Log protecting method based on distribution modes
A log and pattern technology, applied in the direction of digital data protection, generation of response errors, error detection of redundant data in calculations, etc., can solve problems such as difficulty in finding log sequences, no backup, no access rights, etc., and achieve log The content is continuous, ensuring continuity, and realizing the effect of authority access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with specific examples.
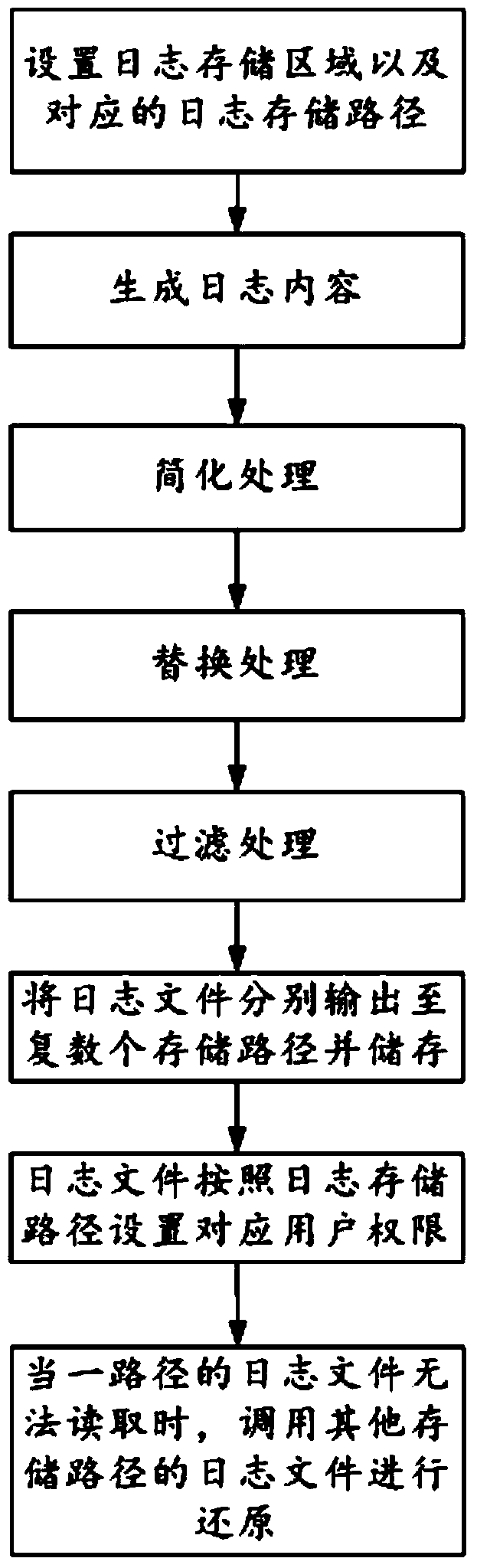
[0029] see figure 1 , a kind of log protection method based on distribution pattern of the present invention, comprises steps:
[0030] First, set log storage areas and corresponding log storage paths on multiple storage media;
[0031] Next, generate the log content;
[0032] Then, the log processing step is carried out: simplifying and replacing the log content to form a log file;
[0033] Wherein, the simplified processing steps include the steps of: extracting event type information, operation record information and post-operation storage pool status information of log content; outputting to a log storage path and storing.
[0034] The replacement processing step further includes the step of: adding disk information corresponding to the device after each device name in the log content, and the disk information includes serial number information and slot number informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com