achieve the effect of protecting user privacy and increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
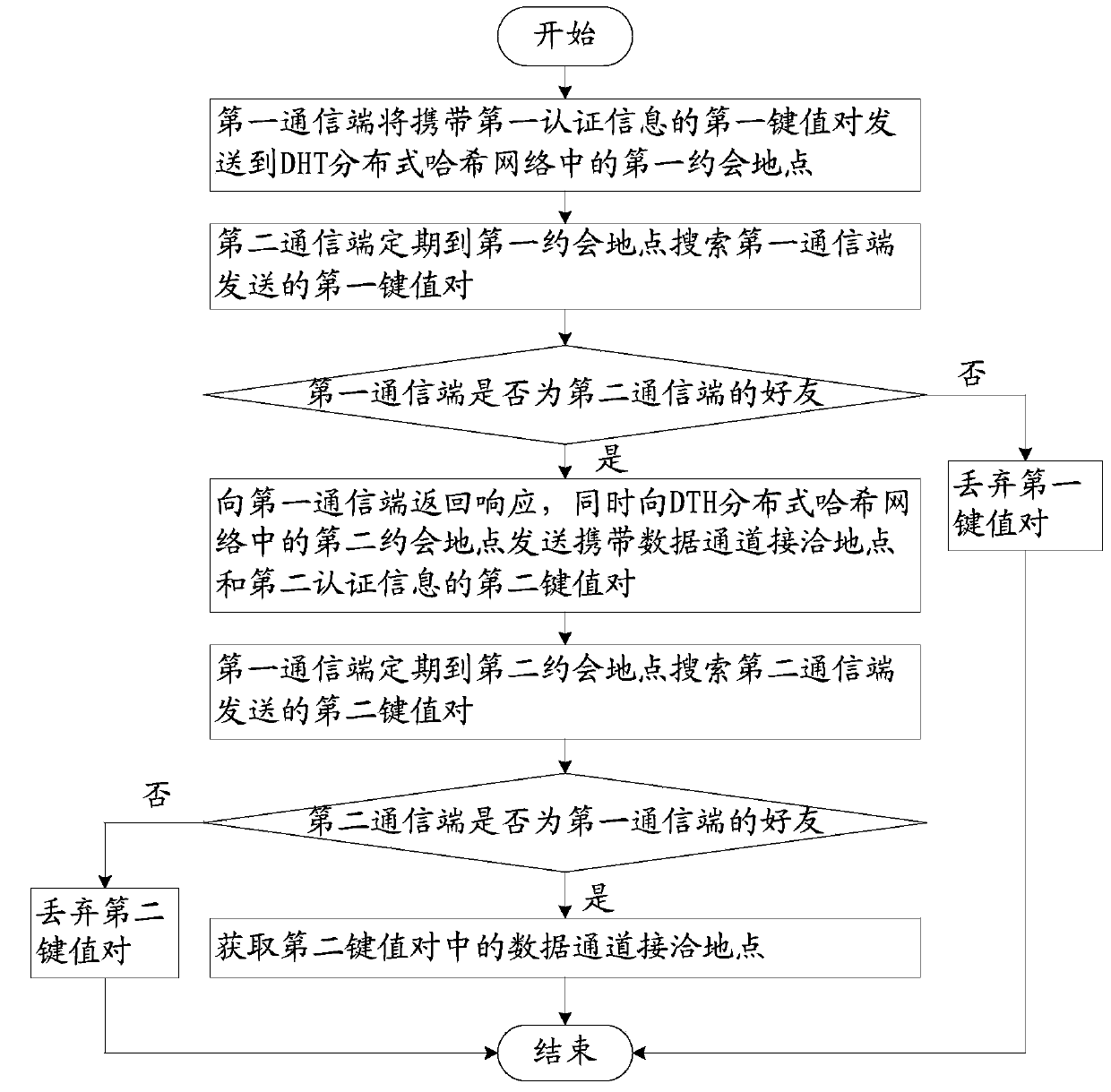
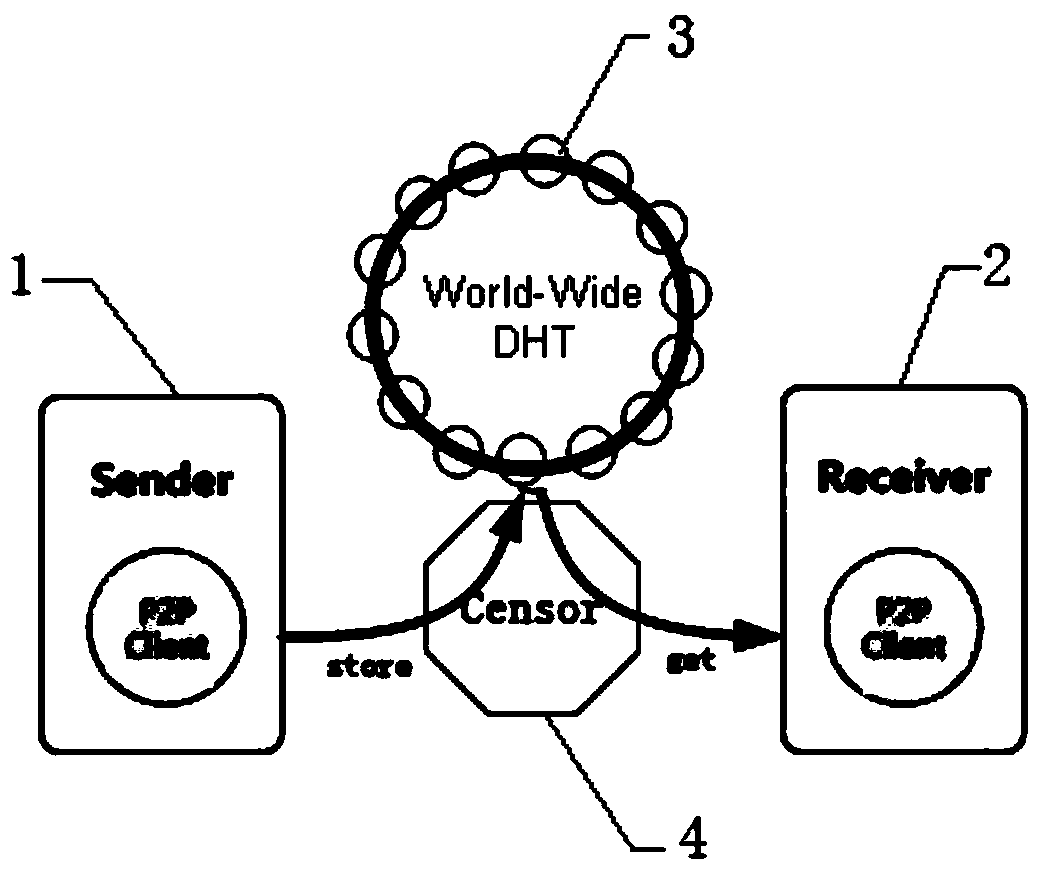
[0044] Such as figure 1 As shown, a concealed and anonymous communication method based on a peer-to-peer network includes the following steps:
[0045] Step 1: Both communicating parties negotiate a shared secret K through out-of-band negotiation;
[0046] Step 2: According to the shared secret K, the communication parties conduct identity authentication through the covert handshake protocol, and secretly negotiate the contact location ID of the data channel;
[0047] Step 3: The first communication terminal derives several sub-data channel contact point IDs by using a certain algorithm according to the data channel contact point ID;
[0048]Step 4: The first communication terminal uses the threshold secret sharin...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap