Protection method and device for privacy data of application program
An application and privacy data technology, applied in the field of data processing, can solve the problems of application privacy data leakage, easy to crack passwords, restricting users' right to access applications, etc., to improve security, protect private data, and avoid data intrusion. Effects of compatibility issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
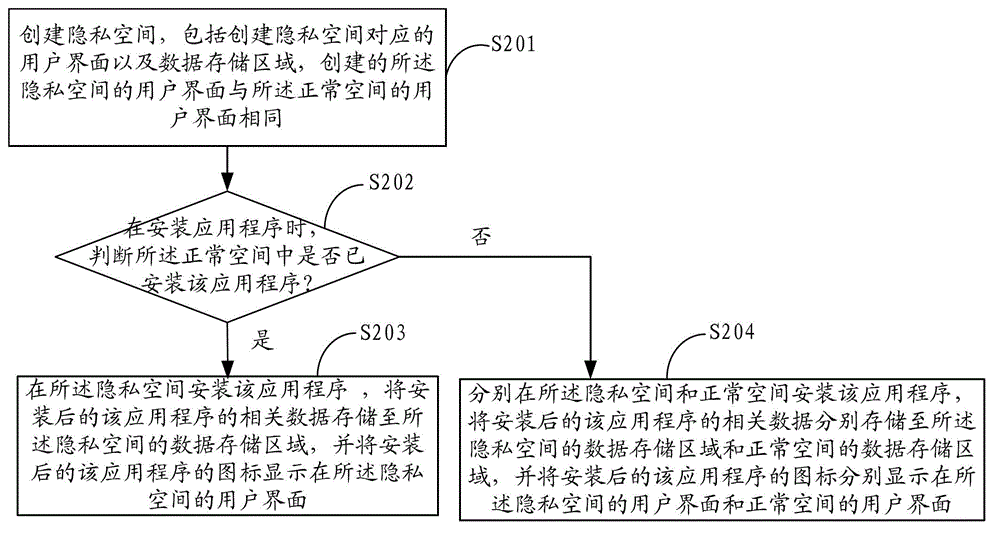
[0030] figure 2 It shows the implementation flow of the application privacy data protection method provided by the first embodiment. The application scenario of this method is applied to a terminal device with a normal space, and the normal space includes a corresponding user interface and a data storage area. The process The details are as follows:
[0031] In step S201, a private space is created.
[0032] In practical applications, a private space creation button or a private space creation instruction can be set in advance, and after receiving the user’s click on the private space creation button or the private space creation instruction, start to create a private space, including creating a private space The corresponding logo, user interface and data storage area, etc.
[0033] Wherein, at least one private space is created, and the application programs installed in each private space may be the same or different.
[0034] It should be noted that, in order to protect...
Embodiment 2
[0062] image 3 It shows the implementation flow of the application program privacy data protection method provided by the second embodiment. The application scenario of the method is applied to a terminal device including a normal space and a private space, and the normal space and the private space both contain corresponding user Interface and data storage area, wherein the user interface of the private space is the same as the user interface of the normal space, the data storage area of the private space is different from the data storage area of the normal space, and the process is described in detail as follows
[0063]In step S301, when installing the application program, install the application program in the private space and the normal space respectively, and store the relevant data of the installed application program in the data storage area of the private space and the normal space respectively. The data storage area, and the icon of the installed application...
Embodiment 3
[0079] Figure 4 The structure of the application program privacy data protection device provided by the third embodiment of the present invention is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown.
[0080] The application program privacy data protection device is applied to a terminal device (such as a mobile phone, a tablet computer, a handheld computer, a computer, etc.) containing a normal space, and the normal space includes a corresponding user interface and a data storage area.
[0081] The application program privacy data protection device includes a space creation unit 41 , a first determination unit 42 and an application program installation unit 43 . Among them, the specific functions of each unit are as follows:
[0082] A space creating unit 41, configured to create a private space, including creating a user interface and a data storage area corresponding to the private space, the created...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com