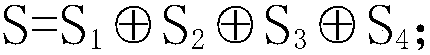A method of network traffic detection
A network traffic and detection method technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems of lack of application layer analysis, inability to identify Bittorrent traffic, etc., to achieve easy promotion, high-speed identification and measurement, and improve efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] A network traffic detection method of the present invention will be described in detail below in conjunction with the accompanying drawings.
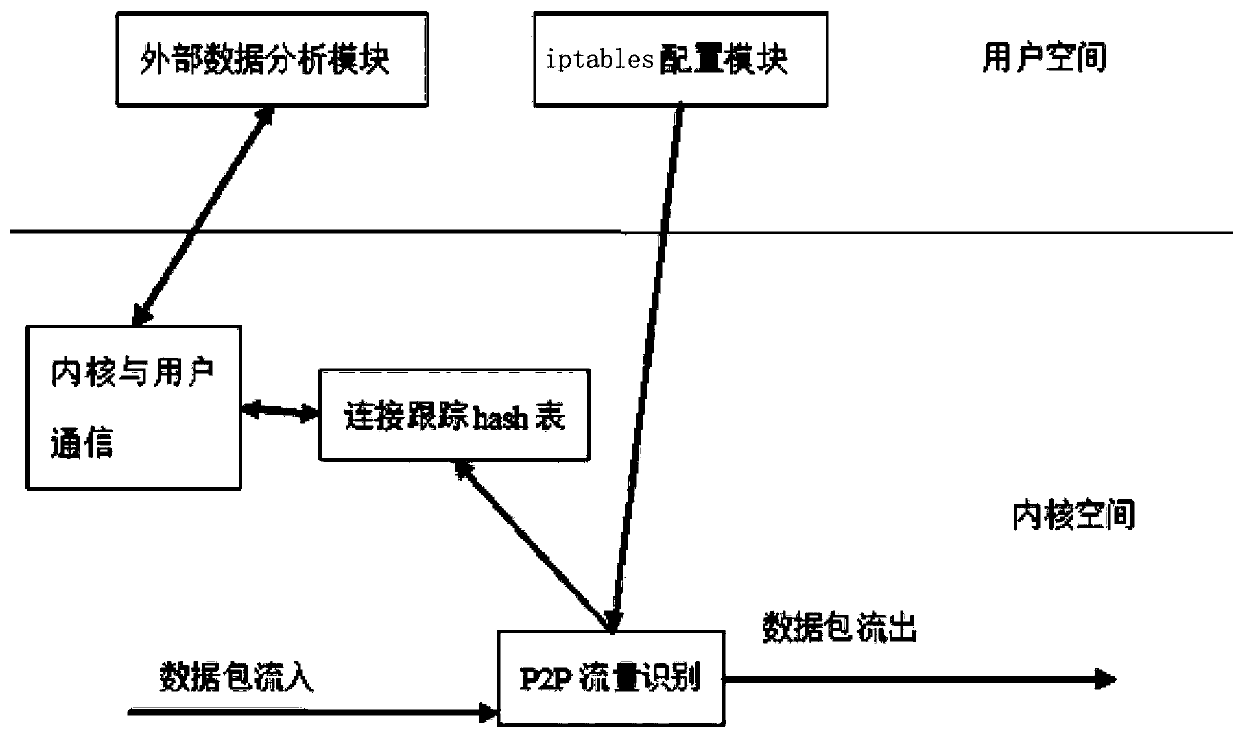
[0026] as attached figure 1 , figure 2 As shown, the present invention provides a network traffic detection method, and its specific implementation process is:
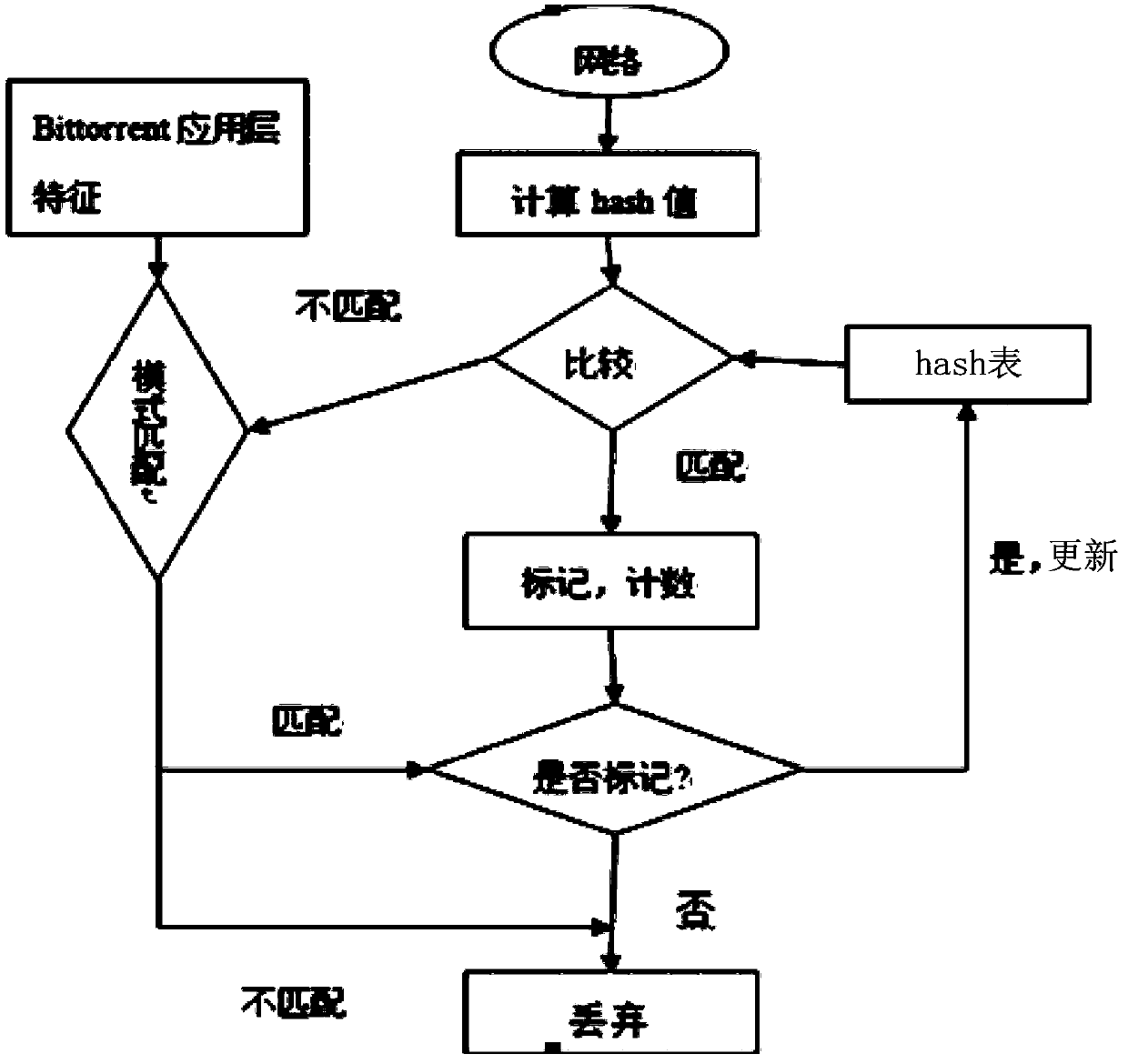
[0027] 1. Identify P2P protocol traffic: How to accurately and quickly identify P2P network data packets has become a difficult problem. A relatively simple method is to determine the P2P network traffic directly through known commonly used ports of P2P software, but this may cause other applications using one of the ports to be unable to use normally. In addition, if the P2P application software can dynamically adjust the port, then this method is powerless. For example, BitTorrent usually listens on port 688l. If this port is occupied, it will try to reach port 6889. The present invention adopts the method of summarizing the characteristic codes of network data pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com