Method and system for protecting object files
A target file and protection system technology, applied in the direction of program/content distribution protection, etc., can solve problems such as inability to protect, achieve the effect of increasing the scope of protection, improving security, and increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The target file protection method and protection system of the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments, but this is not intended to limit the present invention.
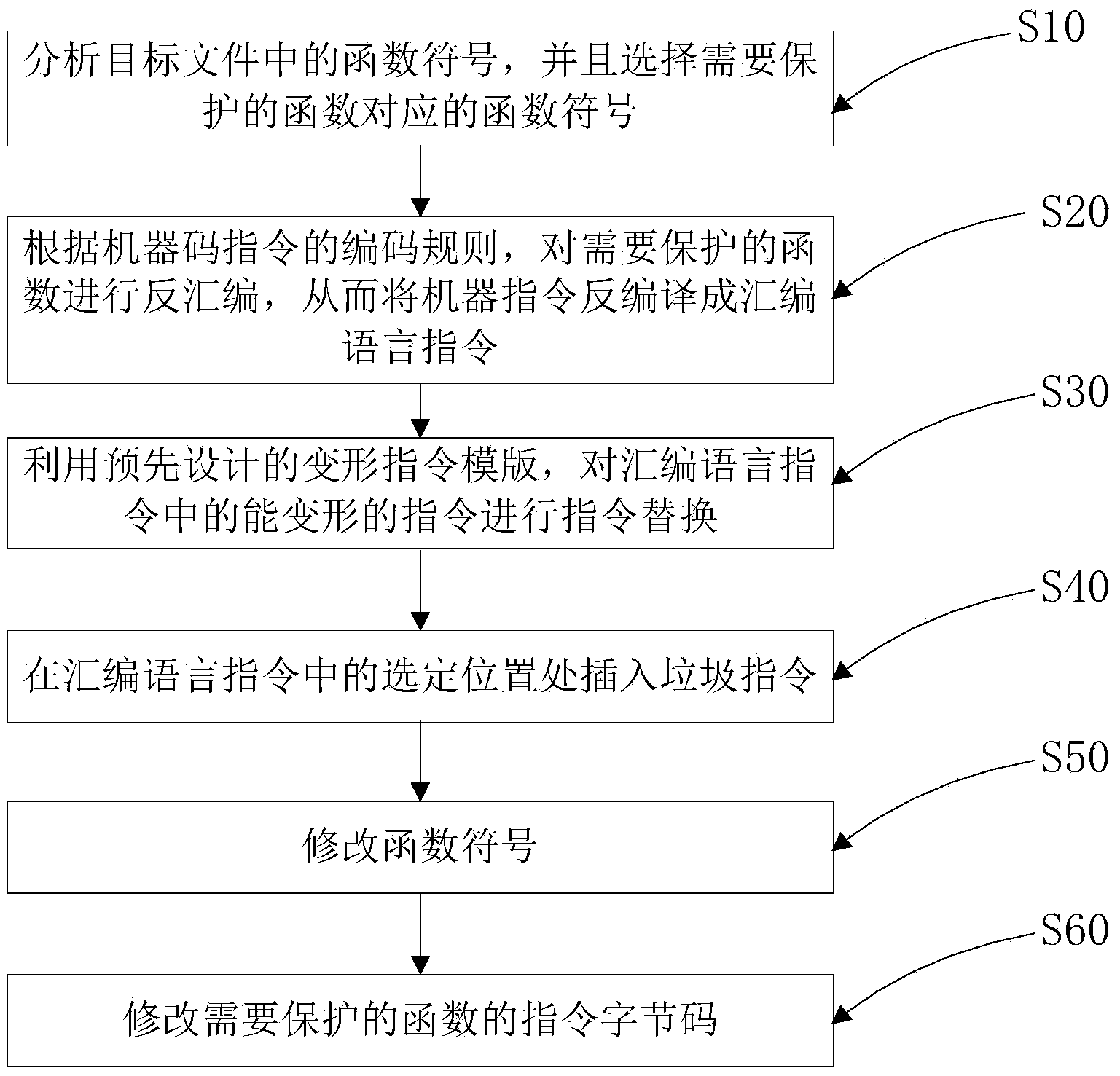
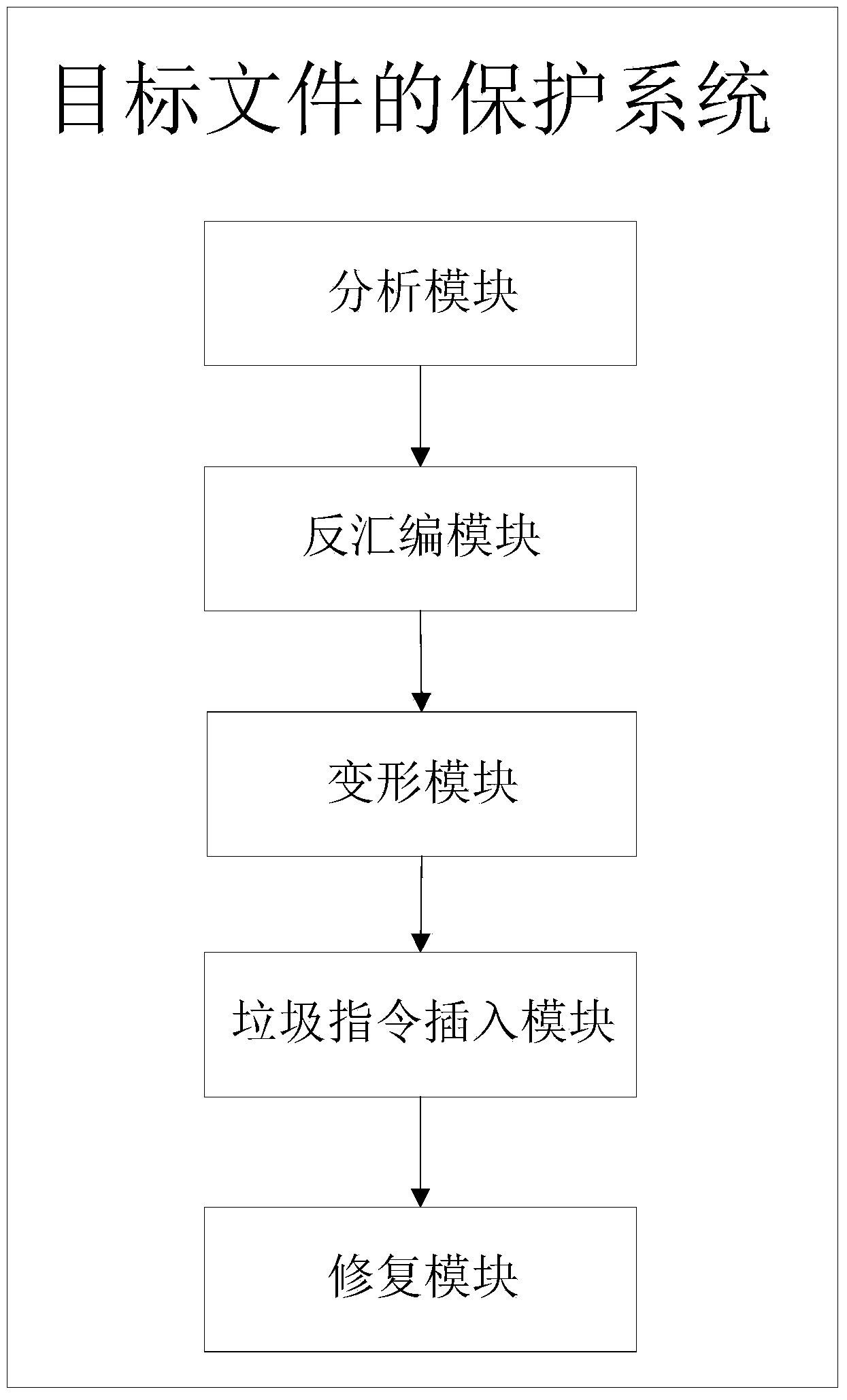
[0041] figure 1 It is a schematic flowchart of a method for protecting a target file according to an embodiment of the present invention. The protection method of the target file of the embodiment of the present invention comprises: After disassembling the function that needs to be protected in each target file used in the software, transforming the instruction of the function, and inserting garbage instructions in the function, thereby Individual object files are protected to form an overall protection for the software.
[0042] The method adopted in the embodiment of the present invention includes the following steps:
[0043] S10: Analyze the function symbols in the target file, and select the fun...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com