Data processing method and apparatus
A data processing and data technology, applied in the field of communication, can solve the problems of not being able to find malicious ordering behaviors of CRBT, heavy workload, uncertain time, etc., and achieve the effect of reducing malicious ordering behaviors of CRBTs, improving efficiency, and ensuring real-time performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
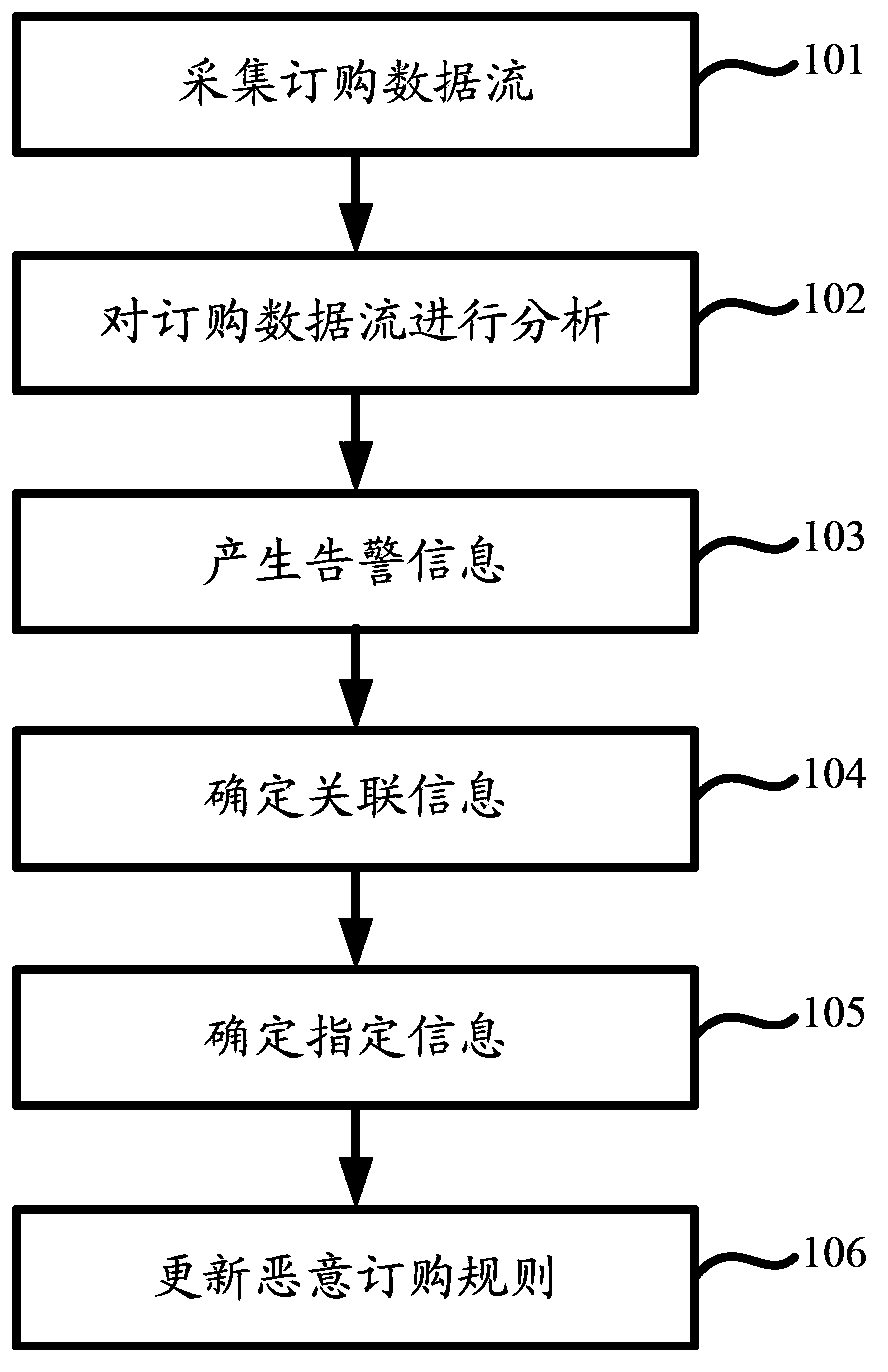
[0026] Embodiment 1 of the present invention provides a data processing method, the steps of the method can be as follows figure 1 shown, including:
[0027] Step 101, collect order data flow.
[0028] In this step, the ordering data flow of ordering CRBT in the CRBT platform can be collected. Ordering data flow can include but is not limited to SMS ordering, website ordering, Interactive Voice Response (IVR, Interactive Voice Response) voice interaction platform ordering, unstructured supplementary data service (USSD, UnstructuredSupplementary Service Data) ordering, wireless application protocol (WAP, The subscription data flow generated by MMS subscription methods such as Wireless Application Protocol) may also include the data flow generated by links such as CRBT copying and CRBT gifting that generate the subscription data flow.
[0029] In this embodiment, it can be understood that the CRBT includes ringtone objects such as service provider (SP) ringtone, group ringtone...
Embodiment 2
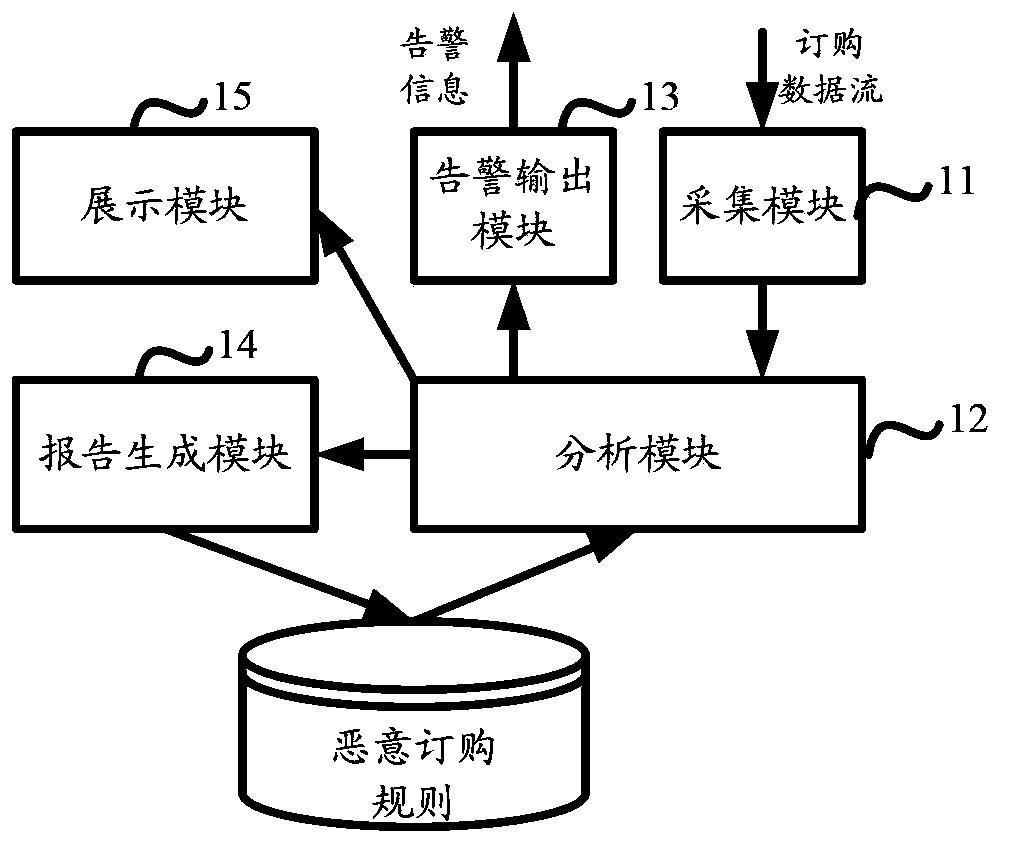
[0060] Embodiment 2 of the present invention provides a data processing device, the structure of which can be as follows figure 2 shown, including:
[0061] Acquisition module 11 is used for collecting the ordering data flow of ordering CRBT in the CRBT platform; Analysis module 12 is used for determining whether the ordering data flow collected includes malicious ordering data according to preset malicious ordering rules; Alarm output module 13 is used for targeting The malicious order data determined by the analysis module generates an alarm message.
[0062] The device also includes a report generation module 14:
[0063] The report generation module 14 is used for determining associated information in the malicious order data determined by the analyzing module; and determining specified information corresponding to the malicious order data according to the associated information.
[0064] The report generation module 14 is further configured to use the determined malici...
Embodiment 3
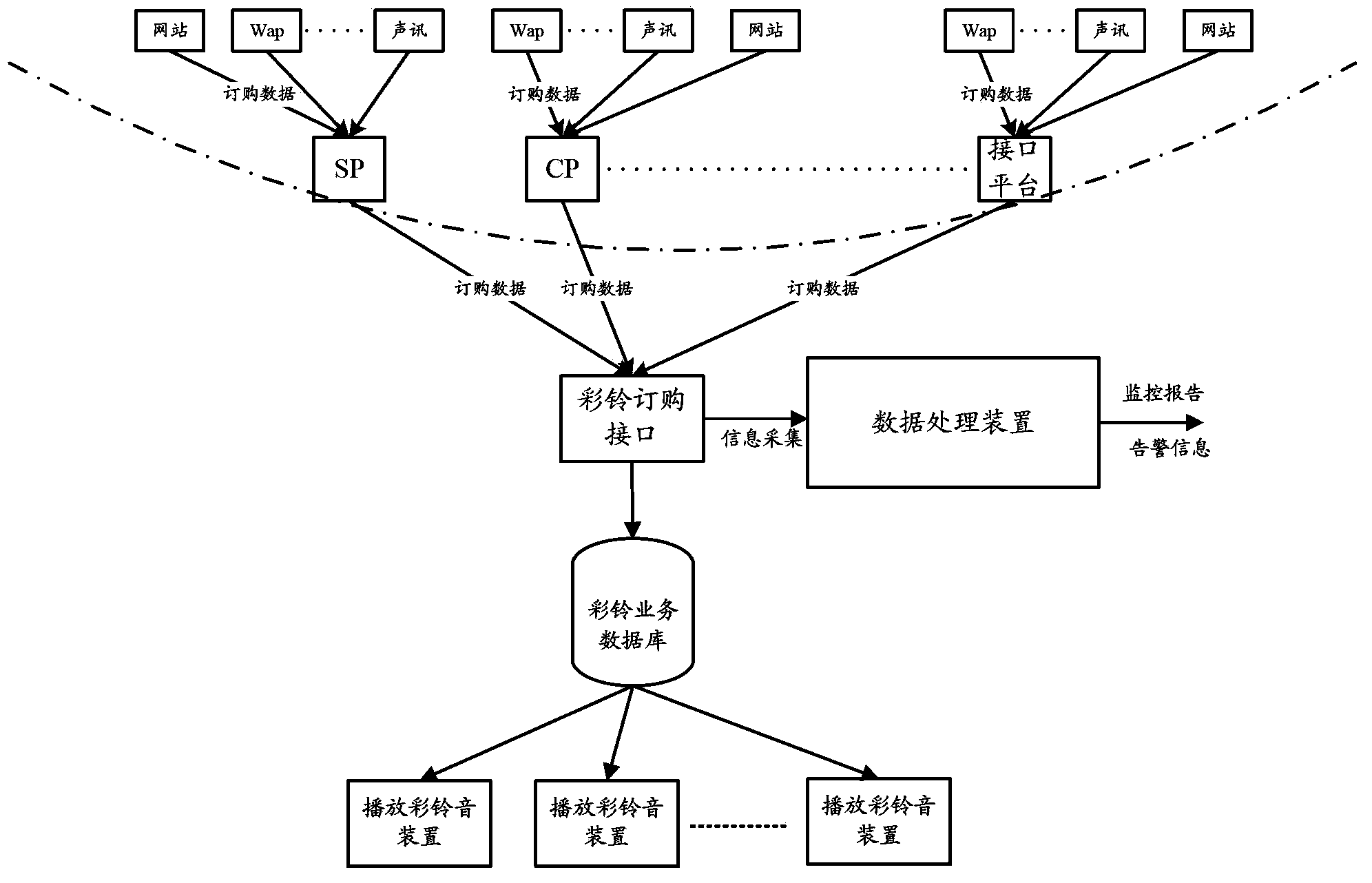
[0071] In combination with Embodiment 2, this Embodiment 3 provides the implementation principle of the data processing method described in Embodiment 1. The implementation principle can be as follows image 3 shown.
[0072] When users order CRBT through websites, voice messages or WAP, etc., the order data can be forwarded by SP, content provider (CP), interface platform, etc., sent to the CRBT ordering interface, and then sent to the CRBT service database through the CRBT ordering interface. The database can realize the playing of the CRBT through the corresponding device for playing the CRBT sound, and realize the response to the CRBT ordering data. However, the data processing device provided by Embodiment 2 of the present invention can collect ordering data streams from the CRBT ordering interface, so that the ordering data streams can be analyzed subsequently, and the malicious ordering behavior of CRBTs can be monitored, and alarm information and monitoring reports can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com